Understand the key Disadvantages of Proof of Work as a blockchain consensus mechanism, including its resource-intensive nature, limited scalability, and susceptibility to 51% attacks.
What is PoW Proof of Work
In order to confirm transactions and add new blocks to the blockchain, miners must solve challenging mathematical puzzles as part of the Proof of Work (PoW) consensus mechanism, which secures networks. This procedure guards against fraud and guarantees that the blockchain’s ledger is unchangeable. Coins like Bitcoin and, more traditionally, Ethereum use Proof of Work (PoW), a fundamental consensus mechanism in blockchain technology. It functions as a protocol for upholding system consensus and confirming transactions on a decentralised network.
Here is a thorough breakdown of proof of work:
Purpose and Function of PoW
- Verification and Consensus: PoW makes ensuring that every node in a network is in agreement on the ledger’s current state and the proper sequence of transactions. In a setting where trust is lacking, it produces a single, accepted version of reality.
- Preventing Double-Spending: PoW is essential for stopping the “double-spend” problem, which occurs when an attacker tries to spend the same digital assets twice.
- Security and Immutability: By making it computationally expensive to change previous blocks, the method secures and impenetrable blockchain. A block’s hash is affected when its data changes, rendering subsequent blocks invalid and exposing tampering.
- Incentivizing Participants: Transaction fees and new cryptocurrency (block rewards) are given to miners, who carry out the “work,” when they successfully add a block to the chain. This reward promotes involvement and protects the network.
- Sybil Attack Resistance: Sybil attacks, in which one entity poses as several entities in an effort to take control of the network, are less likely to occur when PoW is used. It prevents writers from writing on the ledger until they have completed a computationally challenging task.
How Proof of Work Works
Block Creation: A “block” is created by grouping transactions together. A unique reference number, creation time, and a link (hash) to the block before it are among the metadata included in every block.
The Cryptographic Puzzle: A “miner” (a node that may write to the chain) must figure out a computationally challenging challenge before adding a new block.
- The goal of this puzzle is to locate a “nonce” a “number only used once.” A random 32-bit string serves as the nonce (in the case of Bitcoin).
- The miner continually applies various nonce values to the block’s data, including the hash of the previous block, and then hashes the result using a cryptographic hash algorithm like SHA-256.
- The objective is to generate an output hash, or “hash digest,” that satisfies a predetermined “difficulty target” (for example, beginning with a specified number of leading zeros). Although it takes a lot of effort and time to get this solution, others can easily verify it.
Broadcasting and Verification: The freshly formed block is broadcast to the network by the miner as soon as they discover a valid hash. The proof-of-work and the authenticity of the block are confirmed by other nodes.
Longest Chain Rule (Consensus): In the event that several miners discover legitimate blocks at the same time, the network can momentarily split. The network eventually accepts the longest chain, which is the one with the highest cumulative “work” or block height, guaranteeing a single ledger version. The version that is thought to have had the most work done will be the one that nodes switch to.
Difficulty Adjustment: The puzzle’s difficulty automatically changes on a regular basis (e.g., every 2,016 blocks for Bitcoin) to keep the block publishing rate constant (e.g., roughly once every ten minutes for Bitcoin). This modification takes into account the total number of miners and their hashing power.
Proof of Work Advantages
- Robust Security: PoW has demonstrated “astonishingly successful” defences against collusion assaults in public blockchain networks, such as the Sybil attack. The sheer amount of processing power needed serves as a strong enough disincentive to ensure network security.
- Decentralization: With open membership and a genuinely decentralized system, it eliminates the need for a central authority and establishes confidence through computational proof.
Disadvantages of Proof of Work
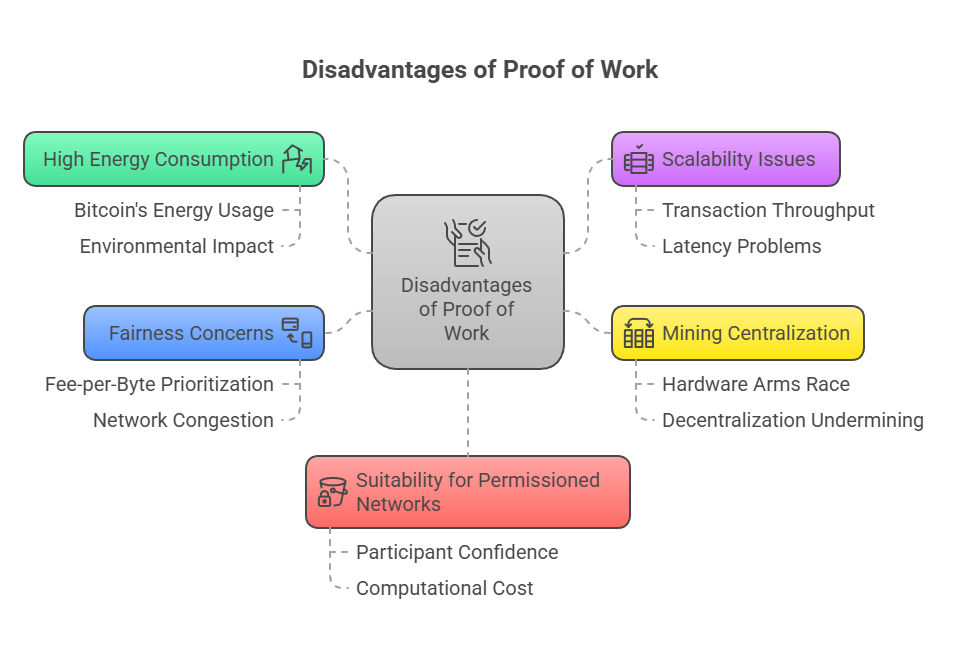
- High Energy Consumption: The enormous amount of computational power and electricity used is a big worry. The Bitcoin blockchain, for example, has been observed to consume more electricity than whole nations.
- Scalability Issues: Compared to other consensus mechanisms, PoW-based systems, such as Bitcoin, are slower because to their limited transaction throughput (around 7-8 transactions per second) and latency problems.
- Mining Centralization: It is arguable that the “hardware arms race” to create potent ASICs (Application-Specific Integrated Circuits) has increased the resource requirements of PoW and moved power to massive mining farms or pools, undermining the fundamental decentralization tenet.
- Fairness Concerns: Concerns regarding fairness may arise when miners choose transactions differently from fee-per-byte prioritization, particularly when there is network congestion.
- Suitability for Permissioned Networks: Due to the increased degree of participant confidence in permissioned blockchains, which enables quicker and less computationally costly consensus processes, PoW is typically neither required nor appropriate for these networks.
Alternatives
Because of its shortcomings, Proof of Stake (PoS) is one of the many alternatives to PoW that have been put out and put into practice. Since validators “stake” cryptocurrency rather than using processing power, PoS uses a lot less energy. Various Byzantine Fault Tolerance (BFT) algorithms, Proof of Authority (PoA), and Proof of Elapsed Time (PoET) are further mechanisms.
