Decentralized identity blockchain projects

Giving people authority and control over their digital identities is the goal of the Decentralised Identity (DID) idea. DID enables users to self-generate and manage their unique IDs, as well as choose when, how, and with whom to disclose their personal information, in contrast to traditional digital identification systems, which manage and control user data and credentials through a central authority or service provider. Centralised systems, in which the service provider has authority and users entrust them with their data, stand in stark contrast to this.
Also Read About Decentralized Application Architecture: Guide To DApp Design
Need for Decentralized Identity
There are serious problems with conventional identity models that are driving the quest for DID:
Centralised Control and Single Point of Failure
User data is kept and managed by a single organisation in federated systems (where identity is managed by a trusted third-party Identity Provider) or centralised identity systems (such as conventional websites that require a username and password). This results in a single point of failure that is susceptible to mistakes, manipulation, or hacking. Widespread chaos could result from the compromise of this controlling authority. Additionally, traditional identity systems frequently have poor security procedures that have resulted in large losses.
Absence of User Control
In conventional systems, users frequently have little say over who can view, access, or use their data. They can give up their privacy. Social media sites, for example, serve as the main authorities controlling user information and attributes.
Data breaches and privacy issues
Centralised systems are vulnerable to improper handling of personal information. Concern over the use of gathered data by governments and businesses is growing.
Friction and Intermediaries
In order to build credibility and validate credentials, traditional systems frequently depend on outside parties (such as banks or solicitors for contracts or background check services for identities). Friction, delays, and expenses result from this.
DID uses decentralised technology like blockchain to try to solve these problems.
Evolution of Digital Identity
Over the years, digital identity has changed:
- Centralised Identity: In the early days of the internet, each service had its own unique username and password, which were kept in potentially unsafe central repositories.
- Federated Identity: Single Sign-On (SSO) across several services is made possible by this architecture, which introduced Identity Providers (IdPs) to handle authentication. It still used a central IdP to store user data even though it lessened password fatigue.
- Although it still frequently involved centralised control, user-centric identification improved upon federated identity by granting users some degree of consent about data sharing.
- The following stage, known as Decentralised Identity (DID), is frequently based on decentralised networks and emphasises user autonomy and control over identity.
Also Read About Features, Advantages Of Symmetric Cryptography In Blockchain
How Decentralized Identity Works
Three primary responsibilities are frequently involved in DID architectures:
- Verifiable credentials (VCs) are digital evidence of attributes (such as a degree, driver’s license, or work status) that are issued by an organisation (such as a university, government agency, or business).Holder: The person who obtains and safely keeps these VCs (for example, on a mobile device).
- Verifier: An organisation that has to confirm the holder’s credentials, such as a bank, airline, or employer.
The process typically involves
- On a blockchain, the Issuer and Verifier generate public/private key pairs and a public DID. Using their private key, the Issuer signs the VC that is sent to the Holder and adds a reference hash of the VC not the actual personal information to a public blockchain. As a result, the data may be independently audited and verified.
- The Holder can share the VC with a Verifier and keeps it safe.
- After receiving the VC, the Verifier verifies its integrity and validity by comparing it to the reference data (the hash) that the Issuer has signed on the blockchain.
- By amending the blockchain’s reference data, which the Verifier may verify, the Issuer can cancel a VC if needed.
Importantly, the blockchain does not keep the user’s personal information. Only hashes or cryptographic proofs are stored, protecting privacy while permitting verification. This complies with data privacy laws such as GDPR. Using cryptographic procedures, the identity itself is frequently generated from a private-public key pair, enabling a self-managed, distinct identity.
Also Read About Types Of Blockchain Wallets: Hot, Cold, Hardware And More
Key Features and Benefits of DID
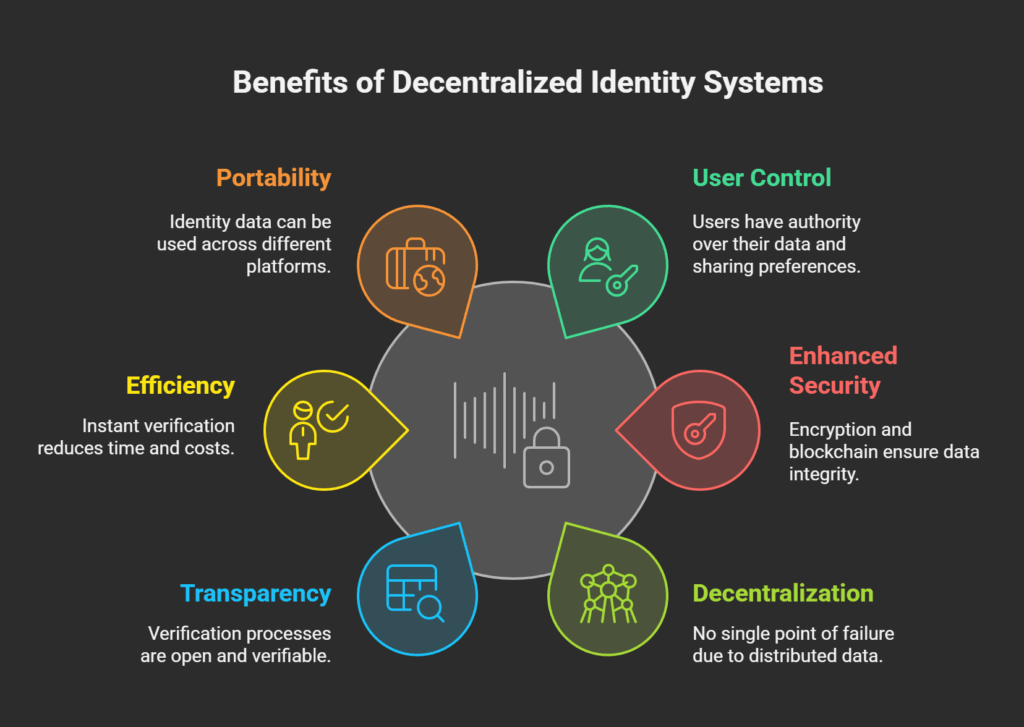
Compared to conventional identity systems, DID has the following benefits:
User Control
Users have authority over their own data and choose what and with whom to share it. This guarantees security and privacy.
Enhanced Security and Integrity
The system is resistant to manipulation since it relies on encryption and the blockchain’s immutability. Since any alteration to the blockchain’s recorded hash would suggest data manipulation, integrity is preserved. DID ensures the presence of credentials and offers protection.
No Single Point of Failure
Because it is decentralised, there isn’t a single server or authority that controls all the data, which removes a significant vulnerability.
Transparency and Trust
The verification procedure can be transparent, even when personal information is kept private. Verifiable credentials that are confirmed on an open, unchangeable ledger and signed by reliable Issuers are the foundation of trust.
Efficiency
Time-consuming background checks through middlemen are no longer necessary because verifiers may instantaneously verify the legitimacy of credentials against the blockchain reference. In general, disintermediation can lower expenses and boost efficiency.
Portability
Users are not restricted to a particular supplier and can use their identity data anywhere they choose.
Challenges
Notwithstanding the advantages, DID implementation has drawbacks:
- Management of Private Keys: Users need to keep their private keys or mnemonic phrases safe because they can be lost, which could result in the loss of their identity and related assets.
- Complexity for Mainstream people: Non-technical people may find it challenging to understand the technical principles.
- Building Trust with Issuers/Verifiers: Although DID eliminates the need for a central authority, confidence in the organisations that issue and validate credentials is still required.
- Scalability: The underlying blockchain network must be able to manage potentially enormous volumes of data references and identity-related transactions.
- Interoperability and Standards: Common standards, such as those created by the W3C, must be followed to guarantee that various DID systems and VCs are interoperable and mutually recognised.
Applications and Use Cases
There are several possible uses for decentralised identity:
- National Identity Programs: These programs provide residents with a fundamental identity that is connected to other official documents such as social security, driver’s licenses, and voter IDs.
- KYC and Onboarding: Instantaneous credential verification allows for the smooth remote digital onboarding of clients, staff, and students.
- Authorisation and Authentication: Next-generation authentication may eventually take the place of conventional passwords for system and service access.
- Enabling safe and verifiable online voting while safeguarding voter privacy and avoiding fraud such as double voting is known as remote e-voting.
- Background Verification: Simplifying the process of confirming credentials such as work history and degrees.
- Healthcare: providing health passports, confirming the credentials of medical personnel, and securely sharing patient data with consent.
- Supply chain management involves locating participants and confirming the provenance and validity of products.
- The Internet of Things (IoT): Giving devices distinct identities to enable safe and verified machine-to-machine communication.
- Decentralised Finance (DeFi): A strong digital identity is necessary to manage the ownership of digital currency and assets.
- Managing permissions to read data recorded on ledgers in permissioned blockchains is known as access control.
DID is already the focus of a number of projects and businesses, including those supported by Ethereum, Microsoft, and Hyperledger. Decentralised Identifier standards are largely defined by the W3C.
