What is a routing attack in blockchain?
A routing attack is a malevolent attempt to take advantage of flaws in the routing system or network architecture in order to alter or interfere with the ordering and transportation of messages and data. The underlying infrastructure, including routers or Internet service providers (ISPs), is the focus of these attacks instead of the blockchain’s code or consensus process.
How Routing Attacks Work
Intercepting, postponing, or rerouting data packets sent between blockchain nodes allows attackers to accomplish their objective. This manipulation may result in:
Routing Protocol Exploitation
Route Flapping
Routes are repeatedly advertised and withdrawn to make routing databases unstable.
BGP Hijacking
Revealing IP address ranges that are inaccurate and outside of the attacker’s control, deceiving networks into sending traffic via malicious systems.
Selective Transmission
Attacker-controlled nodes may target particular users or services by selectively forwarding or deleting communications.
Manipulating Routing Information
Announcing Incorrect Paths
Packets are routed through the attacker’s network when Attacker AS publishes a path to an incorrect prefix.
Exploiting Routing Policies
By controlling which networks they broadcast routes to, attackers might utilize routing policies to target or isolate particular traffic or networks.
Targeting Specific Protocols
Payment Channel Network (PCN) attacks
In order to produce denial-of-service attacks, malicious nodes can pause or cancel transactions in PCNs.
Routing Table Insertion (RTI) Attacks
Attacks that take advantage of flaws in particular routing protocols, such as the Freenet attack described.
Network Partitions
The network can be divided into several discrete parts or chains, with various node groups using different blockchain versions. All traffic may be forced through these broken chains by the malevolent actor acting as a bridge between them.
Disrupting Communication
Attackers can reroute traffic by, in effect, changing road signs, which results in less secure and ineffective information flow between on-chain and off-chain nodes.
Exploiting Centralization
Despite the decentralized nature of blockchains, routing attacks can target any existing points of centralization.
Types of Routing Attacks and Related Network Vulnerabilities
The various kinds of network-based vulnerabilities and routing attacks include:
IP Address Mapping/Transaction Origin Tracking
- By keeping an eye on the time and propagation of transaction traffic, attackers can determine the transaction’s most likely origin and possibly connect accounts to actual people. Transaction transmitters can also be discovered using packet sniffing on unprotected networks.
- Mitigation: Before the transaction spreads widely (Fluff Phase), the Dandelion protocol first passes it sequentially to a single random peer for a number of hops (Stem Phase), hiding the transaction’s origin. Additionally, randomized transaction broadcasting provides some security.
Sybil Attacks
- To obtain an excessive amount of control over network decisions, an attacker fabricates and manages a large number of fictitious identities or nodes. This enables them to circumvent a target node to influence its view of the blockchain (which could result in double-spending), monopolize network control, refuse to relay legitimate blocks, or lower anonymity settings in privacy services like coin mixers.
- Mitigation: Proof of Work (PoW) mitigates this by making influence reliant on processing power. These attacks can be prevented in permissioned blockchains with background verification. Sybil attacks can also be avoided with the aid of Trusted Execution Environments (TEEs) and enhanced privacy identity (EPID) signatures.
DDoS and DoS Attacks
- Flooding a node or network with data, such as zero-fee transactions or wrong blocks, consumes up resources and prevents valid transactions from processing.
- Mitigation: Because blockchain technology is dispersed, it is more difficult to target a single server. Rate limiting in APIs, distributing only legitimate blocks, restricting free transactions, and temporarily banning unruly nodes are among of the measures. Because of verified nodes, Proof of Authority (PoA) is also resistant to DoS assaults.
Eclipse Attacks
Eclipse attacks isolate a network node and may enable a 51% attack by manipulating it to connect only with attacker-controlled IP addresses.
Front-Running
- In order to guarantee that a transaction is executed first and take advantage of market fluctuations, malicious users can submit a similar transaction with a larger gas fee by watching transactions in the memory pool before they are committed.
- Types include suppression, insertion, and displacement.
- Mitigation: To reduce price slippage, strategies such as pre-commit plans, batch auctions, or “mitigations” are used.
Censorship and Network Connection Blocking
- A 51% attack gives the attacker the ability to stop transactions coming from particular addresses. Administrators have the malevolent ability to restrict or reroute connections or exclude users from permissioned networks.
- Mitigation: If a third of bond holders censor for Proof of Stake (PoS), the protocol can modify the rate at which bonds expire, and the bigger network partition may split to censor Byzantine bond holders.
Attacks on Network Communication Protocols
- Even if message content is encrypted, hackers can access data while it is in transit or deduce information from audit trails and metadata.
- For instance, message routing and security may be impacted by problems with Ethereum’s RLPx or DEVP2P protocols, or publicly accessible RPC interfaces.
BGP Hijacking
In order to reroute traffic through their malicious infrastructure and intercept, alter, or interfere with data, attackers broadcast fictitious Border Gateway Protocol (BGP) route information.
Routing Fee Sniping
When an attacker sets up excessive transaction fees on particular routes, users are compelled to pay more or choose other routes.
Probabilistic Payment Fraud
Probabilistic payment fraud occurs when a hostile node pretends a successful transaction was a failure or refuses to produce evidence of payment in order to trick the victim.
Route Flapping
Route flapping is when a malicious node regularly modifies its channel charge structures or restrictions, which makes it hard for other nodes to connect reliably.
Route Leaks
Route leaks occur when a network inadvertently or actively transmits routing information to another network, resulting in traffic taking unexpected routes.
Traffic Interception
Attackers might possibly jeopardize the security and privacy of the data being communicated by using a variety of methods to intercept and examine data packets as they travel over the internet.
Potential Consequences and Impact
Routing attacks may result in serious repercussions:
- Transaction Delays: Processing of transactions may be delayed by interruptions.
- Double-Spending: If nodes are isolated or ignorant of previous transactions, attackers may make it simpler to spend the same cryptocurrency twice.
- Formation of Competing Blockchains: When networks are divided, disparate, incompatible chains may result.
- Denial of Service (DoS): Overloaded networks can render valid transactions unavailable.
- Undermining Trust: Users’ trust in the dependability and security of blockchain networks is undermined by these attacks.
- Attacks frequently take place “behind the scenes,” making it difficult to identify them until harm has been done.
- Computational Resource Waste: Because of delays, miners may expend resources on blocks that are not commonly accepted.
General Mitigation Strategies
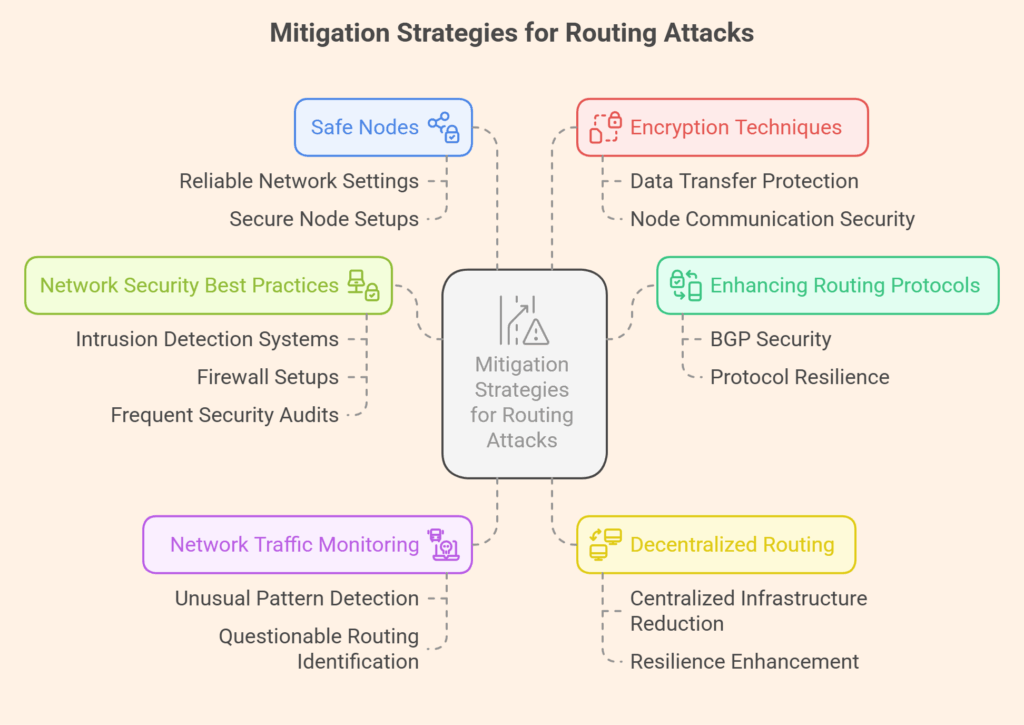
In order to lower the dangers of routing attacks:
- Enhancing Routing Protocols: It is essential to make BGP and other routing protocols more secure and resilient.
- Network Traffic Monitoring: Sturdy network monitoring tools can assist in identifying unusual and questionable routing patterns.
- Decentralized Routing: By investigating decentralized routing options, the network can become more resilient by reducing its dependency on centralized infrastructure.
- Safe Nodes: Making certain that blockchain nodes are set up in reliable and safe network settings.
- Using encryption techniques to protect data transfer between nodes is known as encryption.
- Network Security Best Practices: Adhering to recommended practices, such as intrusion detection systems, firewall setups, and frequent security audits.
Transactions that are not yet part of a published block are nevertheless susceptible to several network and cyber-based attacks, even though blockchain technologies are made to be extremely secure once a transaction is committed. Because blockchain nodes rely largely on internet connectivity, routing attacks emphasize how crucial it is to secure both the blockchain and the underlying network infrastructure that enables it.
