Blockchain DDoS attack
DDoS (Distributed Denial of Service) attacks flood a website, application, server, or network with requests or traffic from multiple sources to disable it. Use its resources to disable or severely impair the target’s ability to execute legitimate transactions or perform its intended activities.
How DDoS Attacks Work
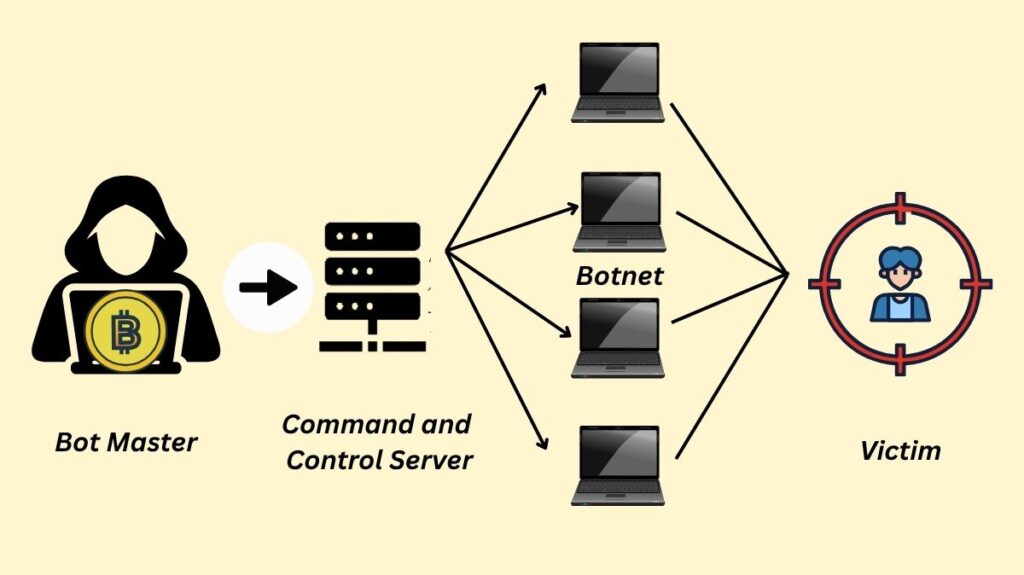
Using several compromised computer systems as sources of attack traffic allows Blockchain DDoS attacks to be effective. These compromised machines are known as bots or zombies, and they can be computers, Internet of Things devices, or other networked resources. These bots come together to form a botnet, which is managed remotely by an attacker who instructs each bot.
Botnet attacks can overburden a server or network since each bot searches the target’s IP address. This traffic drains the target’s processing power, memory, and bandwidth, preventing authorized users from accessing the service. Blockchain DDoS attacks, in contrast to other cyberattacks that take use of weaknesses to compromise systems, frequently flood endpoints using common network connection protocols like HTTP and TCP.
By using IP spoofing, which involves forging fictitious source IP addresses for packets sent from the botnet, attackers frequently hide the origin of their attacks. By using a technique known as “reflection,” attackers can even get the fraudulent traffic to look as though it came from the victim’s own IP address. A botnet is not necessary for every Blockchain DDoS attack; some maliciously take advantage of the regular functions of uninfected devices.
Hackers can use Blockchain DDoS attacks to distract from data theft or network malware.
Types of DDoS Attacks
Based on their strategies and the network architecture they target, Blockchain DDoS attacks are categorized, frequently using the layers of the OSI (Open Systems Interconnection) model. An attacker may respond to countermeasures by alternating between one or more attack vectors.
Common Blockchain DDoS attack types include the following:
Flooding the Network:
- The memory pool, or mempool, can be overloaded with zero-fee transactions by attackers. Resources must be used by the system to download and examine these even if they are refused.
- As nodes download and check the blocks before rejecting them, distributing a lot of faulty blocks also wastes network resources.
- It is possible for malicious individuals to generate numerous replicator identities and bombard the network with false evidence.
- When too much data is sent to one node, it can become overloaded and stop handling regular transactions.
Smart Contract Vulnerabilities:
- Smart contracts can be directly the target of denial-of-service attacks.
- An ill-conceived smart contract might be used, for instance, to devour all of the publishing nodes’ resources in endless cycles.
- DoS with Block Gas Limit: To go past the gas limit and render the network inoperable, attackers can either stuff blocks with too much data or create unbounded activities inside contracts.
- DoS with Unexpected Revert: In smart contract auctions, a malevolent bidder may purposefully take the lead and then make sure that refunds to their address never happen, thereby stopping the auction.
- Insufficient Gas Griefing: By taking advantage of the Ethereum Virtual Machine’s (EVM) gas forwarding limit, an attacker can submit transactions with insufficient gas when a contract makes a sub-call, resulting in transaction failure.
Targeting Centralized Infrastructure
- Targeting centralized parts or services that underpin blockchain applications, like cryptocurrency exchanges, is possible. Such attacks have forced the shutdown of numerous cryptocurrency exchanges supported on blockchain technology.
Application Layer Attacks (Layer 7):
- Because web pages are created and provided in response to HTTP requests at the application layer, these attacks seek to deplete the target’s resources there.
- The cost of processing a single HTTP request is high for the server but low for the client.
- Similar to continually pushing refresh on numerous computers, HTTP flood is a common scenario when a huge number of HTTP requests overwhelm the server. Since it can be challenging to distinguish malicious traffic from normal traffic, these are challenging to guard against.
Protocol Attacks (Layers 3 & 4):
- Exploiting flaws in Layer 3 and Layer 4 of the protocol stack, these attacks also referred to as state-exhaustion attacks use up server resources and network devices such as firewalls and load balancers.
- SYN flood: Sending multiple TCP “Initial Connection Request” (SYN) packets with fake source IP addresses is one way to take advantage of the TCP handshake. After responding to each, the target uses up all of its resources but never gets the last acknowledgement.
- Smurf attack: Involves using a spoof IP to match the victims to an IP broadcast network and delivering an ICMP echo request. The victim’s IP address is overwhelmed by hundreds or thousands of networked devices responding to it.
Volumetric Attacks:
- By using up every bit of bandwidth that is available between the target and the wider Internet, these attacks aim to cause congestion.
- Amplification or botnets are used to send large amounts of data.
- DNS Amplification: When an attacker uses a spoof IP address (the victim’s) to send a DNS lookup request to an open DNS server, the server responds with a lengthy response.
- UDP floods: Fake User Datagram Protocol (UDP) packets are sent to the ports of a target host, leading the host to spend resources searching for applications that aren’t there and sending “destination unreachable” warnings.
- ICMP floods (Ping flood attacks): Attack targets by flooding the server with ICMP echo requests from several spoof IP addresses.
Multivector Attacks:
- In order to maximize damage and make mitigation efforts more difficult, these attack paths are exploited concurrently or alternated. An HTTP flood (targeting layer 7) combined with DNS amplification (targeting layers 3/4) is one example.
Impact of DDoS Attacks
A successful Blockchain DDoS attack may result in serious repercussions, such as:
Service Unavailability: Access to services and transactions are blocked to legitimate users.
Resource Exhaustion: It drains the target’s memory, bandwidth, and processing power.
Economic Losses: Due to outages, companies that depend on internet services may suffer large financial losses as well as harm to their reputation.
Disruption of Trust: Frequent attacks might lower consumers’ trust in a platform’s security.
Identifying and Mitigating DDoS Attacks
Blockchain DDoS attacks are most noticeable by sudden website or service slowdown or unavailability. But legitimate traffic surges can also cause this, making it hard to recognize. Traffic analytics software can detect anomalous traffic patterns, an unexplainable rise in page requests, a flood of traffic from users with a certain behavioural profile, or questionable IP traffic. Inexplicable issues, timeouts, or network-shared service slowdowns are indicators.
Blockchain DDoS attacks are hard to detect and stop because they are distributed and cannot be stopped by blocking one source. Additionally, the signs and symptoms sometimes resemble real traffic surges.
A layered solution is frequently necessary, and organizations can employ a variety of mitigation strategies:
Risk Assessments: Assessing vulnerabilities in software and hardware on a regular basis aids in determining the best mitigation approach.
Traffic Differentiation: It’s critical to distinguish harmful traffic from valid traffic.
Blackhole Routing: Directing all traffic, whether malicious and lawful, to a null route and dropping it there. This prevents the attack, but it also prevents everyone from using the service.
Rate Limiting: Setting a time limit on how many requests a server will allow in a given amount of time. Even though it’s helpful, complicated attacks frequently require more than just this.
Web Application Firewalls (WAFs): To detect and prevent Layer 7 attacks, requests are filtered according to rules.
Anycast Network Diffusion: To absorb and control attack traffic, it is dispersed among a network of dispersed servers.
Content Delivery Networks (CDNs): By distributing traffic and expanding capacity, requests can be forwarded to other servers in the event that one becomes overloaded.
Load Balancing: To maximize availability and divert traffic from overloaded servers, network traffic is divided across several servers.
Traffic Scrubbing: Anomaly detection and authentication are two methods used by specialised networks or services to filter harmful data.
Secure Software Development: For smart contracts in particular, careful design and testing are essential to preventing exploitable flaws.
Transaction Fees (Gas): Gas fees keep unscrupulous users from implementing resource-consuming contracts or overflowing the network with free transactions in blockchain networks like Ethereum.
Decentralization and Distribution: It is more difficult to successfully target a single server due to the distributed structure of blockchain. Resilience is increased when the number of heterogeneous nodes is increased.
Consensus Mechanisms: Economic disincentives or computational costs are used by Proof of Work (PoW) and Proof of Stake (PoS) systems to discourage flooding attacks. Helix and PBFT protocols use committee reelection. Because Proof of Authority (PoA) uses verified nodes and creates blocks on a regular basis, it can withstand DoS attacks.
Layer 2 Solutions: Security and performance can be improved by solutions like sharding (for parallel processing) and the Lightning Network (for Bitcoin), albeit sharding must be implemented carefully to avoid single-shard takeover.
Examples of DDoS Attacks
- Yahoo and eBay were taken down by “Mafiaboy” in 2000, one of the earliest Blockchain DDoS attacks.
- Netflix, PayPal, Amazon, GitHub, and other important websites and services were brought down by a large Blockchain DDoS attack that attacked Dyn in 2016.
- The largest attack in history occurred in February 2020 against Amazon Web Services (AWS).
