This blog post discusses Denial of Service (DoS) attacks, including their definition, methodology, symptoms, issue’s, campaigns, and an explanation of DoS attack vs DDoS.
Denial of Service (DoS) attack
A Denial of Service (DoS) attack is a type of cyberattack in which the attacker’s goal is to prevent the intended users from accessing a computer or network resource. This is accomplished by interfering with a targeted system’s regular functions, usually by sending it malicious requests or overloading it with traffic.
(Or)
DoS attacks block authorized users from accessing a computer, network resource, or service. Denial-of-service attacks prohibit users from accessing an organization’s network to disrupt operations.
Also Read About Avoid Social Engineering Attacks Blockchain: Best Practices
How DoS Attacks Work
DoS attacks flood the targeted machine with requests, information, or traffic, prohibiting valid requests. This heavy traffic drains the system’s memory, processing power, and bandwidth, making it unable to reply to valid requests. Slow performance, website outages, or resource inaccessibility may affect legitimate users. To stop any real customers from logging in, an attacker may make 10 bogus requests each second, for instance, if a bank website can handle 10 logins per second.
DoS attacks generally fall into two categories based on their primary method of attack:
- Attacks known as buffer overflows take use of flaws in a system’s memory buffer to use up all of the available memory, hard drive space, or CPU time. This causes a denial of service by causing slow behavior, system crashes, or other harmful server actions.
- Attacks known as floods occur when a targeted server is overloaded with packets, surpassing its capability. The hostile actor usually requires more available bandwidth than the victim for a flood attack to be successful.
Common DoS Attack methods
DoS attacks, which frequently target servers, network routers, or communication lines, take use of a variety of flaws in computer network systems. They may slow down links or cause systems to crash. Among the methods are:
SYN flood
This method takes use of the TCP handshake procedure. A deluge of TCP/SYN packets with faked sender addresses are sent by the attacker. The server allots resources for every “half-open” connection, but since the faked address never responds, these connections use up all of the server’s resources, blocking valid requests.
Sending a lot of ICMP (ping) requests in an attempt to overload the target is known as an ICMP flood.
Ping of Death
The Ping of Death attack creates and sends unique network signals, particularly ICMP packets with irregular sizes, which disrupt systems that receive them. This attack might easily bring down unprotected Internet servers in the early days of the Web. It is highly advised that you attempt all of the actions listed on virtual machines instead of in your actual workspace.
Smurf attack
- Spoofs the victim’s IP address as the source and uses misconfigured network devices to distribute packets to every host on a network via the broadcast address. As a result, the victim receives an overwhelming volume of responses.
- As previously stated, buffer overflow attacks use software flaws to cause a system to crash by exceeding its memory buffer.
- ARP spoofing is a type of network attack in which a malicious MAC address is linked to a valid IP address in order to reroute traffic.
The purpose of application-layer attacks (Layer 7) is to cause a website or application to crash or become unusable by targeting particular features or capabilities, such as web servers. Because they imitate genuine requests, they are more difficult to detect and use fewer resources than network-layer attacks. Among the examples are:
- The HTTP slow POST attack keeps connections open and uses up server resources by sending the entire HTTP POST header but leaking the message body byte by byte.
- URIs that demand intricate or time-consuming algorithms or database operations are the subject of the Challenge Collapsar (CC) attack, which repeatedly sends regular HTTP requests to a web server, depleting resources.
Also Read About HTTP REST API Blockchain: A Comprehensive Beginners Guide
Are You Dead Yet? (RUDY)
RUDY attacks starve the web server’s available sessions in order to target web applications. Like Slowloris, RUDY uses an arbitrary big content-length header value and never-ending POST messages to stop sessions.
Slow Read Attack
Keeps connections open to deplete the server’s connection pool by requesting valid application-layer answers and reading them very slowly.
DDoS (distributed denial of service) methods: Several DoS tactics can be strengthened when used as DDoS attacks:
- Attackers use impersonating the victim’s IP address as the source when they send fraudulent requests to a large number of machines, known as reflectors. The victim is then inundated with responses. Typical amplification vectors are SSDP, NTP, and DNS.
- Botnets are groups of compromised systems used to launch attacks, such as Internet of Things devices infected with Mirai virus.
- Permanent Denial of Service (PDoS): Also referred to as “phlashing,” this attack uses flaws in hardware management interfaces to corrupt firmware, causing enough harm to a system that it necessitates replacing or reinstalling hardware.
- Protocol attacks: By using excessive server resources in firewalls and load balancers through “state exhaustion,” these attacks seek to render a target unavailable.
- Volumetric attacks: These use botnets or amplification techniques to bombard the victim with enormous volumes of traffic in an attempt to use up all available network bandwidth.
Also Read About Blockchain Trust Layer: How Decentralization Create Security
A DoS Attack’s Symptoms
It might be difficult to identify a DoS attack because its symptoms may be confused with other network problems or high volumes of legal traffic. Nonetheless, important indicators include of:
- Unusually poor network performance, including lengthy file or webpage load times.
- The inability to visit any website or the unavailability of a certain website.
- Unknown volumes or abrupt increases in network traffic, possibly caused by a wide variety of IP addresses.
- Higher CPU utilization on the system in question.
- Abrupt disconnections from devices connected to the same network.
DoS Attacks Issues
DoS attacks have the potential to cause serious issues:
- Downtime: Users are unable to access websites and online services.
- Financial losses: Downtime and lost business can cause organizations to lose money.
- Damage to reputation: An organization’s reputation and client trust may be harmed by attacks.
- Interruptions in network traffic and services that are ineffective or unavailable.
- Cloud cost inflation: Autoscaling under attack can lead to cost explosions for cloud-native apps.
DoS in Adversary Campaigns
DoS attacks are rarely isolated in contemporary cyber operations; instead, they are frequently included into multi-phase campaigns:
- Distraction and diversion: DoS attacks hide data exfiltration, privilege escalation, and lateral movement. The attackers use the disturbance to achieve their goals, while the defenders restore service.
- DoS can act as a precursor or follow-up to ransomware by isolating responders or interfering with backups. In order to do more harm or use leverage in extortion attempts, it can also come after data exfiltration.
- Economic disruption: More and more, modern DoS attacks target cloud service restrictions, API endpoints, or WAF configurations, giving operational and economic disruption precedence above mere bandwidth saturation.
- Erroneous Denial of Service DoS attacks can also happen accidentally as a result of a sudden, massive spike in genuine popularity, which frequently happens when a well-known website connects to a poorly prepared website. The “Slashdot effect” or “Reddit hug of death” are terms used to describe this. Similar to this, websites may lag or collapse as a result of excessive traffic when well-known people or significant events spark a lot of interest online (e.g., Michael Jackson’s death in 2009).
Legality
Denial-of-service attacks are prohibited in a lot of places. For example, under the Computer Fraud and Abuse Act, they may be deemed a criminal offence in the US, punishable by jail time and compensation. Under the Police and Justice Act of 2006, DoS attacks were expressly prohibited in the UK, with a potential sentence of ten years in prison.
DoS Attack Vs DDoS
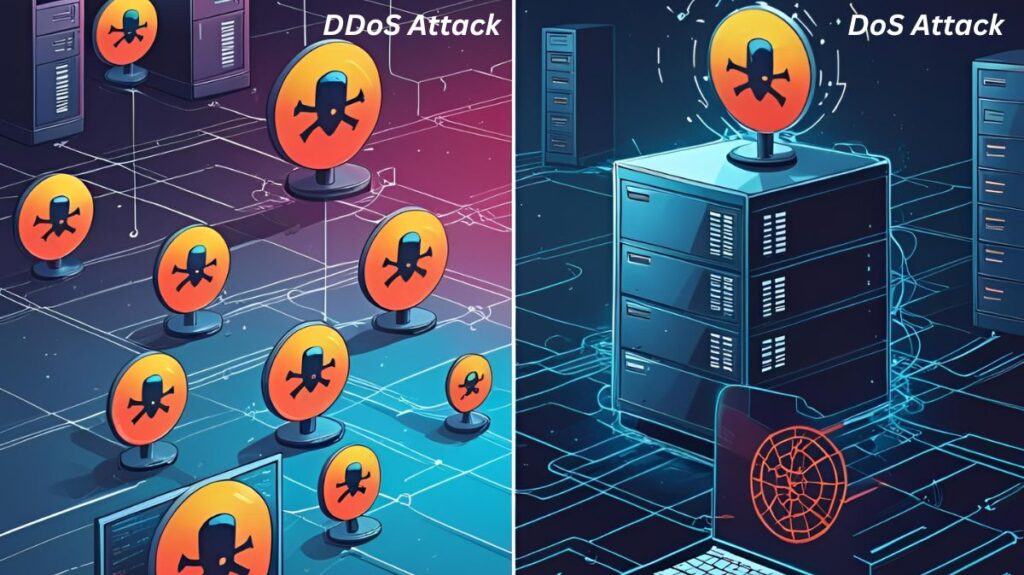
The more complex Distributed Denial of Service (DDoS) attack uses a ‘botnet’ of hacked systems to initiate the attack from several places, whereas a DoS attack starts from one computer or IP address. Dispersed DDoS attacks are harder to identify and block since the bad traffic comes from several sources. Similar to a mob of individuals jamming a shopfront door, a DDoS attack hinders legitimate consumers from entering and disrupts business.
Also Read About Sybil Attack Detection In Blockchain & Sybil Attack History
| Feature | Denial of Service (DoS) Attack | Distributed Denial of Service (DDoS) Attack |
| Source of Attack | Single attacker system or source | Multiple compromised systems (a “botnet”) working together |
| Complexity | Relatively simpler to execute | More complex due to coordination of multiple sources and devices |
| Traffic Volume | Lower volume of malicious traffic | Significantly higher volume of malicious traffic |
| Speed | Generally slower | Typically much faster and more impactful |
| Detection | Easier to detect as traffic originates from one IP address | More challenging to detect due to traffic coming from many diverse IPs |
| Mitigation | Easier to block, often by simply blocking the single source IP | Much more difficult to mitigate due to the distributed nature of the attack |
| Tracing | Easier to trace back to the attacker’s source | Very difficult to trace due to the distributed and often spoofed sources |
| Tools Used | Often uses simple scripts or a single attack tool | Relies on botnets (networks of infected “zombie” devices) controlled by a Command & Control (C&C) server |
| Impact | Can disrupt service, but often temporary and less severe | Can cause prolonged downtime, significant financial loss, and reputational damage |
