Let us learn about the Network Switches, Network Switch Benefits, Features of Network Switch, Types and comparisons with Hub and Routers.
Network Switch
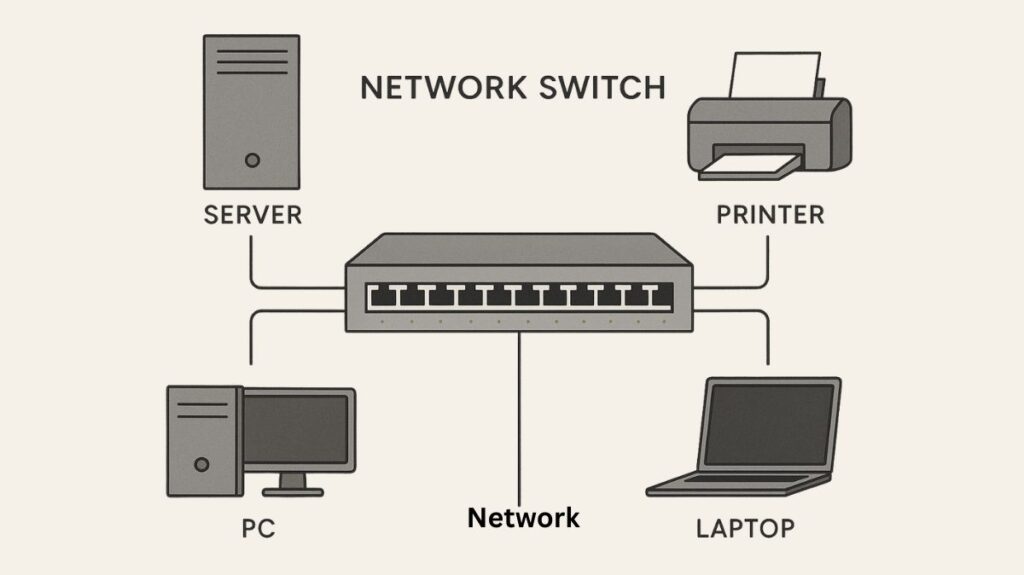
An essential piece of hardware in computer networking, a network switch links several devices including servers, printers, and PCs into a network and enables communication between them by forwarding frames or data packets. Devices on a Local Area Network (LAN) are connected to switches, which serve as the hubs.
How Does a Network Switch Work
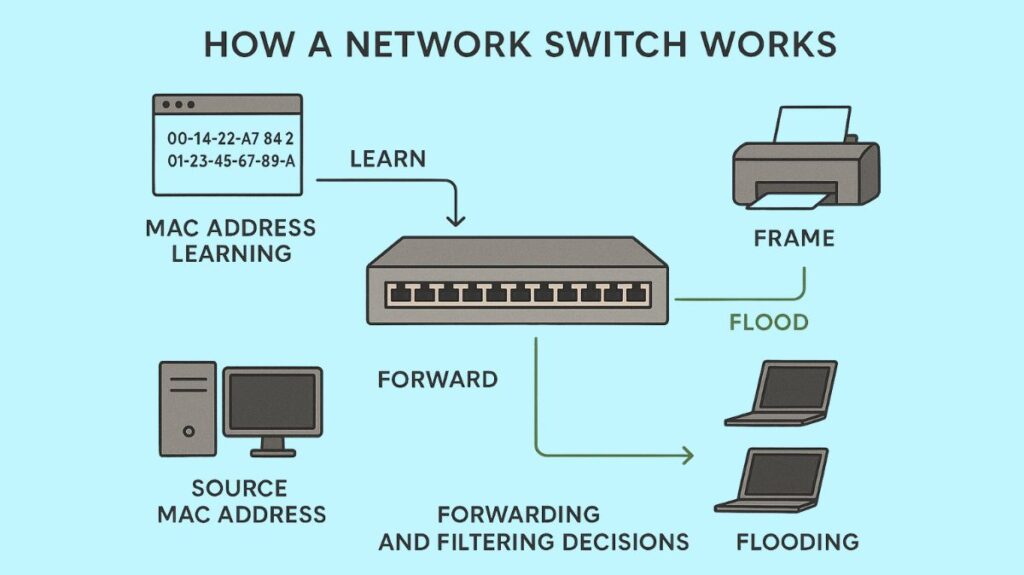
The OSI model’s Data Link Layer, or Layer 2, is where switches typically function. By intelligently forwarding data solely to the intended receiver, switches improve network performance and reduce congestion, in contrast to older devices like hubs that broadcast data to all connected devices. In order to do this intelligent forwarding, switches use a procedure that includes:
MAC Address Learning (Address Learning)
- Additionally referred to as a MAC address table or forwarding table, a switch’s MAC filtering table is initially empty when it is turned on.
- The switch learns MAC addresses by looking at the source MAC address of each frame it receives as it arrives on an input port.
- The source MAC address is linked to the particular port on which it was received by the switch by being stored in its MAC address database.
- This table is created dynamically and kept in RAM. With the display mac address-table dynamic command, you can see dynamically learnt MAC addresses.
- The ageing process of the MAC addresses in the table means that they are finally deleted after a certain amount of time.
Forwarding and Filtering Decisions (Frame Switching)
- The switch determines whether to filter (not forward) or forward a frame based on its MAC address table.
- An arriving frame is filtered by the switch to save needless forwarding and traffic if its destination MAC address is present in the table and points to the same network segment as the source.
- Only the port where the destination device is known to reside receives the frame from the switch if the destination MAC address is on a different segment.
Frame Flooding
- When an incoming frame’s destination MAC address is unknown to the switch (i.e., not listed in its MAC address table), the switch floods the frame by sending it out all ports other than the one it was received on.
- Additionally, broadcast frames and multicast frames are always flooded to all ports within the same broadcast domain (if their destination MAC address is unknown).
Each port on a switch is its own collision domain, therefore this procedure efficiently divides big collision domains into smaller ones. This improves network speed by enabling several devices to broadcast simultaneously without colliding. Communication types supported by switches include broadcast (one-to-all), multicast (one-to-many), and unicast (one-to-one). In order to maximize bandwidth and avoid collisions, they also function in full-duplex mode, which permits simultaneous transmission and receiving.
Features of Network Switch
Intelligent Device: Because switches base their forwarding decisions on MAC addresses, they are thought to be more intelligent than hubs.
Multiport Bridge: Many people refer to a LAN switch as a multiport bridge.
Packet Switching Technique: They transmit, receive, and forward data frames using packet switching.
Error Checking: Before sending data, switches can do some error checking.
Active Devices: Switches are active devices having administration and network software features.
High Port Count: Their ports are usually more numerous, like 24 or 48.
Hardware-based: These days, switches are hardware-based bridging devices that operate at high speeds and low latency by utilizing Application-Specific Integrated Circuits (ASICs).
Types of Switches
Switches can be generally grouped according to their operating layers, management capabilities, and features:
Unmanaged Switches: Small enterprises and household networks frequently employ these low-cost switches. They are easy to set up and begin working as soon as you link them into the network. By using this plug-and-play approach, additional switches can be added as needed. They are known as “u managed” because they don’t need to be set up or watched over.
Managed Switches: Compared to an unmanaged switch, a managed switch has upper control over network configurations and more advanced features. They allow the network administrators to set up, monitor, and administer their network in order to increase its efficacy and protect it from potential intrusions, including hacking. Remote changes are also possible with managed switches via SNMP (Simplified Network Management Protocol). QoS (Quality of Service), VLANs, and redundancy options are among the other protocols that these switches provide.
Layer 2 Switches: A Layer 2 switch functions at the Data Link Layer, Layer 2 of the OSI model. Based on the MAC (Media Access Control) addresses of the devices connected to its network, the switch forwards data packets. Layer II switches determine the proper port for these packets based on MAC in order to enable delivery of this data to specific destination networks. They are most frequently found in Local Area Networks (LAN), where their primary function is to provide various collision domains while reducing congestion within that network.
Layer 3 Switches (Routing Switches/Multilayer Switches): In terms of operating simultaneously at the data link layer (Layer 2) and network layer (Layer 3) in accordance with the Open Systems Interconnection paradigm, a Layer 3 switch is the same as a regular switch. With the use of IP addresses, Layer 3 switches can route packets across several subnets or VLANs (virtual LANs), just like networking devices known as routers do. For large networks that require both rapid switching and routing capabilities, they are hence appropriate.
Power over Ethernet (PoE) Switches: These switches simplify cabling connections and give more flexibility by supplying devices like IP cameras, VoIP phones, and wireless access points with both electrical power and data connectivity via a single Ethernet cable. Advanced PoE switches have the capacity to deliver up to 90 watts per port.
Virtual Switches: These switches are instantiated within Virtual Machine hosting environments and are software-only. They link the data center computers that house virtual machines.
Smart Switches (Partially Managed Switches): These have more restrictions than fully managed switches, but they give you more control over data transfers than unmanaged switches.
Stackable Switches: In order to create a single logical switch from two or more physical switches, these fixed switches can be joined via a backplane cable interface.
Modular Switches: Their slots can accommodate alternative line cards with varied numbers and types of ports, routing, security, and other capabilities, giving them the most flexibility and upgradeability. This permits lifespan longevity and future growth.
Fixed Switches: Fixed switches feature eight, twelve, twenty-four, or forty-eight downlink ports. Devices can be powered by each downlink port, which connects them to a fixed switch. Modular uplink ports with swappable network modules enable the switch’s overall throughput to be increased. Fibre cables for increased throughput or copper cables for PoE can be used to link ports.
Comparison with Hubs and Routers
Hub vs Switches
Layer of Operation: In contrast to Hubs, which function at Layer 1 (Physical Layer), switches function at Layer 2 (Data Link Layer).
Intelligence: Because they use MAC addresses to determine forwarding, switches are more intelligent. Hubs are more straightforward; they only broadcast data to all connected devices and regenerate signals, not recording addresses.
Collision Domains: Switches prevent collisions by establishing distinct collision domains for every port. Because hubs only use one transmission stream, communication collisions happen frequently.
Traffic: Switches only forward data to the designated destination, which helps to reduce network congestion. By copying packets to each device, hubs create congestion.
Network Switches vs Routers
Layer of Operation: Although sophisticated switches can function at Layer 3, they are mainly Layer 2 devices. In general, routers are Layer 3 devices.
Addressing: To determine where to deliver data packets within a LAN, switches use MAC addresses. Routers route data packets to the internet or between several LANs using IP addresses.
Scope: Within a single LAN, switches link devices. Routers are used to link LANs to the internet or other networks.
Data Units: Data frames are commonly utilized by switches. Routers employ packets of data.
Sophistication: Typically more advanced, routers use routing algorithms to guide data over wide networks.
Network Types: The use of switches is limited to wired network connections. Routers are compatible with both Wi-Fi and wired networks.
Services: Traditional Layer 2 switches usually do not provide Network Address Translation (NAT), NetFlow, or Quality of Service (QoS), although routers frequently do. Modern switches, however, can include advanced functionality like routing.
Switching Methods
Various techniques that switches employ to forward frames might impact reliability and latency:
Store-and-forward switching: After receiving the frame, the switch stores it in its buffers. In order to assess data integrity, it then runs a Cyclic Redundancy Check (CRC) and verifies that the frame length is between 64 and 1518 bytes. The frame is sent to its destination if it is error-free and legitimate. Although this approach provides error detection, it increases latency because forwarding cannot start until the complete frame has been received.
Cut-through switching: Before forwarding the frame, the switch reads only its destination MAC address. Although there is less latency with this approach, error detection is not possible.
Fragment-Free switching: a variation of cut-through switching in which the switch does not forward until the first 64 bytes of the frame—known as the collision window—have passed. With virtually little increase in latency, this offers superior error checking over pure cut-through because the majority of errors happen inside the first 64 bytes. Some older switches were set to this by default.
Key Switch Concepts
Spanning Tree Protocol (STP/RSTP)
- RSTP (Rapid Spanning Tree Protocol) and STP (IEEE 802.1D), its faster variant, are essential for avoiding network loops in Layer 2 switched systems with redundant links.
- By setting some connections to standby or blocking mode, STP avoids loops. By default, when a switch is turned on, all of its ports are blocked.
- Each non-root switch selects a root port to connect to the root switch at the lowest cost in STP, which requires electing a root bridge (the switch with the lowest Bridge ID).
- For every LAN segment, switches also choose a dedicated port (DP).
- To ascertain the STP topology, bridges and switches exchange Bridge Protocol Data Units (BPDUs).
- In contrast to regular STP, RSTP enables neighbour searches for faster convergence and each switch generates its own Hellos independently.
Trunking and Dynamic Trunking Protocol (DTP)
- A switch port known as a trunk is capable of carrying traffic for several VLANs, with each frame being identified by a distinct VLAN ID (for example, using IEEE 802.1Q encapsulation).
- Two switches can negotiate a shared trunking mode using DTP, a Cisco proprietary point-to-point protocol.
- The following are typical trunking administration modes:
- on: compel the port to enter trunking mode permanently.
- access: A non-trunk (access) port is always in use.
- dynamic desirable: starts sending out negotiation messages and makes an effort to become a trunk. Newer Cisco switches frequently have this as their default setting.
- dynamic auto: In order to become a trunk, it waits passively for negotiation messages.
- nonegotiate: DTP frames are not sent by the local port since it is in an unconditional trunking state.
EtherChannel
- EtherChannel technology enables switches to combine several physical links into a single logical channel for redundancy and enhanced capacity.
- It can be set up dynamically or manually using protocols like LACP (Link Aggregation Control Protocol) and PAgP (Port Aggregation Protocol).
- Source/destination MAC addresses, IP addresses, or TCP/UDP ports can be used to configure load distribution over the bundled links.
Port Security
- Port security uses MAC addresses to limit access to a switch interface.
- You can set it up to enable predetermined MAC addresses or to learn MAC addresses dynamically (switchport port-security mac-address sticky).
- The switch may respond to a violation by sending out messages, deleting frames, or stopping the interface.
Switch Interfaces and Management
- The phrases switch interface and switch port are interchangeable.
- Interface speed and duplex parameters can be configured and checked, frequently with the help of autonegotiation (IEEE 802.3u).
- An Ethernet interface’s Auto-MDIX (automatic medium-dependent interface crossover) capability enables it to identify and fix improper cable pinouts, such as straight-through cables that require a crossover.
- There are data, control, and management planes on switches. The control plane controls and modifies the data plane (e.g., STP, interface settings), the management plane handles features like Telnet and SSH for device administration, and the data plane conducts frame forwarding.
- Along with Layer 2 switching, Layer 3 switches (also known as multilayer switches) can also carry out simple routing tasks between VLANs. Switched Virtual Interfaces (SVIs) are frequently used for VLAN routing.
Network Switch Benefits
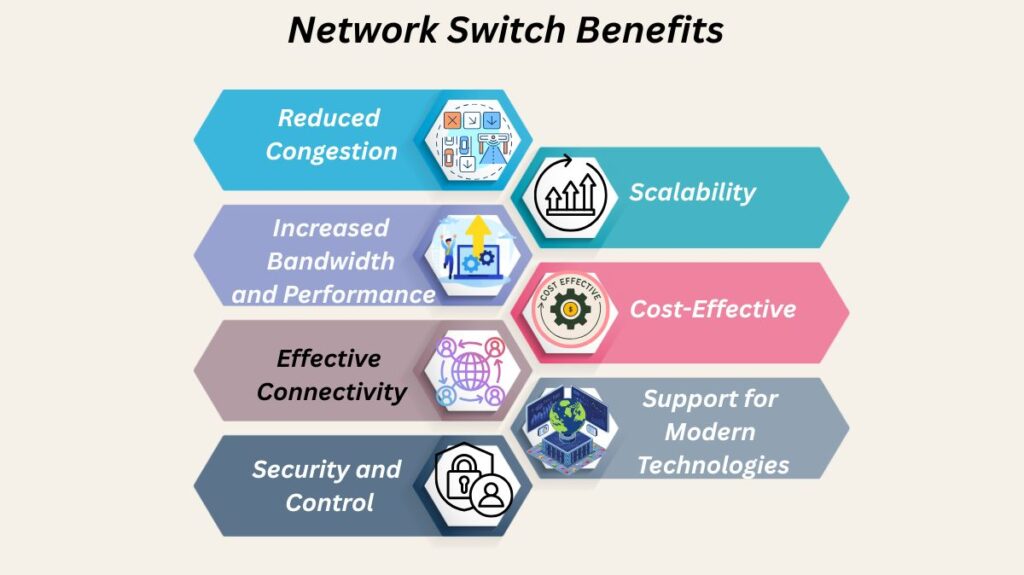
For effective network connectivity and information transfer, switches are essential. They provide a host of advantages:
Reduced Congestion: They reduce needless traffic by clever data forwarding.
Increased Bandwidth and Performance: By maximizing available bandwidth, they enable parallel device communication in an environment that is almost completely free of collisions.
Effective Connectivity: They give networked devices automated link connections, which improve speed and usability.
Security and Control: They offer control over data transport and support features like port security and VLANs, making the network more dependable and safe.
Scalability: With the help of switches, networks may safely grow to accommodate anywhere from three to thousands of devices. To accommodate even more, additional switches can be connected.
Cost-Effective: Switching to a switched LAN environment saves money by allowing the cabling and gear to be reused.
Support for Modern Technologies: Many contemporary switches can gather data from Internet of Things devices for use with artificial intelligence (AI) and machine learning algorithms, and they offer Power over Ethernet (PoE) for powering devices.
Evolution and Advanced Capabilities
More functionalities that were formerly handled by other network components are frequently incorporated into today’s sophisticated switches. They are capable of:
- Combine the functions of switches and routers to eliminate the need for extra hardware.
- Previously handled by specialised firewalls, include security features.
- Assist wireless access points with their throughput requirements by delivering varying speeds (e.g., multigigabit switches that offer 2.5, 5, or 10 Gbps or more).
- As network sensors, use AI and machine learning to gather information for well-informed decision-making and provide automation and insights based on AI.
- Be programmable, enable software-defined networking (SDN), have analytics tools and network monitoring apps, and have APIs for direct network communication.
- Allow for the safe segmentation of specific systems while connecting a large number of systems to a single physical network by supporting virtual networks such as VLANs, VPNs, and EVPN-VXLANs.
- Apply cutting-edge switching techniques such as Fragment-Free, Store-and-Forward, and Cut-through.
Setting Up a Network Switch
Usually, setting up a network switch entails:
- Deciding on a switch purchase based on network specifications.
- Attaching a cable to a switch and connecting it directly to a router via a port, usually an uplink port.
- Establishing the linked devices’ IP addresses.
Leading manufacturers such as Cisco and Juniper provide enterprise-class switches with features like port security, trunking for VLANs, EtherChannel for link aggregation, and Spanning Tree Protocol (STP/RSTP) for loop prevention. These switches can be controlled through a Command-Line Interface (CLI) with operating systems like Cisco IOS or Juniper OS.
