What is hash pointer?
A hash pointer is a basic data structure that combines a cryptographic hash of the data with a conventional pointer to the data’s location. In essence, it lets you confirm that the data hasn’t been altered or tampered with in addition to providing you with information about where to find it.
Components
- Regular Pointer: This portion of the hash pointer keeps track of the data’s memory address so that it can be easily accessed.
- A cryptographic hash is a fixed-size digest generated from a variable-length input by a hash function. This cryptographic hash of the data it points to is stored in the hash pointer.
Also Read About FastBFT in Blockchain, Purpose, How It Works and Features
Integrity Verification
Integrity depends on the cryptographic hash being included. Because of the avalanche effect of hash functions, the hash calculated from the tampered data will vary significantly if the original data is changed in any way. Any tampering can be quickly identified by comparing the hash stored in the hash pointer with the recently computed hash of the data. The data is hence impenetrable.
Properties of Cryptographic Hash Functions
Certain characteristics of the underlying cryptographic hash functions determine how effective hash pointers are:
- Fixed-size output: Regardless of the size of the input, a hash function always generates a hash of a specific length. For instance, SHA-256 takes any input with a configurable bit length and outputs a 256-bit hash.
- Deterministic: The hash output will always be precisely the same given the same input.
- One-way (Preimage Resistant): The hash value of the input data cannot be used to compute the original data.
- Collision Resistant (Second Preimage Resistant): Finding two distinct inputs that provide the same hash output is computationally impossible.
- Avalanche Effect: A considerably different hash value will be produced by even a small change in the input, such as a single character or bit.
- Computationally Efficient: Hash functions are made to be quick and easy to compute, so application speed isn’t affected.
- Puzzle-friendly: This characteristic is crucial for consensus processes in blockchains that use proof-of-work, such as Bitcoin.
- SHA-256 (used by Bitcoin) and Keccak-256 (used by Ethereum) are two popular hash algorithms in blockchain technology. The Merkle-Damgard transform is used by SHA-256 to split arbitrary-length data into 512-bit pieces for processing.
Role in Blockchain Structure
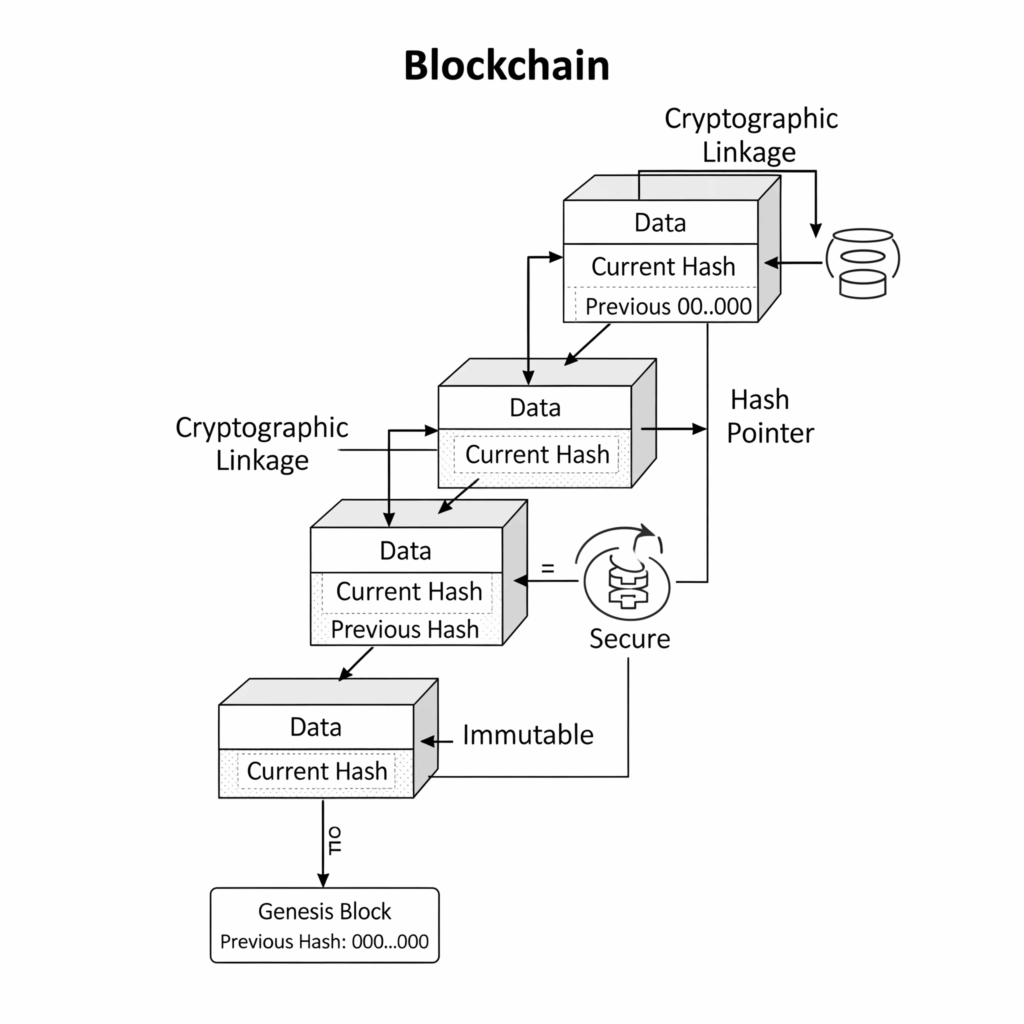
A blockchain is a skilful fusion of hash-based data structures, with hash pointers serving as its fundamental building blocks.
- In essence, a blockchain is a linked list constructed with hash points rather than standard pointers.
- The hash of the previous block’s header is contained in each block header, forming a cryptographic link in the chain.
- The hash of a prior block, which is usually set to all zeros, is absent from the genesis block, which is the first block.
- Immutability and tamper-evidence are ensured by this continuous linking: if any portion of a block’s data is altered, its hash is altered as well, which leads to an inaccurate hash being stored in the next block. Any change will be seen because of this up-the-chain ripple effect, and it gets harder to change earlier blocks as more are piled on top of them.
Also Read About ABFT Blockchain: Asynchronous Byzantine Fault Tolerance
Connectivity to Merkle Trees
- Through a Merkle tree, also called a hash tree, hash pointers are also utilised to confirm the integrity of the data within each block.
- A binary tree made up of hash pointers is called a Merkle tree.
- The hash values of each individual transaction inside a block are stored in the leaf nodes of a Merkle tree.
- This procedure is carried out upstream by non-leaf nodes (also known as intermediary nodes), which carry the hash value of their corresponding child nodes.
- A single Merkle root hash at the top of the tree is the result of this method. The block header then contains this Merkle root.
- By merely examining the Merkle root, this structure enables the effective verification of every transaction within a block. Any modification to a transaction will result in a change to its hash, which will propagate up the tree and change the Merkle root, rendering the block invalid. This system creates a “digital fingerprint” of every transaction in a block and aids in removing fraudulent or duplicate transactions.
Importance and Advantages
Immutability and Integrity
Hash pointers are essential for preserving the immutability and integrity of data both within and between blocks in a blockchain, which makes it extremely safe and verifiable.
Effective Verification
Merkle trees, which are constructed using hash pointers, enable effective data integrity and validity verification with feasible processing power and bandwidth, minimising the quantity of data that must be sent over the network for verification. The temporal complexity of searching for a transaction in a Merkle tree is O(logn), which is faster than O(n) for a linked list.
Proof of Membership
The efficient “proof of membership” (also known as “proof of inclusion”) made possible by Merkle trees enables a miner or client to demonstrate that a specific transaction is a member of a Merkle tree by displaying only the transaction and the hash values on the path from the transaction to the Merkle root, without disclosing the complete dataset. Additionally, this offers Simple Payment Verification (SPV), which allows a client to confirm the legitimacy and presence of a transaction without downloading the full blockchain.
Tampering Detection
By comparing the Merkle root in the block header with the Merkle root recalculated from the block’s data, miners may quickly determine whether any transactions have been tampered with. Tampering is shown by a mismatch.
Reduced Disc Space & No Delay
Merkle trees typically take up less disc space and speed up network data delivery.
Also Read About Understanding The Honey Badger Of BFT Protocols (HBBFT)
