This article gives an overview of How Phishing Works, What it is and how to Recognize it.
What is Phishing Attack in Crypto?

Phishing, a fraudulent technique, involves attackers posing as reputable services to obtain private data. This is equivalent to posing as reliable wallets, platforms, or even people in the cryptocurrency space.
The attackers aim: The main goal of phishing is to steal user information, which in the context of cryptocurrency means getting into accounts and taking money out of them. The goal of an attack is to get private keys, seed phrases, or wallet and exchange login information.
Nature Irreversible and Decentralized: Due to the irreversible and decentralized nature of bitcoin transactions, these attacks are very frequent and destructive. Often, recovery is impossible once attackers have depleted funds.
Influence and Prevalence: The crypto industry’s biggest source of financial losses in 2024 was phishing, with almost USD 1 billion taken in 296 cases nearly 50% of the total value lost and 39.1% of all security events. The cost of phishing attacks to 30,287 victims was USD 225 million in the first half of 2017.
How Phishing Attacks are Carried Out
Phishing attacks are highly skilled forms of social engineering that are intended to fool people into disclosing private information or doing things that jeopardize their security. These attacks usually start with well-written letters that use psychological tricks to further their malevolent objectives.
Phishing attacks typically begin with an attacker sending messages that appear to be from reliable sources, such wallet providers, cryptocurrency exchanges, well-known decentralized applications (dApps), or even businesses that appear to be legitimate (e.g., banks, shipping services, tech support). The purpose of these carefully crafted messages is to:
Appeal to Urgency or Fear: Attackers often create a sense of impending doom or danger to get a hasty, thoughtless response.
- They may complain about unusual account activity, which may suggest illicit access or a security breach that needs immediate attention.
- Notifications of account issues, including a locked account, an impending suspension, or a necessary “KYC update,” may be sent out, urging prompt action to avoid service disruption.
- Fear of impending financial loss or the urge to “secure your funds now” are strong inducements. This exploits the victim’s fear of losing their assets or forgoing a security window.
- A few examples are “Unusual activity has resulted in the temporary locking of your account.” For instant identification verification, go here,” or “Urgent: Unauthorised login detected from a new device.” Make a password change right now.
Offer Enticements: Phishers may also use promises of large profits to entice victims, appealing to their avarice or desire for special opportunities.
- They can offer enticing investment opportunities with irrational returns, frequently imitating approved Decentralized Finance
protocols or the introduction of new tokens. - Phishing bounties or free bitcoin airdrops may be promised in messages, and the recipient must “connect their wallet” to receive the fictitious award.
- Beta programs, new features, or temporary incentives that circumvent critical thinking are all exclusive.
- A “too good to be true” vibe is frequently associated with these, like “Congratulations! For our unique 1000% APY staking pool, you have been chosen. Go here to sign up.
Disguise Source: Attackers go to great lengths to hide the communication’s true source in order to make it appear authentic, perfecting the imitation of trustworthy organizations.
- By employing spoof email addresses like support@crypt0exchange.com, they look to be from authoritative domains.
- Minor misspellings or different top-level domains (e.g.,.net instead of.com) can be used in typosquatting.
- Fake sender identities are used to impersonate famous people or officials.
- The official logos, branding, and communication methods of trusted brands are frequently used by attackers to establish instant legitimacy, making it hard for an untrained eye to detect the fraud.
Malicious Links and Fake Websites: The main component of the majority of phishing attacks is sending victims to phoney websites and malicious links.
- The messages usually contain links that direct readers to phoney websites. They are often hidden under hyperlinked graphics, in fake material, or using URL shorteners.
- Due to their thorough design, which often matches the actual one pixel by pixel, these fake websites are hard to recognise. For authenticity, they mimic dashboard interfaces, security alerts, and login windows.
- These bogus websites request private keys, seed phrases, usernames, and passwords.
- These credentials allow attackers to quickly access the victim’s money and accounts after submission. This may result in additional abuse, identity theft, or the instant depletion of assets.
Recognizing Phishing Attacks
Red flags might help you recognize phishing attacks despite attackers’ sophisticated attempts to resemble authentic communications. Protecting your digital assets requires recognizing these danger indicators.
Even when attackers masquerade as legitimate emails and websites, several warning signals can detect phishing attacks:
Copycatting: Attackers carefully copy a company’s visual and textual aspects as a main approach. This comprises signature colours, typefaces, text wording, and logos that match or resemble the real brand. The best way to start is to learn the actual branding of the services you use. Check their websites, email templates, and communication style often. This familiarity highlights small differences.
Spelling or Grammar Errors: Phishing emails often reveal themselves through grammatical errors despite their elegant presentation. Haste, carelessness, or a lack of native language proficiency can cause errors in phishing emails. These errors can appear in the topic line, body content, or URL. Errors are rare in legitimate companies with experienced copywriters and editors.
Misleading Links: Most phishing attacks send you to a fake site from here. Attackers hide fake website links using truncated URLs or embedded connections. Hovering over a status bar link without clicking reveals its URL. Do not click if the URL doesn’t match the service’s domain.
Using Public Email Accounts: Sender email address is vital to legitimacy. A suspicious email from a business department or official domain (e.g., “@companyname.com” or “@https://www.google.com/search?q=exchange.com”) ends in “@gmail.com,” “@outlook.com,” or other generic public email domains. Large, renowned companies always send important statements via their official website.
Content Misalignment: Phishing attempts might be detected by message inconsistencies. Look for tone or style differences from the company’s usual communications or mismatched embedded images and text (e.g., “click here to sign up” when the button reads “click here to login”). Any request for sensitive information like your private key or seed phrase in an email or linked form is phishing.
Sense of Urgency or Threats: Phishing efforts can entice you into action without contemplation. Messages may threaten account suspension, fund loss, or a limited-time offer if you don’t act quickly. High-pressure tactics are typical scams.
Generic Greetings: Phishing emails often start with “Dear Customer,” “Dear User,” or “Hello,” instead of your name. Accounts with legitimate services personalize their communications.
Unexpected or Unsolicited Communication: Be wary of any unexpected crypto account email or communication, especially if it’s about a problem or offer you didn’t sign up for. It needs further investigation if it’s unexpected.
Blockchain-Based Phish Detection: The Phish Block Framework
Apart from the awareness of individual users, technological innovations are also being investigated to counteract phishing, especially by utilizing the intrinsic qualities of blockchain technology. A blockchain-based system for phishing detection in cloud environments, Phish Block, is one such proposal.
The avalanche effect, immutability, and decentralized, irreversible nature of blockchain make it a powerful source of security for maintaining data integrity. By ensuring that even minor changes to a block’s content result in significant changes to its hash value and all following blocks, the avalanche effect makes data resistant to unauthorized changes.
How Phishing Works
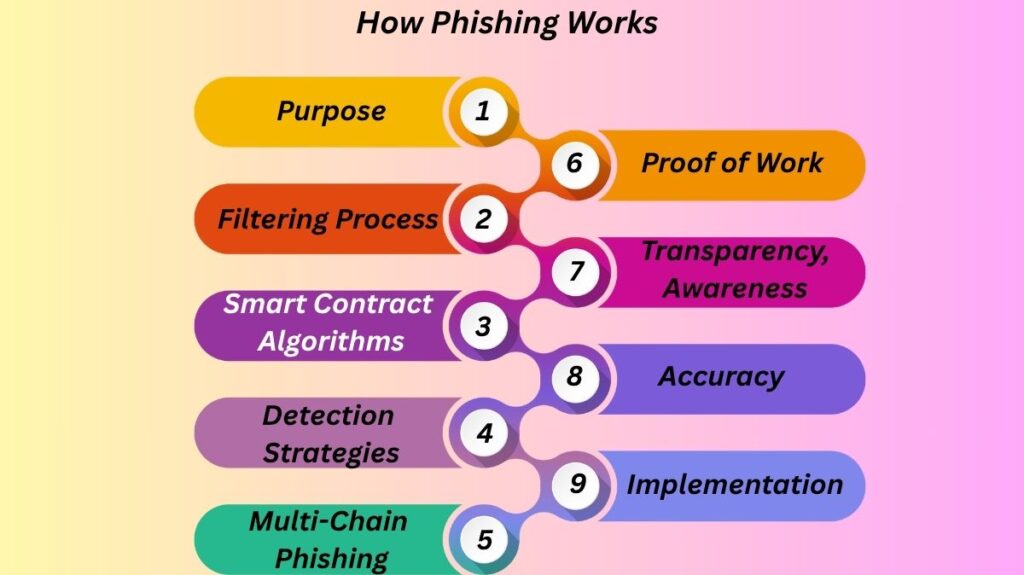
Purpose: In order to guarantee that only authentic documents are kept on cloud storage, Phish Block seeks to distinguish between safe and malicious homographic URLs within documents.
Filtering Process: Users no longer need to double-check for security because it serves as a utility between cloud users and storage during insertions and updates.
Smart Contract Algorithms: To find documents with phishing content, the system uses smart contract methods, specifically a homographic phishing URL detector.
Detection Strategies: It centers on three essential methods for detecting homographic URLs:
- Internationalized Domain Name in Applications (IDNA): Using multilingual characters, Internationalized Domain Name in Applications (IDNA) looks for homographs.
- Typosquatting: Detects misleading domain name spellings in order to detect homographs.
- Reserved Character Usage (RCU): Searches URLs that can be used for redirects for reserved characters (such as “;,” “,” and “@”).
Multi-Chain Phishing: Moreover, the system uses web crawling to locate linkages in identified documents, then recursively verifies these hyperlinks for homographs, allowing multi-chain phishing detection.
Proof of Work (PoW): Among cloud users, an enhanced proof-of-work algorithm chooses a miner to add identified harmful documents as blockchain blocks.
Transparency and Awareness: As soon as a phishing document is added to a block, all cloud users may see its contents, raising awareness of common phishing techniques.
Accuracy: The suggested Phish Block system has shown that it can detect homographic phishing URLs on a produced dataset with an accuracy of about 91%. This high level of accuracy guarantees cloud storage security.
Implementation: Metamask, Rinkeby (test network), Remix (IDE), Truffle, and Go Ethereum are among of the tools used to create the system on a private Ethereum Ethereum blockchain. Secure documents are delivered to cloud storage after being encrypted using the SHA-3 technique.
Even though Phish Block has potential, it currently has drawbacks, like block time overhead brought on by Ethereum’s default difficulty level, which might be reduced on a private blockchain that is self-configured. Its resilience to different forms of phishing content is the goal of future research.
