Ethash meaning
The Ethereum network mainly uses the Proof-of-Work (PoW) algorithm Ethash to secure its blockchain and verify transactions. It requires miners to solve mathematical riddles in order to validate transactions and add them to the network. This procedure is a crucial component of Ethereum’s ecosystem since it guarantees that transactions are validated and added to the blockchain in a decentralized fashion.
Origin and Development
- Ethash is an improvement and replacement for the Dagger-Hashimoto Ethereum algorithm. Ethash’s first iteration was based on Dagger-Hashimoto, which was created by fusing Vitalik Buterin’s Dagger algorithm with Thaddeus Dryja’s Hashimoto algorithm.
- It was created with three primary requirements in mind: full chain storage, light client verifiability, and ASIC resistance. Dagger-Hashimoto used Hashimoto’s method for proving I/O capacity, but instead of using the blockchain as a data set, the Dagger algorithm produced a unique 1GB data set.
- To mitigate the vulnerabilities of Dagger’s shared memory hardware advantages, the dataset used to query blocks was made semi-permanent and refreshed at predefined intervals.
Core Mechanics-How it Works
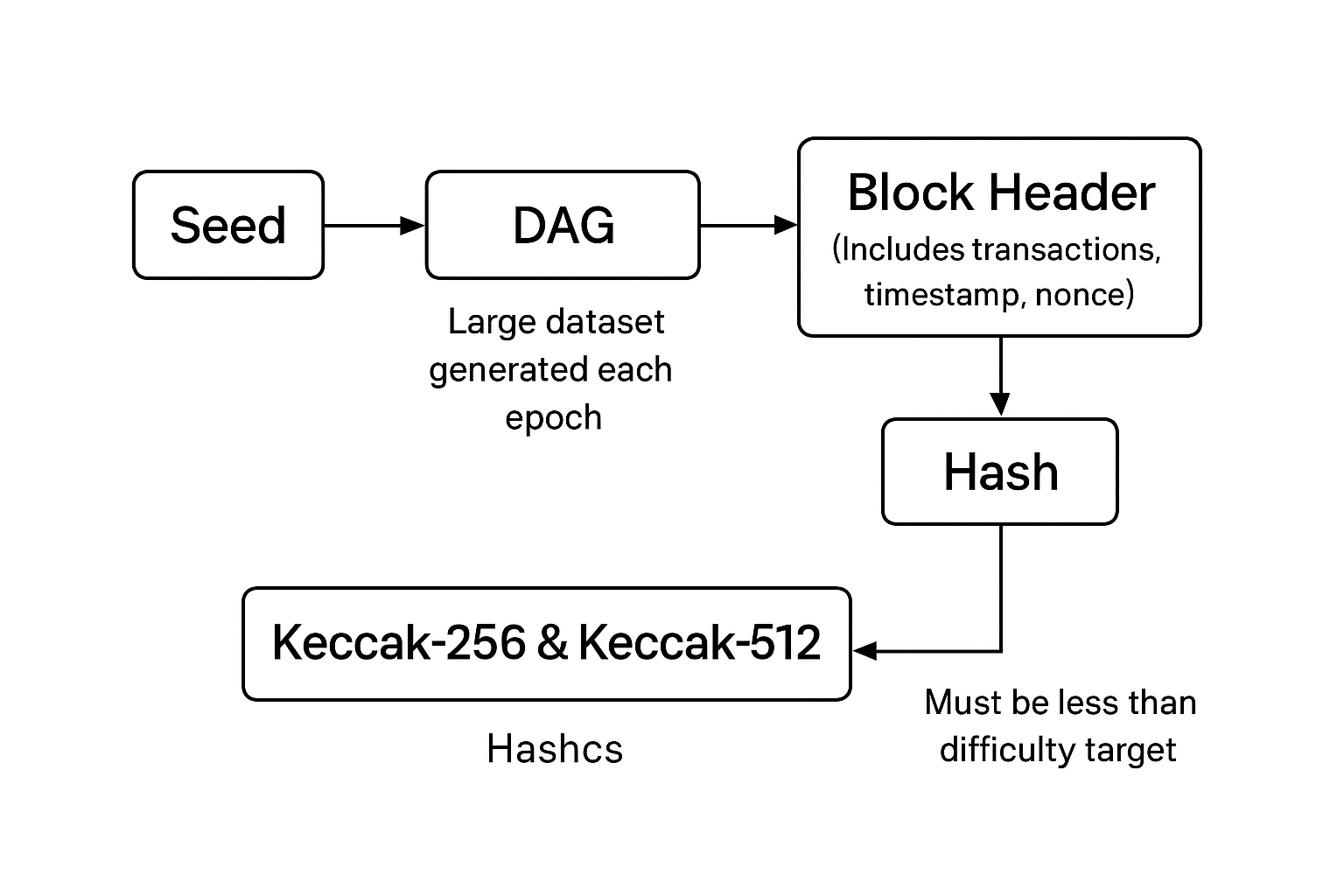
The DAG (Directed Acyclic Graph) is a sizable dataset that Ethash uses to function. The “epoch” in which this DAG is updated is every 30,000 blocks, or roughly every five days, and is created using a “seed” that is taken from recent block headers. The size of the DAG increases with time, starting at about 1GB and rising by about 520KB every epoch. To do calculations effectively, miners need to load this multi-gigabyte DAG into the memory of their mining hardware, notably the GPU’s VRAM. The “Keccak-256” and “Keccak-512” hash algorithms are used in the algorithm. Although the Keccak version utilized by Ethereum is occasionally referred to as “sha3_256” and “sha3_512,” it is not a normal SHA-3 hash algorithm because SHA-3 is a member of the larger Keccak cryptographic primitive family.
Also Read About Web3.shh: Decentralized Messaging With Whisper On Ethereum
In order to solve cryptographic riddles, miners repeatedly hash a block header that contains random DAG elements as well as transactions, a timestamp, and a nonce. Finding a hash value below a predetermined threshold value known as difficulty is the aim. In order to control the block mining pace, the Ethereum network dynamically modifies this difficulty, raising it when the block discovery rate is high and lowering it when miners are having trouble mining blocks.
Important Design Guidelines
- ASIC Resistance: Being ASIC-resistant was a key design objective for Ethash, which means that it makes it challenging for specialised hardware, such as Application-Specific Integrated Circuits (ASICs), to obtain a sizable mining advantage. By making mining available to a larger population using consumer-grade technology, this strategy encourages decentralization.
- Memory-Hardness: Ethash’s memory-hard PoW algorithm allows it to withstand ASIC attacks. In addition to raw processing power, it needs a large quantity of RAM and memory bandwidth. While ASICs usually have small memory caches and are less effective for memory-intensive operations, GPUs are well-suited for Ethash mining due to their huge VRAM and parallel processing capabilities.
- GPU-Friendly: GPU mining is the ideal choice for Ethash because it is memory-hard. Due to GPU miners’ far superior efficiency, CPU mining is no longer economical for cryptocurrencies based on Ethash. In general, AMD GPUs perform better than Nvidia devices in the same category.
Also Reda About What Is ewasm Ethereum WebAssembly In Blockchain
Ethash Mining Process and Tools
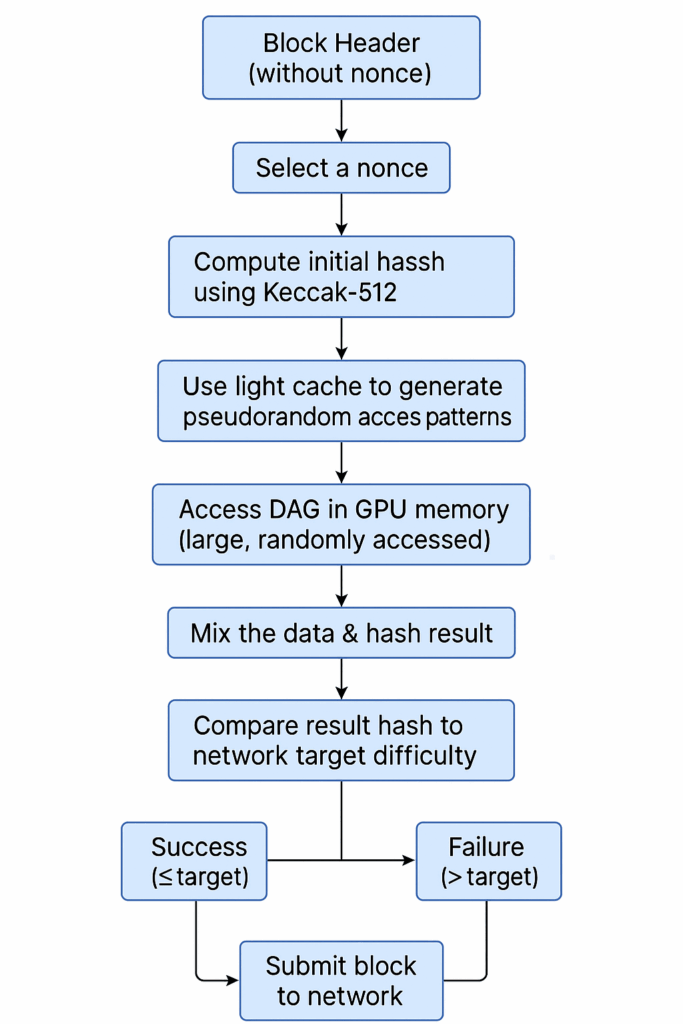
- Start by adding a selected nonce to the block header.
- To generate an intermediate value, hash them.
- To decide which sections of the DAG to read, use the cache.
- Read a large number of arbitrary DAG sections into GPU memory (memory-hard step).
- Create a final hash by combining all the data.
- Examine the hash in relation to the goal network difficulty:
- The block is mined and broadcast if it is valid (hash ≤ goal).
- If not, repeat with the next nonce.
- To maximize performance, miners can utilize a variety of tools, such as Ethminer, Claymore, and PhoenixMiner. The Ethereum team created Ethminer, which is compatible with the majority of Ethash-based cryptocurrencies.
- Despite usually needing minor fees (about 1-2% of income), pool mining is also possible and frequently advised for well-known Ethash-based coins, especially for those with subpar equipment.
- The price of the cryptocurrency being mined, hash rate, and electricity expenses are some of the variables that affect mining profitability.
- In addition to gas expenses (transaction fees) and extra rewards for adding ‘uncles’ (ommer) to the block, miners on Ethereum receive a flat block reward of three ether for each block they mine.
Benefits and Security
- By requiring a large amount of memory and processing power, Ethash strengthens Ethereum’s security by discouraging malevolent actors and making blockchain manipulation resource-intensive.
- The design is essential for network scalability and accessibility since it enables “light clients” to rapidly validate blocks without storing the complete big DAG.
- The network is protected against attacks such as 51% attacks by the combination of the difficulty adjustment mechanism and computing effort.
Coins Using Ethash
- The Ethereum network is undoubtedly the most well-known Ethash-based blockchain.
- Ethereum Classic (ETC), which runs separately but uses the same mining algorithm, also uses Ethash. This allows miners to move between networks according to profitability.
- Although only a small number of ERC-20 tokens can be mined, many other cryptocurrency projects are built on Ethereum’s technical standard ERC-20 and de facto use Ethash as a proof-of-work algorithm.
- Independent cryptocurrencies like as Metaverse (ETP), Expanse (EXP), Musicoin (MUSIC), Ellaism (ELLA), Elementrem (ELE), and DaxxCoin (DAXX) each have their own Ethash-based blockchains and are minable.
Present and Prospective Situation
- For many years, Ethereum’s security was based on Ethash. But in September 2022, Ethereum underwent “The Merge” to switch to a Proof-of-Stake (PoS) consensus system. This indicates that Ethash is no longer used on the Ethereum mainnet.
- Despite this shift, other Ethash-based cryptocurrencies and Ethereum forks like Ethereum Classic that still use the Proof-of-Work paradigm also use Ethash (or its variations). For older GPUs with limited VRAM, the increasing DAG size for these chains remains a challenge.
Ethash is essentially a digital memory puzzle in which miners must swiftly access and interpret a sizable, continuously expanding library of data (the DAG) in order to locate the nonce, or right answer, and append a new chapter (block) to the blockchain. This design ensures that more common “researchers” (GPU miners) can participate and contribute to the integrity of the network by making it difficult for specialised “super-computers” (ASICs) that are good at brute-force computations but lack the requisite memory agility.
Ethash Parameters
| Parameter | Value (approx) |
|---|---|
| Epoch length | 30,000 blocks |
| DAG growth per epoch | ~520 KB |
| Initial DAG size | ~1 GB |
| DAG size as of 2022 | > 5 GB |
| Cache size | ~16 MB (grows too) |
| Hash function | Keccak-256 & Keccak-512 |
Summary Table
| Feature | Ethash |
|---|---|
| Algorithm type | Proof of Work |
| Focus | Memory-hard, ASIC-resistant |
| Main dataset | DAG (Directed Acyclic Graph) |
| Hardware-friendly to | GPUs |
| Used in | Ethereum (pre-Merge), Ethereum Classic |
| Strengths | Decentralization, ASIC-resistance |
| Weaknesses | High power use, growing DAG size |
