What is collision attack?
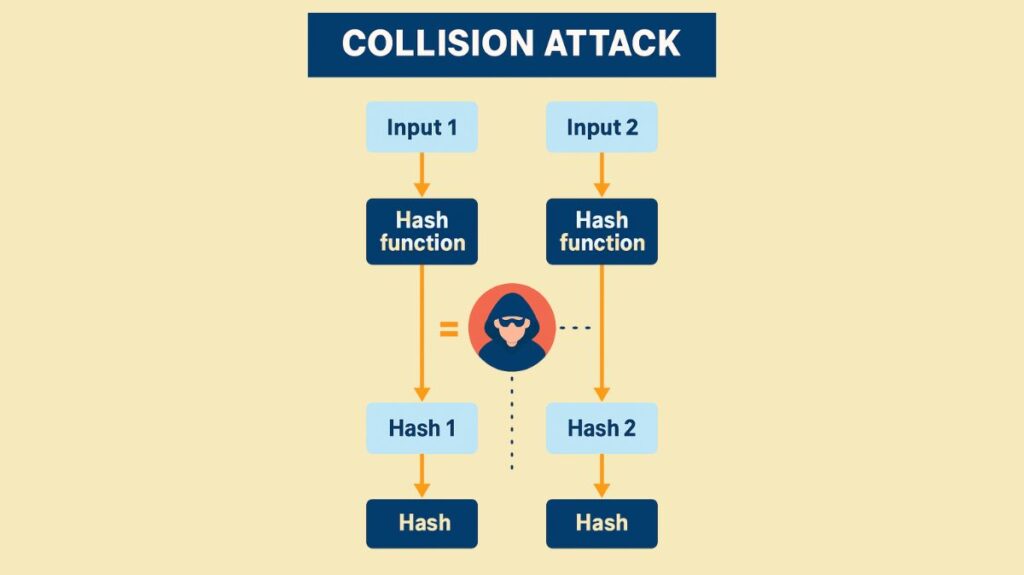
In cryptography, a collision attack is an attempt to identify two distinct inputs that, when processed by a cryptographic hash function, yield the same hash result, or “hash value.” This is especially true for blockchain technology.
In mathematics, this can also be expressed as locating two distinct messages, h1 and h2, so that hash(h1) = hash(h2).
Attacks of this kind compromise hashes uniqueness, which is an essential feature for the safety and integrity of systems like blockchain. The objective of a “preimage attack,” in contrast, is to locate the original input that matches a particular target hash value, as opposed to merely locating any two inputs that collide.
Types of Collision Attacks
- Classical Collision Attack: This involves finding any two different messages (m1 and m2) that produce the same hash value, without the attacker having control over the content of either message.
hash(m1) = hash(m2)
- Chosen-Prefix Collision Attack: This is a more generic and frequently more useful type. Given two distinct prefixes (p1 and p2), the attacker’s goal is to locate two appendages (m1 and m2) so that the hash of the two combined messages (p2 ∥ m2) equals the hash of the first combined message (p1 ∥ m1). This was one of the ways that the “Flame” malware was able to impersonate code signing using a Microsoft root certificate.
- The Manipulated Transaction Collision (MTC) attack type is designed to target “Execute-Order-Validate” blockchains, which execute transactions simultaneously and may cause interruptions and state inconsistencies.
You can also read Avalanche Performance, Consensus Mechanism, and Use Cases
How Collision Attacks Work and Their Impact
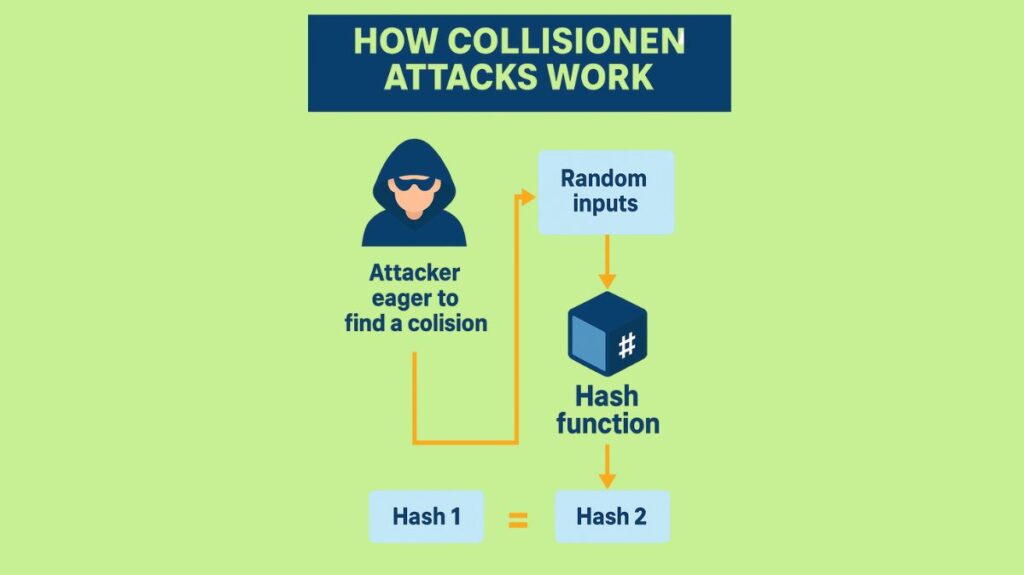
Every cryptographic hash function is subject to “birthday attacks” because of the “birthday problem,” which makes them prone to collisions. Compared to brute-force attacks, these attacks are far faster; according to hash function evaluations, a hash of n bits can theoretically be “broken” in 2^(n/2) time. Hash function-specific cryptanalysis can be used to launch more effective assaults. Frequently, the hash function is considered “broken” when an attack is found to be faster than a birthday attack.
Importance
In blockchain, cryptographic hash functions (like SHA-256 used in Bitcoin) are fundamental for:
- Linking blocks securely.
- Identifying transactions uniquely.
- Creating digital signatures.
- Preventing tampering.
- Ensuring data integrity.
A successful collision attack would have disastrous effects on the integrity and security of the blockchain:
- Block Tampering and Chain Integrity: The blockchain’s tamper-evident security may be jeopardized if an attacker were to change data inside a block without altering the hash value. A collision could allow a fraudulent block (Block A’) to replace a valid one (Block A) if hash(A) = hash(A’), changing history.
- Transaction Forgery and Double-Spending: Using the same hash, an attacker might produce two transactions: one that looks genuine (T_legit) and another that is fraudulent (T_fraud). Attackers may try to replace the phony transaction with the authentic one if the sender signs it. This would make it possible for fraud, including double-spending, to occur.
- The process of digital signature forgery frequently involves hashing the transaction data. If an attacker discovers two distinct transactions with the same hash, they can steal money because a signature created for one (for example, a modest payment) would also be legitimate for the other (for example, a huge payment to the attacker). An example from the real world was a faked X.509 signing certificate that impersonated a certificate authority by taking use of a prefix collision attack against MD5.
- Compromising Identity and Private Keys: Although extremely unlikely given the size of the address space, two distinct users would have the same private key in the event of a collision, allowing for illegal access to money.
You can also read What Is SegWit2x & Recommendations for Users During the Fork
Feasibility and Protection
As of right now, collision attacks are thought to be computationally impossible for powerful cryptographic hash functions like SHA-256, which employed by Bitcoin. SHA-256 collisions would demand a tremendous amount of processing power, substantially more than is currently available. For example, it is almost hard to identify a collision in SHA-256, which would need an average of about 2^128 computing efforts.
On the other hand, collisions have been discovered with older or weaker hash algorithms like SHA-1 and MD5, which have recognized problems. Collisions against MD5, for instance, may be carried out on a standard computer in a matter of seconds as of 2007. In order to identify more robust alternatives, such as SHA-3, the NIST hash function competition was launched.
The following are the main components of blockchain protection against collision attacks:
- Employing collision-resistant hash algorithms like SHA-256 or SHA-3.
- Update algorithms if vulnerabilities are detected.
- To make manipulation more difficult, digital signature systems include extra cryptographic techniques, like randomized hashing.
- Memory-hard functions are used to complicate brute-force attacks.
- Monitoring blockchain implementations and smart contracts regularly.
- Creating sophisticated detection techniques, such as detection supported by machine learning.
The likelihood of a collision rises as more inputs and outputs are compared and as hash outputs get shorter. Long-term worries about quantum computing stem from the possibility that it may theoretically undermine some of the present cryptographic presumptions, which could make collision attacks more practical.
An example of a collision attack would be attempting to locate two entirely distinct books with identical barcodes in a large library. By making it extremely difficult, if not impossible, to uncover such a duplicate barcode by chance or by sophisticated searching, a well-designed library system (a powerful hash function) ensures that every book has a unique identity. Because books would be unable to be identified by their barcodes, fraud and misplacement would result, and the library’s entire organizational structure would collapse if someone could simply locate these duplicate barcodes.
You can also read Online vs Offline Password Attack & Tool Brute Force Attack
