Nakamoto Consensus
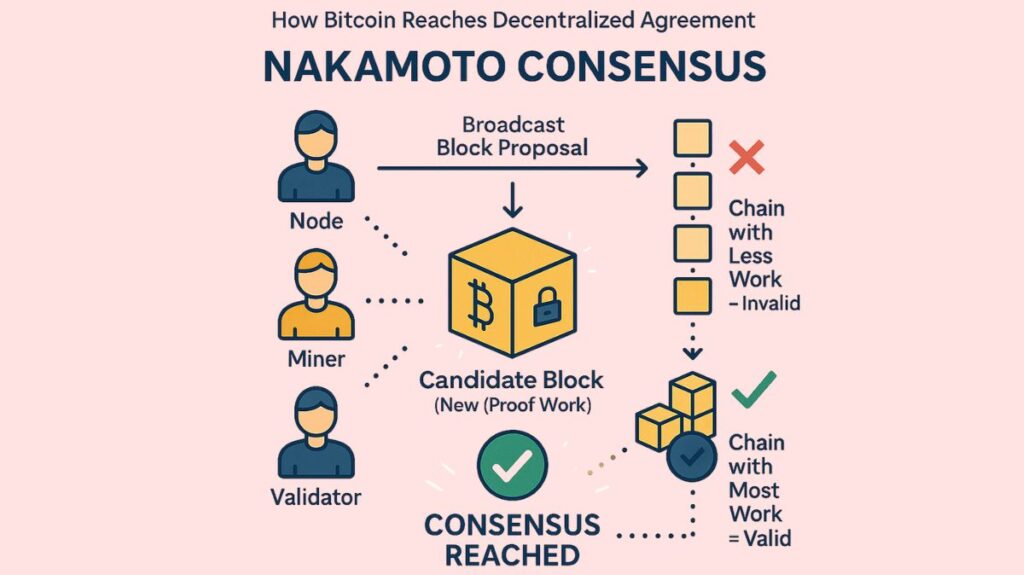
Blockchain networks, like Bitcoin, use the Nakamoto Consensus process to obtain consensus on the blockchain’s state without a central authority. The mystery Bitcoin creator, Satoshi Nakamoto, utilized it in 2009. This clever algorithm acts as “the glue that holds the Bitcoin blockchain together” to allow users to reach a decentralized, trustless blockchain consensus.
Key Components of Nakamoto Consensus
The integrity and security of the Nakamoto Consensus are maintained by a number of interrelated components:
Proof of Work (PoW): Mining requires solving complex mathematical riddles to add new blocks to the network. The next block is added and the first miner to solve it is rewarded. Although the problem is challenging to solve, other nodes may easily check its solution. The “proof” that work has been done is the computing effort that has been expended. It’s important to know that Proof of effort is a system or mechanism that generates proofs of computing effort using cryptographic functions. Although it is part of Nakamoto Consensus, which is a more comprehensive protocol, the two are not the same.
Block Difficulty: These mining problems’ difficulty automatically modifies itself to guarantee that new blocks are added consistently, usually every ten minutes for Bitcoin. Maintaining the desired block generation rate becomes increasingly challenging as more miners join and improve computational power (hash rate).
Block Rewards and Incentives: Bitcoins and transaction fees are paid to miners for blocks. These incentives motivate miners to secure the network by processing. Dishonesty costs resources and reduces incentives.
Decentralization: Global nodes and miners power the Nakamoto Consensus, not a central authority. The blockchain is secure, resilient, and censorship-resistant since it is decentralized.
Longest Chain Rule: The Nakamoto Consensus states that the longest valid chain the one with the most cumulative computing labour or number of blocks is deemed to be the correct one in the event of rival blockchain splits. This rule prevents attacks like double-spending by encouraging miners to operate on the same chain and making it very difficult for an attacker to establish a longer fake chain.
How Nakamoto Consensus Works
The steps involved in keeping a safe and reliable blockchain are as follows:
Transaction Broadcast: Every node in the network is informed when a user starts a transaction.
Transaction Broadcast: Nodes verify the transaction’s authenticity by checking the sender’s balance and network restrictions. Transactions that are deemed invalid are refused.
Inclusion in a Block: Miners arrange verified transactions into blocks. The Proof of Work problem for that block is then started by miners.
Solving the Proof of Work: The core of the Nakamoto Consensus is this. PoW pits miners against one another to solve a challenging mathematical puzzle that demands a lot of processing power. The network is informed of the solution by the first miner to solve the issue, and subsequent miners promptly confirm the outcome. Although this procedure requires a lot of resources, it guarantees that malevolent actors will find it difficult to control the network.
Block Addition: The solution is broadcast to the network by the first miner to solve the challenge. If the solution is confirmed by other nodes, the new block is appended to the blockchain. Miners begin working on the next block after this one becomes the most recent entry.
Chain Continuity: Lastly, the longest valid chain is the right one, according to the Nakamoto Consensus. This implies that the network will accept the chain with the highest total processing power, even if two miners solve the PoW simultaneously. By guarding against forks and attacks like double spending, this system guarantees continuity.
Nakamoto Consensus and Byzantine Fault Tolerance (BFT)
Because it solves the Byzantine Generals Problem, Nakamoto Consensus is regarded as a Byzantine Fault Tolerant (BFT) consensus process. The goal of this well-known computer science problem is to reach a consensus in a distributed network with potentially hostile, erratic, or defective nodes.
The longest chain rule and Proof of Work are combined in the Nakamoto Consensus to accomplish BFT. The decentralization of the system, which allows any member to become a node in the network, contributes to its robustness. Since attempts to manufacture invalid blocks would be expensive and swiftly rejected by the honest majority using the longest chain rule, economic incentives deter malevolent activity. For large networks like Bitcoin, this makes it nearly hard for bad actors to manipulate the network without owning more than 50% of the network’s processing power (a 51% attack).
The probabilistic finality of the Nakamoto Consensus is one of its main features. This means that adding blocks to a transaction increases its irreversibility. Before declaring a transaction irrevocable, Bitcoiners should wait six blocks (approximately an hour).
Nakamoto Consensus Benefits and Challenges
Benefits
Trustless Environment: Participants can trade without trusting a central authority or each other with blockchain technology. So, the protocol assures transaction legitimacy. By eliminating banks and governments from transaction verification, it allows direct peer-to-peer contacts. Streamlining multi-party and administrative processes decreases counterparty risk and boosts productivity.
Security: A double-spending or data manipulation attack cannot harm the network. Because of Proof of Work (in many popular blockchains), difficulty adjustment, and decentralization. This immutable chain is formed by cryptographically hashing and linking transactions. Changes to past transactions would involve recalculating all blocks, rendering them impossible. The ledger is immune to attacks, censorship, and shutdowns since transaction data is dispersed over thousands of nodes worldwide.
Transparency: All blockchain transactions are public and verifiable, increasing trust. Even when identities are pseudonymous (linked to wallet addresses), value movement and transaction history are auditable. In supply chains, financial records, and public finances management, transparency makes transaction audits and verification easy, reducing fraud and promoting accountability. An immutable record of a transaction builds faith in the data’s integrity.
Financial Inclusion: Any internet user can participate, expanding financial access. This permits “banking the unbanked” billions worldwide who cannot access traditional financial services owing to lack of identification, geography, or expensive fees. Blockchain allows smartphone-based global economic participation. International money transfers are cheaper and faster with its lower transaction fees and speeds. People can borrow, lend, and insure without bank accounts or credit checks via decentralized finance (DeFi).
Challenges and Criticisms
Energy Consumption: Bitcoin uses PoW consensus methods, which need plenty of computer power. Its enormous carbon footprint, especially when powered by non-renewable sources, boosts energy costs and environmental issues. Mine complex problems and add blocks with ASICs use lots of electricity. PoW’s long-term sustainability is questioned by this massive energy need, encouraging research in energy-efficient consensus methods like PoS.
Scalability: Due to block size and time intervals, Bitcoin and other basic blockchains execute 3–7 transactions per second. During high demand, users fight for block space, causing network congestion and higher transaction costs. Decentralization, security, and scalability are commonly described as the “Blockchain Trilemma” improving one often compromises another. Layer-2 scaling or sharding often works.
Centralization Risk: Although decentralized, a few mining pools could centralize processing. Competitive dynamics have formed massive “mining pools” where PoW miners share computer resources. A “51% attack” (albeit expensive and risky) could be possible if a few strong pools reached 51% of the network’s hash rate. Using centralized infrastructure layers like major exchanges and a small group of powerful engineers to design core protocols can also lead to centralization.
Forks: Network upgrades and community disagreements can cause complex and unpredictable blockchain forks. These are “soft forks” (backward-compatible) or “hard forks”. Community disagreements usually produce hard forks, which can permanently split developers, miners, and users. Forks confuse users and investors about which chain to support and increase market volatility and confusion.
Real-World Applications and Evolution
Although the foundation of Bitcoin is Nakamoto Consensus, many other blockchain projects have embraced and modified its ideas. For example, Ethereum Classic (ETC) is a safe smart contract blockchain that still uses Nakamoto Consensus with its ETCHash cryptographic algorithm. This approach is also used by other blockchains, such as Bitcoin Cash and Litecoin.
The foundation for the larger blockchain and cryptocurrency ecosystem has been established by Nakamoto Consensus. By facilitating safe, decentralized, and trustless operations in domains including supply chain management, voting and governance systems, intellectual property protection, and Decentralized Finance (DeFi), its uses go beyond straightforward cryptocurrency transactions.
But the world of blockchain is changing quickly. Nakamoto Consensus (PoW) is the “gold standard for decentralized security” for Bitcoin, however Proof of Stake and Delegated Proof-of-Stake are becoming more popular because to their lower energy usage and possibly faster transaction processing. Ethereum 2.0/Serenity controversially switched to PoS. Engineers constantly struggle to balance consensus approaches’ scalability, security, and efficiency.
