How does IAM work?
Giving people safe access to an organization’s resources is divided into two parts: access management and identity management.
Identity management
Identity management compares a login attempt to a database that keeps track of all the people who should be able to access it. The scope of the organization changes, people join or depart, and their jobs and projects change, thus this information needs to be updated continuously.
Employee names, job titles, managers, direct reports, email addresses, and mobile phone numbers may be in an identity management database. Users’ usernames and passwords are authenticated against their database identities during authentication.
Multifactor authentication (MFA) is required by many companies for further security. MFA, sometimes referred to as two-factor authentication (2FA) or two-way verification, is more secure than only utilizing a login and password. The login procedure now includes an additional stage where the user must use a different verification method to confirm their identity. These methods of authentication may involve personal email addresses and cell phone numbers. The user has a certain amount of time to enter the one-time code that the IAM system typically delivers to the alternate verification method into the login portal.
Access management
IAM’s second component is access management. The resources that the person or object trying to access are tracked by access management once the IAM system has confirmed that the person or thing matches their identification. The majority of organizations provide different degrees of access to data and resources, and these levels are based on project, tenure, job title, and security clearance.
Authorization is the process of appropriately granting access once a user’s identity has been verified. IAM solutions are designed to ensure that authorization and authentication occur safely and accurately at each access attempt.
Advantages of identity and access management
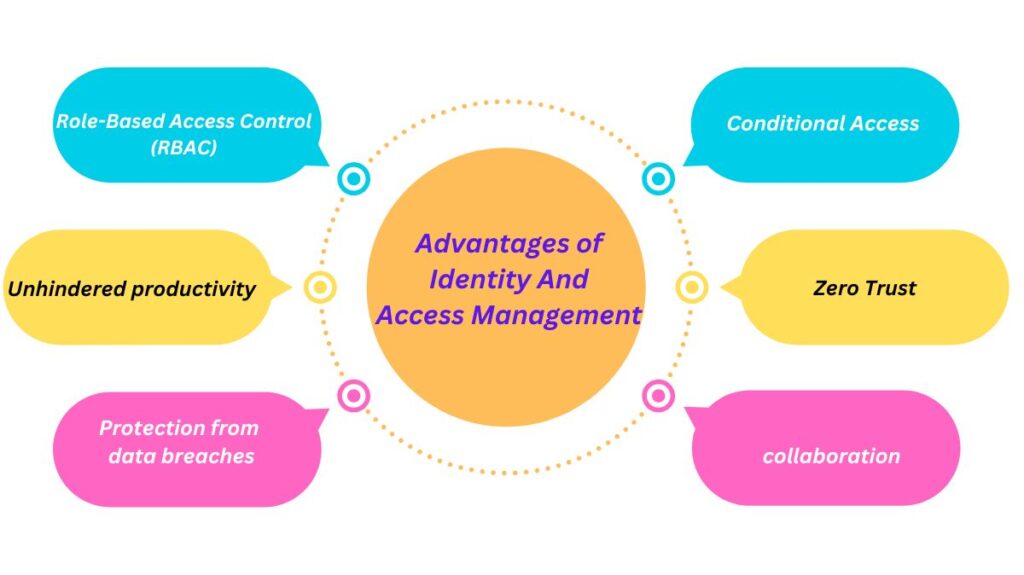
The correct IAM system offers a company several advantages.
For the right people, the correct access
IAM systems enable the design and enforcement of centralized rules and access privileges, allowing users to access resources without accessing sensitive data. RBAC is role-based access control. A scalable method of limiting access to those who require it to carry out their duties is RBAC. A fixed set of permissions or unique settings can be used to assign roles.
Productivity without hindrance
Security is crucial, but so are user experience and productivity. Implementing a complex security system to prevent breaches may seem alluring, but it is a tedious user experience to have several logins and passwords, among other productivity hurdles. Employees can be granted safe access to a variety of channels, including on-premises resources, cloud data, and third-party apps, without requiring constant logins, thanks to IAM solutions like single sign-on (SSO) and unified user profiles.
Protection against data breaches
Even though no security system is perfect, the danger of data breaches is greatly decreased when IAM technology is used. MFA, passwordless authentication, and SSO are examples of IAM solutions that allow users to authenticate themselves using more than just a username and password, which can be shared, forgotten, or compromised. Increasing user login options with an IAM solution lowers that risk by strengthening the login process with an extra layer of protection that makes it more difficult for hackers or others to share or hack.
Data Encryption
The fact that many IAM systems provide encryption features is one of the reasons IAM is so successful at enhancing an organization’s security. Sensitive data is protected throughout transmission to and from the company thanks to features like Conditional Access, which let IT managers specify access criteria based on device, location, or real-time risk information. Since the data can only be decrypted under verified circumstances, it is safe even in the case of a breach.
Less IT manual labor
IAM solutions can save IT organizations time and effort by automating operations like assisting users with password resets, account unlocking, and access log monitoring to spot irregularities. As a result, the IT department may concentrate on other crucial duties, such as enforcing a Zero Trust policy across the entire company. IAM is crucial to Zero Trust, a security strategy based on the ideas of assuming breach, employing least privileged access, and explicitly confirming.
Enhanced cooperation and effectiveness
Keeping up with the speed of modern work requires seamless collaboration between suppliers, contractors, vendors, and employees. This collaboration is made possible by IAM, which ensures that it is quick, simple, and secure. To save time during onboarding, IT administrators can also create role-based automated workflows that expedite the authorization procedures for new hires and job transfers.
IAM services and solutions
Manually completing many essential IAM workflows, such as user authentication and activity tracking, is challenging or impossible. Rather, businesses use technological solutions to automate IAM procedures.
Organizations used to employ point solutions to manage various aspects of IAM, such as one solution for user authentication, another for access policy enforcement, and a third for user activity auditing.
These days, IAM solutions are frequently all-inclusive platforms that combine several products into one cohesive whole or perform everything. Although IAM systems vary widely, they all generally have some basic characteristics in common, such as:
- Centralized directories or connections to third-party directory services, such as Google Workspace and Microsoft Active Directory.
- Automated processes for establishing, modifying, and deleting online personas.
- The organization can manage identity and access for all apps and assets, including older apps, through a single, authoritative directory by establishing a network-wide, product-agnostic identity fabric.
- MFA, SSO, and adaptive authentication are examples of built-in authentication choices.
- Features for access control that let businesses create detailed access rules and apply them to all users, including those with privileged accounts.
- Tracking features to keep an eye on users, identify questionable behavior, and guarantee adherence.
- The capabilities of customer identity and access management (CIAM) extend identity lifecycle management, authentication, and authorization procedures to digital portals for partners, customers, and other external users.
- Certain IAM solutions are designed for particular ecosystems. The IAM platforms of Google Cloud and Amazon Web Services (AWS), for instance, manage access to resources housed in their respective clouds.
Other IAM solutions, such as those made by IBM, Oracle, Microsoft, and others, are designed to function with all corporate network resources, regardless of their hosting location. By exchanging user authentication data between apps using open standards like SAML and OpenID Connect (OIDC), these IAM systems can serve as identity providers for a wide range of services.
Cloud Identity And Access Management
Identity and access management solutions are going off-premises and employing SaaS. These cloud-based “authentication-as-a-service” (AaaS) or “identity-as-a-service” (IDaaS) IAM solutions offer functionality that on-premises systems may not.
When distributed users access resources on-site and in private and public clouds via a variety of platforms (Windows, Mac, Linux, and mobile), IDaaS technologies can be helpful in complex corporate networks. While IDaaS frequently can, on-premises IAM technologies might not be able to easily support so many diverse users and resources across regions.
Additionally, IDaaS can assist businesses in extending IAM services to non-employee roles such as contractors and clients. Because the business doesn’t have to employ separate systems for various users, this can make IAM deployments simpler.
Some of the most time- and resource-intensive parts of IAM, such as establishing new user accounts, verifying access requests, and identity governance, can also be outsourced by businesses using IDaaS technologies.
