Proof of Space Time

Block validation in blockchain networks is based on a consensus process called Proof of Space Time (PoST), which combines time and storage capacity. Participants must assign and demonstrate the ongoing availability of a specific quantity of storage space over time. By confirming that users are regularly keeping their storage promises, this protocol protects the network. Because the true cost of storage is related to the product of storage capacity and usage time, its authors, Tal Moran and Ilan Orlov, called it “Rational Proofs of Space-Time.”
How Proof of Space Time Works
PoST combines two fundamental consensus processes:
- Proof of Space (PoSpace): This algorithm basically proves that a network participant can store network data by allowing them to dedicate a sizable quantity of memory or storage space to build new blocks and validate transactions. Unlike Proof of Work (PoW), which involves solving intricate mathematical problems, participants use their storage devices to generate “plots,” or data structures. The purpose of these plots is to show that the participant has set aside the necessary amount of storage space.
- In order to verify that a specific period has elapsed after the storage was allotted, Proof of Time (PoT) provides a verifiable delay function (VDF). The participant must demonstrate that they have kept the storage up to date for that amount of time using the VDF output as a challenge. This lessens the likelihood that bad actors would quickly devise schemes and try to manipulate the system. PoT prioritises a node’s performance and activity length to determine its reliability, and it chooses validators based on ranking scores and predetermined stakes.
You can also read Blockchain Validator: Organize, Validate Transactional Data
In practice, network users usually create a sizable dataset called a “plot” to show their storage commitment. Proofs in this plot are based on publicly available criteria known as “challenges,” which are updated frequently to keep the plot fresh. Participants must show that they have kept this plot for an epoch to add a new block to the blockchain. The network verifies if the proof, usually a segment of the plot, matches the current challenge and the participant’s previous proofs to ensure the participant doesn’t change their plots each epoch.
Following verification, the right to produce the next block and related awards is awarded to the first player to present the most exact proof. Miners can solve two hash puzzles: the WindowPoSt puzzle needs supplying blockchain data at predetermined intervals to ensure data is not erased, and the WinningPoSt puzzle requires a randomly chosen miner to promptly give a duplicate of stored network data.
Benefits of PoST
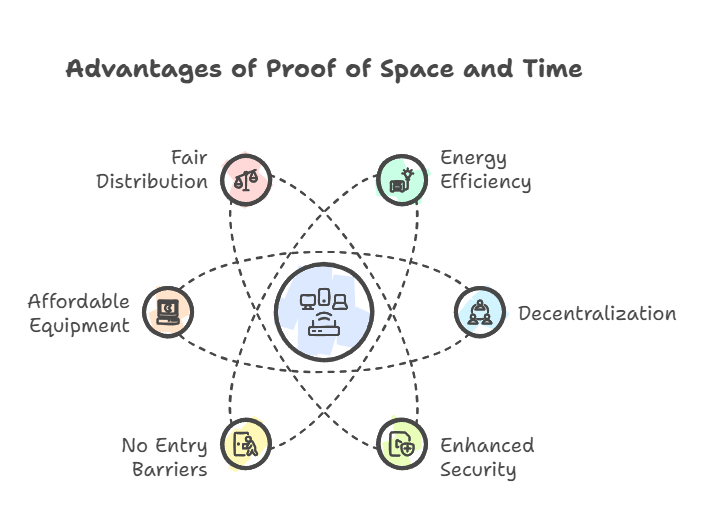
Benefits of Proof of Space Time
There are various benefits to the protocol:
- Energy Efficiency: Because PoST depends on time and storage space rather than a lot of processing power, it is far more energy-efficient than PoW.
- Decentralization: PoST may enable a larger group of users to join the network by using storage space as a resource, hence promoting further decentralization. Anyone with a computer can participate, guaranteeing stability and sustainability.
- Enhanced Security: Because security is predicated on the gradual commitment of storage resources, it is more impervious to computationally intensive attacks. It is too costly to interfere with reserved space and disrupt PoST operations.
- No Entry Barriers: The initiative is accessible to everyone with a hard drive and doesn’t require large financial outlays.
- Affordable Equipment: There is no need to regularly upgrade storage devices.
- Fair Distribution: PoST allows for the fair distribution of block rewards while still ensuring network security and consensus. It incentivises those who store network data diligently.
Shortcomings of PoST
PoST has significant disadvantages despite its advantages:
- Limited Number of Projects: Only a few blockchains have adopted this method.
- Malware Risks: Mining and timestamping may be interfered with if a computer becomes infected.
- Energy Consumption Concerns: Widespread adoption could potentially impact storage drive prices and might lead to the development of less resource-efficient models.
- Shortened SSD Lifespans: Some implementations, like Chia’s, have raised concerns over shortened lifespans of Solid State Drives (SSDs) due to the intensity of write activity involved in plot generation.
You can also read What Is ECDSA? Elliptic Curve Digital Signature Algorithm
Examples of Networks Using PoST
Prominent examples of blockchains that utilise the PoST consensus mechanism include:
- Chia Network: A well-known example of a blockchain using the PoST consensus mechanism. Chia’s spacetime model depends on “plotting” (generation of proof-of-space files) to the storage medium to solve a puzzle. However, Chia plots do not store any useful data.
- Filecoin: This blockchain is renowned for achieving consensus without the use of centralised solutions by utilising PoST methods. The PoST method of Filecoin demonstrates that a storage miner is still storing a distinct piece of information for the network.
Distinctions from Other Concepts
Proof of Space Time (PoST) vs. Proof of Stake (PoS):
Although both are consensus systems, PoS incentivises users to validate transactions by holding or “staking” a certain amount of cryptocurrency. A user’s influence increases with the number of coins they own. PoST, on the other hand, is made expressly to encourage users to keep data on the blockchain for a long time, paying them for their sustained storage dedication. Because PoST encourages careful data storage among all stakeholders, it is referred regarded be a more democratic method.
Proof of Space Time (PoST) vs. Proof of Capacity (PoC):
The consensus method used by PoST and PoC is similar in that players receive rewards for their efforts, and validators in PoC are required to use their hard drive space in order to check and confirm activities. However, when storage miners are chosen at random to confirm transactions, PoST specifically requires them to present convincing evidence of keeping data for a predetermined amount of time. PoST gives the idea of “capacity” the dimension of “time.”
Comparison to Proof of Work (PoW)
An energy-efficient substitute for Proof of Work (PoW) is PoST. PoST’s security is dependent on participants’ commitment of storage resources rather than processing capacity, whereas PoW necessitates a substantial amount of computing power to solve intricate problems. Unlike traditional models that require users to solve complex problems requiring computational resources in order to receive an incentive, PoST rewards miners for retaining data on their devices. As a result, networks can make use of a novel participatory paradigm that capitalises on the physical storage shortage.
You can also read What Is Proof Of History? & How Does Proof Of History Work?
