Role of cryptography in blockchain
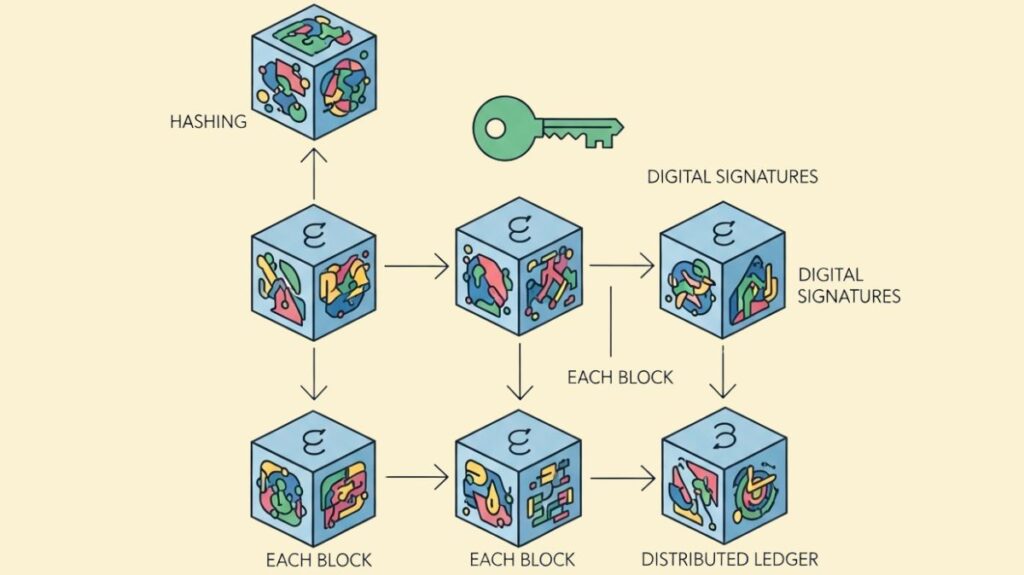
What is cryptography in blockchain?
The science of secure communication and information security in the face of adversaries is known as cryptography. To do this, it makes use of algorithms, sometimes referred to as ciphers. Cryptography is referred to as the backbone, a vital basis, and one of the pillars upon which the entire system is based in blockchain technology, rather than merely a component. In decentralised systems, it facilitates trust.
Also Read About The Blocks, Chaining, And Hashes Of Blockchain Architecture
Cryptography used in blockchain
Blockchain operations rely heavily on cryptography, which offers several vital services:
- Security: Protects the network and data. Cryptography protects blockchain technology and transactions, making them “cryptographically secure”.
- Data integrity and trust: Cryptography ensures and builds trust. It confirms that information hasn’t been changed while being transmitted.
- Privacy and Confidentiality: Although public blockchains are frequently transparent, privacy and confidentiality issues need the use of cryptography. There are methods for maintaining privacy while enabling public verification.
- Cryptography ensures that a message’s origin can be confirmed and that its sender cannot retract their actions. The term is authentication and non-repudiation.
- Identity and Digital Signatures: Cryptography is needed to sign communications and transactions and establish a participant’s digital identity, usually based on public/private key pairs.
Blockchain’s fundamental building blocks, or cryptographic primitives, are as follows:
Hash Functions:
- A hash function is a one-way mathematical operation that generates a fixed-size output known as a hash value, message digest, or simply digest from an input of any size (data).
- Because they are deterministic, the same input consistently yields the same result.
- The avalanche effect is the phenomenon whereby a slight alteration in the input will produce an entirely different output hash.
- Since they are irreversible, figuring out the original input from the hash output alone is computationally impossible.
Blockchain uses hash functions for a number of reasons, such as:
- Block linking: To make the chain tamper-evident, a cryptographic link is created by including the hash of the previous block in the header of the subsequent block.
- Data integrity can be confirmed by hashing and storing the hash, which allows for the detection of any further data modifications through re-hashing and comparison of the results.
- Making Merkle Trees: These tree topologies enable fast confirmation that a transaction is part of a block by effectively condensing all transactions in a block into a single hash (the Merkle root) via hashing.
- Mining: Miners work to solve a cryptographic problem in Proof-of-Work (PoW) systems by determining a hash value that satisfies a predetermined difficulty threshold.
- Address generation: In certain systems, such as Ethereum, the shorter account address is obtained by applying a hashing function to the public key.
- SHA-256, RIPEMD-160, Ethash, SCrypt, SHA-512, and Keccak-256 are examples of common hash algorithms that are discussed.
Also Read About What Are The Characteristics Of Blockchain And Core Concepts
Asymmetric cryptography, or public key cryptography:
- A public key and a private key are two mathematically related keys used in this technique.
- While the private key needs to be kept confidential, the public key can be freely disseminated.
- Only the recipient’s matching private key may decrypt a communication encrypted using their public key.
- On the other hand, anyone can use the matching public key to verify (decrypt) material that has been encrypted (signed) with a private key. The foundation of digital signatures is this.
- The key distribution issue that symmetric cryptography faces in a decentralized network is resolved by its asymmetric nature.
- In general, symmetric algorithms are faster than public key algorithms.
In blockchain, they are widely utilised for:
- Digital Signatures: To demonstrate ownership of assets or authorisation to carry out an operation, the sender signs a transaction using their private key. Nodes use the sender’s public key to validate this signature.
- Identity: A participant’s identity on the network is represented by their public key or derivatives (addresses).
- When necessary, key exchange/management is used to safely create shared keys for symmetric encryption.
- Wallet Security: Private keys are safely kept in wallets.
- ECC and RSA are crucial algorithms. ECDSA is Ethereum and Bitcoin’s standard.
Symmetric cryptography in blockchain:
- This technique encrypts and decrypts data using a single secret key.
- Compared to asymmetric cryptography, it is typically faster.
- Sharing the key securely between parties is a challenge.
- DES, 3DES, and AES are examples of algorithms.
- Utilised in blockchain applications for purposes such as wallet file encryption and possibly protecting peer-to-peer communication between recognised nodes. Symmetric keys can also be used to create Message Authentication Codes (MACs).
Advanced Cryptography in Blockchain
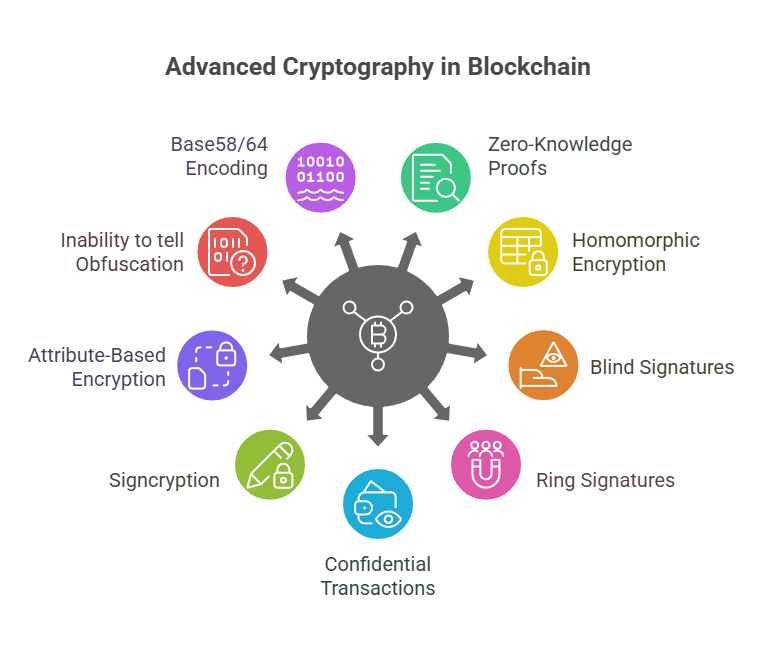
In addition to these fundamental primitives, sophisticated cryptographic ideas that are pertinent to blockchain, like:
- Zero-Knowledge Proofs (ZKPs): These enable a prover to demonstrate to a verifier that a statement is true without disclosing any additional information. pertinent to the secrecy of transactions in initiatives such as Zcash. comprises variations such as zk-STARKs and zk-SNARKs.
- Homomorphic encryption is important for data processing privacy because it enables calculations to be done on encrypted data without decrypting it.
- Blind signatures, which are employed in digital payment schemes for anonymity and unlinkability, enable a signer to sign a communication without being aware of its contents.
- Ring Signatures: A kind of digital signature that conceals the identity of the signer and enables a group member to sign a message on the group’s behalf.
- Confidential Transactions: Methods for hiding a public blockchain transaction’s value.
- Signcryption: A primitive that effectively combines the capabilities of encryption and digital signatures.
- Attribute-Based Encryption (ABE) is a type of public key cryptography that offers confidentiality and access control by relying on attributes for keys and ciphertexts.
- Inability to tell Obfuscation (IO): A method of obscuring code so that it behaves indistinguishably, which might turn smart contracts into a privacy black box.
- Base58 (used in Bitcoin addresses) and Base64 encode binary data into text for storage or transmission.
Also Read About Understanding Distributed Ledger Technology (DTL) Overview
For financial cryptography and blockchain technology’s specific opportunities and problems, such as privacy and quantum computing, cryptography is constantly explored and developed. Blockchain network security protocols require it.
