What is a Network Security Threat?

Any action, occurrence, or weakness that could harm, steal, or interfere with data, devices, or communication within a computer network is considered a network security threat. These risks take advantage of flaws in software, systems, or human conduct to obtain illegal access, hurt others, or profit from sensitive data.
Malware, phishing, DDoS attacks, man-in-the-middle attacks, and insider threats are examples of threats to a computer network’s availability, confidentiality, or integrity that aim to interfere with normal business activities, steal information, or obtain unauthorised access. These sophisticated threats try to breach data and take advantage of system flaws, which can result in operational and financial harm.
To comprehend network security threats, one must know a few fundamental terms:
Asset: Anything valuable to a company that requires safeguarding. Intangible assets like intellectual property, database data, contact lists, accounting data, and a company’s reputation are included in this, as are physical assets like people and computers.
Vulnerability: A flaw that could jeopardise safety. It is an exploitable weakness in an operating system, application, protocol, or system design. Every day, new vulnerabilities are found.
Also Read About What Are The Common Network Security Vulnerabilities?
Exploit: The particular technique or tools used to breach an asset by taking advantage of a vulnerability.
Risk: The possibility of an asset being harmed, compromised, destroyed, or accessed without authorisation. It happens when a threat is present and countermeasures are either insufficient or nonexistent. Effective countermeasures lower total risk by decreasing the chance that a threat will succeed.
The way a threat actor enters a server, host, or network is known as the attack vector. These may come from within a network or from outside of it.
How Network Security Threats Work?
Threat actors use a variety of instruments and techniques to initiate assaults and take advantage of vulnerabilities in networks. These techniques frequently seek to obtain unauthorised control, steal data, or interfere with operations:
Spoofing attacks entail fabricating a frame or packet’s originating address. In order to hide their identities and make innocent people seem to be the attack’s source, attackers frequently spoof source IP addresses. It is also possible to trick hosts and routers on a local network by spoofing MAC addresses in ARP replies.
Denial-of-Service (DoS) attacks try to prevent authorized users from accessing network services by overloading the network, bringing down systems, or severely slowing them down. A UDP flood attacks is one example, in which a large number of UDP packets are sent to a server, frequently from a spoof host, resulting in excessive traffic and bandwidth use. Another kind of DoS attacks is a distributed denial-of-service (DDoS) attack.
Reconnaissance attacks are methods of discovery in which the attacker maps a network and determines its systems, resources, and possible weaknesses. Usually, the first stage in getting ready for a bigger attack is this.
In a man-in-the-middle (MitM) attack, two parties’ communications are intercepted by the attacker. An attacker can view data that isn’t encrypted, including private information like passwords and usernames. Layer 3 (such as a rogue router tampering with routing protocols) or Layer 2 (such as MAC address spoofing or modifying Spanning Tree Protocol to become the root switch) are two possible locations for MitM attacks.
Malware, often known as malicious software, is code created with the intent to harm, interfere with, steal, or perform unauthorized operations on data, hosts, or networks. Typical kinds include of:
- Viruses: Affix themselves to trustworthy programs and propagate when they are run.
- Worms are self-propagating programs that can cause system crashes by spreading throughout computers, frequently by making copies in memory.
- Trojan horses are malicious software applications that pose as trustworthy software.
Password attacks Brute-force attacks, dictionary attacks, and password guessing are examples of password attacks. Passwords and usernames that aren’t encrypted can also be revealed by eavesdropping.
Social engineering is the practice of deceiving users into divulging private information or taking activities that jeopardise security. This can be accomplished through malicious websites (pharming, watering hole attacks), emails (phishing, spear phishing, whaling), or even face-to-face encounters.
Eavesdropping the practice of secretly listening to network traffic in order to get private company information is known as eavesdropping (also known as network snooping or packet sniffing), particularly when the packets are not encrypted by default.
Also Read About What Is Inter VLAN Routing And How Inter VLAN Routing Works
Trust Exploitation when an attacker uses poorly configured trust models, like firewalls with incorrect access rules or misconfigured directory services like Active Directory or Network File System (NFS), to obtain unauthorized access to internal networks from less secure zones (like the DMZ), this is known as trust exploitation.
- Another frequently stated attack type is buffer overflow attacks.
- VLAN, DHCP, and ARP assaults are examples of LAN-specific attacks.
- MAC spoofing and CAM table overflow attacks are also included in Layer 2 attacks.
History of Network Security Threats
The field of network security has changed significantly:
Early Networks
Coaxial cabling was used to connect devices to physical buses in the beginning. This was followed by 10BASE-T and UTP cabling with hubs. Strong security was absent from these early LANs. By just connecting a network analyser to a hub, anyone could view all traffic or access network resources.
TCP/IP Origins
The United States developed the Transmission Control Protocol/Internet Protocol (TCP/IP) package. Early understanding of resilience and security is highlighted by the Department of Defense’s (DoD) fundamental mission to sustain communications and ensure data integrity even in the event of catastrophic warfare.
Development of Security Focus
When LANs initially appeared in the early 1980s, security was frequently an afterthought rather than a primary concern. However, security quickly rose to the top and became a mission-critical component of business networks as networks expanded rapidly and became necessary for daily operations.
Wireless Security
Since data is transferred over the air and is susceptible to interception by anybody nearby, wireless connections pose special security risks. Wired Equivalency Privacy (WEP), one of the earliest wireless security systems, had serious flaws and frequently sent private data “in the clear”. As a result, new secure standards like WPA, WPA2, and WPA3 were created.
Also Read About How Does Distance Vector Routing Work And Examples
Current Threats
Cybercriminals have developed the skills and resources needed to carry out complex assaults, including ones that have the ability to bring down vital systems and infrastructure. Because threats are ever-evolving, security procedures must be updated and vigilantly monitored.
Why Network Security is Important?
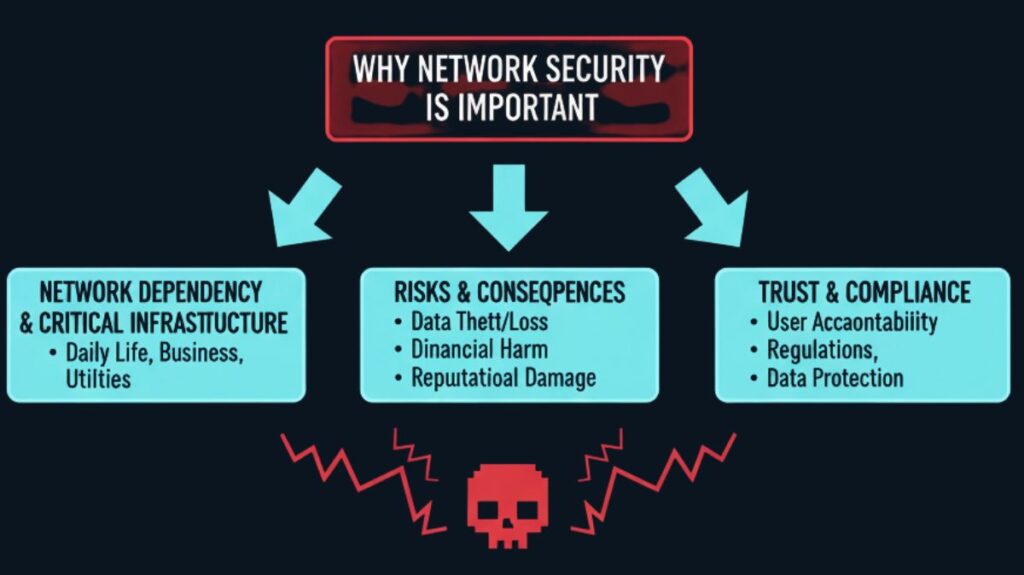
Network security is crucial due to:
- Network Dependency: Because wired and wireless computer networks are so important to people’s daily lives, it is imperative that they be protected.
- Devastating Consequences: Because of the theft or corruption of vital data and assets, unapproved intrusions and attacks can cause expensive network outages, a great deal of work loss, and severe financial and reputational harm.
- Critical Infrastructure Protection: Threat actors have the ability to interfere with vital systems and infrastructure.
- Trust and Compliance: It is necessary to take precautions because not all network users can be relied upon to follow the regulations. Strong security implementation is also motivated by regulatory compliance.
- Core Security Objectives (CIA Triad): Generally speaking, network security seeks to guarantee:
- Confidentiality: Keeping sensitive or classified data out of the hands of unauthorized people or systems, whether the data is on storage media or moving across a network. The main methods for doing this are encryption and, if at all possible, sending private information over other networks.
- Integrity: Verifying that information hasn’t been altered, altered, or distorted while being transmitted or stored.
- Availability: Ensuring that authorized users have access to data and systems at all times. Availability is the immediate target of denial-of-service attacks.
Network Security Threats Types
Threats to network security can be grouped, level of complexity, or goal:
Threats by Origin/Sophistication
- Unstructured Threats: Frequently started by inquisitive people, frequently referred to as “Script Kiddies,” who use easily accessible resources and data from the internet. They usually lack extensive technical skills and are motivated by thrills or the ability to brag.
- Structured Threats: Performed by highly skilled, technically proficient, and cunning individuals or organisations. These actors write their own hacking scripts, are frequently repeat offenders, and have a thorough awareness of network architecture and vulnerabilities.
- External Threats: These threats come from sources outside the network, such the internet. These are typical as most businesses have a strong online presence.
- Internal Threats: These originate from within the network, usually from staff members. Because internal users already have permitted access and are familiar with the network, they can swiftly wreak major harm, making them especially difficult to discover and stop.
Primary Network Attacks by Objective
- Identifying resources, systems, and possible vulnerabilities, as well as mapping network topology, are examples of reconnaissance attacks. This data is frequently utilised as a prelude to more focused attacks in the future.
- Access Attacks: These are intended to obtain information, obtain unauthorised access, or increase authority within a system or network. Intellectual challenge, theft, and business espionage are only a few examples of motivations.
- Denial of Service (DoS) Attacks: These attacks try to stop authorised users from using network resources by destroying or preventing network services from functioning. This may entail slowing down or crashing systems to make them unusable. UDP floods, SYN floods, reflection attacks, and amplification assaults are a few examples.
Common Specific Network Attack Types
- Eavesdropping, which includes packet sniffing and network snooping.
- Unauthorised entry.
- WareZ.
- IP spoofing, or masquerade attacks.
- Replaying or hijacking a session.
- Rerouting.
- Refusal.
- Smurfing, an ICMP-based DoS attack.
- Password attacks, such as dictionary, guessing, and brute-force attacks.
- Attacks by a man in the middle.
- Attacks at the application layer.
- Attacks using HTML.
- Watering Hole Attacks, Smishing, Whaling, Phishing, Spear Phishing, and Pharming (social engineering techniques).
- Local area network-specific attacks, such as VLAN, DHCP, and ARP.
- Layer 2 specialized MAC spoofing and CAM table overflow attacks.
- A zero-day vulnerability is one that the people who should be interested in mitigating it are unaware of.
Sources of Vulnerabilities:
- Problems with the policy.
- Mistakes in design.
- Flaws in the protocol.
- A configuration error.
- flaws in software.
- Human factors, such as users falling for social engineering scams.
- Malicious software.
- vulnerabilities in hardware.
- The ability to physically access network resources.
Advantages
Although network threats by themselves don’t benefit the defender, putting strong network security measures in place has several advantages:
- By restricting switch interfaces to only permit expected devices, port security lessens the vulnerability to assaults in which unauthorised devices connect to unused switch ports or wall sockets.
- DHCP Snooping: A Layer 2 security feature that functions as a firewall by differentiating between trusted and untrusted interfaces, verifying DHCP packets, and stopping rogue DHCP servers.
- Dynamic ARP Inspection (DAI): This switch feature aids in thwarting ARP attacks and Layer 2 address spoofing.
- Firewalls and Next-Generation Firewalls (NGFWs): They can thwart attacks by filtering packets, monitoring traffic, and removing harmful data. Full packet reassembly, deep packet inspection up to Layer 7, application visibility and control (AVC), and intrusion prevention system (IPS) policies are just a few of the sophisticated features that NGFWs offer. They guard against unauthorised users, harmful data, protocol flaw exploitation, and the exposing of sensitive systems.
- Intrusion Prevention Systems (IPSs): Keep an eye on in-line traffic to identify whether it’s part of an exploit or not, and block attacks by removing harmful data. In contrast to Intrusion Detection Systems (IDS), which simply identify attacks, IPS can both detect and block them.
- Secure communication over public, untrusted networks, such as the Internet, is made possible by virtual private networks, or VPNs. Through data integrity, encryption, authentication, and anti-replay features, VPNs offer confidentiality. They provide a secure WAN solution that is affordable and accessible worldwide.
- Encryption: This method can identify the sender and jumble data to prevent unauthorised readers from reading it. An industry-standard framework for safe IP-based data transfer is called IPsec. Encryption is included into wireless security protocols such as WPA, WPA2, and WPA3.
- Routers are equipped with Access Control Lists (ACLs) to regulate packet flow, filter traffic according to IP addresses and TCP/UDP ports, and shield sensitive equipment from unauthorised access. IP spoofing, DoS TCP SYN attacks, smurf attacks, and ICMP message filtering are just a few of the attacks they can prevent.
- In order to prevent remote access and management traffic from being intercepted, a network protocol called Secure Shell (SSH) creates a safe, encrypted route for data transmission between networked devices.
- Training and User Awareness: Crucial components of a successful security program. Since users are a major vulnerability, educating them about security risks and adherence to corporate standards is essential to threat mitigation.
- Physical Access Control: Using keypads or locks to secure network equipment in areas with restricted access lowers the possibility of theft or tampering.
- Shutting Down Unused Ports: This stops unauthorised devices from connecting to the network, which may cause information vulnerabilities or network disruptions.
- Antivirus software: This program scans files to stop malware infestations on workstations and servers; in order to stay effective, virus signatures must be updated frequently.
- Rather than using a single point of control, the defense-in-depth approach makes use of several layered security methods. The network is protected by the remaining layers even if one is compromised.
Disadvantages of Network security threats
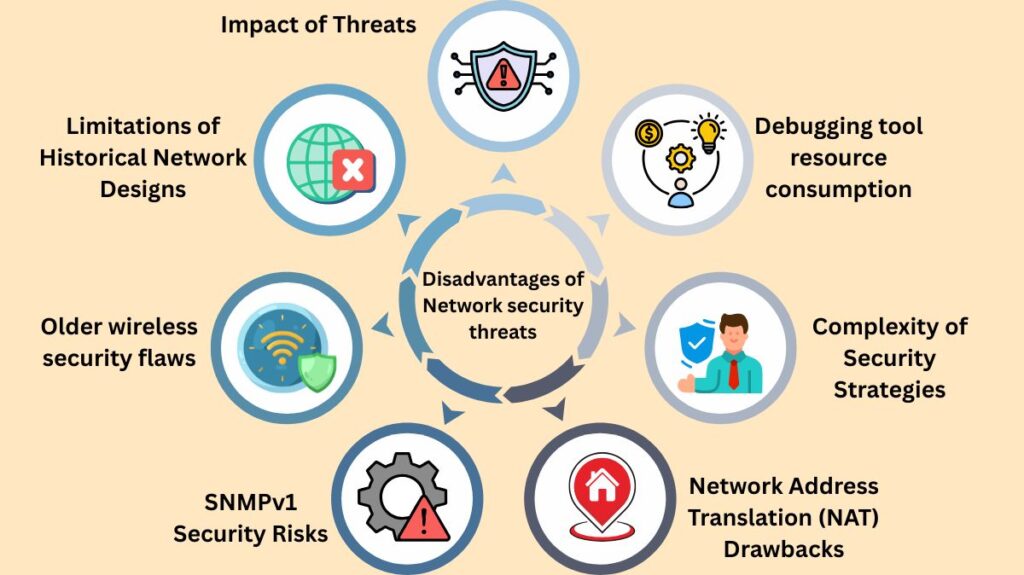
- Impact of Threats: The primary drawbacks of network security threats are expensive network outages, lost productivity, data theft, financial consequences, and harm to vital infrastructure, as explained in the “Why it is important” section.
- Limitations of Historical Network Designs: Hubs and bridges were the mainstay of earlier network topologies, which were fundamentally insecure and inefficient. By creating expansive broadcast domains, they made it simple for anyone to join a workgroup or examine traffic by just connecting a workstation or network analyser.
- Older wireless security flaws: WEP and other early wireless encryption protocols had serious problems and frequently sent data in “cleartext,” making them insecure for business settings without proprietary solutions.
- SNMPv1 Security Risks: SNMPv1 poses a security risk since it transmits community strings, or authentication strings, in plain text, which makes them susceptible to spoofing and interception.
- Network Address Translation (NAT) Drawbacks: Although NAT is advantageous, the sources point out that there are “downsides” or a “dark side” that network engineers should take into account before putting it into practice. However, the paragraphs that are presented do not go into specific disadvantages.
- Complexity of Security Strategies: Excessively intricate security plans may backfire, be challenging to execute properly, and maybe introduce unanticipated security flaws.
- Debugging tool resource consumption: Cisco IOS commands such as debug are high-overhead operations that can force packet process switching and use a lot of router resources. They are not intended for ongoing monitoring, but rather for temporary troubleshooting.
Network Security Applications
Threats to network security and ways to mitigate them apply to every facet of contemporary networking:
- Enterprise Networks: To guarantee authentic communication and guard against breaches that could impair operations, security is essential for all devices, including endpoints, servers, routers, and switches.
- Local Area Networks (LANs): VLAN, DHCP, and ARP attacks are among the dangers that must be addressed in order to protect LANs. Switches are specifically equipped with Layer 2 security capabilities, including as port security, DHCP snooping, and Dynamic ARP Inspection (DAI), to safeguard the access layer.
