Discover the versatile Applications of Directed Acyclic Graph, from cryptocurrency to complex task scheduling. Learn about their non-cyclic structure and the significant benefits like enhanced throughput and parallel processing they provide.
A unique data structure known as a Directed Acyclic Graph (DAG) has become a strong contender to replace conventional blockchain technology, especially in the fields of cryptocurrencies and distributed ledger technology (DLT).
Directed Acyclic Graph Definition
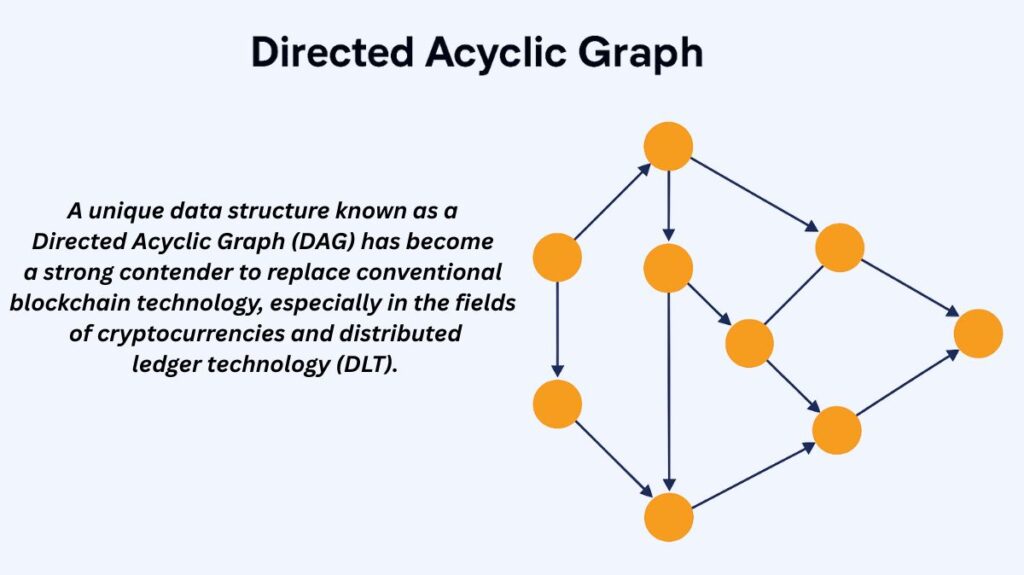
Instead of employing the linear chain structure included in conventional blockchains, a DAG is a sort of data structure that arranges data using interconnected structures resembling a web of relationships. Let’s dissect a DAG’s name in order to understand it completely:
Graph: Relationships between individual data entries (or transactions) create a network based on causal relationships in a graph database, which is how data is arranged in the context of DLT. Complex transactional linkages and dependencies inside the network can be captured using this method. A graph has vertices (nodes or points) and edges (lines).
Directed: This means every graph connection or interaction has an arrow showing its direction. Data integrity and transaction speed depend on this feature, which restricts data movement to one direction.
Acyclic: This indicates that the ledger or database cannot be made to produce a loop or cycle. To put it simply, a database route cannot return to a scenario in which a previous transaction depends on a subsequent operation.
To put it briefly, a DAG is a database that is organized as a network of related transactions, or bits of information, that are connected to one another according to their dependencies. This creates a graph that grows with every new transaction. The most basic type of DAG is a blockchain, which is a linear structure made up of directed and acyclic nodes (blocks) and edges (references).
Beyond Bitcoin, DAGs can be used to depict family trees or map spreadsheet formulas with causal linkages to guarantee accurate updates.
How DAG Works
Transactions inside a DAG in a cryptocurrency setting have explicit links with one another, forming a structure akin to a web.
Transactions as Vertices: Individual transactions are maintained as vertices (or nodes) in a DAG, as opposed to blockchains that aggregate transactions into blocks. Accordingly, “blocks” in the conventional sense are usually absent.
Referencing Previous Transactions: Each new transaction must reference prior transactions to be permitted onto the network, just like blockchain blocks do.
Proof-of-Work (PoW): Usually, nodes must do a brief Proof of Work task before they may submit a transaction. The purpose of this PoW task is to stop spam and validate previous transactions.
Consensus and Confirmation:
- A transaction is considered confirmed when it is mentioned in another transaction. A transaction must be approved by a supermajority of network validators in order to reach full consensus.
- One significant distinction between DAGs and blockchains is that each validator in a DAG often stores a distinct subset of the network state, as opposed to the full network state. Rather, individual transactions are spread, obtaining signatures from validators who possess the necessary expertise to verify them.
- Tip Selection: Which “tips” (unconfirmed transactions) a new transaction should be built upon is decided by an algorithm; tips with more confirmations are more likely to be selected.
- Asynchronous and Concurrent Processing: Compared to blockchains, this structure offers a more flexible and scalable method by enabling transactions to be confirmed both asynchronously and simultaneously.
Double-Spend Protection: In order to prevent double-spends, nodes in DAGs verify previous transactions by tracking back a path to the DAG’s first transaction and confirming the sender’s balance. A user runs the risk of having their transaction ignored if they attempt to double-spend or build upon an incorrect path. Selection algorithms settle conflicts between multiple paths by favouring tips with a higher cumulative “weight” (number of confirmations).
Structure of DAG
- Graphs, which are similar to a web of relationships, are used in DLT to arrange data using interconnected structures. Complex transactional linkages are captured by these relationships, which are frequently between individual data items or transactions and form a network based on causal dependencies.
- An acyclic database or ledger is one in which a loop or cycle cannot be formed. This allows one-way information flow and prevents transactions from relying on each other.
- A graph relationship marked as directed suggests information flows in one direction. Maintaining integrity and facilitating effective transaction processing depend heavily on this directed character.
- In its most basic form, a DAG is a database organised as a network of related transactions or bits of information that are connected to one another according to their dependencies, creating a graph that grows with every new transaction. In contrast to conventional blockchains, which have a linear chain topology, DAGs resemble a network of interconnected nodes. Vertices, or nodes, joined by directed edges are used to record transactions.
Key Characteristics and Concepts of DAGs
DAG-based systems present novel ideas and provide a number of benefits.
Scalability: Compared to conventional blockchain systems, DAGs provide for higher throughput by enabling parallel processing of transactions. High transaction volumes are supported by this parallel topology.
Speed: Because block generation does not restrict processing, transaction speeds are high. Simultaneous node development allows for faster and more efficient transaction processing.
Cost Reduction: DAG-based systems can drastically save operational expenses and energy usage by eliminating the requirement for conventional mining operations for validation and consensus, which frequently results in lower or even no transaction fees.
Security: DAGs are intended to increase the difficulty of network compromise by providing numerous validation points.
Risk Management: More advanced risk management systems are made possible by the structure of DAGs, which improves transaction dependency monitoring and management.
Topological Sorting: Every edge in this DAG’s linear ordering signifies the end of one vertex and the start of another, guaranteeing that tasks are finished in a particular sequence determined by dependencies.
Transitive Closure and Reduction: By finding direct linkages that might otherwise need several intermediate stages, transitive closure can help programs reach nodes in fewer steps. A graph with the fewest feasible edges is the result of transitive reduction.
Causal Inference and Relationships: DAGs are great tools for mapping causal links and consequences, demonstrating the direct influence of one event or transaction on another.
Blockchain VS DAG
Although both distributed ledger technologies DAGs and blockchains use consensus techniques for decentralization, validation, and transaction recording and do not require a central validating authority, their structure and methods of operation are very different.
| Feature | Directed Acyclic Graph (DAG) | Blockchain |
| Structure | Web-like network of interconnected nodes (transactions) | Linear chain of blocks |
| Transactions | Individual transactions are nodes; processed asynchronously and concurrently | Transactions are batched into blocks; processed stepwise, block by block |
| Consensus | Individual transactions achieve consensus once signed by a supermajority of validators | Validators assess entire blocks, requiring supermajority agreement for validity |
| Mining/Fees | No traditional miners or block creation; often lower or zero transaction fees | Miners compete to verify transactions; involves mining rewards and often higher transaction fees |
| Scalability | High transaction speeds due to parallel processing; greater throughput | Limited by block creation time and size; can face scalability challenges |
| Energy Usage | Lower energy consumption as traditional mining is not required | Can consume massive amounts of electricity due to Proof of Work mining |
| Maturity | Still in early stages of use for cryptocurrencies; not yet fully decentralized | Well-established and widely used (e.g., Bitcoin, Ethereum) |
| Decentralisation | Has challenges in achieving full decentralisation, sometimes relying on central coordinators | Typically designed for high decentralization, though raising block size can affect it |
| Security | Multiple validation points; can be vulnerable to attacks with low transaction volume | Transparent, unalterable, and generally highly secure |
Example of Directed Acyclic Graph DAGs
DAG technology has been implemented or is being investigated by a number of coins and protocols:
Sui: Sui uses a DAG for consensus and transaction propagation. In order to preserve historicity and data custody, it then arranges these previously completed transactions into “checkpoints” (which resemble blocks) in a different linear method, thereby fusing the best aspects of blockchains and DAGs. Its record-breaking transactions-per-second performance is a result of this hybrid strategy.
IOTA: One well-known DAG protocol is “Tangle” from IOTA, in which every node represents a transaction. All users are essentially “miners” since they validate one new transaction by confirming two previous ones. It strives for strong decentralisation, scalability, and almost minimal transaction fees.
Nano: Nano uses a “block-lattice” technology, which combines blockchain with DAG. Every user has their own blockchain or wallet, and transactions are finalized when the sender and the recipient both make changes to their chains. Nano provides fast speeds and no transaction costs.
Obyte: Obyte is a blockchain-independent cryptocurrency that employs a DAG foundation and a validator system that double-checks transactions using “witnesses” trusted individuals. Although there is still a cost for transactions, it offers untraceable transactions and uncreachable contracts.
Hedera: Hedera is a pioneer in DAG-based technology, employing a “gossip protocol” and a “hashgraph” consensus method. This promotes quick agreement by allowing nodes to share all fresh information with random nodes. Hedera is compatible with the Ethereum Virtual Machine and provides quick transactions with low, predictable fees.
Block-DAG Protocols: Although Block-DAG protocols are not yet in production, a lot of research has been done on them. Each node in the DAG is a block that contains several transactions, much like a blockchain block. GHOST, SPECTRE, and PHANTOM are some of the protocols that seek to boost throughput without sacrificing Proof-of-Work consensus. Block-DAGs’ primary engineering difficulty is to arrange blocks in a linear form.
DAGs’ efficiency, scalability, and speed make them desirable for decentralised networks, even though their use in cryptocurrencies is still evolving.
Advantages of DAG
As opposed to the linear chain of conventional blockchains, DAGs are organized as a web-like network of connected nodes (transactions). This special construction offers a number of advantages:
Scalability: Compared to conventional blockchain systems, DAGs provide for higher throughput by enabling the parallel processing of transactions. High transaction volumes are supported by this parallel topology. For instance, Sui’s DAG-based consensus mechanism, which handles transactions in an effective, non-linear fashion, helps it reach record-breaking transactions-per-second performance.
Speed: Because block generation does not restrict processing, transaction speeds are high. Simultaneous node development allows for faster and more efficient transaction processing. For example, lightning-fast transactions are made possible via Hedera’s gossip protocol and hashgraph consensus mechanism.
Cost Reduction/Low or Zero Transaction Fees: DAG-based systems can drastically save operating costs and energy usage by eliminating the requirement for conventional mining operations for validation and consensus. This frequently results in reduced or even nonexistent transaction fees. For instance, IOTA and Nano provide almost zero or no transaction fees.
Energy Efficiency: Because Proof-of-Work blockchains do not require conventional mining operations, which use enormous quantities of electricity, DAGs use less energy and have a positive environmental impact.
Security (Multiple Validation Points): DAGs are intended to increase the difficulty of network compromise by providing numerous validation points. Selection algorithms that prioritize tips with a higher total “weight” or number of confirmations settle disputes that arise from various pathways in a DAG. Because malicious concealed blocks would be voted on as coming last, this also makes double-spend attacks more difficult, even for an attacker with a significant share of hash power.
Risk Management: More advanced risk management systems are made possible by the structure of DAGs, which improves transaction dependency monitoring and management.
Suitability for Microtransactions: Because to their cheaper price structure, DAGs are perfect for transactions of all sizes, including microtransactions and large volumes of transactions.
Asynchronous and Concurrent Processing: Compared to blockchains, this structure offers a more flexible and scalable method by enabling transactions to be confirmed both asynchronously and simultaneously.
Disadvantages of Directed Acyclic Graphs (DAGs)
Notwithstanding their benefits, DAGs presently have certain drawbacks:
Decentralization Challenges: The fact that DAGs are not entirely decentralized, in contrast to conventional blockchains, is arguably their biggest disadvantage. The decentralization of certain DAG-based systems may be impacted by their dependence on trusted “witnesses” or central coordinators.
Early Stages of Use: The application of DAGs in cryptocurrency contexts is still relatively new. Their main purpose is to “get a network started” rather than to serve as a foundation for a long-lasting and reliable network.
Vulnerability to Attacks (with Low Transaction Volume): When transaction traffic is low, DAGs may be subject to attacks.
Engineering Challenges for Block-DAGs: Although there is a lot of research being done on Block-DAG protocols in which every node is a block no production Block-DAG protocols are currently in use. Block-DAGs’ primary engineering difficulty is to arrange blocks in a linear form to maintain consistency and avoid problems like Condorcet’s Paradox, which can compromise the protocol’s liveness (the system’s capacity to continuously compute new states). For example, linear block ordering is not guaranteed by SPECTRE.
Applications of Directed Acyclic Graph
Supply chain management, Internet of Things and sensor networks, and cryptocurrency are just a few of the domains where DAGs are being used. Industry 4.0 apps and commercial platforms also make advantage of them.
Cryptocurrencies using DAGs include:
Unibright, Cardano, Anion, and SEELE are further instances.
IOTA: makes use of a DAG structure known as “Tangle” and is intended for the Internet of Things (IoT), allowing for safe communication and feeless transactions between IoT devices.
Nano: quick and feeless transactions made possible by a peer-to-peer cryptocurrency based on a DAG design, specifically a block-lattice structure.
Hedera Hashgraph: Low latency and high throughput distributed ledger system that uses DAG’s benefits for micropayments, smart contracts, enterprise apps, and safe data sharing.
Obyte (Byteball): A cryptocurrency that operates without a blockchain and using a DAG framework with a validator system that verifies transactions twice via witnesses. Additionally, it supports unreachable contracts and untraceable transactions.
