MD5 Message Digest algorithm 5
MD5, a popular cryptographic hash function, generates a 128-bit hash value. A fixed-size output is generated from any input message, typically used to verify data integrity. MD5, a secure hash function, is no longer secure for cryptographic applications due to flaws. Non-cryptographic functions like checksums to identify unintended data corruption nevertheless use it.
MD5, or Message-Digest Algorithm 5, is a well-known hash function in cryptography. Ronald Rivest created it in 1991 as an enhancement to the previous MD4 method, mainly for increased security and to allow digital signature verification. Below, we discussed MD5, including what it is, what hashing is, how MD5 algorithm works, functions, applications of MD5, benefits of MD5, drawbacks and security issues, and alternatives to MD5.
What is Hashing?
It’s crucial to comprehend hashing before diving into MD5. Hashing is the technique of employing a hash function to turn a conventional string of data into a complicated, unintelligible piece of information. In order to create a hashed value also referred to as a digest or hash digest that is entirely distinct from the original, this procedure jumbles the original value. One important feature of hash functions is that, for a given hash function, such as MD5 or SHA1, the digest size is always constant, independent of the size of the input.
Key functions of MD5
- MD5 outputs a 128-bit hash regardless of input data length. The 128-bit digest is commonly a 32-digit hexadecimal integer.
- 1Way Function: Reversing hashing to get the original input from the hash value is computationally impossible.
- Avalanche Effect: A digest that changes drastically with even small input string changes. This characteristic is ideal for identifying instances of data manipulation.
Also Read About RIPEMD 160: What Is It, How It Work, Applications & Benefits
How the MD5 Algorithm Works
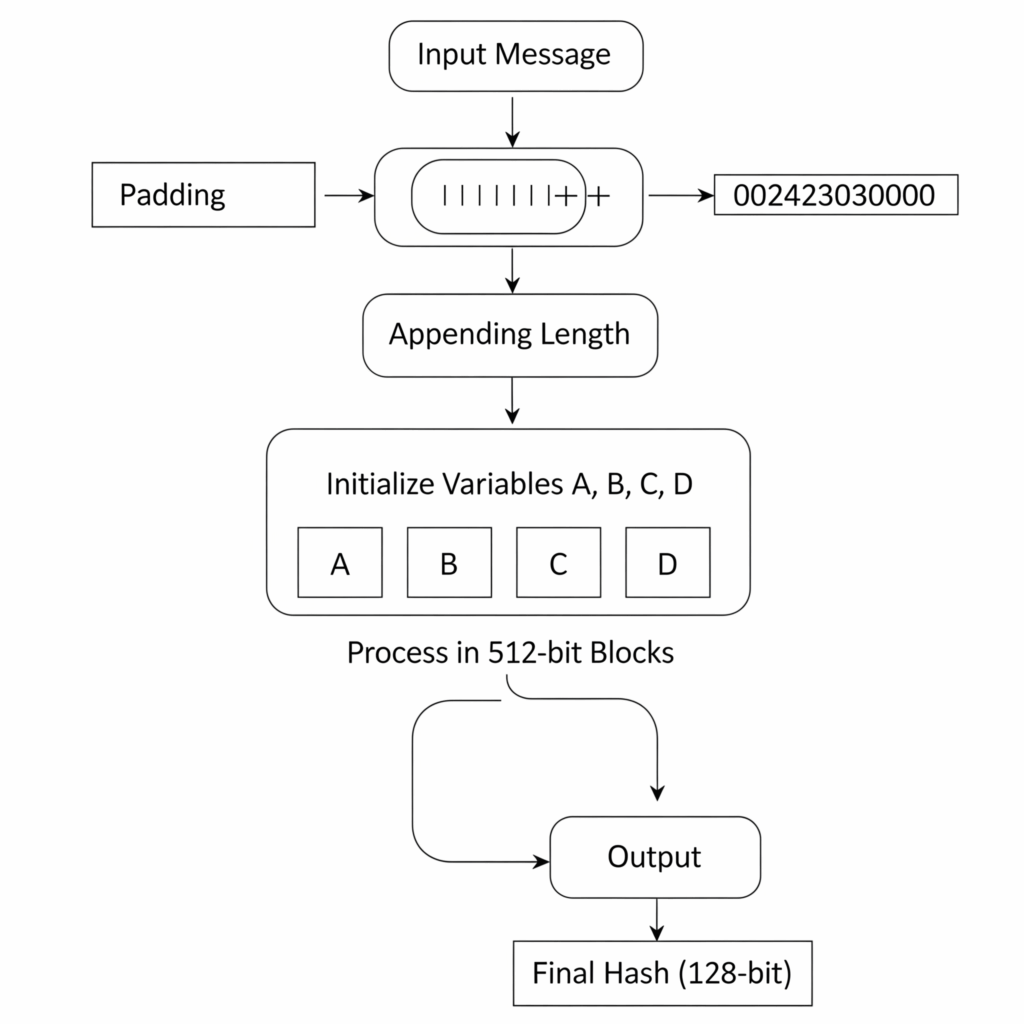
Data is processed by the MD5 algorithm in multiple primary steps:
- In order to guarantee that the input message’s length (in bits) is 64 bits less than an exact multiple of 512, it is padded. Adding one ‘1’ bit and enough ‘0’ bits to reach the specified length does this.
- A 64-bit integer indicating the original message’s length (in bits) is attached to the padded message after padding. This ensures the hash input has the original length. Appended length bits and padded message equal 512 bits.
- MD Variables/Buffer Four 32-bit variables (A, B, C, and D) are initialized with hexadecimal constants.
- A = 0x67452301
- B = 0xefcdab89
- C = 0x98badcfe
- D = 0x10325476
- Full string becomes 512-bit chunk. Each 512-bit block has 16 32-bit subblocks.
- Each 512-bit block has 64 operations across four 16-operation rounds. These operations require M-to-M subblocks, T-to-T constant array values, and four buffers. Each cycle uses a non-linear function (F, G, H, I) to update buffer variables via bitwise operations, modular additions, and left rotations.
- After processing all 512-bit blocks, concatenating variables A, B, C, and D provides the MD5 hash. A 128-bit message digest will result.
Also Read About Segregated Witness Blockchain: How SegWit Works & Impact
Benefits of MD5
- Simple to Compare: A 32-digit digest is comparatively simpler to compare when confirming the digests, in contrast to the most recent hash algorithm families.
- Password storage: It is not necessary to keep passwords in plaintext, which leaves hackers and other bad actors with access to them. Because all hash values will have the same size, using digests also improves the database.
- Low Resource: To combine several services into a single framework without CPU overhead, a comparatively small memory footprint is required.
- Integrity Check: By comparing hash values before and after travel, you can keep an eye out for file corruption. File integrity checks are legitimate and prevent data damage once the hashes match.
Drawbacks and Security Issue’s
MD5, despite its widespread use, is no longer cryptographically secure and should not be used for security-sensitive applications due to serious vulnerabilities.
- Multiple inputs can generate the same MD5 hash value. Its capacity to guarantee data authenticity and integrity is weakened as a result. On ordinary computers, researchers have shown how to create MD5 collisions with ease, even producing them in a matter of minutes or seconds.
- Preimage Attacks: An attacker can discover the original input that hashes to a specific MD5 hash by using preimage attacks, which are another vulnerability of MD5. This shows the digest fails the computationally difficult-to-retrieve original message requirement.
- Brute-force attacks are possible with MD5 hashes due to their speed.
- Many modern security methods no longer employ MD5 due to its weaknesses. Future protocol designs should avoid MD5 hashes for cryptographic authentication and collision-resistant digital signatures.
- Compared to SHA1 and SHA256, MD5 is less secure.
Applications of MD5
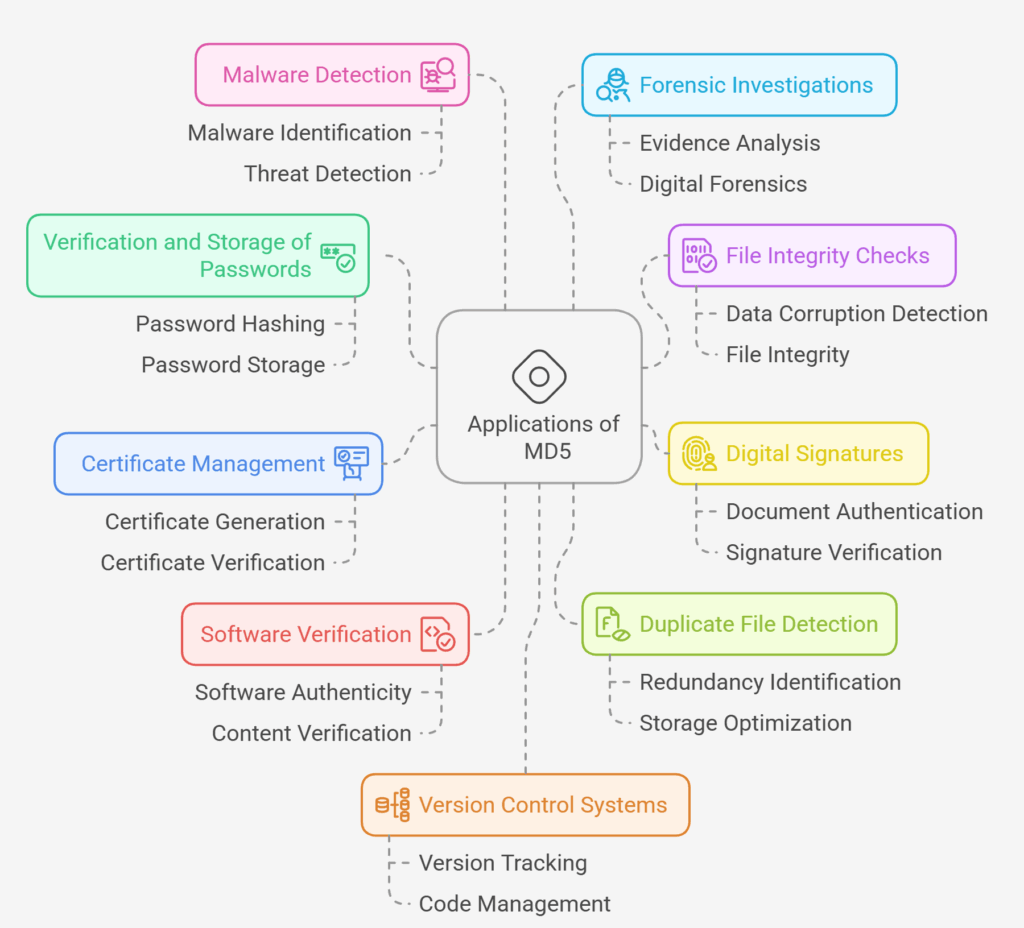
MD5 has been utilized in many applications both historically and today, although because of flaws, its use has decreased in security-sensitive areas:
Verification and Storage of Passwords
In order to protect user credentials from hackers, they were often stored in a hashed format. To verify login, the system hashes the password entered and compares it to the hash that has been stored.
MD5 checks files for data corruption
Creating and comparing hash digests before and after transmission or storage can reveal data corruption. It is still regarded as appropriate for safeguarding against protocol faults.
Digital Signatures
Due to security flaws, MD5 is no longer advised for use in digital signature verification. Previously, it was used to generate distinct “fingerprints” of documents.
Certificate Generation and Verification
Digital certificates can be created and validated using MD5 algorithms in Public Key Infrastructure (PKI) systems. An MD5 hash of the certificate data is produced by the certificate authority (CA) and incorporated into the certificate upon issuance. This makes it possible to confirm the integrity of the certificate when it is shared or utilised.
Software and digital content verification
MD5 hashes are often used to verify software and digital content. Open-source software releases often include MD5 checksums. Users can check the downloaded file’s checksum against the MD5 hash to ensure a full download.
Detecting Duplicate Files
Applications check MD5 hashes to discover duplicate files for data deduplication and file management.
Malware Detection
In cybersecurity, MD5 hashes can detect malware. Security researchers and antivirus software providers update malware hash databases. The MD5 hash of a suspicious file can be quickly compared to the database to identify malware.
Forensic Investigations
Digital forensics uses MD5 hashes to generate hash values for digital evidence in order to guarantee its integrity. An MD5 hash is created and recorded once the evidence has been gathered. To ensure that the evidence has not been tampered with, the hash can be recalculated as the investigation and analysis go.
Version Control Systems
For effective change tracking, certain version control systems employ MD5 hashes to pinpoint certain file versions or revisions. Game boards and graphics.
Also Read About What is Distributed Hash Table Blockchain And How it works
Alternatives to MD5
Stronger cryptographic hash algorithms are advised for applications needing strong security due to MD5’s flaws. These include:
- Some companies no longer support SHA-1, which generates 160-bit data better than MD5.
- Digital signatures, blockchain, and SSL certificates require longer SHA-256 and SHA-512 hash values (224, 256, 384, or 512 bits).
- A redesigned internal structure makes SHA-3 a superior cryptographic alternative to SHA-2.
- A 160-bit RIPEMD-160 hash is safer than MD5.
- Whirlpool: 512-bit high-security cryptographic hash function output.
MD5 provides a 128-bit “fingerprint” for each piece of data, like a digital finger printer. It’s good at detecting even a single dust particle (a minor modification) touching the original data, but a skilled forger might easily manufacture two “items” with the same fingerprint. If identical fingerprints could be generated from various people, a fingerprint system would be unreliable. This means it cannot provide the uniqueness and integrity that modern security requires.
