Finney Attacks
Finney attacks are double-spending attacks in blockchain networks, notably those using Proof Of Work(PoW) consensus mechanisms like Bitcoin. Hal Finney, a Bitcoin developer and first receiver, theorized the attack. This attack takes advantage of a lag between a transaction’s broadcast and block inclusion. The attacker broadcasts a previously mined, concealed block in an attempt to invalidate a legal transaction made to a merchant.
How Finney Attack Works
The attack consists of a malicious miner’s well planned series of actions:
Preparation
The attacker, who needs to be a miner, usually builds up a mining pool and purchases a sizable quantity of cryptocurrency.
Mining and Private Transaction
To begin, the attacker initiates a transaction that transfers funds from one wallet (Wallet A, for example) to another wallet (Wallet B, for example). The attacker mines a fresh block that contains this self-to-self transaction in private rather than broadcasting it to the network. The rest of the network is not aware of this private mining operation.
Also Read About Types Of Blockchain Wallets: Hot, Cold, Hardware And More
Fraudulent Purchase
The attacker then purchases something from a merchant using the identical monies that were taken out of Wallet A. Importantly, the attacker depends on the merchant accepting the payment as legitimate without awaiting blockchain confirmation (i.e., accepting an unconfirmed or zero-confirmation transaction), even though this second transaction is meant for the merchant (Wallet C, for example).
Block Release
The attacker broadcasts their already mined block containing the self-to-self transaction to the network after the merchant delivers the goods or services, assuming they have been paid.
Profit and Invalidation
The network invalidates the merchant’s transaction when it accepts the pre-mined block since the coins were “spent” in the attacker’s private transaction. The attacker keeps both the coins and the stuff they bought.
Also Read About How Oracle Manipulation Attacks Works: Understanding Threat
Conditions for Success and Difficulty
Finney attacks are difficult to carry out and require certain circumstances:
- Mining Capability: Before another miner verifies the merchant’s transaction, the attacker must be a miner with enough mining power to produce their block.
- Merchant Acceptance of Unconfirmed Transactions: The victim, who is the merchant, is required to accept transactions that have zero or no confirmation. Transaction speed is given precedence over security in this way.
- Timing and Patience: Until the merchant approves the fraudulent transaction, the attacker’s pre-mined block must not be published. Given the network difficulty and amount of miners, waiting for a block might take a long time, thus the attacker must be very patient and use careful timing. The attacker also needs a few minutes to complete the merchant’s transaction.
- Network Conditions: If another miner on the network finds and transmits a block that contains the merchant’s transaction before the attacker broadcasts their pre-mined block, the attack will fail.
The attack’s success is mostly dependent on the miner’s hashing power; the lower the hashrate, the less likely it is to succeed, however it is theoretically feasible to use less than 51% of the network’s hash power.
Impact on the Victim
Usually a merchant, the victim thinks they have received a legitimate and final payment. The victim’s transaction is reversed, though, and they lose the money they initially thought they received along with any goods or services they supplied, after the attacker publishes their covertly mined block.
Unconfirmed bitcoin transactions and internet businesses that allow quick downloads (like video games) are especially vulnerable.
Also Read About Types Of Phishing Attacks & How To Prevent Phishing Attacks
Protection and Mitigation Strategies
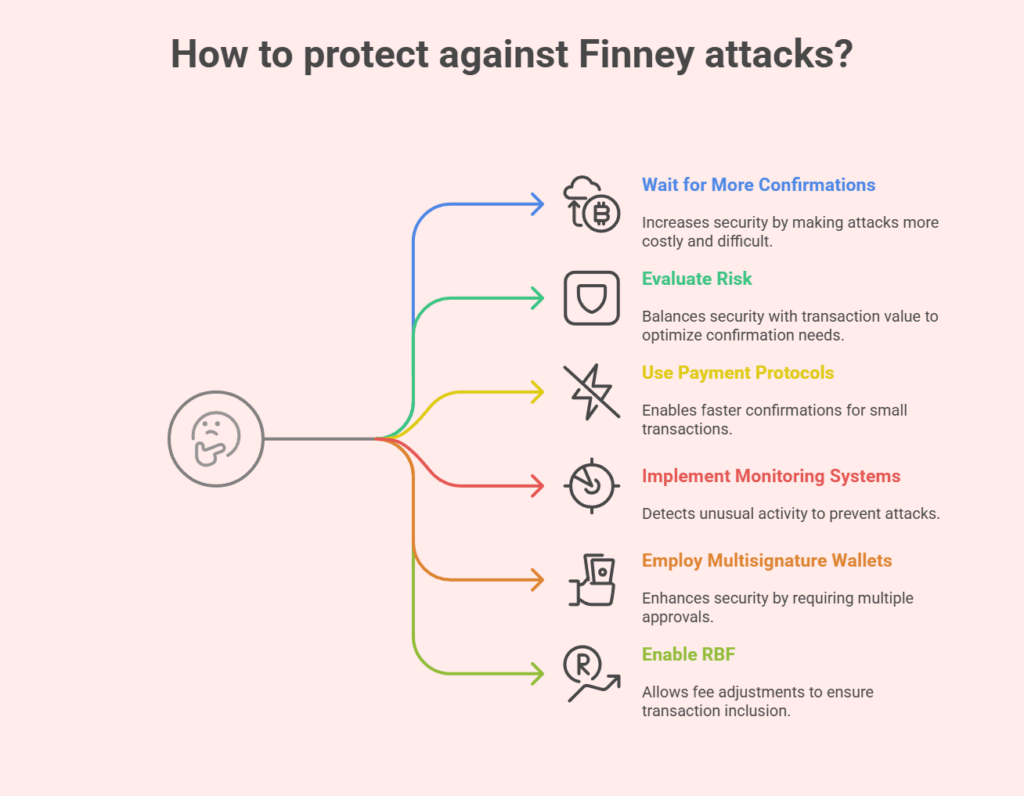
Several tactics can be used to defend against Finney attacks:
Wait for More Confirmations
The best course of action is to hold off on deeming a transaction final and irreversible until a greater number of block confirmations have been received. It is customary to wait for a minimum of six confirmations for Bitcoin. Higher-value transactions require more confirmations, even though decentralization has progressed to the point that one or two confirmations are plenty for small sums. For an attacker, waiting for further confirmations raises the cost and difficulty.
Evaluation of Risk
Evaluate the risk in light of the transaction value. One confirmation might be enough for small-value transactions (less than €/£/$100, for example), since the expense of carrying out the attack would probably be greater than the possible benefit. A longer confirmation period is recommended for high-value transactions.
Payment Protocols
Faster confirmations via off-chain payment protocols like Bitcoin’s Lightning Network mitigate Finney attacks for smaller, faster transactions.
Monitoring and Alert Systems
Real-time monitoring and alert systems can detect unusual blockchain activity and thwart attacks.
Multisignature Wallets
Using multisignature wallets requires multiple secret keys to approve transactions. This can increase security by making Finney attacks harder.
Transaction Replace-by-Fee (RBF)
If your blockchain supports it, enable RBF for your transactions. In order to reduce the likelihood that an unconfirmed transaction will be included in a block, RBF enables you to substitute a new transaction with a larger fee.
Practicality in Modern Blockchain Networks
Despite being the first recorded attack on Bitcoin, Finney attacks are typically seen as less frequent, less useful, and less lucrative than other kinds of blockchain attacks, such 51% attacks. The window of opportunity for Finney attacks has shrunk as blockchain networks and security measures have developed, making them exceedingly challenging and unlikely to execute in practice today.
