SHA 3 Algorithm
The most recent standard in the Secure Hash Algorithm family is represented by the cryptographic hash function known as SHA-3, or Secure Hash Algorithm Version 3, or Keccak. A group comprising Guido Bertoni, Joan Daemen, Michael Peeters, and Gilles Van Assche created it, expanding on previous concepts such as PANAMA and RadioGatún. After NIST held a competition beginning in 2006, SHA-3 was formally accepted as a new FIPS standard on August 5, 2015. Given successful attacks on MD5, SHA-0, and SHA-1, the competition’s objective was to offer a unique cryptographic hash rather than to replace SHA-2 because of any known attacks.
How it Works (Design and Mechanism)
The sponge building is a novel technique that forms the basis of SHA-3’s operation. Because of its construction, it can “squeeze” out a digital print of a chosen length after “absorbing” input data.
There are two primary stages to the process:
Absorbing Phase:
In the absorption phase, the length of the original message (M) is first made divisible by the ‘rate’ (r) by padding it with a particular “10…01” pattern. After that, a subset of the internal state is created by XORing message blocks. The input is dispersed throughout the entire state by using a permutation function (f), called Keccak-f for SHA-3. The security level is determined by the ‘capacity’ (c), which is the portion of the state that remains unaltered.
Squeezing Phase
Following absorption, the state is subjected to the permutation function (f), which is used to copy portions of size r from it until the desired hash length is reached.
The “sponge” keeps its internal state at 1600 bits. A 5×5 array of w-bit words, where w is 64 bits for SHA-3, is how this state is conceptualized. The fundamental block transformation is the Keccak-f permutation, which has 24 rounds (12 + 2ℓ, where ℓ=6 for 64-bit words). There are five different steps in each round:
- θ (theta): Computes the parity of 5-bit columns and XORs it into nearby columns.
- ρ (rho): Each of the 25 words is rotated by a distinct triangular number using bitwise.
- π (pi): Changes the 25 words in a predetermined way.
- χ (chi): The only non-linear operation in SHA-3, bitwise combines along rows using a non-linear operation (XOR, NOT, AND).
- ι (iota): breaks symmetry by XORing a round constant into a single word of the state.
Also Read About SHA 256 Blockchain: Modern Technology And Digital Security
Features
- Unidirectional Function: SHA-3 is a one-way function, which means that reversing the hash to get the original input data is not computationally viable.
- The standard SHA-3 variations (SHA3-224, SHA3-256, SHA3-384, and SHA3-512) generate fixed-length hash values of 224, 256, 384, or 512 bits, respectively. This is known as the fixed-length output (for SHA3-XXX).
- SHA-3 also introduced two new Extendable Output Functions (XOFs): SHAKE128 and SHAKE256. These are adaptable for a range of applications since they may generate hash messages with varied output lengths.
- Distinct Internal Structure: SHA-3 relies on the sponge structure, which is essentially different from SHA-1 and SHA-2, which use the Merkle-Damgård construction. Because of its design, it is immune to length extension attacks, which are a weakness of hashes based on Merkle-Damgård.
- Configurable Parameters: The original Keccak algorithm enables optimization for cryptographic stability and performance on various platforms by allowing for the configuration of parameters like the number of rounds in the f function, the size of the data block, and the size of the algorithm state.
- Domain Separation: To prevent communications from generating identical hash outputs across various Keccak hash function implementations, SHA-3 instances attach domain separation suffixes to the message.
Benefits of SHA-3
Increased Security:
- Resistance to Known Attacks: In light of successful attacks on MD5, SHA-0, and SHA-1, SHA-3 was created as a substitute for SHA-2, meeting the requirement for a distinct cryptographic hash function. There are currently no known vulnerabilities against SHA-3 that have been proven.
- Preimage Resistance: It provides strong defence against preimage Attacks.
- Defence Against Length Extension Attacks: SHA-3’s sponge structure makes it naturally impervious to length extension attacks, which can compromise SHA-2 and other hashes based on Merkle-Damgård.
- Resistance to Quantum Computing: SHA-3 seems to be more resilient to attacks based on quantum computing than SHA-2. Studies reveal that it is highly effective in thwarting preimage attacks that employ Grover’s quantum search technique.
- Tamper Evidence: Any tampering is instantly apparent because even a small change to the original data results in a completely different hash.
Hardware Efficiency
Application-Specific Integrated Circuits (ASICs) provide a great platform for SHA-3. According to the Keccak team, it uses a lot less energy per bit and has a throughput that is an order of magnitude higher for a given circuit size than SHA-2 or other SHA-3 finalists. Keccak is a “green cryptographic primitive” as a result. Platforms such as ARMv8, IBM z/Architecture, and the proposed RISC-V extensions offer hardware acceleration.
Flexibility
The underlying Keccak algorithm’s adjustable parameters and the addition of Extendable Output Functions (SHAKE128, SHAKE256) enable arbitrary output lengths and adaptation to a range of cryptographic requirements.
Drawbacks and Restrictions
Software Speed
On general-purpose CPUs without specific instructions for Keccak operations, SHA-3 has been seen to operate more slowly. For example, on certain Intel CPUs, SHA2-512 can be more than twice as fast as SHA3-512. To get speed comparable to SHA2-256 and SHA2-512, the developers advise utilising SHAKE128 and SHAKE256, but at the cost of halving preimage resistance.
Also Read About Intel Software Guard Extensions SGX In Blockchain Technology
Weakening Controversy (Historical)
NIST first proposed using alternative SHA-3 “capacity” values in 2013, which led to controversy because it would have decreased preimage resistance for some variations. Bruce Schneier and other critics were concerned that it would erode confidence in the algorithm. In subsequent drafts and the final release, NIST successfully addressed these issues by returning to the original idea of c = 2d (where d is output size, c is capacity) for all SHA-2 drop-in replacement instances.
Applications of SHA-3
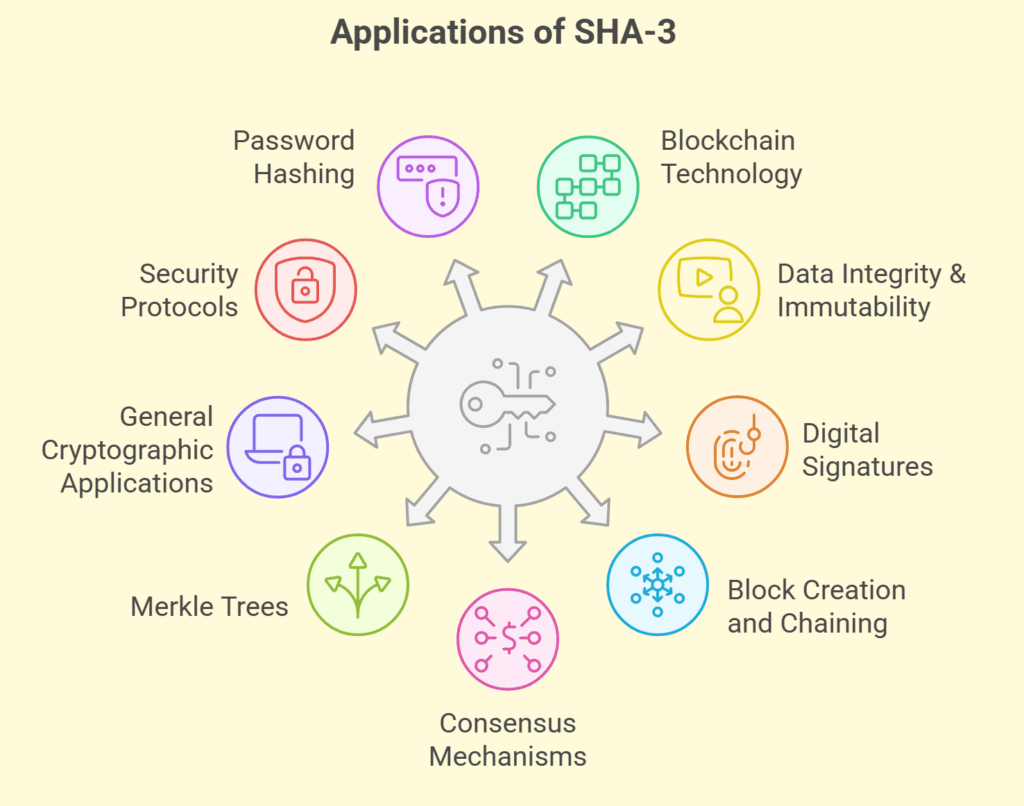
SHA-3 and hash algorithms in general are essential to blockchain technology and contemporary cybersecurity.
- Blockchain Technology: The foundation of blockchain is hashing, which guarantees data security, immutability, and integrity.
- Data Integrity & Immutability: Since hashing transforms transaction information into a fixed-length string, even little changes result in an entirely different hash. Because changing a block requires recalculating the hashes of all following blocks, which is nearly difficult given the computational resources needed, this makes the data resistant to tampering.
- Digital Signatures: To ensure that only authorized users initiate or validate transactions, hashing plays a crucial role in creating cryptographic signatures that confirm the legitimacy and origin of transactions.
- Block Creation and Chaining: To create an unchangeable chain, each block includes a hash of its own data as well as the hash of the block before it.
- Consensus Mechanisms: In procedures like Proof of Work or Proof of Stake, hashing is essential to reaching consensus among network nodes and guaranteeing the legitimacy and sequence of transactions.
- Merkle Trees: Merkle Trees use SHA-3 to effectively arrange and condense several transactions into a block, which lowers the amount of data needed for verification and improves network performance. For instance, Ethereum employs the Keccak-256 hash function.
- General Cryptographic Applications: Used in a variety of computer systems to preserve system security and safeguard private information.
- Security Protocols: Used in secure boot engines, encrypted data storage, e-commerce, financial transaction systems, and IP-sec and TLS/SSL protocol engines.
- Password Hashing: Passwords are hashed using cryptographic hash functions, such as those in the SHA-3 family.
Additional Information
SHA-3 Variants (NIST Standards)
The NIST standard specifies particular SHA-3 example and extendable output functions for SHA-3 variations.
- SHA3-224: A secure hashing technique called SHA3-224 generates a hash value of 224 bits. It is primarily utilized in systems that require a moderate level of security while attempting to conserve space. Digital signatures and low-resource devices benefit greatly from it.
- SHA3-256: Generates a hash digest with 256 bits. One of the most widely used SHA-3 variations is SHA3-256. It provides robust 128-bit security and generates a 256-bit hash result. Blockchains, data verification, and other general-purpose security tasks all make use of this method.
- SHA3-384: Generates a hash digest of 384 bits. SHA3-384 provides a better level of security, around 192 bits, and generates a 384-bit hash. It is frequently utilised in delicate systems where additional data security is crucial, such financial services.
- SHA3-512: Generates a hash digest of 512 bits. SHA3-512 offers the highest level of security (256-bit) and produces a 512-bit result. It is perfect for settings like government and military applications that need the highest level of protection.
- SHAKE128: An arbitrary output length XOF with 128-bit security. A versatile hashing technique, SHAKE128 allows you to select the required output length. It is ideal for use in streaming, custom-length keys, or flexible encryption systems and provides up to 128-bit security.
- SHAKE256: A 256-bit secure XOF that generates an arbitrary output length. Similar to SHAKE128 but with 256 bits of extra security, SHAKE256 is more robust. It is employed in sophisticated cryptography when a flexible output length and excellent security are required.
Also Read About What is Scrypt Algorithm, How it works, And Advantages
| Function | Digest Length | Security Level | Type | Output Length | Common Use Cases |
|---|---|---|---|---|---|
| SHA3-224 | 224 bits (28 bytes) | ~112 bits | Hash Function | Fixed | Lightweight hashing, digital signatures |
| SHA3-256 | 256 bits (32 bytes) | ~128 bits | Hash Function | Fixed | General-purpose hashing, blockchain, integrity checks |
| SHA3-384 | 384 bits (48 bytes) | ~192 bits | Hash Function | Fixed | Enhanced security needs (e.g., high-assurance systems) |
| SHA3-512 | 512 bits (64 bytes) | ~256 bits | Hash Function | Fixed | Maximum security, sensitive data hashing |
| SHAKE128 | User-defined | Up to 128-bit security | XOF (Extendable Output Function) | Variable (arbitrary) | Streaming hash output, flexible length requirements |
| SHAKE256 | User-defined | Up to 256-bit security | XOF (Extendable Output Function) | Variable (arbitrary) | Strong cryptographic hashing with flexible output |
Derived Functions
Other SHA-3-derived functions that NIST has released include:
- Customisable SHAKE, or cSHAKE, allows for explicit domain separation.
- Keyed hash, or KMAC, is a Keccak-based keyed hash function.
- TupleHash: Used to hash string tuples, with result contingent on sequence and content.
- ParallelHash: Developed to take advantage of parallelism in contemporary CPUs to hash data more quickly.
Also Read About Explain Digital Signature Algorithm Definition, Advantages
Subsequent Advancements
- KangarooTwelve: A quicker, 12-round (as opposed to 24-round) variant of Keccak that uses parallelism and tree hashing to achieve great speed, particularly for short messages. 128 bits of security are claimed.
- MarsupilamiFourteen: A 14-round version of KangarooTwelve that boasts 256 bits of security.
- Kravatte and Farfalle construction: An alternative construction and its application to the Keccak-p permutation.
- Sakura tree hashing: This method is based on RawSHAKE.
Hardware Acceleration
When SHA-3 is implemented on hardware rather than software, it can be substantially faster. Keccak algorithms are accelerated by special instructions or hardware aids found in contemporary architectures such as IBM’s z/Architecture, Apple’s A13 SoC (ARMv8), and the proposed RISC-V extensions. For acceleration, software libraries like SSE2 and AVX-512 also employ vectorization.
Implementations
SHA-3 is supported by a number of cryptography libraries, such as Botan, Bouncy Castle, OpenSSL, Golang’s x/crypto/sha3, and Rust’s sha3. Functions for computing SHA-3 hashes are built into both Python and Java.
Example Hash Values
The output hash is significantly changed by a single bit change in the input, illustrating the powerful avalanche effect of SHA-3.
Consider SHA-3 to be a cutting-edge, safe digital mixer. This blender employs a novel “sponge” mechanism in place of more traditional, inflexible systems (such as SHA-2’s predetermined sequence of operations). Any quantity of ingredients (input data) can be added. In its internal container (the 1600-bit state), the sponge then fully combines and jumbles them. Because of its 24 rounds of exact operations, this blending is so thorough and intricate that it is nearly difficult to identify the original components from the hash value of the final smoothie. Additionally, the sponge is extremely resistant to methods that may reveal the recipe if you just knew the output length because it has a concealed “capacity” of information. Because of this, SHA-3 is a very versatile and robust instrument for generating safe, unchangeable digital fingerprints.
