This article gives an overview of the Benefits Of Hardware Wallet, disadvantages, how it works and examples.
A hardware wallet is an actual technological gadget made to safely keep your private keys for cryptocurrencies offline. It works similarly to a secure USB device for your digital assets, including cryptocurrencies like Bitcoin. The reason this storage technique is sometimes called “cold storage” is that the private keys are kept off the internet.
What is a Hardware Wallet for?
Cryptocurrency private keys are mainly stored safely in hardware wallets to guard against online dangers including malware, phishing scams, and hackers. Cryptocurrency keys are thought to be among the safest ways to store them. They have additional purposes, such maintaining several accounts on different blockchains and offline transaction signing, but they can also serve as cold wallets for storing digital assets that never communicate with smart contracts. Large sums of wealth are especially well-suited for long-term storage.
How Hardware Wallets Work
Hardware wallets work on the basis of storing your private keys in a safe, offline location.
Key Generation and Storage: A hardware wallet creates and saves your private keys within the device when you set it up. Without ever contacting a computer or phone with an internet connection, this process takes place fully inside the device. Like those on credit cards and passports, the private key is frequently kept on a tamper-resistant chip.
Offline Private Key Security: The device never loses the private keys. This is essential for safeguarding blockchain assets because losing money can result from a private key compromise.
Transaction Process:
- The hardware wallet is connected to a computer or smartphone via Bluetooth or a USB connection in order to send cryptocurrency.
- A companion piece of software or an app on your linked device is used to initiate the transaction data (the recipient’s address and the amount).
- The private key is used to “sign” the transaction offline after the transaction data are transferred to the hardware wallet. The device itself is where this signing takes place.
- A crucial layer of two-factor authentication (2FA) is provided by the requirement that you physically verify the transaction on the device’s screen using its buttons or touchscreen.
- After the transaction is signed, the companion app broadcasts it to the blockchain network after receiving it from the hardware wallet.
- Because the private key is never made public online throughout this procedure, it is protected from phishing, malware, and keyloggers.
These tasks are safely carried out by a hardware wallet using its computer chip and a special operating system made for private keys. An internet-connected device serves as the hardware wallet’s interface, broadcasting the transaction that has already been signed.
Benefits of Hardware Wallet
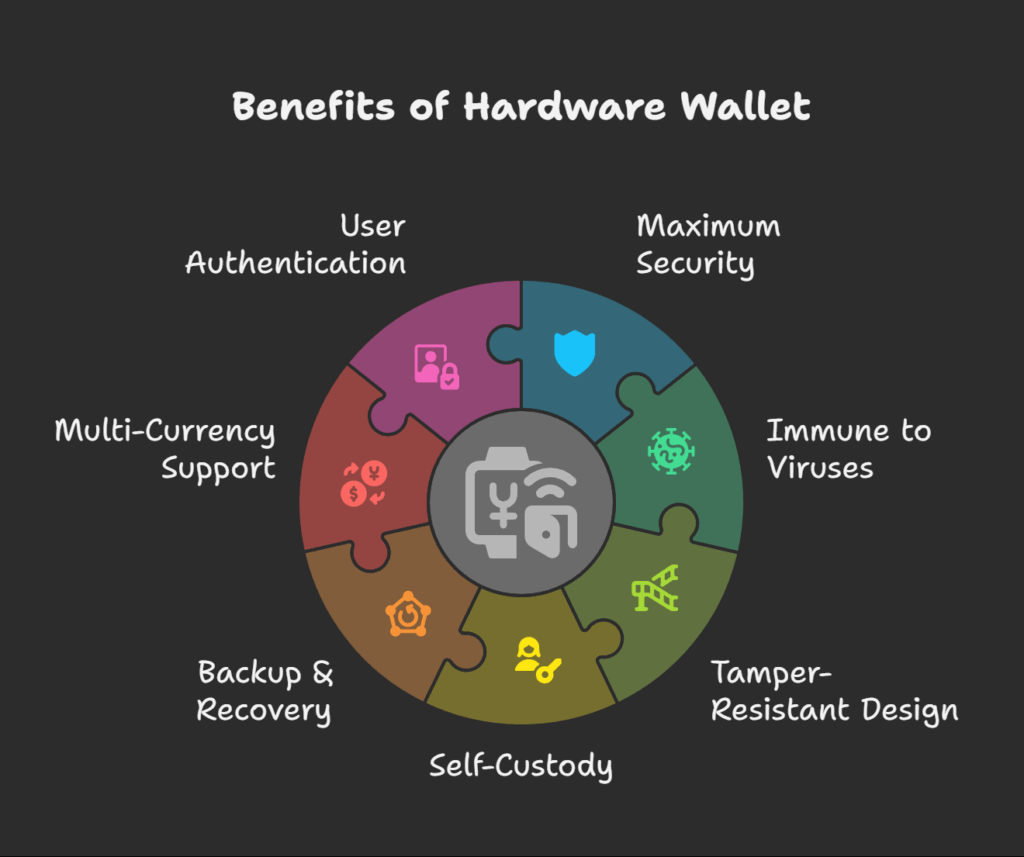
Maximum Security: Due to their offline storage in a tamper-resistant device, private keys are impervious to the majority of typical online threats. The private key is secure even if malware is present on your computer.
Immune to Viruses: They are protected from online viruses and hacks since they are offline.
Tamper-Resistant Design: Hardware wallets are designed to withstand tampering. Some will delete themselves after multiple unsuccessful attempts, and many are secured by a PIN.
Self-Custody (Non-Custodial): The idea that “not your keys, not your crypto” is embodied by hardware wallets, which provide you total control over your private keys.
Backup & Recovery: A recovery seed phrase, sometimes referred to as a secret recovery phrase, mnemonic phrase, or key phrase, is included with hardware wallets and can be used to recover your money in the event that the device is lost, stolen, or damaged. For all of the private keys the device manages, this phrase serves as a master key.
Multi-Currency Support: The majority of hardware wallets support a wide range of cryptocurrencies, enabling users to manage several assets from a single device.
User Authentication: User authentication is necessary for transactions, and this can be done through a passcode or physical device confirmation.
Hardware Wallet Disadvantages
Cost: Hardware wallets are not free; they usually cost between $50 and $200.
Less Convenient: Because a physical device is required to authorise each transaction, they are less practical than mobile or online (hot) wallets for everyday or fast, on-the-fly transactions.
Complexity for Beginners: New users may find the initial setup and recovery seed management daunting.
Recovery Phrase Security: Your recovery phrase needs to be secure. Your money could be lost if it is stolen or compromized since anyone who finds it will have access to all of the accounts that your hardware wallet protects.
Malicious Smart Contracts: Malicious smart contract signature is not prevented by hardware wallets. Before signing, it’s critical to comprehend what you’re getting into. A feature called “Clear Signing” allows some systems, such as Ledger, to provide transaction data in a way that is readable by humans.
User Error: Hardware wallets are not impervious to human error. Double-checking transaction details on the device’s screen and using test transfers to confirm receiving addresses are examples of best practices.
Examples of Hardware Wallets
A few well-known brands are:
- Ledger: Examples of these models are the Ledger Nano S/X, Ledger Nano S Plus, Ledger Nano X, Ledger Flex, and Ledger Stax. A Secure Element chip and a proprietary operating system are used by ledger devices to improve security.
- Trezor: models such as the Trezor One and Model T.
- SafePal: The SafePal S1 model is well-liked.
- BitBox.
- KeepKey.
- CoolWallet.
Always get a hardware wallet from a reliable manufacturer rather than a “used” one because secondhand devices may harbour malware.
