Distributed Hash Table Blockchain
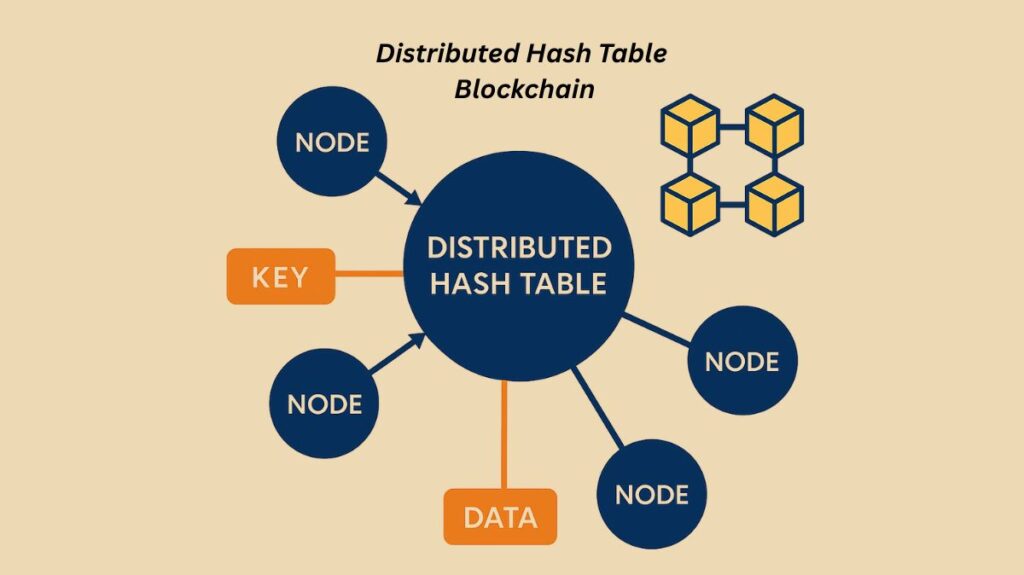
Peer-to-peer (P2P) networks use Distributed Hash Tables (DHTs), which are data structures with information dispersed among many nodes. DHTs provide decentralization, fault tolerance, and scalability in contrast to conventional databases. To put it simply, the nodes in a DHT work much like the “buckets” in a traditional hash table.
The Core Idea: Hash and Distribute
Envision possessing an enormous quantity of data, comparable to the volumes in a library. For a standard hash table, the location of each book would need to be stored on a single, enormous computer. Comparatively speaking, a DHT functions similarly to thousands of little libraries.
- Key-Value Pairs: A DHT stores data in key-value pairs, just like a conventional hash table. The data itself (the book) is the “value,” while the “key” is a special identification (such as an ISBN).
- Hashing: When you want to store or retrieve data, the key is put through a consistent hashing algorithm. This algorithm takes the key and produces a unique, fixed-size numerical ID.
- Responsibility: The magic of a DHT is that each node in the network is responsible for a specific, contiguous range of these numerical IDs. This range is determined by its unique numerical ID. When you hash a key, the resulting ID tells you which node is responsible for storing that data.
You can also read What is Decentralized Storage? How it works, And Benefits
How it Works in Practice
Let’s use an analogy of a circular “ID space.”
- Nodes: This circular ID space is where each node in the network is given its unique ID.
- Keys: When you want to store a piece of data, its key is also hashed to produce an ID on the same circular space.
- Storage Rule: The data is kept on the node whose ID is “closest” to the ID of the key, usually by moving in a certain direction (clockwise, for example) throughout the ID space.
- Lookup: The key is hashed once more when you wish to access the data. A node “closer” to the key’s ID receives the request that your node makes to its neighbors, who then transmit it to another node around the circle. Until the request is received by the node in charge of that key and the data is returned, this process keeps going.
This process is highly efficient, typically requiring only a small number of “hops” to find the right node, even in a network with millions of participants.
Key Characteristics and Benefits
- Decentralization: DHTs have no central server or authority, making them unattackable. Nodes behave as peers.
- Scalability: The number of nodes and data volume can be effectively increased with their design. Functionality is not much affected by the addition or removal of nodes, and data can be dispersed uniformly.
- Fault Tolerance: DHTs can handle node failures and network partitions gracefully, ensuring data remains available and consistent. If a node fails, its data can be replicated or reassigned to other nodes.
- Efficiency: DHTs offer fast lookup times. Lookups are highly efficient, typically having logarithmic complexity (O(logN)) relative to the number of nodes, meaning finding data is swift even with millions of nodes.
- Consistency: They usually offer eventual consistency guarantees, which refer to the process by which all copies finally converge to a consistent state and updates to the DHT are spread throughout the network.
- Flexibility: They can be applied to several tasks, including decentralized currency, content delivery networks, and file sharing.
- High Availability and Link Stability: DHTs are made to guarantee that network connections are constantly available and data is available when needed.
You can also read Advantages And Disadvantages Of Mobile Wallet In Blockchain
Key Properties of DHTs
| Property | Description |
|---|---|
| Decentralized | No central server; all nodes share responsibility. |
| Scalable | Works efficiently even with millions of nodes. |
| Fault-Tolerant | Data remains accessible even if some nodes fail. |
| Efficient Lookup | Typically takes O(log N) steps to find data in a network of N nodes. |
| Self-Healing | Automatically adapts to nodes joining and leaving. |
Why They Are Needed
- In traditional client-server systems, central servers can become bottlenecks or single points of failure. In decentralized networks, data needs to be shared across many nodes, and nodes can join and leave at any time (dynamic membership).
- DHTs solve these problems by distributing data evenly and allowing fast, reliable data retrieval without a central authority. They provide an easy way to find information in large data collections because keys are in a consistent format, allowing fast identification of where key/value pairs reside.
Implementations and Examples
- A popular technique for DHTs in peer-to-peer networks, Kademlia optimises key-value retrieval and storage through the use of effective routing algorithms while guaranteeing fault tolerance. An XOR-based distance metric is used by Kademlia for effective routing. Java implementations (TomP2P, kad-socks, J-Kademlia), Rust-Kademlia, Python Kademlia libraries (kademlia-dht, pykad), and libp2p (Go) are a few examples of open-source Kademlia examples.
- Pastry (which routes messages based on prefix-matching), Chord (which arranges nodes in a ring topology), and CAN (Content Addressable Network) are other well-known DHT technologies.
- A DHT-like architecture is also used by Amazon Dynamo to replicate and split data for high availability.
Real-World Applications/Use Cases
- Peer-to-Peer (P2P) File Sharing: Applications like BitTorrent use DHTs for decentralized tracking and distribution of files among peers.
- Decentralized Storage Networks: Applications such as IPFS (InterPlanetary File System) use DHTs (specifically Kademlia) to locate and retrieve content from distributed nodes.
- Blockchain and Cryptocurrencies: Some blockchain applications utilize DHTs for peer discovery, network self-organization, and data distribution, improving scalability. Ethereum, for instance, uses the Kademlia protocol for its node discovery mechanism.
- Content Delivery Networks (CDNs): DHTs enable efficient caching of content based on geographical locations, enhancing content distribution efficiency and reliability.
- Decentralized Messaging and Communication: Secure messaging platforms and VoIP services use DHTs to connect peers and forward messages without central servers, enhancing anonymity.
- IoT Networks: DHTs can organize data storage and retrieval in decentralized IoT networks.
- Distributed Databases and Caching: They can distribute data across multiple servers for high availability and horizontal scalability.
Challenges
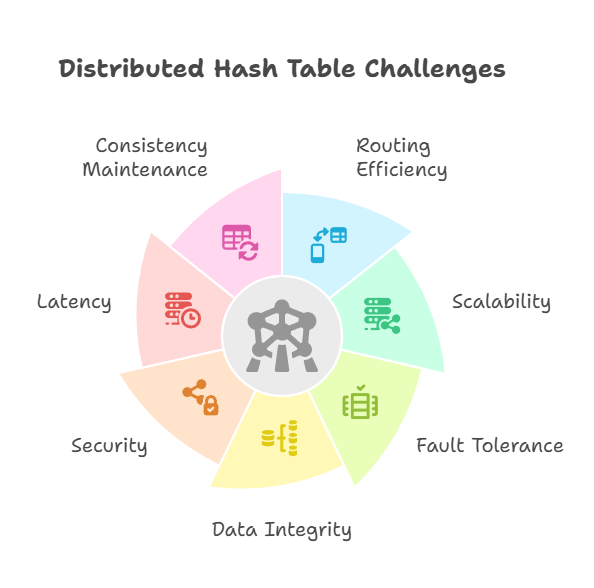
Distributed Hash Table Challenges
- Routing Efficiency: For quick data location across big networks, it’s essential to maintain effective routing tables.
- Scalability: Smoothly adding or removing nodes without affecting performance.
- Fault tolerance: Handling node failures without effecting system availability or data loss.
- Data integrity: Maintaining distributed node dependability and consistency, especially during network partitions or concurrent updates. Incorrect behavior or failure of nodes may result in inconsistent data.
- Security: Protecting against malicious attacks or unauthorized access within the decentralized network.
- Latency: Lookup operations typically require multiple network hops, which can introduce latency compared to centralized systems. Network latency can affect performance in very large or unstable networks.
- Consistency Maintenance: Maintaining consistency across replicas in a dynamic network (where nodes frequently join or leave) can be challenging, potentially leading to outdated or conflicting data until reconciled.
Summary Table
| Feature | Distributed Hash Table |
|---|---|
| Structure | Decentralized key–value store |
| Nodes | Peers in a network, each with an ID |
| Data | Stored based on hashed keys |
| Efficiency | O(log N) lookup |
| Use Cases | File sharing, decentralized storage, blockchain |
You can also read What Is A Desktop Wallet And How Does Desktop Wallets Work
