ECIES standard
This is a thorough explanation of ECIES:
Hybrid Approach:
- The advantages of both symmetric and asymmetric encryption are combined in ECIES.
- Data encryption is faster with symmetric encryption and key exchange using ECC.
- This approach balances security and speed, making it suitable for digital signatures and secure texting.
Key Derivation:
- ECIES uses a key derivation function (KDF) to create a symmetric key rather than immediately encrypting with a public key, which is computationally costly.
- A shared secret obtained by ECC’s Diffie-Hellman key exchange serves as the foundation for this symmetric key.
Security:
ECIES’ security relies on the cryptography-challenging elliptic curve discrete logarithm problem (ECDLP).
Components:
- Elliptic Curve Cryptography (ECC) secures key exchange and secret creation.
- Symmetric Encryption: AES or ChaCha20 encrypt the message.
- HKDF or PBKDF2 is used to derive a symmetric key from the shared secret.
ECIES Standard
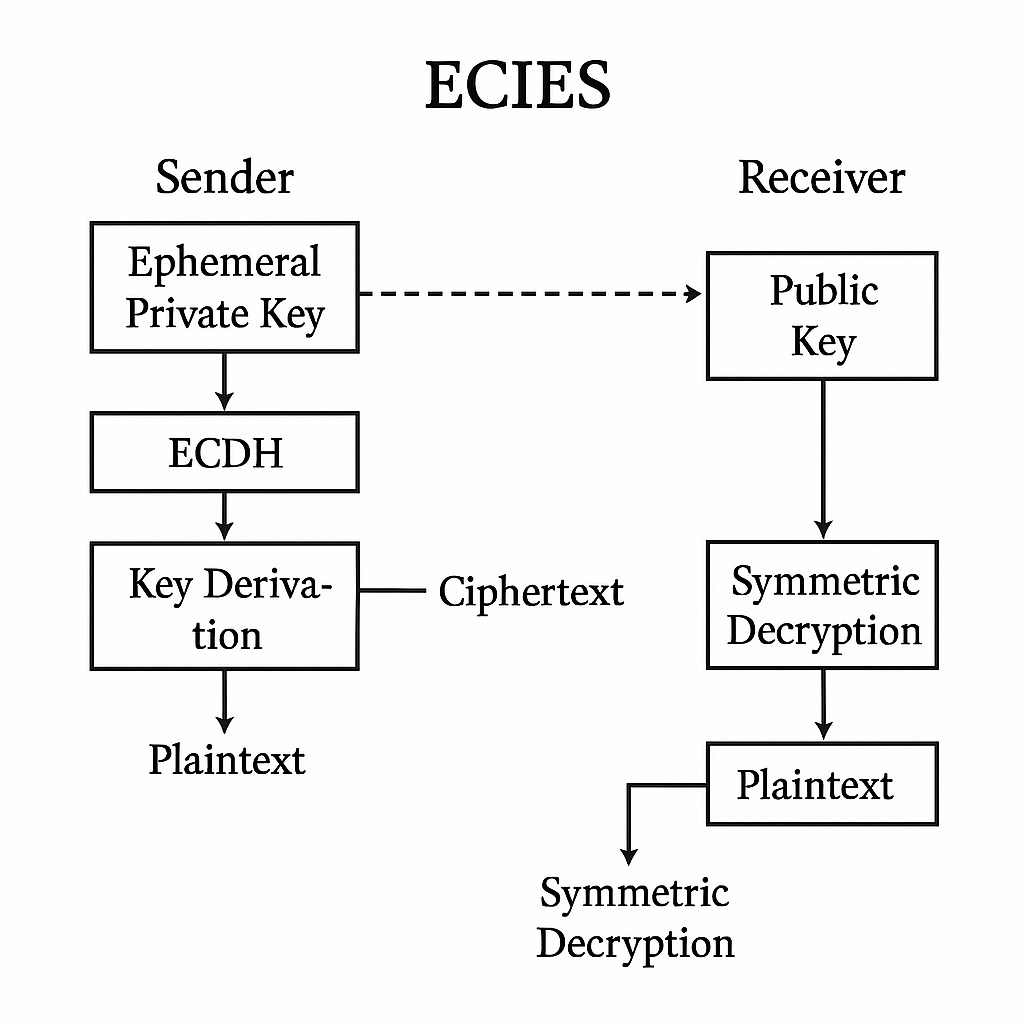
Process Overview
Recipient’s Key Generation:
ECIES begins with the recipient generating public and private keys. A random integer ‘D’ is chosen as the private key, and the matching public key ‘Q’ is derived as D * G, where ‘G’ is a fixed point on the elliptic curve. The recipient shares ‘Q’ but not ‘D’.
Sender’s Actions:
- Senders produce unique secret keys for each message. A random number ‘R’ is generated, and two elliptic curve points are calculated: T = R * Q (a secret point) and U = R * G (the sender’s public key).
- The sender creates an encryption key using the secret ‘T’. A key derivation function generates a 256-bit SHA-256 key from point ‘T”s x-coordinate.
- First 128 bits are encryption key, second 128 bits are MAC key.
- Symmetric methods like AES encrypt communication.
- HMAC-SHA256 verifies message integrity with the sender’s MAC key and encrypted message. Encrypted text for the MAC increases security because the recipient would notice any modifications to the encrypted message.
- The recipient receives the encrypted message, MAC, and sender’s public key, ‘U’.
Recipient’s Actions:
- First, the recipient multiplies the sender’s public key ‘U’ by their private key ‘D’ to calculate T’ (T Prime) (T’ = D * U). This T’ needs to match the ‘T’ used by the sender.
- The recipient then generates the same symmetric encryption and MAC keys that were used by the sender using this shared secret T’.
- The recipient confirms the MAC they received. MAC verification guarantees the encrypted message was not altered during transmission.
- Finally, the recipient decrypts with symmetric key.
- In conclusion, ECIES combines symmetric encryption and a secure MAC to guarantee message integrity with elliptic curves to allow the safe computation of shared secrets without disclosing private keys.
- Digital signatures, secure storage systems, and secure messaging protocols are just a few of the uses for ECIES.
Security of ECIES
Based on the security of the underlying symmetric encryption and MAC techniques, as well as the difficulty of the Elliptic Curve Discrete Logarithm Problem (ECDLP), ECIES offers robust security assurances.
Assumptions in ECIES security
- ECIES’s security is predicated on the idea that solving the ECDLP is computationally impossible.
- This indicates that it is quite challenging to determine the scalar $k$ such that $Q = kG$, where $G$ is the base point, given a point $Q$ on the elliptic curve.
- Additionally, ECIES makes the assumption that the MAC method (such as HMAC) and underlying symmetric encryption scheme (such as AES) are safe and impervious to known attacks.
Also Read About What Is ECDSA? Elliptic Curve Digital Signature Algorithm
Security proofs for ECIES
- It has been demonstrated that ECIES offers security against indistinguishability under chosen ciphertext attack (IND-CCA) and indistinguishability under chosen plaintext attack (IND-CPA).
- Even if an opponent manages to gain the encryptions of selected plaintexts, IND-CPA security makes sure that they are unable to discern between the encryptions of two distinct messages.
- An extra degree of protection is offered by IND-CCA security, which makes sure that even if an adversary manages to decrypt selected ciphertexts (apart from the challenge ciphertext), they would not be able to discover any information about the plaintext.
- The previously stated presumptions and the security of the underlying primitives are the foundations of ECIES’ security proofs.
Applications of ECIES
ECIES is widely used in many fields that need data protection and secure communication.
Use cases for ECIES
- Applications for secure messaging frequently employ ECIES to encrypt and decrypt user communications.
- It also secures email transmission, ensuring privacy and accuracy.
- Blockchain and cryptocurrency systems protect user privacy and transactions with ECIES.
- Smart contracts and IoT devices employ ECIES for secure data sharing and communication.
Advantages of ECIES in applications
- Applications requiring high levels of security can benefit from ECIES’s robust security guarantees, which are based on the ECDLP’s hardness.
- Elliptic curve cryptography’s tiny key sizes minimize transmission and storage overhead, making ECIES effective for devices with limited resources.
- ECIES’s integrated message authentication removes the requirement for a different MAC technique, making implementation easier and the attack surface less.
- ECIES works with many symmetric encryption methods and elliptic curves, so developers can choose the parameters that suit their needs.
Also Read About Blockchain RSA: Public-Key Cryptography For Data Transport
Limitations of ECIES in applications
- Public key management and distribution must be done securely for ECIES, which can be difficult in large-scale systems.
- Particularly for large communications, ECIES’s performance could be slower than that of symmetric encryption techniques.
- Since ECIES depends on the security of the symmetric encryption methods and underlying elliptic curve, any flaws found in these primitives could affect ECIES’s security.
- Proper key generation, secure random number generation, and defense against side-channel attacks are just a few of the factors that must be carefully considered in order to implement ECIES effectively and safely.
Variants and extensions of ECIES
A number of ECIES extensions and variations have been put forth to meet certain security needs and boost productivity.
Modified ECIES schemes
- A variation known as Ephemeral-Static ECIES (ES-ECIES) reduces computational overhead by using a static key pair for the receiver rather than creating a new ephemeral key pair for every encryption.
- Elliptic Curve Integrated Encryption Scheme with Key Encapsulation Mechanism (ECIES-KEM) is made more flexible by the Encapsulation Mechanism (ECIES-KEM), which divides the data encapsulation and key encapsulation processes.
- Schnorr ECIES (SECIES) adds extra authentication and non-repudiation features by substituting Schnorr signatures for the ECDH key exchange.
Also Read About Understanding Cryptography Mechanisms In The Blockchain
Integration of ECIES with other primitives
- To improve security or add new features, ECIES can be coupled with various cryptographic primitives.
- Digital signatures, such as ECDSA, can be coupled with ECIES to enable authentication and non-repudiation of encrypted messages.
- Several keys for various uses (encryption, authentication, etc.) can be derived by combining ECIES with key derivation functions (like HKDF). from the mutually held secret.
- Additional protection against chosen-ciphertext attacks can be achieved by combining ECIES with padding methods (such as OAEP).
ECIES standardization
- Numerous organizations have standardized ECIES in order to guarantee interoperability and encourage secure deployments.
- Standards like ANSI X9.63 define and guide ECIES implementation.
- IEEE 1363a recommends ECIES for public-key encryption.
- SECG SEC 1 describes ECIES and provides test vectors for implementation validation.
- ECIES is part of NIST’s public-key cryptography and key management standards.
