Proof of Elapsed Time in Blockchain
By lowering computational expenses and energy consumption, Proof of Elapsed Time Blockchain(PoET), a blockchain consensus method, seeks to offer a more cost-effective substitute for Proof of Work (PoW). Its purpose is to equitably choose the person who will suggest the blockchain’s next block.
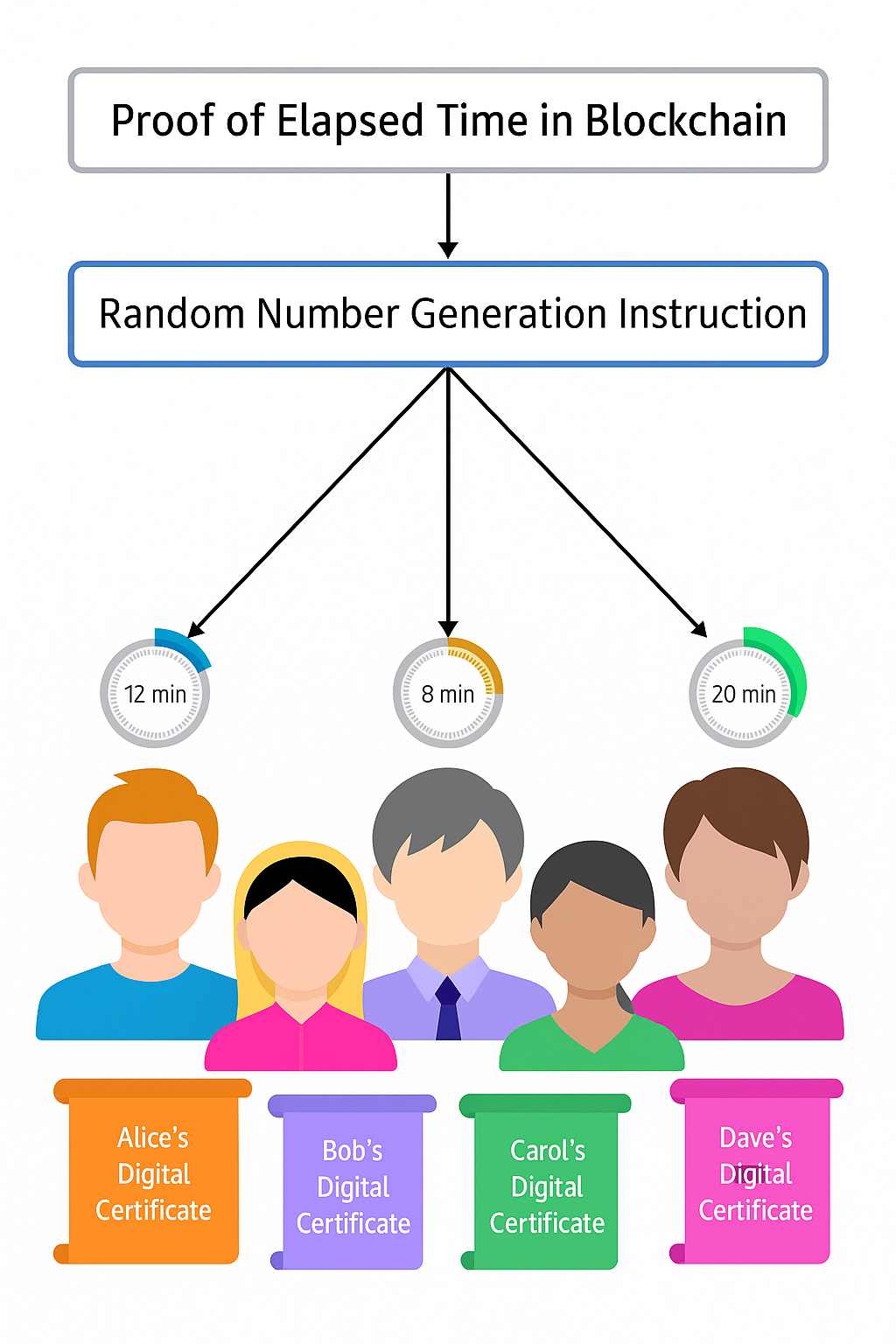
How PoET Works
Participating nodes are given a randomized waiting time, which is the fundamental idea behind PoET. The next block can then be created and published to the blockchain network by the node whose timer expires first.
Several crucial steps and elements are involved in the process:
Random Wait Time Generation: Every publishing node asks its computer system’s secure hardware time source for a wait time. A random wait time is created by this secure hardware time source and sent back to the node’s software.
Idling and Publishing: After that, the publishing nodes sit inactive for the remainder of the random time allotted to them. A node creates and publishes a block after its idle state is over. The entire procedure restarts for the following block when any other publishing nodes that are still waiting stop their timers.
Verification of Fairness: Maintaining process integrity requires verifying that a random time was used and that the publishing node waited the appropriate period. PoET running in ARM’s TrustZone, AMD’s Platform Security Processor, or Intel’s Software Guard Extensions (SGX) fits these requirements.
Signed Certificates: Programs from outside sources cannot change the software that runs in a TEE. The publishing node asks the TEE for a signed certificate after waiting the allotted amount of time, verifying that it did, in fact, wait the time that was chosen at random. After that, the block and this certificate are both published.
By ensuring that each trusted node has an equal chance of being chosen to mine a block and get the reward, this approach seeks to do away with the necessity for computationally demanding mining procedures that are included in PoW. In order to stop nodes from routinely winning the election, the algorithm additionally incorporates extra checks.
Applications of Proof of Elapsed Time Blockchain
The different applications of PoET are as follows:
- Internet of Things: For Internet of Things applications where devices have limited energy and processing power, PoET may be useful. Its energy-efficient consensus process fits very nicely with IoT device limitations.
- Blockchain Technology for Digital Identity: Without the high energy costs of PoW, PoET can be employed in digital identification systems to guarantee safe and equitable consensus among entities in charge of digital IDs.
- Digitization and Tokenization: Because of its fairness and scalability, PoET may be used to manage digital currencies and tokenized assets in networks that have access to reliable hardware.
- Industries Under Regulation: PoET is helpful in regulated businesses where operational transparency and energy usage compliance are crucial. In these situations, its fair method and low energy requirements are beneficial.
- Workplace Settings: PoET works well in business settings where using reliable hardware is possible and efficiency and equity are crucial. PoET’s equitable consensus process and low energy consumption are advantageous to businesses.
Proof of Elapsed Time Blockchain architecture
The general architecture of PoET is as follows:
- Safe Hardware: In order to create and enforce random wait periods, PoET depends on the deployment of reliable hardware, such as Intel’s Software Guard Extensions (SGX), which offers a secure execution environment. Because of this hardware, wait times are created securely and are not susceptible to manipulation or prediction.
- Components of PoET Software: The PoET method is implemented by the software component that controls node-to-node communication and consensus-building.
- Nodes: In a PoET-based network, nodes are in charge of proposing blocks, creating random wait periods, and validating transactions as part of the consensus process.
- Layer of Communication: This makes it easier for nodes to communicate with one another in order to broadcast transaction details and block suggestions.
- Network Layer: The fundamental network infrastructure that facilitates the communication needed for the PoET consensus process and links every node.
- Security Layer: The PoET process’s integrity and security are guaranteed by the security layer, which also validates suggested blocks and generates and measures wait times securely.
Important Proof of Elapsed Time Blockchain Features
The following are PoET’s salient features:
- Minimal Power Use: PoET reduces energy consumption by eschewing intricate computations. Instead of solving computational challenges, waiting times are used to reach a consensus.
- Managing Large Transaction Volumes: Because of its architecture, PoET can effectively manage a high volume of participants and transactions, which makes it appropriate for scalable blockchain networks.
- Effective Use of Resources: Because PoET requires less computing power than PoW-based systems, it can handle a larger transaction throughput.
- Equal Chance for Nodes: Because the selection process in PoET is based on randomly chosen waiting times, each node has an equal chance of being chosen to submit a block.
- Selection at Random: All nodes are given an equal chance to create blocks with the usage of random wait times.
- Low Costs of Infrastructure: The overall infrastructure costs for operating a PoET-based blockchain network are decreased due to the decreased requirement for high-performance computer hardware.
Advantages of Proof of Elapsed Time Blockchain
- Reduced Computational Cost and Energy Consumption: Because PoET requires a lot less computing power than PoW, it uses less energy and has lower operating expenses. Compared to PoW, it uses 30 times less energy while mining on hard drives.
- Fairness in Leader Election: By guaranteeing that each miner or validator has an equal opportunity to produce their block, the randomized timing method fosters equitable network participation.
- Scalability: It has not been documented that PoET has scaling problems. With less resource usage, it enables a high number of validators.
Disadvantages and Limitations Proof of Elapsed Time Blockchain
- Hardware Dependency: Certain hardware capabilities are necessary for PoET, particularly the utilization of Trusted Execution Environments (TEEs) such as Intel SGX and a secure hardware time source. The model’s security is predicated on the hardware clock used to determine time not being hacked.
- Time Synchronization Challenges: The exact operation of a time-based consensus method can be made more difficult by the fact that true time synchrony is nearly unachievable in distributed systems due to speed-of-light delay constraints.
- Sybil Attacks: Sybil attacks, in which a hacker fabricates multiple false identities in order to influence the network, can affect PoET. Nevertheless, this issue can be lessened by adding more nodes in consortium networks, where identities are usually known.
- Stale Chip Problem: The “stale chip problem” is one restriction that Ittay Eyal brought to light.
- Production Readiness: Existing implementations, like Hyperledger Sawtooth, are not meant for production use and may make use of simulated TEE environments for testing.
Implementations and Variations
Permissioned blockchain networks are the main use for PoET.
- Hyperledger Sawtooth: Notably, PoET is one of the consensus algorithms used by Intel Corporation’s Hyperledger Sawtooth.
- PoET CFT: This variant can run on any CPU since it makes use of a simulated SGX environment, which eliminates the need for real hardware. It does not offer Byzantine Fault Tolerance (BFT), but it does offer Crash Fault Tolerance (CFT).
- PoET SGX: This is the hardware-dependent version, which uses very minimal CPU power and depends on SGX to provide Byzantine Fault Tolerance (BFT).
- Devmode: A development-only option that isn’t appropriate for production but is good for testing installations with a single validator. It uses a straightforward approach for choosing a leader at random.
Despite being categorized as a Proof of Work algorithm, PoET is essentially different since it relies on a trusted computing model rather than brute-force processing power to satisfy PoW requirements.
