In this article, we will discuss what asymmetric cryptography is, how it works, examples and, Asymmetric Cryptography Algorithms
Asymmetric Cryptography
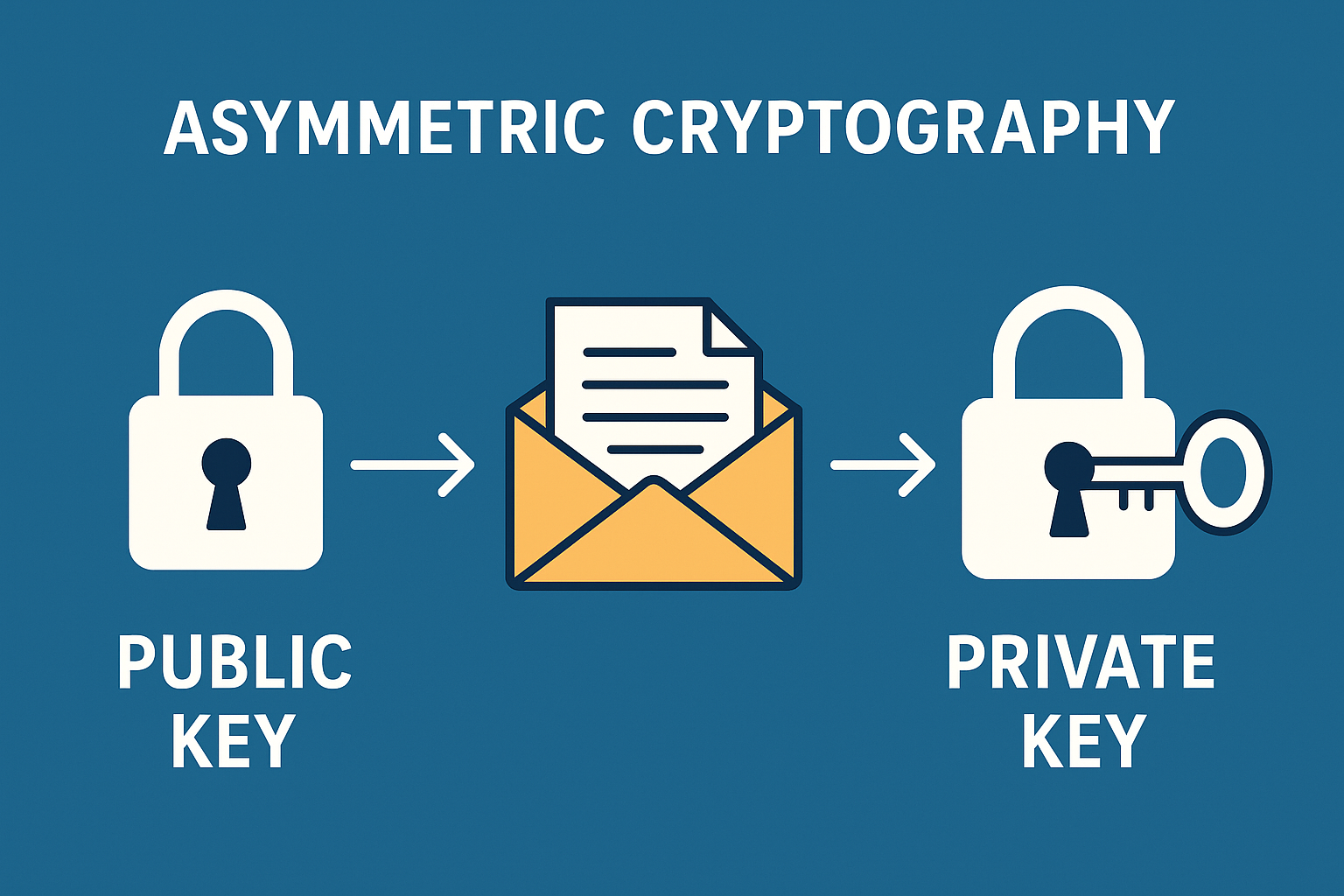
Public key cryptography (asymmetric cryptography) powers blockchain. Symmetric cryptography uses one secret key for encryption and decoding, while asymmetric uses two mathematically linked keys, public and private.
Public-key asymmetric cryptography uses public and private keys. Share public keys, but hide secret keys. Digital signatures and secure communication are two uses for this system.
How it works:
Key Generation:
Cryptographic procedures generate public and private keys, which are mathematically connected.
Public Key Distribution:
Anyone can use the public key to securely connect with the private key owner.
Encryption
Senders encrypt with recipients’ public keys before sending.
Decryption:
Just the recipient with the private key can decrypt the message.
Digital Signatures:
Digital signatures, which confirm a message’s integrity and authenticity, can also be made with the private key.
You can also read The Blocks, Chaining, And Hashes Of Blockchain Architecture
Benefits of Asymmetric Cryptography
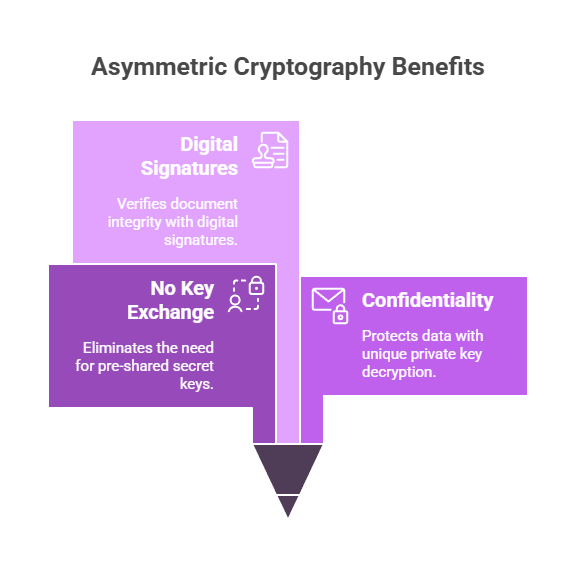
No Key Exchange Needed:
It is perfect for secure communication over public networks because the sender and recipient do not need to exchange a secret key beforehand.
Secure Communication:
Confidentiality is ensured because only the matching private key can decrypt data encrypted with the public key.
Digital Signatures:
Digital signatures can be created and verified using asymmetric cryptography, guaranteeing the integrity and validity of digital documents.
Here’s a detailed breakdown:
Key Pair Structure and Relationship:
- Asymmetric cryptography uses a pair of keys: a private key and a public key.
- The owner of the private key is required to keep it a secret number.
- Through mathematical procedures, the private key is converted into the public key. Determining the private key from the public key is computationally impossible, despite their mathematical similarity.
- The public key is made to be freely and publicly exchanged without jeopardising the system’s or the private key’s security.
Core Functions of Asymmetric Cryptography:
- Only the user’s private key can decrypt public key-encrypted data. Anyone can send a private message knowing only the recipient can read it.
- Digital Signatures: By utilising their private key, a user can “sign” a communication or transaction. Anyone with the corresponding public key can verify this signature. Digital signatures guarantee message validity and non-repudiation.
Mathematical Foundations:
- The mathematical difficulties that underpin asymmetric algorithms are simple to compute in one way but very challenging to reverse.
Some examples are as follows:
- Algorithms like RSA (Rivest–Shamir–Adelman) use integer factorization to solve problems like factoring the product of two huge prime numbers.
- Discrete logarithm: Algorithms such as DSA (Digital Signature Algorithm) and ECC (Elliptic Curve Cryptography) exploit problems based on modular arithmetic, where determining the exponent is computationally impracticable given the base and the result.
You can also read What Are The Characteristics Of Blockchain And Core Concepts
Asymmetric Cryptography Algorithms
Public-key cryptography encrypts and decrypts with public and private keys. Asymmetric encryption methods like RSA, Diffie-Hellman, and ECC are popular. A more thorough examination of the many forms of asymmetric cryptography is provided below:
RSA (Rivest-Shamir-Adleman):
- Relying on the mathematical challenge of factoring huge numbers, RSA is one of the most popular asymmetric algorithms.
- Digital signatures, encryption, and decryption are among its applications.
- Strength: RSA’s strength lies in how hard it is to identify a huge composite number’s prime factors.
Elliptic Curve Cryptography (ECC):
- Using the mathematical characteristics of elliptic curves, ECC is another well-liked asymmetric technique.
- ECC is utilised in digital signatures, encryption, and key agreement.
- Strength: For some applications, ECC is more effective than RSA because it provides robust security with shorter keys.
Diffie-Hellman
- Mostly used for key exchange, Diffie-Hellman enables two parties to create a shared secret key via an unprotected channel.
- Instead of directly encrypting or decrypting data, it makes it possible to establish a safe key, which symmetric encryption algorithms employ.
- In TLS/SSL and other protocols, Diffie-Hellman is frequently used to provide secure communication channels.
Digital Signature Standard (DSS):
- Asymmetric algorithms like the Digital Signature Algorithm (DSA) are the foundation of the DSS, a standard for digital signatures.
- The primary purpose of DSS is to confirm the integrity and validity of digital documents and communications.
- Strength: DSS is a commonly used standard for digital signatures that guarantees the accuracy of documents and transactions conducted online.
Other Asymmetric Algorithms:
ElGamal:
Another Diffie-Hellman-like method for digital signatures and key exchange.
Paillier cryptosystem:
A version of RSA specifically built for partial-information cryptography protocols.
Various password-authenticated key agreement techniques:
To establish a safe key, these methods mix symmetric and asymmetric cryptography.
Relevance to Blockchain’s Defining Characteristics:
- Identity: Asymmetric cryptography offers a safe method of using public keys to generate distinct digital identities (account addresses) for users in a decentralised system. For example, in Ethereum, an address is formed from the public key’s Keccak hash, which is taken from the private key. With this self-managed identification, identity verification does not require a central authority.
- Transaction Security and Integrity: Digital signatures, which are generated with the sender’s private key and validated with their public key, guarantee that transactions are genuine and unaltered. This makes it possible to exchange values securely and without middlemen.
- Establishing trust between unknown participants in a Decentralization network requires the use of asymmetric cryptography. The required proof of ownership and authorisation is provided by the cryptographic signatures themselves, negating the requirement for a reliable third party to validate transactions.
In conclusion, asymmetric cryptography is a fundamental component that makes possible blockchain’s decentralised structure, security, and participant confidence, especially when it comes to the use of public and private key pairs for digital signatures and identity. Without depending on a central authority, it enables people to safely own and manage their assets and take part in the network.
You can also read Understanding Distributed Ledger Technology (DTL) Overview
