This blog post explains symmetric cryptography, including its types, features, advantages of symmetric cryptography, and relevance to blockchain, as illustrated below.
What is symmetric cryptography?
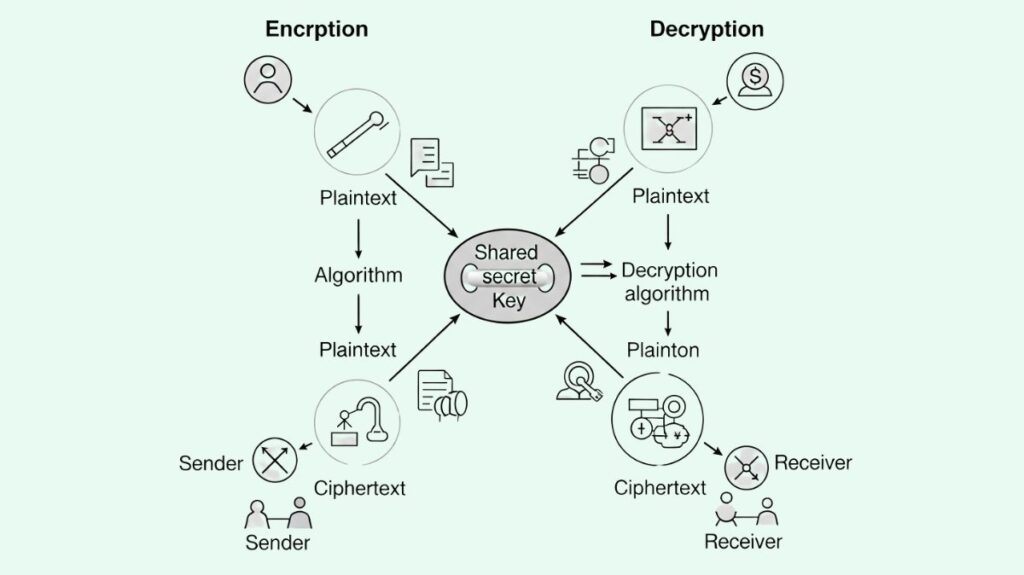
Secret key cryptography, another name for symmetric cryptography, is a technique in which the encryption and decryption keys are shared by both parties. Because of its efficiency and speed in comparison to asymmetric cryptography, it is most appropriate for bulk encryption. Data is encrypted and decrypted using the same key in symmetric cryptography, also known as shared key or secret key cryptography.
Also Read About What Are The Challenges Of Decentralisation & It’s Methods?
Symmetric cryptography features
The following summarises its salient features and applicability:
Core Principle
- A single, shared secret key and an encryption method are used by the sender to convert plaintext to ciphertext.
- The recipient decrypts the ciphertext using the same secret key and procedure to get plaintext.
- The key, encryption, and decryption can be simple or complex.
Contrasting Asymmetric Cryptography
- Asymmetric cryptography, often known as public key cryptography, uses mathematically related public and private keys.
- Despite being faster to compute, symmetric cryptography’s fundamental issue is secure key distribution. Before communicating, both parties must agree on and safely exchange the secret key. This is difficult in decentralized networks with anonymous users.
Services Provided
- Symmetric cryptography restricts information access to authorized parties to guarantee confidentiality.
- Along with hash functions, it can aid integrity and authentication.Message integrity and data origin authentication are provided by Message Authentication Codes (MACs), which employ a shared key with a hash function.
Key Management
- The shared key needs to remain confidential. The communication loses its security if the key is compromised.
- Random key generation, Key Derivation Functions (KDFs) like Scrypt (used in Ethereum wallets to encrypt private keys), or key exchange protocols like Diffie-Hellman can all be used to generate keys.
- In order to improve security and thwart attacks like replay attacks, cryptographic protocols also frequently employ arbitrary numbers known as nonces or initialization vectors (IVs) that are only usable once.
Advantages of symmetric cryptography
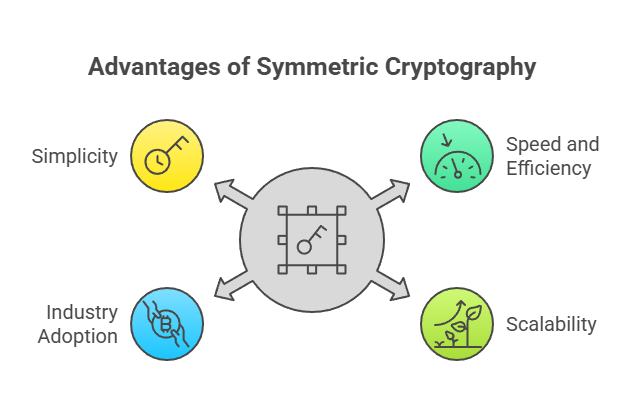
- Quickness and Effectiveness: Blockchain networks with huge data sets benefit from symmetric algorithms’ speed and resource efficiency.
- Blockchain transaction scalability and speed require symmetric encryption algorithms with superior memory management and performance metrics than asymmetric ones.
- Symmetric algorithms are fast and efficient for massive database encryption or blockchain transaction storage.
- Asymmetric encryption is harder to construct and manage than symmetric encryption, which uses a single key.
Scalability: As the number of users and encrypted data increases, symmetric algorithms can grow effectively because to their comparatively minimal processing overhead. - Industry Adoption: Because of their speed and security, symmetric encryption algorithms like AES have established themselves as industry standards for data encryption and are frequently used in blockchain applications.
Also Read About Role Of Cryptography In Blockchain Explained For Beginners
Types of Symmetric Ciphers
- Stream ciphers: These encrypt data one bit (or byte) at a time, usually by combining the plain text and a key stream via an XOR operation.
- Block ciphers: Divide the plaintext into blocks of a predetermined size, then encrypt each block using a different method. AES, Triple DES, and DES are examples.
- Block ciphers can use Counter (CTR), Cipher Block Chaining (CBC), or Electronic Code Book (ECB), which is unsafe.
Pertinence to Blockchain
- A key component of secure systems, such as blockchain technology, is symmetric cryptography.
- Symmetric cryptography is still in use even though asymmetric cryptography is essential to identity and digital signatures in decentralized blockchains (resolving the key distribution issue for verification and authentication without a trusted third party):
- for employing techniques such as AES in CTR mode (e.g., AES-128-CTR in Ethereum wallets) to encrypt private keys in wallets.
- for protecting communication between nodes (e.g., AES CTR for Ethereum P2P communication).
- It is frequently used in conjunction with asymmetric approaches or inside frameworks that oversee safe key exchange (e.g., private transactions in Quorum use symmetric keys transferred via ECDH) in some privacy solutions or specialized protocols for data encryption.
- Symmetric keys are managed by protocols such as Whisper, which is Ethereum’s messaging protocol, to enable peer-to-peer secure communication.
- Sometimes asymmetric cryptography is used to safely exchange a symmetric key first, and subsequently the majority of the data is encrypted using the faster symmetric method.
Also Read About What Are The Blockchain Transaction Steps And Types?
Summary
In summary, symmetric cryptography is still essential for protecting data and communication channels within the system, especially when performance is crucial or parties have already established a secure connection, even though asymmetric cryptography supports blockchain’s decentralised trust model for identity and signatures.
