The Secure Hash Algorithm (SHA) is covered in this article along with its definition, works, types, features, applications, real-world scenarios, benefits of SHA, drawbacks, and future. Data security is the goal of the Secure Hash Algorithms (SHA) family of cryptographic hash algorithms. They are crucial for data encryption and decryption, protecting private data for both individuals and enterprises.
What is a Secure Hash Algorithm?

A cryptography method called a Secure Hash Algorithm (SHA) transforms plaintext into a message digest using a hash function. The National Security Agency (NSA) created it, and the National Institute of Standards and Technology (NIST) standardised it for use in digital signatures, message integrity checks, key generation, and authentication, among other applications.
Hashing is a one-way mathematical function, in contrast to encryption, which ensures privacy and confidentiality by using a shared key for both encryption and decryption. This makes it nearly impossible to convert hashed data back into the original message because the hash digest that is produced cannot be undone or “decoded” back into the original data. Hashing uses bitwise operations, modular additions, and compression functions to reduce input data of arbitrary length or size to a smaller, fixed-size, unintelligible form.
How SHA Works (Processing)?
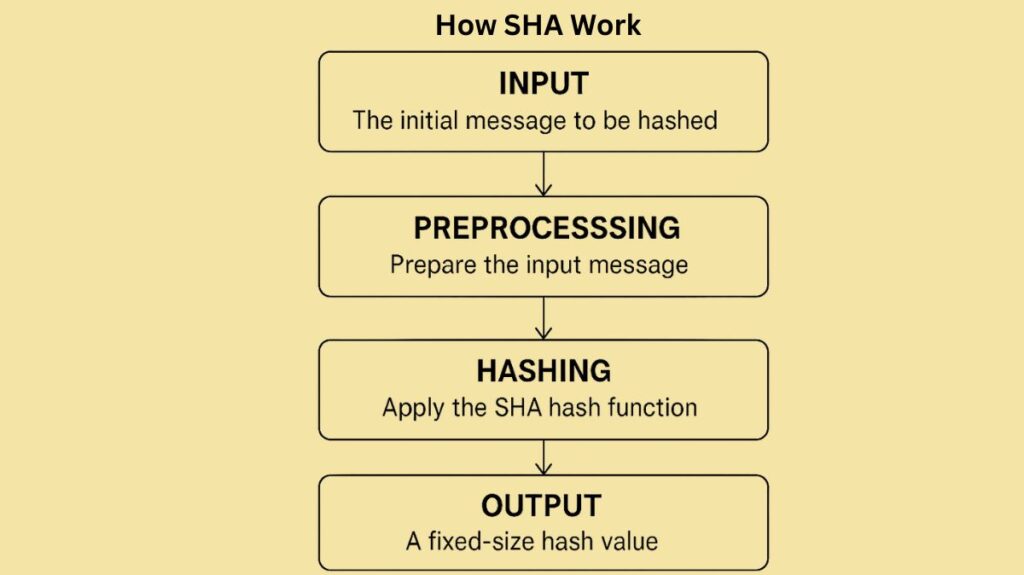
In order to convert an input message into a fixed-size hash value, SHA processing entails many crucial steps:
- Input: The initial message that has to be hashed is where the process starts. Take the phrase “Hello, World!” as an example.
- Preprocessing: In this stage, the input message is prepared. It can entail translating the message into a binary format and eliminating extraneous characters or punctuation. Padding the message to a predetermined length in SHA-1 also entails adding a 64-bit length representation to make it 512 bits, for example, from 448 bits.
- Hashing: The central step in the procedure, when the preprocessed input message is subjected to sophisticated and common mathematical techniques by the SHA hash function. These operations include of compression functions, bitwise operations, and modular additions. This entails 80 compute iterations utilising constant words and logical functions for SHA-1.
- Output: A fixed-size output, sometimes referred to as a message digest or hash value, is the end product. The input message is the only one with this hash value. A 256-bit (32-byte) hash value is produced, for example, using SHA-256.
Determinism is a key feature of SHA, which means that any computer or user will always output the same hash digest given the same input and hash algorithm. This characteristic is essential for confirming the accuracy of data. The message has been tampered with and should be deleted if the recipient calculates a different hash value for the same message than the one transmitted.
The Avalanche Effect is also supported by SHA functions. This implies that even a slight alteration to the input message will cause the hash value to change significantly and greatly. This feature makes it easier to see changes and stops hackers from disguising changes or interpreting the original message. While “heaven” (only a case change) yields “66da9f3b8d9d83f34770a14c38276a69433a535b,” hashing “Heaven” with SHA-1, for instance, yields “06b73bd57b3b938786daed820cb9fa4561bf0e8e,” indicating a significant change.
Types of Secure Hash Algorithms (SHA)
There are various varieties of Secure Hash Algorithms (SHA) with unique characteristics and security levels:
SHA-0
First released in 1993, this was the first 160-bit hash algorithm. An revealed “significant flaw” led to its withdrawal soon after release, and flaws have since made it outdated.
SHA-1
An NSA-designed 160-bit hash function that is similar to the previous MD5 method. Despite being extensively utilized in protocols such as TLS, SSL, PGP, SSH, IPsec, and S/MIME, cryptographic flaws had been found, including collision problems. By 2017, SHA-1 encryption certificates were no longer accepted by Microsoft, Google, and Mozilla, and it was no longer authorized for the majority of cryptographic applications after 2010. It was more vulnerable to brute-force assaults because of its small bit length.
SHA-2
SHA-256 and SHA-512 are two hash algorithms in this family that have varying digest length. Word sizes vary between both (SHA-512 uses 64-bit words, while SHA-256 uses 32-bit words). There are other truncated versions, such as SHA-224, SHA-384, SHA-512/224, and SHA-512/256. Because of their longer bit lengths (256-bit to 512-bit), SHA-2 functions are thought to be more secure than SHA-1, providing greater resistance against collisions and brute-force assaults. Since 2016, digital signatures and SSL/TLS certificates must adhere to the industry standard SHA-2, specifically SHA-256.
SHA-3
Previously called Keccak, SHA-3 was selected in 2012 following a public contest. Although it supports the same hash lengths as SHA-2 (SHA3-224, SHA3-256, SHA3-384, and SHA3-512), its internal structure differs greatly from that of the other members of the SHA family. Even though it was launched in 2015, most organisations were still switching to SHA-2, therefore it hasn’t yet become the industry standard. SHA-3 is quicker in hardware than SHA-1 and SHA-2, while being first thought to be slower in software. It is still improving.
Also Read About Transaction Scheduling & Transaction Executor In Blockchain
Features of secure hash algorithms
Fundamental security features are built into secure hash algorithms to protect data:
Pre-image Resistance
With just the hash value, this feature makes it computationally challenging and time-consuming for an attacker to identify the original input message. The one-way nature of SHA functions ensures this.
Second Pre-image Resistance
This feature makes it very challenging to locate another message that generates the same hash value if one message is known. This stops hackers from using a different password that produces the same hash in place of the original one.
Collision Resistance
The most demanding feature is collision resistance, which makes it very difficult for an attacker to identify two distinct inputs that result in the same hash value. The purpose of contemporary SHA versions, such as SHA-256 and SHA-3, is to drastically lower the likelihood of these collisions. Digital signatures could be compromised if they lack collision resistance because an attacker could produce a separate document that looks to have the same signature as the original.
Efficiency
Even with enormous volumes of input data, SHA algorithms may generate hash values rapidly due to their computational efficiency.
Uniqueness
For a variety of inputs, SHA aims to generate distinct hash returns. To lessen the likelihood of collisions, SHA-2, for instance, is made to give each hash digest a distinct value.
Also Read About Understanding Cryptography Mechanisms In The Blockchain
Benefits of SHA
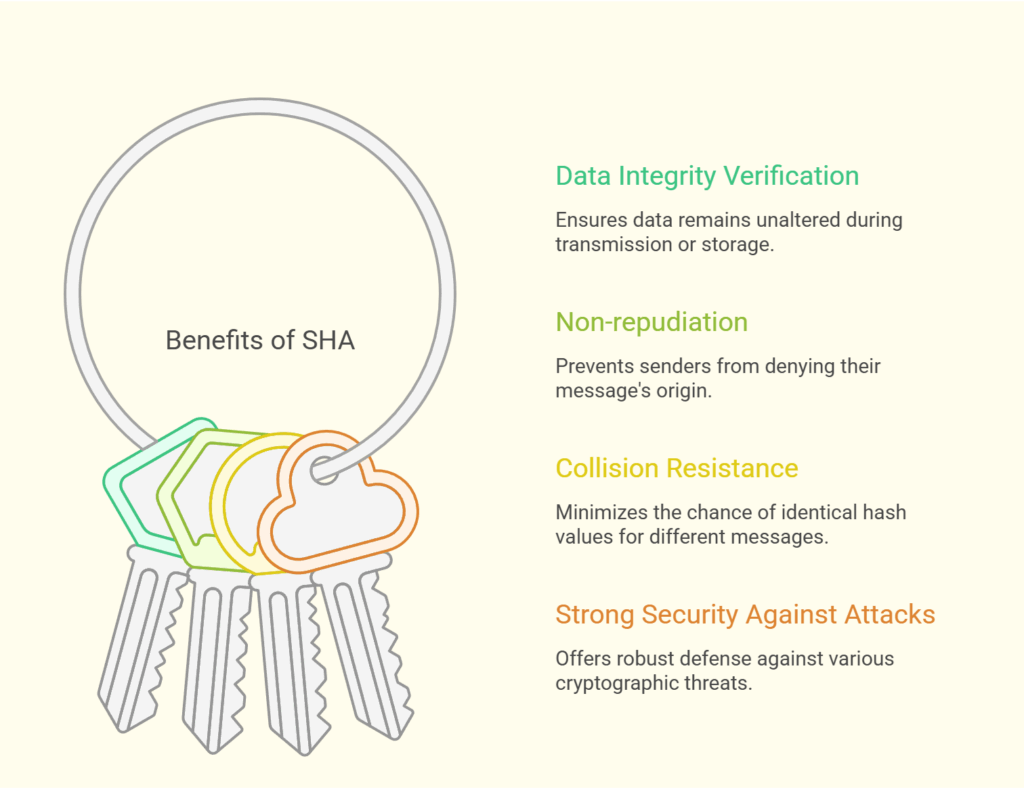
In cryptography, secure hash algorithms provide a number of noteworthy benefits.
- Data Integrity Verification: To make sure that electronic documents, messages, and information haven’t been altered or tampered with during transmission or storage, SHA hash functions are frequently employed to confirm data integrity and authenticity. At the recipient’s end, this is accomplished by recalculating the hash value and comparing it to the original.
- Non-repudiation: It is challenging for a sender to deny sending or encrypting a communication since hash values are determined methodically based on message content.
- Collision Resistance: For example, SHA-256 is designed to be collision-resistant, which lowers the likelihood of the same hash value and guarantees distinct digests for various messages. Because of this, it is very challenging for attackers to produce a malicious file that imitates a valid one’s hash.
- Strong Security Against Attacks: SHAs make it very difficult for attackers to use brute-force assaults to expose the plaintext of hash digests; cracking these attacks can take years or even decades, squandering the time and resources of attackers. Additionally, they are made to withstand cryptographic attacks such as pre-image and second pre-image.
Drawbacks of SHA
Notwithstanding their benefits, SHA algorithms do have certain drawbacks:
- Consistency is a benefit, but the constant hash value size (e.g., 32 bytes for SHA-256) can be wasteful for very long messages and occasionally necessitates the use of many hash functions in a chained fashion, which can be laborious.
- Key Management (for MACs): Applications such as Message Authentication Codes (MACs) may be vulnerable to security breaches and unauthorised access if the secret key used for hashing is misplaced, stolen, or misused.
- Older Version Vulnerabilities: Older versions, such as SHA-1, are deprecated because of known cryptographic flaws, such as collision attacks.
- Performance trade-offs: Newer versions, such as SHA-3, are quicker in hardware and are still becoming better, but they were first thought to be slower in software than SHA-2, although being usually more efficient.
Applications for Secure Hash Algorithms
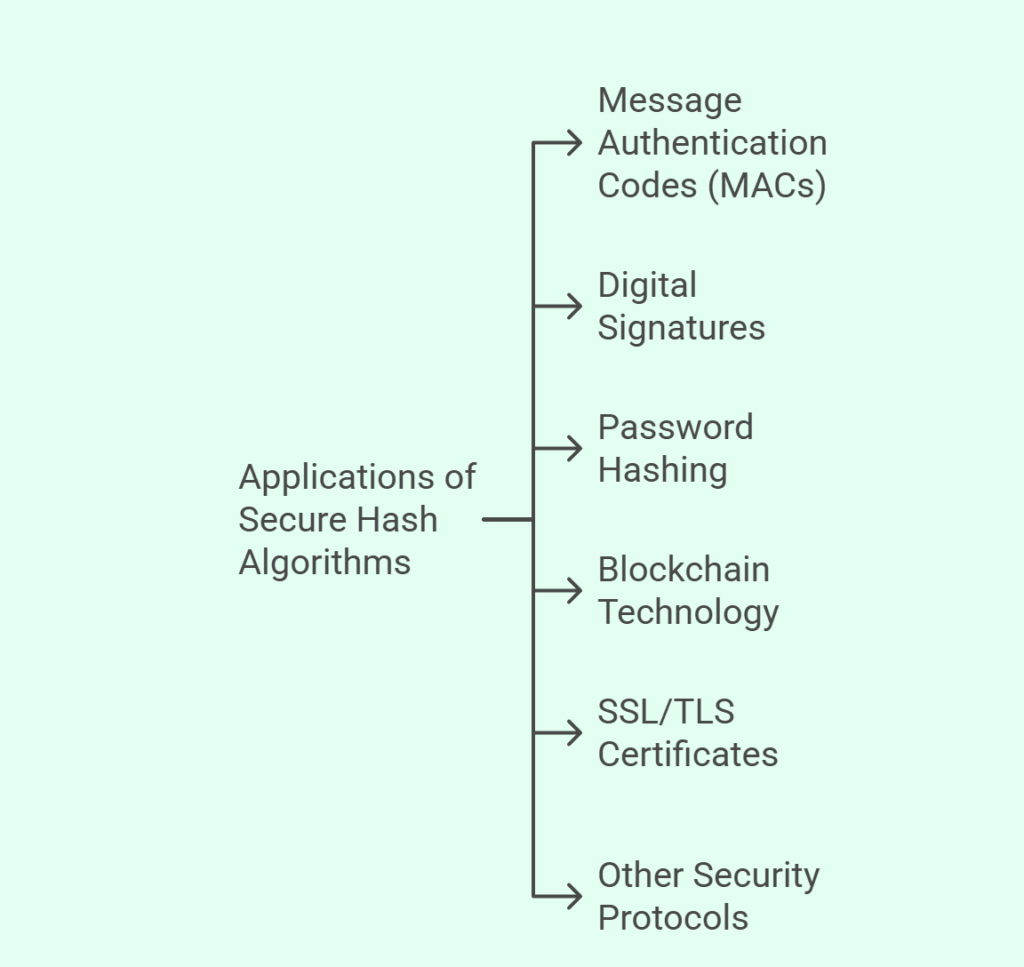
SHA functions are extensively used in many different security domains:
- Message Authentication Codes (MACs): By appending a SHA hash to the input message prior to transmission to the receiver, SHA is commonly utilized to guarantee message integrity. To confirm integrity, the recipient can then recalculate the hash.
- Digital Signatures: To confirm the legitimacy and identity of electronic documents, including emails, private reports, and project data, SHA is used in conjunction with digital signatures. The document is delivered with its hash value, which is calculated using SHA and signed with a private key.
- Password Hashing: SHA is an essential component for password management and storage in online apps and websites. By utilizing SHA to hash passwords and storing them in databases, the risk of cyberattacks and security problems from database leaks is decreased because it is difficult to figure out the original password, even if the database is compromised.
- Blockchain Technology: SHA-256 is essential to the mining process of cryptocurrencies like Bitcoin because it helps solve challenging mathematical puzzles that validate and add new transactions to the blockchain.
- SSL/TLS Certificates: To guarantee their legitimacy and integrity during secure connection, all SSL certificates on the Internet must be hashed using a SHA-2 method.
- Other Security Protocols: SHAs are used by programs like IPSec (Internet Protocol Security), SSH (protect Shell), and S-MIME (Secure / Multipurpose Internet Mail Extensions) to protect communications.
Also Read About Benefits Of Bitcoin, Disadvantages And Characteristics
Real-Life Scenarios
Take a look at these instances of SHA in action:
Transmission of Secure Emails
Corporation ABC wishes to transmit MNC important contract details. ABC uses their private key to digitally sign the email content, calculates the email’s hash value using SHA-256, and attaches it as a separate file. Using the same SHA-256 function, MNC recalculates the hash value upon receiving the email and compares it to the hash that is attached. MNC is guaranteed that the email is whole and unaltered if they match.
Identifying Confidential Message Tampering
Let’s say A uses SHA-256 for secure communications and integrity while sending B sensitive information for a top-secret project. C recalculates the hash value of the altered message and delivers it to B if a third party, C, intercepts it, modifies the content, and inserts malware. After receiving the message, B verifies it again and finds a discrepancy between C’s hash and a newly computed one, discarding the malicious message. This illustrates how useful SHA is in protecting private data in real-world situations.
Also Read About Explain Digital Signature Algorithm Definition, Advantages
The Future of Hashing
The industry standard for hashing algorithms at the moment is SHA-2. Even though NIST published SHA-3 in 2015, SHA-2 is still the industry standard. This is partially because SHA-2 was still seen as being extremely safe when SHA-3 was published, and the majority of organisations were in the process of switching from SHA-1 to SHA-2. In contrast to SHA-1 and SHA-2, SHA-3 is quicker on hardware and keeps getting better every year, despite its original perception of being slower in software. As SHA-2 becomes less secure or obsolete, the industry is probably going to switch to SHA-3 later.
Consider a secure hash algorithm as a digital data fingerprinting method. A hash value is a way to uniquely identify a piece of digital data, just like a fingerprint may identify a person. It would be like a person’s fingerprints abruptly and drastically changing if even the smallest bit of information changed. This makes it clear right away that something is wrong, even if you are unable to identify the exact change or how it occurred. Importantly, even if it’s simple to make a fingerprint from a person, you can’t use that fingerprint alone to reconstruct the person.
