Blockchain Architecture
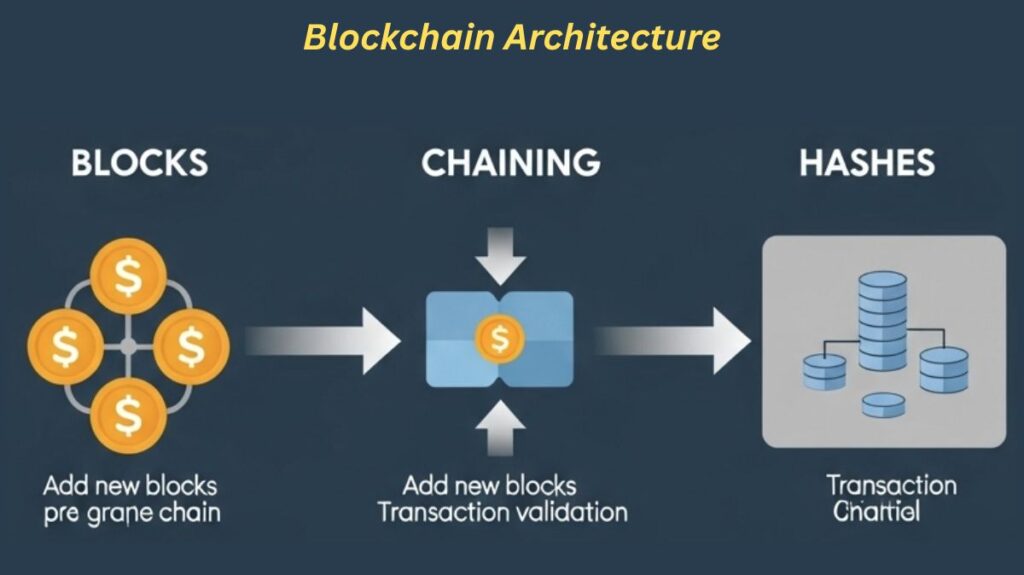
The Blocks
The basic data structures in a blockchain are called blocks. They act as containers for assembling digital events or transactions that have taken place during a given time frame. Consider a block to be a “page” in a transaction ledger.
Also Read About Blockchain For Beginners: A Basic Overview Of The Technology
Key components of a blocks
A block’s essential elements usually consist of:
Block Header
This includes information about the block in question. Typical crucial fields in the block header are:
- A distinct block reference number.
- A timestamp that shows the block’s creation date.
- A cryptographic nonce (if required for Proof of Work or other consensus methods).
- Level of difficulty (for chains of Proof of Work).
- Details about the consensus process, like the proposer or recipient.
- Gas usage and limit (in Ethereum).
- Data structure roots, such as the state tree root, transaction trie root, and reception trie root (in Ethereum).
- A cryptographic hash of the header from the previous block. This is the most important component for chaining.
- A Merkle root is a sum of the hashes of all the transactions that are part of the block. This makes it possible to efficiently verify every transaction in the block by examining just the Merkle root hash.
Block Body (Content)
A verified list of digital assets and instruction statements, including the names, quantities, and addresses of the parties participating in transactions, are usually found in the block body (content). The block body consists of a collection of transactions.
- The genesis block, a pre-configured block, is the first block in any blockchain network. It starts the chain.
Also Read About The History And Evolution Of Blockchain Technology
Chaining
The “chain” component of a blockchain is created via chaining, which is the process of connecting blocks in a sequential manner. The header of the current block contains the cryptographic hash of the header of the preceding block, which establishes this linkage.chaining
Chaining Mechanism works and its implications
The chaining mechanism works and its implications are as follows:
- The distinct hash produced from the header of the previous block in the chain is included in the header of a newly created and validated block (often via a consensus process).
- This essentially ties the new block to the old one by establishing a cryptographic link.
- The hash of a block will change if any of the data within it is changed.
- The link is broken because the original (now erroneous) hash of the modified block is contained in the subsequent block in the chain.
- Because their hashes would likewise change in a cascade effect, this renders invalid not just the block that was immediately connected to the modified block but also every block after it in the chain.
The blockchain tampering is made clear by this technique. Modifying an older block gets increasingly challenging and computationally demanding as more blocks are added on top of it. This is because tamper resistance is created by recalculating the hashes of all subsequent blocks. One of the main security features of blockchains is their append-only nature, which means that once data has been recorded and validated, it usually cannot be removed or changed.
Although the fundamental idea of chaining utilising the cryptographic hashes of earlier blocks is widely used, different DLTs may have distinct data structures. For instance, R3 Corda is a distributed ledger that connects at the transaction level, where the hash of one transaction is applied to the state of the subsequent transaction, rather than using blocks as in other distributed ledgers. Nonetheless, the fundamental idea behind the technology is still the cryptographic linking of records to guarantee immutability and provide a transparent history.
Comprehending Hashes
Blockchain technology requires hashes to protect data. Understanding hashes and how they work is essential to blockchain.
What Are The Hashes?
Hashed cryptographic results are produced by hash functions. Function input is uniquely represented as a fixed-size alphanumeric string. Like digital fingerprints, hashes no two data bits generate the same hash, as two humans have the same fingerprint.
Blockchain’s role
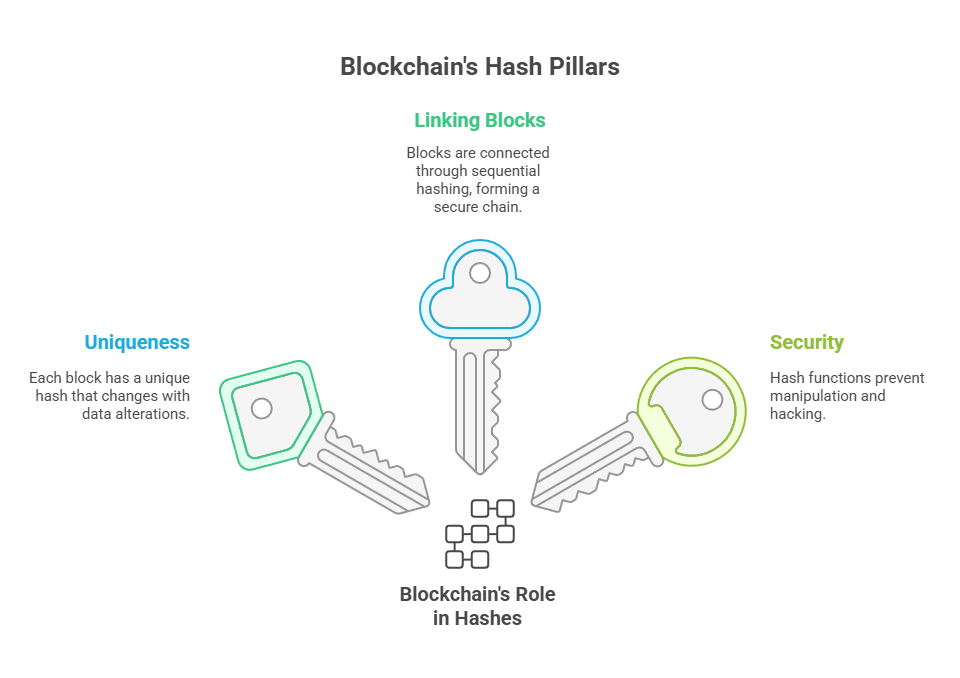
Hashes play a number of vital roles in blockchain:
- Uniqueness: A blockchain has a distinct hash for every block. This hash changes whenever the data in the block changes. This distinctiveness aids in identifying modifications or block tampering.
- Linking Blocks: To form a chain, each block includes the hash of the one before it. Blocks are linked chronologically and securely to this sequential hashing.
- Security: The hash function prevents manipulation and hacking by making output prediction and reverse engineering computationally difficult.
Hash Functions in Cryptography
Blockchains often utilize secure cryptographic hash methods like SHA-256. Features of these functions include:
- Deterministic: Same input, same hash result.
- Fast Computation: The hash function can quickly generate the hash value for any data set.
- Irreversibility: Reversing the hash function to determine the original input is computationally impractical.
- Collision Resistance: It is very unusual, but not impossible, for two distinct inputs to collide and generate the same hash.
- Avalanche Effect: A small input modification, even a single bit change, might produce a very different hash output.
Also Read About Understanding Distributed Ledger Technology (DTL) Overview
Maintaining Security and Integrity
Hashes protect the blockchain’s security and integrity in a number of ways:
- Immutability: Modifying a block’s data after uploading to the blockchain changes its hash. Because every block carries the hash of the block before it, modifying one block would change every block after it, which is extremely impossible depending on processing capacity.
- Verification: Blockchain nodes may quickly verify a block’s integrity by calculating its hash and comparing it to the recorded value.
- Tampering Security: Cryptographic hash algorithms make it impossible for an attacker to modify a block and recalculate all subsequent hashes in a recognisable way.
Hashes underpin blockchain security and integrity. They make blockchain a secure digital ledger, making it ideal for data storage and transactions in secure and trusted environments.
