Explore the architecture of a RADIUS server. Understand the roles of the client and the server, and discover How Does A RADIUS Server Work, uses, and Functions.
RADIUS Server
An open standard protocol created by the Internet Engineering Task Force (IETF) is a networking server known as a RADIUS Server (Remote Authentication Dial-In User Service). Centralized authentication, authorization, and accounting (AAA) administration is offered to users and devices connecting to network services through its client/server architecture. Unlike setting individual network devices, RADIUS centralizes security information by managing user accounts, passwords, and access controls, improving scalability.
RADIUS Servers, in short, make guarantee that only authorized users may access a network and give administrators access to comprehensive usage information.
RADIUS Server Functions (AAA Services)
In addition to offering accounting supervision, RADIUS integrates authorization and authentication into a single process.
Authentication: This feature compares a user’s or device’s credentials (such as username and password) to a database, like Active Directory or LDAP, to confirm the identity of those seeking to access the network. Access is allowed to the user if the credentials are legitimate; if not, access is refused.
Authorization: Following successful authentication, authorization establishes the extent of access to certain services that the user is allowed to utilize. For example, the type of service, permitted connection times, or even the IP address to be assigned can all be specified by the RADIUS server and sent to the client.
Accounting: This service keeps tabs on resource usage and user behaviour. Information like session length, data usage (measured in bytes), login and logout times, IP addresses utilized, and services accessed are all recorded. This data is essential for network management, billing, and auditing and is kept in logs on the RADIUS server.
You can also read NTP Server Configuration And How Does NTP Server Work?
How does a RADIUS Server Work
These steps are usually involved in the process:
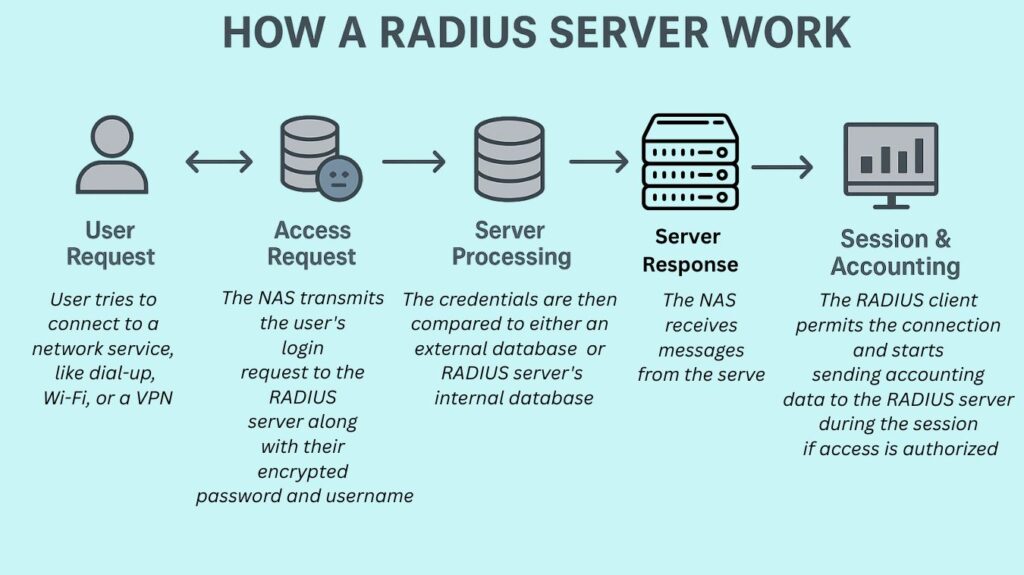
User Request: User tries to connect to a network service, like dial-up, Wi-Fi, or a VPN.
Access Request: As the RADIUS client, the network access server (NAS) (such as a router, switch, or wireless access point) transmits the user’s login request to the RADIUS server along with their encrypted password and username. Remarkably, RADIUS only encrypts the password in the access-request packet; the remainder of the payload is left unprotected.
Server Processing: The credentials are then compared to either an external database, such as Active Directory, or the RADIUS server’s internal database.
Server Response: The NAS receives one of the following messages from the server:
- Accept (Access-Accept): Shows that access has been given after the user’s authentication and authorisation have been successful.
- Reject (Access-Reject): Signifies that access is prohibited and that the login and password are invalid.
- Challenge (Access-Challenge): Asks for more details from the user, like for multifactor authentication.
- Change Password: Tells the user to choose a different password.
Session & Accounting: The RADIUS client permits the connection and starts sending accounting data (Accounting-Start, Accounting-Stop, and periodic updates) to the RADIUS server during the session if access is authorized. This session information is logged by the server.
RADIUS Server Architecture and Components
Client/Server Model: The authenticating device (such as a router, switch, or access point) acts as the client and queries the RADIUS server in the client/server model that RADIUS uses. A Network Access Device (NAD) or Network Access Server (NAS) are common names for this client device.
RADIUS Server: The main server, usually a Windows or Unix machine, that handles AAA requests.
Shared Secret: Both the RADIUS client and server have this important case-sensitive key set up. It guarantees secure data exchange and encrypts communications.
Protocols and Ports
The User Datagram Protocol (UDP) is the communication protocol used by RADIUS.
- Modern RADIUS servers usually use UDP port 1812 for authentication.
- Commonly, UDP port 1813 is used for accounting.
- In older RADIUS setups, UDP port 1645 may be used for authentication.
RADIUS Server Uses
RADIUS servers are widely used to guarantee that a network is only accessible by authorized users. Applications that are often used include:
- WPA2-Enterprise/WPA3-Enterprise schemes and 802.1X for SSID security are particularly important for protecting Wi-Fi networks in businesses, academic institutions, and other establishments.
- Granting remote workers access to a VPN.
- Overseeing broadband or dial-up access for ISP services and verifying ADSL connectivity subscribers.
- Limiting access to wired network ports (Ethernet) for users connecting to networks in businesses and educational institutions.
- Wireless LAN Controllers (WLCs) management features can only be accessed by authenticated wireless administrators.
Configuration on Cisco Devices
RADIUS server configuration for AAA services is supported by Cisco routers and switches. This usually entails:
- With the aaa new-model command, AAA services are enabled.
- Establishing the IP address and shared secret key for the RADIUS server.
- A AAA group is added to the server.
- This RADIUS group is used when configuring default login authentication, frequently with a fallback to local authentication to preserve access in the event of an outage. RADIUS server configuration for WLCs can be completed through a web browser by inputting the IP address, port number, and shared secret of the server, and then turning it on for particular user types. Globally and per WLAN, WLCs can handle numerous RADIUS servers. Cisco provides AAA services, such as RADIUS, through its Identity Services Engine (ISE) and older Access Control Server (ACS) platforms.
RADIUS Server Comparison with TACACS+
RADIUS and TACACS+ are both AAA protocols, although they differ in a few important ways:
Standard: The Cisco proprietary protocol TACACS+ is different from the open standard RADIUS.
Transport: Whereas TACACS+ utilizes TCP port 49, RADIUS uses UDP.
AAA Separation: TACACS+ divides the AAA tasks of authorization and authentication, whereas RADIUS merges them into a single procedure.
Encryption: The entire packet between the server and the client is encrypted by TACACS+, whereas RADIUS merely encrypts the password in the access-request packet.
Authorization Granularity: Whereas RADIUS is mainly utilized for remote access and wireless user authentication, TACACS+ provides more precise control over command authorization, making it generally more appropriate for device deployment.
You can also read Network Print Server, How It Works & Types Of Print Servers
