How to prevent sybil attack in blockchain
Verifying identities, examining network behavior, and raising the price of fabricating identities are all necessary to stop Sybil Attacks. Since no one method is infallible, it is frequently advised to combine several steps for maximum protection.
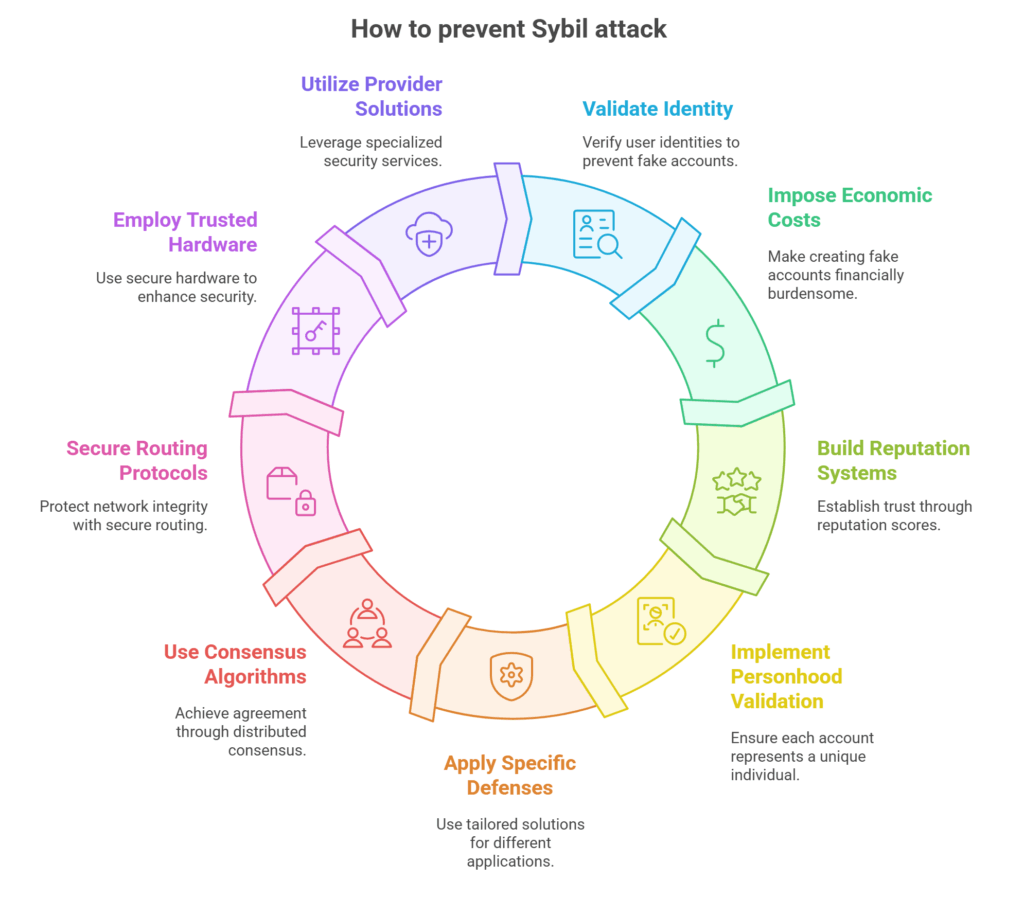
The following are important preventative strategies:
Identity Validation
- Proof of Identity: Sybil attacks can be avoided by implementing measures that confirm users’ actual identities, such as social security numbers, email verification, or integration with reliable identity suppliers. For authorized users, these could be expensive or inconvenient.
- Direct Validation: A central authority or an existing member confirms new network members, maybe requesting information such as their real name or IP address. While accountability is provided, anonymity may be compromised.
- Indirect Validation: An experienced member confirms with other members, who can then confirm with newcomers. Because the established entity has validated the verifiers, new hires are trusted. Because current validators may only approve people they know, this strategy may result in centralization.
- Identity Proxies: Real-world applications may employ techniques such as IP address, credit card, or phone number verification. These can be get around, though, via spoofing or by acquiring several proxies.
- Proof of Ownership (PoO): This approach uses distinct pseudonyms produced by an Enhanced Privacy Identity (EPID) signature and needs participants to be in a Trusted Execution Environment (TEE). Malicious actors find it more difficult to reset their epoch register for many usage when these pseudonyms are used to track whether multiple proofs originate from a single participant.
Economic Costs (Work/Stake Proof)
- Cost of Identity Creation: Making it expensive to fabricate an identity discourages attackers. Since numerous identities can support security and privacy, the goal is not to just create new ones, but to make it impossible to run multiple phoney identities at the same time.
- Bitcoin’s security method, known as Proof of Work (PoW), makes sure that adding blocks or transaction records to the blockchain necessitates a substantial amount of processing power. Because miners compete to solve challenging mathematical problems, attackers find it very costly to set up and run phoney nodes. Mining a single Bitcoin block might cost about $50,000 in electricity and equipment in 2025.
- As of 2025, Bitcoin’s mining capacity requires $20 billion in hardware and billions in energy, making a 51% attack nearly impossible. Bitcoin’s massive hash rate, spread across millions of miners, makes coordinated attacks nearly hard.
- No fake prizes: Miners receive 6.25 Bitcoins by following network rules. The tens of thousands of nodes immediately reject incorrect or fake blocks, thus there is no reward for lying.
- Proof of Stake (PoS): Ethereum and other blockchains use PoS, which requires users to “stake” a sizable sum of money (for example, 32 ETH, or around $48,000) in order to operate a node. It is not economically appealing to run numerous malicious nodes because of this high price barrier.
- Paid Verification (such as Twitter Blue): Elon Musk’s Twitter Blue subscription, which costs $8 a month to display a blue checkmark, was designed to deter bots by creating a financial barrier and requesting credit card information and phone numbers. As a result, maintaining sizable bot armies became much more costly for hackers.
Reputation and Trust Systems / Social Graph Analysis
- Analysing User Behaviour: To find potentially harmful entities, reputation systems monitor user interactions and behaviour.
- Analyzing Social Graphs: Sybil attack patterns can be found by looking at the relationships between individuals in a social network. In order to limit harm, methods such as Sybil Guard, Sybil Limit, Advogato Trust Metric, and Sybil Rank assess connection features.
- Hierarchical System: New Sybil nodes can be stopped from carrying out significant Attacks by putting them under suspicion and giving more authority to established, reliable nodes.
- If an attacker controls a significant portion of the network, these techniques may be vulnerable and computationally costly.
Personhood Validation
- This entails utilising techniques like behavioural biometrics or CAPTCHAs to confirm a user’s “personhood” in order to differentiate humans from bots.
- It can validate physical presence at a “pseudonym party” to enforce a “one-per-person” rule without requiring actual identity information. In order to guarantee that every human participant has one vote, this is suggested for permissionless blockchains.
Application-Specific Defenses
- Adjusting defences to meet the needs of certain applications.
- Token systems in wireless sensor networks or unique identifiers are two examples.
- Certain algorithms, such as I2P’s Kademlia implementation, Whānau for distributed hash tables, and SumUp and DSybil for content recommendation/voting, are made to be Sybil-resistant.
Distributed Consensus Algorithms
- Data tampering is made more difficult by using strong consensus procedures, which guarantee that all participants agree on the system’s state.
- Permissioned Blockchains: Since authors are not anonymous, Sybil attacks can be avoided by requiring background checks on all participants.
- ByzCoin: Using Pow, membership is defined without the Sybil vulnerability.
- Random Validator Sampling (Shading): Security is dispersed in shaded networks, which are systems that are separated into parts. To solve this, Ethereum selects validators at random from each shard. One shard cannot be controlled until more than 50% of the nodes in that shard endorse it.
- Expanding Network Size in PBFT: Sybil Attacks can be lessened in Practical Byzantine Fault Tolerance (PBFT) networks by expanding the number of nodes.
Secure Routing Protocols / Dynamic Adjustment of Node Connections
- By putting in place safe and dependable routing, traffic hijacking is avoided and data is guaranteed to go through authentic nodes.
- By changing the connections between nodes, an attacker can avoid encircling a node and controlling its network view for long stretches of time.
Trusted Hardware Components / Trusted Execution Environments (TEEs)
By demonstrating immutable uniqueness within a network, TEEs such as those based on Intel SGX can successfully thwart Sybil attacks. In order to manage various proofs from a single participant, PoET additionally uses TEEs to create distinct pseudonyms and build trust among nodes.
Provider-Specific Solutions (e.g., Imperva)
- Technologies to defend against Sybil attacks and other risks are provided by cybersecurity firms such as Imperva, especially for blockchain and cryptocurrency investments:
- Web Application Firewall (WAF): Prevents harmful bots, verifies the legitimacy of user requests, and shields web applications from cyberattacks.
- DDoS Protection: Protects foundation and bitcoin exchange websites.
- Advanced Bot Protection: With an Account Takeover module for login security, it guards against business logic Attacks via a variety of access points, including as websites, mobile apps, and APIs.
- Within the application runtime environment, Runtime Application Self-Protection (RASP) offers real-time threat detection and prevention.
- API Security: API endpoints are automatically protected.
- Attack Analytics: Identifies attack campaigns and patterns using machine learning.
- Provides access and control over third-party JavaScript code to prevent supply chain fraud and client-side attacks.
Decentralized systems are at risk from Sybil attacks, which allow one person to assume the identity of numerous individuals and influence system choices, spread false information, or bring down infrastructure. Identity verification, economic disincentives, and inventive design, like Twitter’s paid verification and Bitcoin’s Proof of Work, can protect networks.
Types of Sybil Attacks
Sybil attacks were divided into two primary groups by John R. Douceur:
Direct Sybil Attack
In order to disrupt the system, the phoney nodes (run by a single hacker) directly target the legitimate users and interact with them as actual participants. It’s comparable to a scammer creating 100 phoney profiles on a review site to use negative evaluations to ruin a rival product. Since the phoney identities blend in so well, the honest users have no suspicions.
Example:
A fraudulent seller creates 100 fictitious buyer accounts (hiding their real location) in order to launch a Direct Sybil Attack on the product of one of Amazon’s rivals. They all write one-star reviews, which reduces the product’s rating from 4.5 to 2. The genuine vendor loses $10,000 in weekly sales as a result of customers ignoring the product. By gaining direct access to the reputation system, the copycat nodes (accounts) deceived Amazon’s algorithm into showing a lower score.
Indirect Sybil Attack
Malicious nodes do not target innocent users directly in this more subtle scenario. As an alternative, they attack the network by taking control of a “middleman node” a reliable device or account. This corrupted intermediate deceives the legitimate users, making it more difficult to detect the attack.
Example:
50 phoney IoT devices are created by a hacker using a botnet in a smart home network. When a Wi-Fi router (the intermediary) receives too many bogus commands from these fakes, it sends erroneous signals to a real smart thermostat, causing it to fail and raise energy costs. The router, not the phoney nodes, was the one that tricked the honest nodes.
