This blog discusses the following topics: what a Sybil attack is in blockchain, its history, how it works, problems and threats it poses, Sybil Attack Detection, and examples.
What is a Sybil Attacks in blockchain?
Peer-to-peer (P2P) networks are vulnerable to a cybersecurity issue known as a Sybil Attacks, in which a single attacker concurrently establishes and manages several false identities in an attempt to obtain an excessive amount of power and influence over the network. Often called “Sybils” or “sockpuppets,” these fictitious identities give the impression to outside observers that they are genuine, one-of-a-kind users. Subverting reputation systems and gaining majority influence to commit malevolent acts is the main goal of this attack.
History of Sybil Attacks
Flora Rheta Schreiber’s 1973 novel Sybil follows dissociative identity disorder sufferer Sybil Dorsett (Shirley Ardell Mason), who had 16 identities. From the novel, “Sybil Attack” comes.
In his 2002 work, “The Sybil Attack,” Microsoft Research researcher John R. Douceur introduced it as a cybersecurity term at the International Workshop on Peer-to-Peer Systems. It was created by Brian Zill at Microsoft Research in 2002 or earlier. According to Douceur, this is a serious flaw in decentralized systems, especially P2P networks, because users share control and are therefore susceptible to attackers who create several bogus identities in order to exert unwarranted influence. With the rise in popularity of P2P technologies like BitTorrent and early blockchain concepts, this study was a “eye-opener” for network security.
Sybil attacks have changed from a hypothetical danger to a real cybercrime since 2002:
Early Days (2000s)
In the early 2000s, P2P file-sharing networks such as BitTorrent and Napster had problems akin to Sybil, in which phoney nodes disseminated damaged data, disrupting the system.
Blockchain Era (2010s)
Cryptocurrencies like Ethereum and Bitcoin were targeted heavily, including 51% and double-spending Sybil Attacks.
Social Media Surge (2010s–2020s)
Phishing accounts that disseminate false information, manipulate polls, or advertise phoney goods were used to launch Sybil attacks on sites like Reddit and Twitter (now X).
IoT and Web3 (2020s)
By 2025, these attacks use the growth of P2P technology to target decentralized applications like NFT markets and smart home networks (such as fake IoT devices).
Also Read About Swarm Blockchain: Decentralized Marketplaces & Communities
How Sybil Attacks Work
Decentralized systems, in which users (or “nodes,” such as computers or gadgets) cooperate to make decisions without a central authority, are the subject of a Sybil Attacks. These steps are typically included in the process:
False Personas Galore
The attacker creates hundreds or thousands of fake nodes, user identities, or IP addresses using a single machine or business. To the network, these seem like separate, authentic users.
Gaining Influence
An attacker can influence network choices in their favour by outvoting or overwhelming legitimate users with a huge number of phoney accounts. This is comparable to manipulating an election by stuffing a ballot box with fictitious votes.
Once powerful, the attacker can:
Voting manipulation
False blockchain nodes can verify phoney transactions, stealing Bitcoin or Ethereum.
Distribute False Information
Malicious nodes can spread compromised files on peer-to-peer networks, causing system slowdown or crash.
Sabotage Reputation Systems
Phishing accounts can post erroneous reviews or ratings on websites like Reddit, Uber, and Amazon, deceiving people about goods or services.
Overwhelm Networks
Phishing devices have the ability to overload smart home systems on Internet of Things networks, resulting in the breakdown of genuine devices such as thermostats, lighting, and cameras.
Also Read About Ethereum 2.0 Price (Formerly Eth2): Market Data & Analysis
Problems and Threats Caused by Sybil Attacks
Sybil attacks have the potential to seriously impair the performance and integrity of numerous networks:
- Privacy Vulnerability: Attackers can employ malicious nodes to gather private information, including user IP addresses, that is transmitted between trustworthy nodes.
- A 51% attack, in which one person or organisation takes control of more than half of a blockchain’s mining power or computer hash rate, can result from a Sybil attack. This damages the integrity of the blockchain system by enabling the attacker to alter transactions, reverse their own transactions (resulting in double-spending), and stop the confirmation of valid transactions. In 2019, there was such an attack on Litecoin Cash.
- Block Users from the Network (Censorship): Attackers can prevent other users from accessing the network legally by out-voting trustworthy nodes, which prevents them from sending or receiving blocks.
- Block Withholding Attack: The blockchain may become stale and ineffective over time if a sizable percentage of malevolent validators refuse to add new blocks.
- Misusing Reputation Systems: False reviews on e-commerce platforms can damage trust and confuse users.
- In the 2022 U.S. midterm elections, social media sybil bots propagated COVID-19 and election results falsehoods, causing pandemonium.
- To deceive users into clicking phishing links or fraud, fake accounts may impersonate politicians, celebrities, or companies.
- Attackers can interrupt voting, data aggregation, and routing.
Sybil Attack Examples
Sybil attacks have taken several different forms on a variety of network types:
P2P File-Sharing Networks
Napster and BitTorrent are early instances of networks in which fictitious nodes exchange damaged data.
Blockchain Networks
51% and double-spending attacks have targeted Bitcoin and Ethereum in particular. Attacks on smaller chains, such as Ethereum Classic, accounted for 51% in 2019. Targeted blockchains include Ethereum Classic, Verge, and Monero.
The Tor Network
- The Tor anonymity network was the focus of a significant Sybil attack and a traffic confirmation attack in 2014, which lasted for several months and sought to identify and track down certain users. The attacker gained disproportionate impact by controlling roughly 115 relays from a single IP address.
- In 2020, there was a “deadlier” Sybil attack on Tor that targeted Bitcoin owners. In order to deprive Bitcoin users of their money, attackers in control of numerous phoney Tor relays would intercept their online activities. They would occasionally use SSL stripping to degrade secure connections and transfer money to their wallets.
- A threat actor known as KAX17 deanonymized Tor users by controlling more than 900 malicious servers, mostly middle points, between 2017 and 2021.
- A malevolent party can take control of tens, hundreds, or thousands of nodes in a Sybil Attack on Tor, jeopardizing the privacy of the network. Attackers can keep an eye on the data flowing through both the entrance and egress nodes if they are under control.
Also Read About What Is Pure Proof of Stake (PPoS)? Decentralized Blockchain
Social Media (Twitter/X)
- In 2022, Sybil Attacks heavily targeted Twitter (now X), with “bot armies” undermining user protection, distributing false information, and upsetting confidence. In a single month, Twitter claimed to have eliminated 44 million fraudulent accounts. These bots did the following:
- Employing hashtag trends, retweets, and fake likes to promote fraud or silence authentic voices.
- Spreading false COVID-19 or election news.
- A brand or popular personality is impersonated to promote a phishing link. Sybil attacks were a contributing factor in the estimated 5% to 15% of Twitter’s 240 million daily active accounts that were bots as of mid-2022.
Sybil attack detection
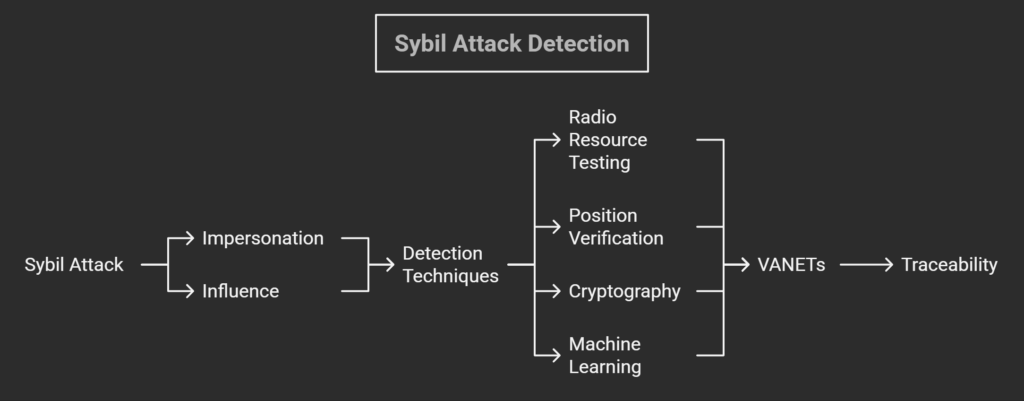
A Sybil Attack occurs when a malevolent actor creates several false identities within a network in order to exert excessive influence. Though they differ, detection techniques often seek to locate and separate these false identities. It use a variety of methods, such as machine learning, cryptography, position verification, and radio resource testing.
Impersonation
A Sybil attack is an impersonation technique in which one attacker assumes several identities.
Influence
The objective is to overrun the network with phoney nodes in order to seize control or interfere with regular operations.
Detection Techniques
- Radio Resource Testing: identifies attackers based on resource exhaustion and assumes that each node has limited resources.
- Position Verification: Confirms the nodes’ actual locations, making sure each one has a unique identification.
- Cryptography: Makes use of cryptography methods to identify irregularities and confirm identities.
- Machine learning: Develops algorithms to recognize trends and irregularities suggestive of Sybil Attacks.
VANETs (Vehicular Ad-hoc Networks)
Fake identities can cause safety problems in VANETs, where vehicles communicate with one another, and sybil Attacks are a concern.
Traceability
Even when rogue nodes try to avoid detection, certain techniques concentrate on tracking them down.
Challenges
It can be difficult to identify Sybil attacks, particularly when the perpetrators are very skilled.
Example
A rogue car could broadcast misleading information about traffic congestion in VANETs, leading other vehicles to choose risky routes in a Sybil attack.
Further Research
Numerous studies examine various methods for detecting Sybil attacks, including the ones listed above. While some studies examine more general approaches like machine learning, others concentrate on particular network types like VANETs.
Also Read About Ethereum Security: Redefining Trust in a Decentralized World
