Introduction to IoT Identity Protection
IoT gadgets simplify and ease life. One can operate smart cars, obtain real-time weather information, and remotely turn on and off the bedroom lights. Comfortable living is made possible by smart refrigerators, security systems, and thermostats. As computers, hackers and cybercriminals may attack these devices.
Unfortunately, the internet of things allows hackers to swiftly access systems and steal vital data. Therefore, IoT-enabled systems and devices must provide effective IoT protection to prevent significant crimes.
Identifying users and things
When it comes to customised gadgets, identity concerns are significant. For instance, using IoT devices to conduct sensitive and important tasks like internet banking requires security. It can make sure that the user’s identity is protected by implementing features like multi-factor authentication, consent forms, terms and conditions, and agreements.
Furthermore, standards for authentication, encryption, and authorisation are necessary for all IoT devices.
Implementing security for identities from the start
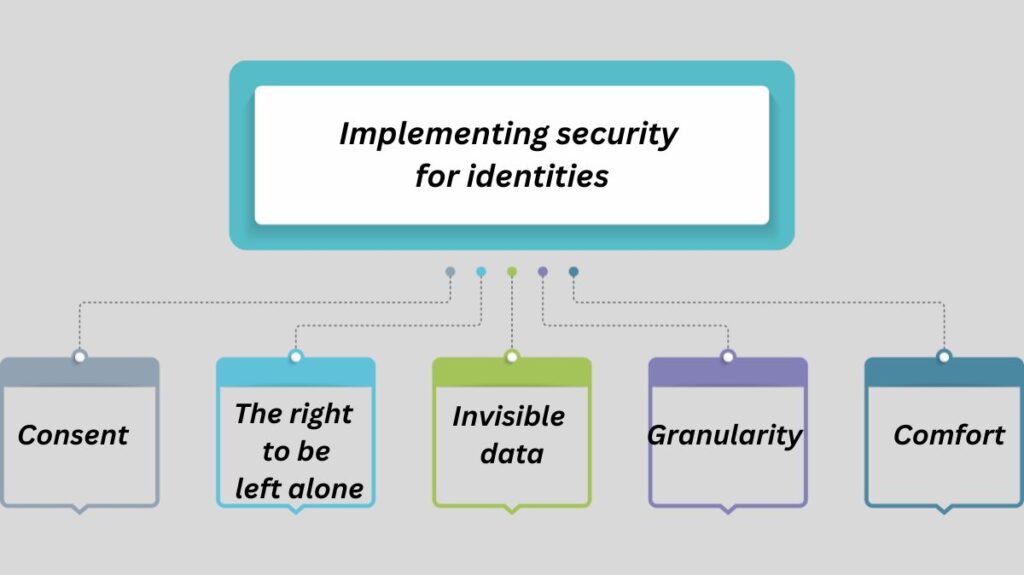
Because IoT devices are interconnected, it is crucial to guarantee security from start to finish. The security solution needs to be dependable, engaging, and easy to use.
Consent
Consent is the main issue with IoT devices. The data collection system and the type of data collected by the devices are not disclosed to users by the device manufacturers. Occasionally, the devices may gather pertinent data, which results in the processing of irrelevant data. These gadgets give businesses access to users’ private information.
The right to be left alone
In some circumstances, users and consumers have frequent expectations regarding privacy. While security cameras in commercial places may be expected, users may be surprised to discover cameras in their smart automobiles. IoT devices recognise these rights as the “right to be left alone” and impede progress.
Invisible data
There are several applications for IoT in the real world, and the majority of them aim to assist a group of people rather than a single user. The IoT might not be able to accommodate every user’s preference, even though each user might supply a set of actions. Small IoT devices in complexes, for instance, are unable to comply with every customer’s request.
Granularity
Big data puts system and user privacy at serious danger. Due to its intimacy and tremendous scalability, IoT gathers vast amounts of data from several sources. This puts the user at direct risk of serious injury and peril and results in the building of extremely detailed profiles about them.
Comfort
IoT is normalising the disclosure of personal user data. Users believe that giving digital systems sensitive information is commonplace. People who don’t know much about technology are vulnerable to phishing and other online scams. This is all due to the fact that IoT makes it easy to exchange important consumer data with less security precautions.
How could you pose the greatest risk to your online safety?
It lives are significantly made easier by the internet of things. However, businesses may neglect security considerations because of product delivery schedules.
Data access is the primary component of identity theft. Hackers closely monitor appliances including refrigerators, ovens, geysers, microwaves, and thermostats in order to obtain information from all of them.
It gets easier for the hacker to take the user’s identity the more information they have about them.
Sensitive data is everywhere
It can observe that everyone in immediate vicinity has a personal mobile phone that links to their own devices due to the advent of customised technological devices. This makes it easy for someone to hack the rest of a user’s devices if they use their phone outside and someone manages to figure out their password or pin.
Names, email addresses, credit card numbers, and a host of other private and sensitive data are stored on our smartphones and smartwatches. Therefore, hackers find it easier to obtain sensitive data.
Identity theft is currently the biggest threat
Identity theft occurs when the person who hacks your devices poses as you. And in linked, modern world, this is a greater problem. Unaware that the hacker is attempting to obtain their assets and personal data, other people who know you and get in touch with you might think it’s you and give you their personal information.
Keep yourself and your data safe
- Recognise who has access to your data and only divulge the information that is required. Avoid answering questions from people posing as representatives of banks and life insurance firms.
- To make sure your messages are secure and confidential, encrypt your data both when sending and receiving.
- Employ robust authentication. Each device should have a unique pin, code, and password with strong characters to prevent hacking.
- Read the fine print before buying an IoT device. Observe all security instructions to the letter.
Identity protection measures implemented in IoT
Internet of Things should have coverage for individual consumer indemnity. The security and case protection of any user’s personal information is crucial. The following are a few identity protection measures:
- Make sure your passwords are strong and case-sensitive. Every device should have a unique password, and you should never share this information online.
- Make sure your documents are secure.
- To securely connect personal devices, apply for a VPN personal wireless service.
- Don’t allow unauthorised access to any digital device and encrypt user data Smart chips are installed in every sensor.
- Cryptography is the most effective authentication method for Internet of Things devices. Cryptographic keys can interface with Internet of Things devices.
Summary
This had to do with IoT identity protection. Saw a number of problems with user identity in the Internet of Things. The measures implemented to safeguard identification in the Internet of Things were then examined.
