The components and purpose of cryptocurrency wallets, as well as types of blockchain wallets and their crucial functions, are covered in this article.
Cryptocurrency Wallet

In essence, a cryptocurrency wallet often just called a wallet is a piece of software that is used to store and manage a user’s cryptographic keys and credentials, including public and private keys and the addresses that go with them. Since the cryptocurrency itself does not physically reside on any device, it acts as an interface for safely keeping these keys. The wallet solely stores blockchain-stored digital asset keys. Digital identities and money access are made possible by wallets, making them essential for blockchain network participation.
Blockchain wallets, also known as crypto wallets, come in two main types: custodial and non-custodial, each with its own security and convenience characteristics. Within these broad categories, you can find sub-types like hot and cold wallets, as well as software, hardware, and paper wallets.
Also Read About What Are The Different Types Of Blockchains Technology?
Core Components and Purpose
The following are the Core Components and Purpose of wallets:
Cryptographic Keys
Cryptographic keys, mainly a private key and a public key that is obtained from it, are managed by wallets. Owners must protect these secrets, usually cryptographic keys, in order for cryptocurrencies and decentralised assets to remain secure.
Address
A wallet also controls the blockchain address or addresses, which are usually generated using a hash function and a user’s public key. Digital assets are sent and received via addresses, which are brief alphanumeric characters.
Blockchain Interaction
Wallets create transactions to be recorded on the blockchain and keep track of assets on the blockchain. They can broadcast signed transactions to the network and query the blockchain to find out how much money is available.
Not a Storage of Assets
Wallets hold the keys that regulate access to the digital assets listed on the distributed ledger, not the actual digital assets themselves (such as Bitcoin or Ether). For instance, there are no coins on the Bitcoin network; instead, wallets use the blockchain to store transaction data, notably UTXO (unspent outputs), which is used to determine balance.
Also Read About Types Of Nodes In Blockchain: Full, Light, Mining And More
Essential Roles
- Transaction Signing: To demonstrate ownership of the related digital assets, wallets digitally sign outgoing transactions using the private key.
- Sending and Receiving: They make it easier to transfer and receive sensitive data or digital currency.
- Balance Inquiry: Wallets use blockchain queries to determine the current balance of assets linked to the addresses they oversee. They might also carry out additional tasks, such figuring out how many digital assets a consumer might own overall.
- Smart Contract Interaction: An interface for communicating with smart contracts may be found in wallets.
- Account Management: They offer crucial functionality for managing accounts.
Importance of Private Keys and Custody
- The protection of one or more private keys that the user maintains is essential to asset security.
- A user instantly loses access to their money if their keys are misplaced or compromised. Since it is computationally impossible to regenerate a private key, any digital asset linked to it is lost if it is lost. All digital assets under the ownership of a stolen private key are fully accessible to the attacker.
- The adage “if you don’t own the keys, you don’t own the asset” emphasises how crucial it is to keep one’s private keys under control.
Types of blockchain wallets
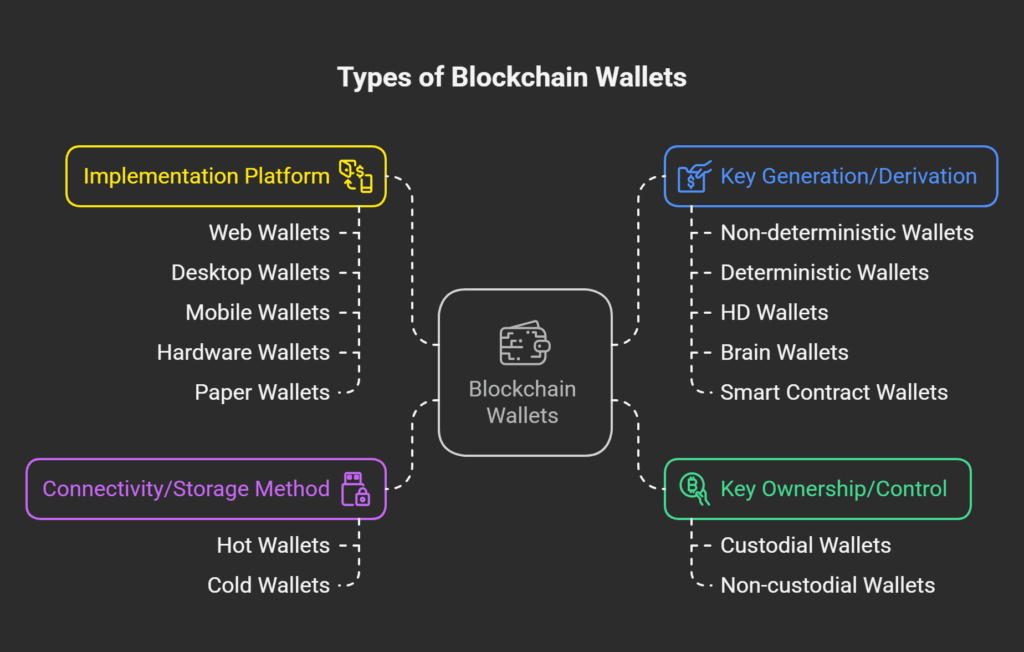
Wallets fall into a number of categories, many of which overlap:
Based on Key Ownership/Control
- Custodial Wallets: In a custodial wallet, the user depends on a third party (such as an exchange) to hold the private keys. This necessitates complete faith in the third party for security, even though the user bears less responsibility for key handling. Although they are frequently chosen by non-techies, they are thought to be less secure than non-custodial varieties in the event that the provider is compromised. Exchanges frequently provide custodial wallets with password reset and recovery capabilities via web-based or mobile app platforms.
- Non-custodial wallets: The private keys and related assets are fully owned and controlled by the user. Although this method offers complete control security, it is dangerous for novice users who could misplace their keys. It takes work to secure these.
Based on Connectivity/Storage Method
- Hot wallets: Having an internet connection makes it possible to have keys for transactions easily accessible. Provide accessibility. Custodial wallets are frequently hot wallets. frequently susceptible to exploits and cyberattacks.
- Cold wallets: Keep keys offline, usually on paper or a hardware device. The device never loses its keys. Being offline makes it more safe, but regular transactions will find it less convenient.
Based on Implementation Platform
- Web wallets, often known as online wallets, are accessible through a web browser. Convenient, yet maybe vulnerable to security risks. The user has faith in the website operator’s security. Coinbase (custodial) and Blockchain.com (non-custodial) are two examples.
- Desktop wallets: Computer programs that have been downloaded and set up. If the PC is secure, provide greater security than online wallets. Data may not be transferable. MetaMask (desktop version) and Electrum are two examples.
- Installed on mobile devices are mobile wallets. Both popular and portable. frequently make advantage of phone functions like paying with a QR code scan. Blockchain Wallet, Breadwallet, Copay, and Jaxx are a few examples.
- Hardware wallets are offline, physically impenetrable devices used to store private keys. Keys never leave the device and are used inside to sign transactions. regarded as extremely safe. Trezor and Ledger are two examples.
- Paper wallets: Usually accompanied by a QR code, the private key is printed or written down. provides long-term cold storage and offline keys, which lowers the danger of online theft. beneficial in low-tech settings. prone to bodily harm.
Based on Key Generation/Derivation
- Not deterministic “Just a Bunch of Key wallets” are wallets that hold randomly generated private keys. Many of these keys are challenging to manage and prone to mistakes, necessitating frequent backups.
- Keys for deterministic wallets are generated from a single seed value, which is frequently a seed phrase or mnemonic code word. Since the seed can retrieve every key, managing them is made simpler.
- Advanced wallets of the Hierarchical Deterministic (HD) variety store keys in a tree structure that is created from a single seed. A master key is created by the seed, from which child keys are derived, and so on. incredibly lightweight and simple to maintain. BIP32 and BIP44 define it. For the seed, mnemonic phrases are frequently employed. Deterministic generation of a wallet’s account addresses is made possible using a mnemonic.
- Brain Wallets: A kind of wallet in which the hash of a password that has been committed to memory serves as the master private key. prone to brute-force and guessing assaults.
- Wallets controlled by a smart contract, known as smart accounts or identity contracts, enable more sophisticated control logic, including multi-signature requirements or simpler device recovery.
Also Read About What Is Append Only Blockchain, Tamper Evident And Resistant
Other Wallet Concepts
- In deterministic wallets, a mnemonic or seed phrase is a group of phrases that can be used to recover a private key or restore accounts. Since losing it or having it compromised could result in the loss of all related funds, it is imperative that this be kept private and secure.
- SPV Client: A thin node that serves as a wallet of sorts, confirming transactions without requiring the whole blockchain to be downloaded.
- Multi-signature wallets: These provide increased security by requiring signatures from several private keys (for example, M of N) in order to approve a transaction. frequently used for large-scale storage or by teams.
Conclusion
Wallets, which offer the interface to manage the cryptographic keys that control their digital assets instead of keeping the assets themselves, are, in short, the key tools for users to engage with blockchain networks. Depending on the kind and implementation, there are significant differences in their design and security.
