Although it is more frequently employed in its form, elliptic curve digital signature algorithm the Digital Signature Algorithm (DSA) is a basic cryptographic approach in blockchain technology. Within decentralized networks, DSA is essential for guaranteeing the non-repudiation, integrity, and authenticity of digital documents, software, or messages.
Digital Signature Algorithm Definition and Origin of DSA
For digital signatures, DSA is a Federal Information Processing Standard (FIPS) and public-key cryptosystem. In August 1991, the National Institute of Standards and Technology (NIST) suggested including it in the Digital Signature Standard (DSS). The discrete logarithm issue, which is thought to be computationally intractable, and the mathematical idea of modular exponentiation serve as the foundation for DSA. This algorithm creates digital signatures using public-key cryptography and is a signature algorithm rather than an encryption technique. Though it can still be used to validate previously created signatures, DSA will no longer be permitted for the creation of digital signatures, according to the most recent specification, FIPS 186-5 from February 2023.
Core Principles and Mechanism of DSA
For each user, asymmetric-key cryptography (public-key cryptography) uses two mathematically related keys: a public key shared freely and a private key kept hidden. Based on this, DSA works. Whoever has the matching public key can validate a signature generated by the private key owner.
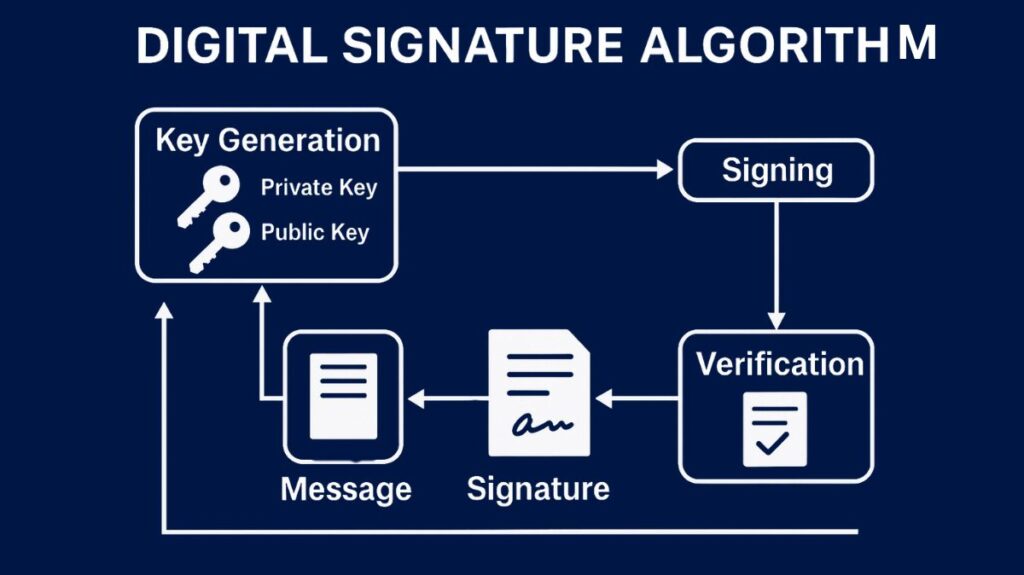
These steps are often involved in the process:
- Key Generation: There are two stages involved: per-user key generation and parameter generation, which can be shared by users.
- Parameter Generation: The key lengths (L and N bits) and cryptographic hash function (SHA-1, SHA-2) are selected. They choose an N-bit prime q and an L-bit prime p, where p-1 is a multiple of q. To calculate g:= h^((p-1)/q) mod p, an integer h is selected. It is possible to exchange these parameters (p, q, g).
- Per-User Keys: The public key y is calculated using the formula y = g^x mod p, whereas the private key x is selected at random from 1 to q-1. Deriving x from y is not computationally viable.
- Key Distribution: The private key x is kept confidential, but the public key y is made public.
- Signing: To sign m, a user must calculate r and s. This involves using SHA-256 to generate a fixed-size hash or message digest of the transaction data. Now the sender signs this hash with their private key. This creates the digital signature. A randomly generated integer k is also needed for each signature.
- Verification: The message, signature (r, s), and sender’s public key (y) are sent to the relevant node. The sender’s public key is used to generate the message’s hash and decipher the digital signature. Signatures are valid if newly computed and decrypted hashes match. Valid signatures have v equal to r, which is derived using the sender’s public key, message hash, and public key components.
This verification mechanism guarantees authenticity (the transaction came from the supposed sender) and integrity (the data hasn’t changed since signing).
DSA’s Role in Blockchain
Blockchain security relies heavily on digital signature techniques, especially ECDSA. Ethereum, Bitcoin, and other blockchains use ECDSA, the most used algorithm. Bitcoin uses ECDSA with secp256k1 elliptic curve. Digital signatures are essential in blockchain because they:
- Transaction Validation: Private key cryptography verifies ownership and approves digital asset transfers. Before adding transactions to a block, network nodes verify these signatures.
- Data Integrity and Immutability: Signatures guarantee that data on the blockchain has not been altered and validate smart contract execution in addition to value transfers. Any data change would render the impacted signatures invalid, notifying the network.
- Consensus and Governance: On-chain voting and governance systems use digital signatures to verify that authorised participants voted or proposed, ensuring impartiality.
- Cryptocurrencies: They validate ownership of digital assets and authorize transactions.
- Smart Contracts: They are able to restrict access and guarantee that only permitted individuals are able to carry out particular tasks.
- Digital Identity: Individual account addresses that serve as decentralised identities are based on cryptographic key pairs.
Key Algorithms and Variants
A variation of the Schnorr and ElGamal signature techniques is DSA. Additional blockchain-related digital signature algorithms are as follows:
- Elliptic Curve Digital Signature Algorithm (ECDSA): Renowned for its effectiveness and security with reduced key lengths, and it is widely utilized in Ethereum and Bitcoin.
- Edwards-curve Digital Signature Algorithm (EdDSA): Used in blockchains like Monero, which are known for its efficiency and attack resistance.
- Schnorr Signature: Enhances privacy and scalability by being efficient, linear, non-malleable, and able to aggregate signatures.
- BLS Signatures (Boneh-Lynn-Shacham): Provide strong security and key and signature aggregation, which aids blockchain scale, especially in Ethereum 2.0.
- Rivest-Shamir-Adleman (RSA): Encrypting the message hash using the sender’s private key is another frequent way.
- Rabin signature algorithm: Hashing was introduced as a crucial step in one of the earliest digital signature techniques.
Advantages of DSA
As a digital signature system, DSA provides the following advantages:
- Authentication: Confirms the sender’s identity and establishes that the message originated.
- Integrity: Assures that since it was signed, the transaction data has not been changed.
- Non-repudiation: Because the signature is mathematically connected to the sender’s private key, the sender cannot claim not to have signed the transaction. For non-repudiation, a reliable third party may also be included.
- Efficiency: Reduces manual verification and paperwork by automating and expediting the electronic transaction signature process. RSA is slower than DSA at creating signatures.
- Security: Prevents forgery by using hashing techniques and public-key cryptography.
- Cost Savings: Reduces the need for manual handling, courier, and printing expenses by doing away with the requirement to physically move documents.
- Timestamping: Can provide the time and date of a digital signature, which is crucial for actions that need to be completed quickly and to prevent replay assaults.
- Legal Validity: Similar to handwritten signatures, it is widely recognized and legally binding in many jurisdictions.
- Traceability: Facilitates record-keeping by establishing an audit trail.
- Workflow Automation: Minimizes errors and delays by standardizing and optimizing workflows.
- Memory Efficiency: Since DSA generates the signature using a 160-bit hash value, it utilizes less memory than competing techniques like RSA.
Disadvantages and Security Considerations
Notwithstanding its benefits, DSA and, consequently, ECDSA have drawbacks and security issues.
- Quantum Computing Threat: Powerful quantum computers have the potential to seriously undermine algorithms like DSA and ECDSA that depend on the computational difficulty of solving discrete logarithms. DSA is “no longer secure” under this situation. Using distinct addresses for every transaction can provide a certain amount of quantum safety, even if Bitcoin may have some protection because public keys are only released upon spending.
- Sensitivity to Random Number k: For DSA and ECDSA, the random signature value k’s entropy, secrecy, and uniqueness are crucial. An attacker can obtain the complete private key if any of these conditions are broken. The private key x can be found, for example, by using the same k value again, a predictable value, or by leaking even a little portion of k over several signatures. This vulnerability was revealed via the PlayStation 3 hack, in which Sony neglected to create a fresh random k for every signature. By deterministically determining k from the private key and the message hash, this problem can be lessened.
- Malicious Implementations: Even from ostensibly safe offline devices, malicious implementations could decide to covertly leak information using signatures.
- Key Management Complexity: It is difficult to generate, store, distribute, and revoke cryptographic keys securely.
- Infrastructure Dependence: Digital signatures require secure PKIs and CAs. This infrastructure may be corrupted or unavailable, affecting trust.
- Initial Setup Costs: Costs for user training, security precautions, and certificates may arise when a full digital signature system is implemented.
- Offline Usability: Without the signer’s private key, digital signatures are difficult to use, and security components and hardware tokens make things more difficult.
- User Education: Effective implementation requires adequate user education, which includes raising knowledge of potential risks and vulnerabilities.
- Vulnerability to Key Compromise: Fraudulent signatures may result from a compromised private key, underscoring the necessity of strong security.
- Need for Standardization: To enable smooth interaction between various digital signature techniques, a single standard is required.
To sum up, DSA is a key component of the blockchain security concept, primarily through its ECDSA form. By offering cryptographic proofs for asset ownership, data integrity, and transaction validity, it permits decentralized systems to operate without centralized trust. Even while it has many benefits, its flaws especially with regard to quantum computing and the control of the k value need constant attention and mitigation techniques.
