What is a preimage attack
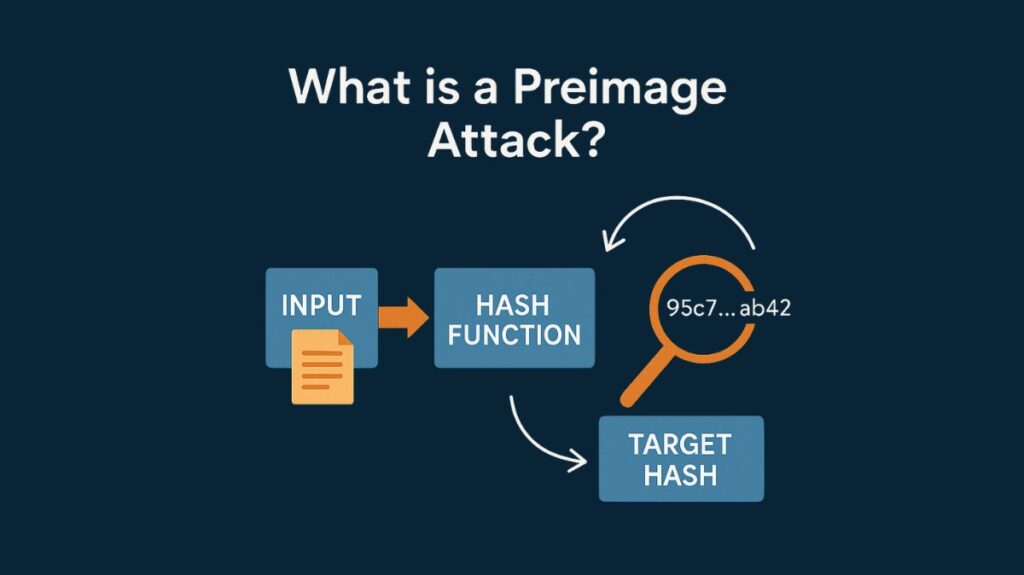
A preimage attack is a type of cryptographic attack that specifically targets cryptographic hash functions. The primary goal of such an attack is to reverse the “one-way” property that these functions are designed to possess.
It is crucial to first understand the foundations of cryptographic hash functions and their characteristics in order to comprehend a preimage attack:
- Pure deterministic functions known as cryptographic hash functions can accept any size input (typically referred to as “message” or “original data”) and output a fixed-length result, often termed a digest or hash value. Scrypt, Ethash, RIPEMD, SHA-256, and SHA-512 are a few examples. They are made to calculate quickly and efficiently, but they are computationally impossible to reverse. According to this theory, a minor alteration to the input will result in an entirely different output, and the same input will always create the same output (determinism).
- The preimage resistance (one-way property) of cryptographic hash algorithms is a basic security feature. According to this rule, the original input value (x) that generated a hash output (y) must be computationally impossible to calculate or trace. Put more simply, it shouldn’t be easy to figure out the original data if you only have the hash. A preimage attack targets this characteristic directly.
You can also read Avalanche Performance, Consensus Mechanism, and Use Cases
What a Preimage Attack Aims to Do
This preimage resistance feature is immediately targeted by a preimage attack. Finding any input (the “preimage”) that hashes to a given hash output is the attacker’s objective. It is deemed that the hash function is vulnerable if an attacker can effectively locate such an input without needing to try every conceivable input.
Contrast with Other Hash Function Properties
It is important to distinguish preimage attacks from other related cryptographic attacks:
- Second Preimage Resistance (Weak Collision Resistance): This property states that given an input (x) and its hash (h(x)), it is computationally infeasible to find a different input (m) that produces the same hash output (h(m) = h(x)). A preimage attack, however, doesn’t necessarily seek a different input; it just seeks any input matching the hash.
- Collision Resistance (Strong Collision Resistance): Any two distinct inputs (x and z) that hash to the same output (h(x) = h(z)) must be computationally impractical to possess this attribute. Preimage attacks target a particular output and attempt to locate its original input, while collision attacks seek to locate any pair of inputs that intersect. In general, collision attacks are thought to be simpler than preimage attacks since they only need about 2^(n/2) operations for an n-bit hash, while preimage attacks need roughly 2^n operations.
How Preimage Attacks Work (Theoretically)
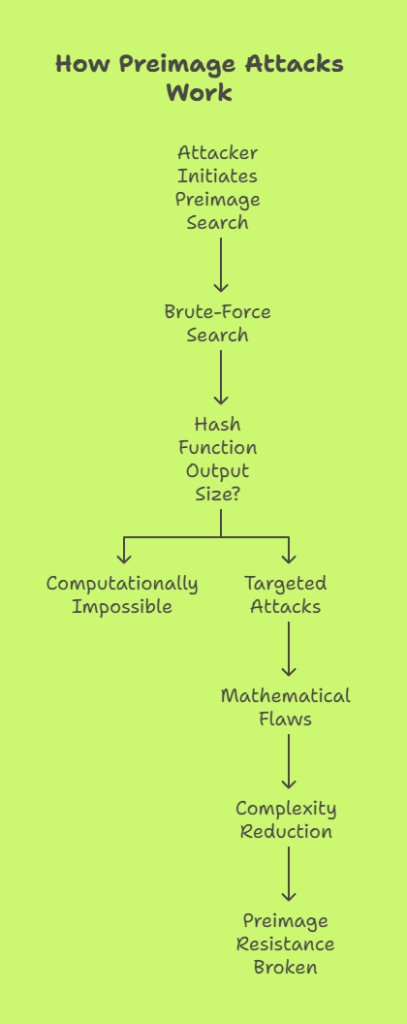
How Preimage Attacks Work
An attacker may try a brute-force search in its most basic form in order to locate a preimage. Attempting random inputs, hashing each one, and determining whether the intended hash result is produced are all part of this process. On the other hand, a brute-force attacks would need an average of 2^256 operations for powerful cryptographic hash functions with big output sizes (SHA-256, for example, which generates 256 bits), which is an absurdly high number and computationally impossible now.
Researchers and cryptographers are always trying to develop more effective means of breaking hash algorithms with targeted attacks. In order to locate preimages much more quickly than brute force, these techniques search for mathematical flaws in the fundamental structure of particular hash algorithms. If a flaw like this lowers the complexity (for example, from 2^n to 2^(n-k)), the hash function for preimage resistance is deemed broken.
You can also read Benefits Of SHA: Secure Your Data And Digital Transactions
Types of Preimage Attacks
Cryptographers distinguish between two types of preimage attacks:
- First Preimage Attack: The most direct form, where the goal is to find any input message (m) for a given hash output (h) such that H(m)=h. This scenario involves an attacker knowing a hash value and wanting to uncover the original data that produced it.
- The attacker is presented with an initial input message (m₁) and its hash H(m₁) in the second preimage attack (weak collision resistance). The objective is to identify an alternative input message (m₂) such that H(m₂)=H(m₁). This is frequently done maliciously, for example, to change a document without nullifying its hash or to forge a digital signature.
For a secure hash function, first preimage attacks are usually the most difficult to carry out, requiring about 2^n operations for an n-bit hash. Second preimage attacks are also challenging, usually involving about 2^n procedures.
Applications and Consequences
Preimage resistance is a critical property for the security of many cryptographic applications. If a hash function were vulnerable to a preimage attack, it would have serious implications and consequences:
- Password Storage: Systems store hashes of passwords, not the passwords themselves. If a database containing password hashes were breached, a feasible preimage attack would allow attackers to easily find the original passwords, compromising user accounts.
- Digital Signatures: The security of digital signatures relies on hash functions. If a preimage attack were possible, an attacker could forge a signature by finding a different document that produces the same hash as the original, allowing them to claim you signed something you didn’t.
- Message Integrity: Hash functions are used to verify data integrity. A successful preimage attack could allow an attacker to modify a file while keeping its hash the same, making the alteration undetectable.
- Blockchain and Cryptocurrencies: Hash functions are fundamental to blockchain security. A practical preimage attack would have catastrophic implications, potentially allowing the manipulation of transaction histories or the forging of blocks, leading to the theft of cryptocurrencies.
- Wider Implications: If a hash function is successfully attacked, all applications using that same function become vulnerable unless immediately upgraded, which could take years.
Preventing Preimage Attacks
Preventing preimage attacks is crucial for data security and integrity. Key measures include:
- Use strong cryptographic hash functions: It is recommended to use algorithms designed to be resistant against preimage attacks, such as SHA-256, SHA-3, or BLAKE2, instead of weaker ones like MD5 or SHA-1.
- Keep software up-to-date: Regularly updating system software and applying patches helps prevent vulnerabilities that attackers might exploit.
- Implement salted hashes: Adding random data (salt) to the input before hashing makes it significantly harder for attackers to guess or calculate the original input value.
- Use secure key management practices: For key-based authentication, ensure keys are stored securely and not unnecessarily shared.
- Implement access control policies: Limiting access to sensitive data to authorized personnel minimizes the risk of attackers gaining access through weak passwords or social engineering.
- Use a VPN: While not directly preventing a preimage attack on a hash function itself, a Virtual Private Network (VPN) can secure your identity and data by encrypting your internet connection and concealing your IP address, adding an extra layer of overall security, especially on public Wi-Fi.
The basic “one-way” character of a hash function is essentially questioned by a preimage attack, and its success calls into question the security presumptions of numerous digital systems.
Envision an extremely safe shredder that creates a unique, fixed-length barcode from any document. Reconstructing the original document from which the barcode originated is nearly hard due to preimage resistance. A preimage attack would be similar to attempting to use that barcode and find the original document that generated it by some ingenious method (rather than simply trying every document that may possibly exist). It would successfully breach the shredder’s “one-way” protection, so exposing the private data it was designed to safeguard.
You can also read What Is SegWit2x & Recommendations for Users During the Fork
