Regarding identity concealing, anonymity and pseudonymity are two different ideas that are very pertinent when discussing blockchain technology and cryptocurrencies. Both provide varying degrees of anonymity, but they vary in how much a person’s identity and behavior can be tracked.
Anonymity in blockchain
When someone is anonymous, their identity is totally unknown and their behavior cannot be traced back to them. No user identification is ever disclosed, not even inadvertently, in an anonymous system.
What is Anonymity in blockchain?

- Definition: Complete lack of identity is implied by anonymity. Nobody, not even the perpetrator, can link the action to a person. Blockchain security prevents linking transactions to individuals. Anonymous blockchain transactions prevent user identification.
- Privacy: Anonymity is more private than pseudonym.
- Social media pen names allow anonymous survey completion.
Benefits
- Protects privacy, allows sensitive whistleblowing, and allows free speech without retaliation.
- Preserves privacy: In order to prevent monitoring or safeguard personal data, users can choose to secure their financial privacy.
- Permits the use of whistleblowers in delicate circumstances.
- May improve security by making it more difficult for bad actors to find and target people.
- Crucial for preventing censorship, particularly in nations with stringent regulations. People can give to delicate causes through anonymous transactions without disclosing who they are and running the danger of being persecuted.
Limitations and Challenges
- Since most public blockchains use pseudonymous addresses, it is challenging to obtain true anonymity on them. On top of the fundamental blockchain technology, it is frequently an add-on feature that requires independent implementation.
- Can be utilized for evil, making accountability difficult. One of its main drawbacks is that malevolent actors can act freely.
- The “right to be forgotten” and other legal notions are incompatible with blockchain’s unchangeable nature.
Pseudonymity in blockchain
People conceal themselves via pseudonyms. User transactions on the public blockchain can be linked to an alias or address, even if their identity is unknown.
What is Pseudonymity in blockchain?

- Definition: Using a pen name or pseudonym to hide one’s true identity. Instead than using their true names, users of blockchain communicate using pseudonyms, or blockchain addresses. A particular address may be connected to a transaction, but not always to the person who initiated it.
- Traceability: All transactions are available to the public, and the user’s account identifiers are not anonymous, even when their true identity is not directly connected. It may be possible to track down every transaction connected to a pseudonymous address if one can connect it to a real-life identity.
Also Read About Eclipse Attack Blockchain Detection And Prevention Explained
Examples
- A writer using a pen name for publication.
- A person using a username that is not their own name when they register for an account on a social media site.
- Experts such as Dwayne Johnson’s “The Rock” perform under a stage name.
- In cryptocurrency, pseudonymity is provided by the alphanumeric address that is generated when you create a Bitcoin wallet and is viewable on the blockchain.
- Bitcoin’s founder or founders, Satoshi Nakamoto, are anonymous under a pseudonym.
Benefits
- Keeps one’s professional and personal identities apart.
- Makes it possible to establish a reputation under a different name.
- Protects internet data.
- Because of pseudonymity, many favors Bitcoin.
Limitations
- Transactions and behaviors can be linked to a pseudonym, allowing identification.
- It may be possible to link financial forensics on a public address to a real-life identity.
- Some people misuse pseudonymity for financial benefit by using phoney identities, even if it permits an identity to be retained under a different name.
Anonymity and Pseudonymity in Cryptocurrencies
It would be more correct to characterize the majority of public blockchains, including Ethereum and Bitcoin, as providing pseudonymity as opposed to complete anonymity. This is due to the fact that every transaction on the blockchain is associated with a unique public address that can be tracked.
On-Chain Analysis
Pseudonymous accounts can be linked to real-world identities by analyzing transaction patterns, addresses, and entity graphs because all transactions are publicly accessible and the complete transaction history is accessible. For instance, an individual may disclose their cryptocurrency address on a personal website, connecting it to their true identity, or law enforcement may request documents from an exchange.
True Anonymity Challenge
Public blockchains struggle to achieve true anonymity despite privacy measures. Even with modern blockchain research tools, transactions may be linked to humans if users reuse addresses or use centralized exchanges that need KYC data.
Methods and Strategies for Strengthening Anonymity
Although pseudonymity is provided by many public blockchains, a number of architectural and cryptographic techniques seek to improve or accomplish true anonymity:
Key Pairs and Cryptographic Primitives
- Blockchain transactions are connected to cryptographic identities through public-private key pairs and digital signatures. Without disclosing the true name, a public key (or an address generated from it) is visible, demonstrating access to the private key.
- Users can create an infinite number of asymmetric key pairs and addresses on many permissionless blockchains, which adds to the many levels of pseudo-anonymity.
- By cryptographically protecting client identity privacy, cryptographic hashing aids in transaction and chain security.
Network Design and Permission Models
- A certain amount of pseudonymity is provided by permissionless blockchains, such as Bitcoin and Ethereum, which are open and decentralized, enabling participation by anybody without centralized control.
- Participants on permissioned blockchains, also known as private or consortium blockchains, normally do not have anonymity because their identities are frequently known and verified.
Privacy-Focused Technologies and Protocols
Privacy Coins
The purpose of Privacy Coins is to improve user privacy by going beyond pseudonymity.
Zcash (ZEC)
Through “shielded transactions,” Zcash (ZEC) allows for private transactions and even the private execution of smart contract code on a public blockchain by utilizing Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (zk-SNARKs).
Monero (XMR)
Using a mix of ring signatures (which make it more difficult to identify the true signer among a group), ring confidential transactions, and stealth addresses (unique, one-time addresses for every transaction), Monero (XMR) Makes transaction data hidden. Additionally, Monero conceals Unspent Transaction Outputs (UTXOs) by using decoy outputs.
Mixing Protocols (e.g., CoinJoin/PrivateSend)
By severing the direct connection between transaction inputs and outputs, mixing protocols like CoinJoin/PrivateSend seek to offer anonymity. A mixing service sends back various currencies of the same value to destinations after users pool their funds, making tracing challenging. Private Send is used by Dash Coin.
Dandelion Protocol
Alters protocols such as Bitcoin’s peer-to-peer (P2P) network layer. It is more difficult to track down the origin of transactions since they are relayed one-to-one in a “stem phase” before being disseminated in a “fluff phase.”
Layer 0 Methods (Network Layer)
By obscuring users’ IP addresses, technologies like as I2P (Invisible Internet Project) and Tor (The Onion Router) work at the network level to conceal users’ identities.
Homomorphic Encryption
Homomorphic encryption protects data on blockchains by enabling computations on encrypted data without the need to decrypt it.
Privacy Managers
Privacy managers are off-chain parts of commercial blockchains that ensure secrecy by using a hash index in place of transaction payloads. This ensures that only parties engaged can access the encrypted payload.
Also Read About What Is A Cold Wallet Crypto?, Cold Wallet Benefits Overview
What is the difference between anonymity and pseudonymity?
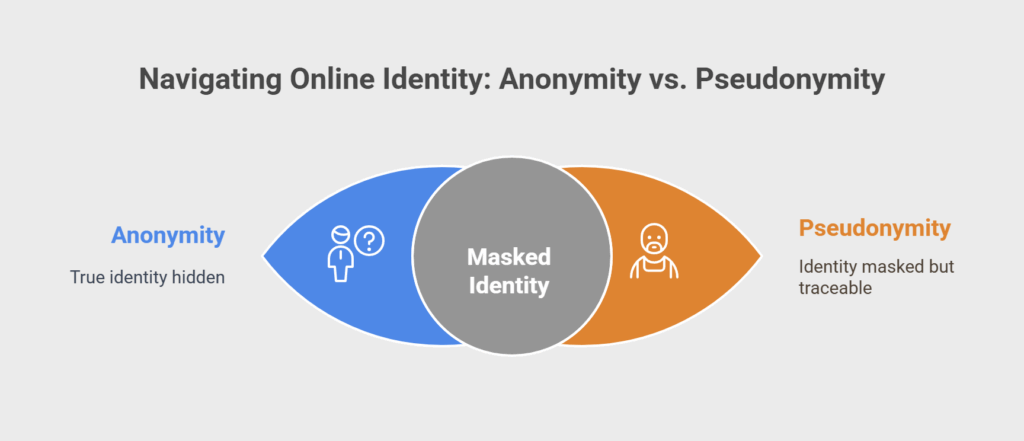
The following are the main differences between pseudonymity and anonymity:
- Identity: While pseudonymity entails adopting a false identity, anonymity ensures that no identity is disclosed.
- Traceability: While pseudonymity enables acts to be linked to the pseudonym, anonymity precludes any traceability of actions.
- Accountability: Pseudonymity allows some responsibility, but anonymity makes it hard to hold someone accountable.
| Feature | Anonymity | Pseudonymity |
|---|---|---|
| Definition | No identification, identity unknown | Using a false name, but can be linked to identity |
| Identification | Not identifiable, unknown identity | Can be identified, but not by real name |
| Traceability | Not traceable | Potentially traceable |
| Example | Posting online with no identifying information | Using a username to post online |
| Risk of Retaliation | Low risk | Moderate risk |
| Privacy Level | Highest | Moderate |
| Accountability | Difficult to hold accountable | Potentially accountable |
| Data Utility | Can be limited | Generally allows for more data usage |
| Data Security | Requires careful management of data | Requires careful management of pseudonyms and related data |
| Functionality | May limit data usage/sharing | Can maintain functionality |
| Example (Crypto) | Privacy coins like Zcash and Monero | Bitcoin, where addresses are pseudonyms |
Overall, blockchain technology provides pseudonymity through distributed, transparent ledgers and cryptographic identities, but genuine anonymity requires privacy-focused blockchains. Politicians and privacy activists are debating the blockchain trade-off between openness, privacy, and regulatory compliance.
