Blockchain digital signature

Digital signatures are a basic cryptographic approach in blockchain technology used to verify digital documents and messages. The digital equivalent of a stamped seal or handwritten signature. Decentralised blockchain networks need this method for security and trust.
Fundamental Ideas
Fundamental Ideas and Asymmetric-Key Cryptography Mechanism:
- Asymmetric-key cryptography, sometimes referred to as public-key cryptography, is the main foundation of digital signatures. Each user in this system has two cryptographic keys that are mathematically related:
- A private key that its owner keeps hidden.
- A publicly accessible key that is freely exchanged. Signatures are only valid for private key owners. Without the secret key, anyone with the corresponding public key can verify that signature.
How Signing Works in Blockchain
The following procedures are involved in signing a message or transaction:
Creation of a Transaction
A user starts a transaction, providing information like the address of the recipient and the total amount of cryptocurrency.
Hashing
A cryptographic hash technique like SHA-256 is used to generate a fixed-size unique output, called a “hash” or “message digest,” from transaction data. As a “digital fingerprint” its hash changes with even minor data changes. Hashing allows digital signatures to use fixed-length message digests, making it crucial.
Signing
The sender signs this hash with their private key. This procedure generates the distinct digital signature, which is mathematically connected to the sender’s private key and the transaction data. The digital signature is made up of the hash method and the encrypted hash value.
Also Read About What Are The Blockchain Transaction Steps And Types?
How Blockchain Verification Operates
Anybody can confirm a transaction once it has been broadcast to the network along with its digital signature:
- Data Receiving: The recipient or validator receives the transaction data, sender public key, and signature.
- Recipient repeated message using identical cryptographic hash.
- Compare and Decrypt: The recipient uses the sender’s public key to decrypt the digital signature. If the decrypted hash matches the recipient’s, the signature is valid.
This validation confirms two key points:
- The transaction’s authenticity, confirming that the sender has the private key.
- Validating that transaction data hasn’t changed since signing. Changing the signature nullifies it.
The Benefits of Blockchain
Digital signatures provide trust-building security in decentralisation:
- They verify that communications or transactions come from the intended sender.
- Integrity: They guarantee no transaction data changes since signing.their private key is mathematically connected to their transaction signature, the sender cannot retract it.
- Blockchain validates digital signatures without an intermediary or central authority to generate confidence.
- Efficiency: Electronic signatures eliminate paperwork and laborious verification, speeding online transactions.
- Secure: Hashing and public-key cryptography prevent digital signature fraud.
Key Algorithms
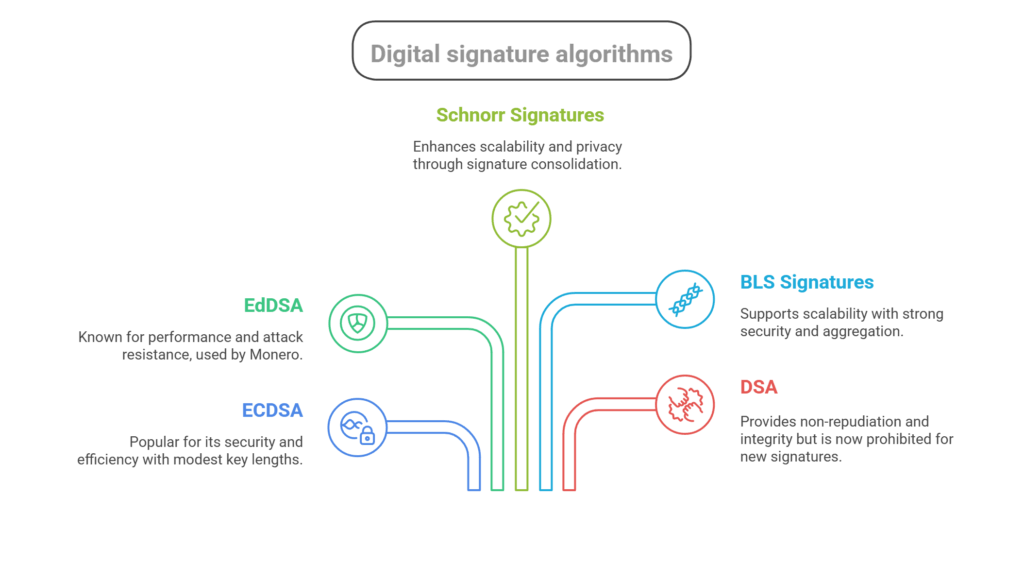
Blockchain utilises several digital signature algorithms:
- Ethereum, Bitcoin, and other blockchains use the Elliptic Curve Digital Signature Algorithm (ECDSA), the most popular blockchain algorithm. Its modest key lengths make it effective and secure. Bitcoin uses secp256k1 ECDSA.
- Edwards-curve Digital Signature Algorithm (EdDSA) is used by Monero for its performance and attack resistance. Newer algorithms EdDSA/Ed25519 power Ethereum and Bitcoin.
- Schnorr Signatures are effective, non-malleable, and may consolidate several signatures into one compact signature, boosting scalability and privacy.
- BLS Signatures (Boneh-Lynn-Shacham) assist scale Ethereum 2.0 with strong security and key and signature aggregation.
- The discrete logarithm problem and modular exponentiation power the public-key cryptosystem Digital Signature Algorithm (DSA). It was first proposed by NIST in 1991. DSA generates signatures faster than RSA but validates slower. Non-repudiation, integrity, and authentication are provided for messages. DSA-based ElGamal and Schnorr signature systems. FIPS 186-5 (February 2023) prohibits DSA from creating digital signatures, however it can validate signatures created before that standard.
Uses Not Just for Transactions
Other blockchain scenarios also make use of digital signatures:
- Smart contracts: Confirming that instructions haven’t been altered and that the execution of a smart contract is permitted. Logic for digital signature verification can also be incorporated into smart contracts.
- Governance: Making certain that proposals or votes in Decentralised Autonomous Organisations (DAOs) are valid and cast by authorised members.
- Verifying the accuracy of data stored on the blockchain is known as data verification.
- Digital Identity: NFTs use cryptographic keys for decentralised verification of virtual identities and digital assets. Cryptographic key pairs are essential for generating distinct account addresses that function as decentralised identities.
- Platforms utilise digital signatures to sign and transmit documents on the blockchain securely and verifiably.
Security Points to Remember
The entropy, confidentiality, and uniqueness of the random signature value k are crucial components of DSA and ECDSA. An attacker could obtain the full private key if any of these conditions are broken. The private key may be revealed, for instance, by using the same value of k twice, by employing a predictable value, or by leaking even a little portion of k over several signatures. The PlayStation 3 hack served as an example of this, as Sony was unable to produce a fresh random k for every signature. By determining k deterministically from the private key and the message hash, this problem can be lessened.
Furthermore, strong quantum computers have the potential to compromise algorithms that depend on the computational complexity of solving discrete logarithms, such as DSA, ECDSA, and Diffie-Hellman. DSA is “no longer secure” under this situation.
Also Read About EOA Meaning Blockchain: An Externally Owned Accounts
