We discussed Buffer overflow attack in this topic, including their history, how it Works, different types of buffer overflow attacks, advantages, disadvantages, applications, mitigation, and prevention.
Buffer overflow attack
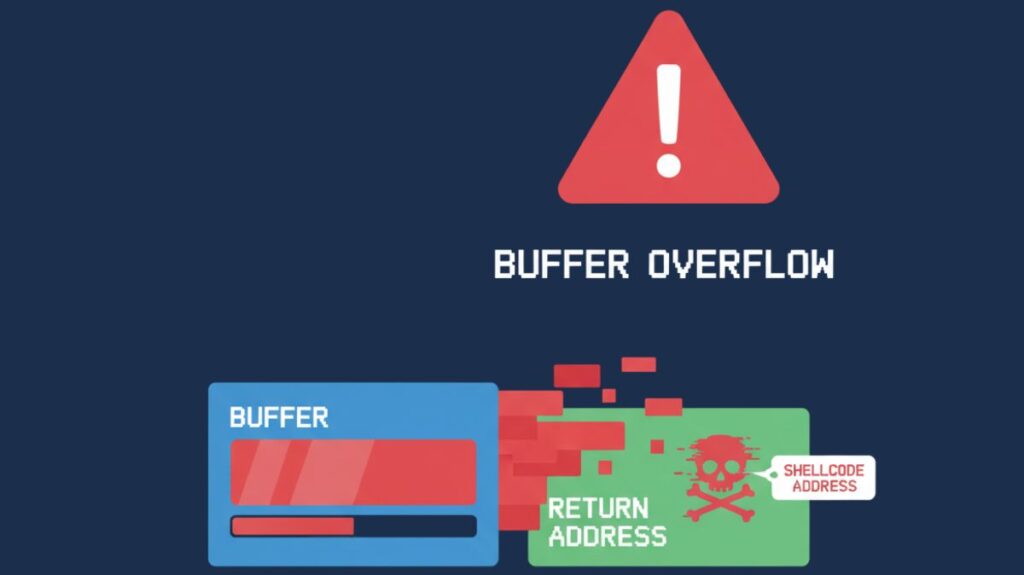
When a program attempts to write more data into a buffer a fixed-length memory area than it can accommodate, it is known as a buffer overflow attack. This extra information “overflows” the buffer’s edge and replaces nearby memory, which may include important information or commands. An attacker can insert and run their own malicious code thanks to this memory modification.
History
With the Morris Worm in 1988, buffer overflow was first brought to the public’s attention as a security flaw. This worm showed the devastating potential of this attack vector by quickly spreading over the internet by taking advantage of a buffer overflow in the fingerd service on early Unix systems. Buffer overflows have since become a common feature of cyberattacks and continue to pose a serious risk, causing flaws in popular operating systems and software.
Also Read About What Are Spoofing Attack Types? How It Works, And Advantages
How it Works
The attack focusses on a program’s memory management, particularly the heap or stack.
- Buffer Allocation: To store user input, a program sets aside a buffer of a given size in memory, such as 10 bytes.
- Excessive Input: An attacker transmits a data string that exceeds the allotted size, such as 20 bytes.
- Overflow: The full 20-byte string is written into the 10-byte buffer by the software since it does not have adequate boundary checks. The neighbouring memory region is overwritten by the additional 10 bytes that flow out.
- Code Injection: Malicious code and a return address are purposefully crafted into the overflowing data by the attacker. The attacker’s code is shown by this updated return address. When the software completes its duty, it jumps to and runs the attacker’s code rather than going back to its regular function.
Different types of buffer overflow attacks
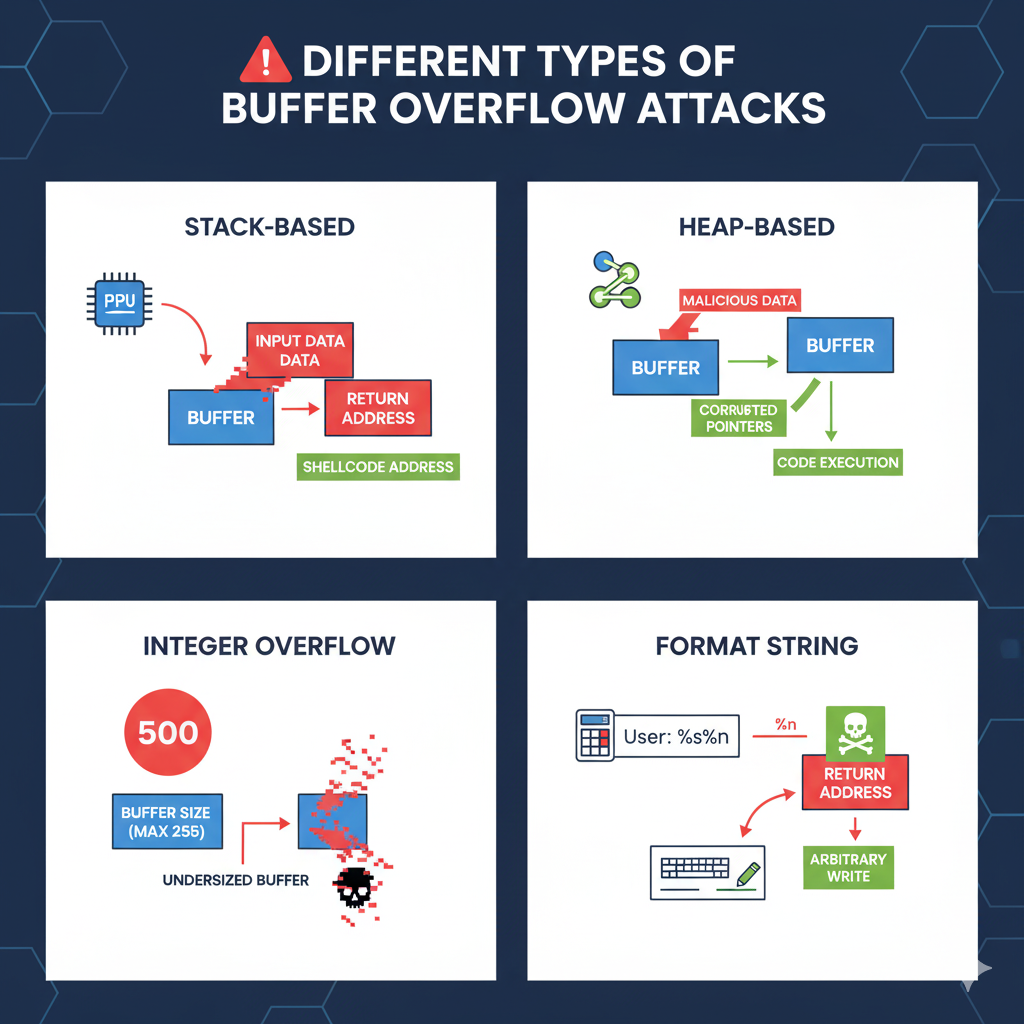
Stack-based Buffer Overflow
The most prevalent kind is the traditional buffer overflow attack. It happens when a program pushes data over the edge of a call stack buffer. Local variables, function arguments, and the return address the address the program should go to after the function is finished are all stored in the stack, a section of memory that functions employ.
An attacker supplies input that exceeds the stack-allocated buffer in order to exploit it. The return address on the stack is overwritten when the extra data overflows. The address of the attacker’s malicious code, sometimes referred to as shellcode, can then be used in place of the valid return address. The software leaps to the attacker’s code rather than its intended destination when the function returns, giving the attacker complete control over the program.
Heap-based Buffer Overflow
The buffer allocated on the heap, a section of memory utilised for dynamic memory allocation, is the target of this attack. The application controls the heap’s memory at runtime, unlike the stack (for example, by using C’s malloc()). Program data is stored in the heap instead of function control data, such as return addresses.
How to exploit it: Because heap overflows cannot directly take over a program’s execution by overwriting a return address, they are more complicated than stack overflows. Rather, attackers usually take advantage of the data structures that the heap management itself uses. To reroute the program’s flow or corrupt other data structures, they could, for instance, rewrite function pointers or other important information kept on the heap, resulting in a denial of service or improper code execution.
Integer Overflow
When a mathematical process attempts to produce a numeric number larger than the maximum size of the integer variable storing it, it is known as an integer overflow vulnerability.
How it operates: This can be a sign of a buffer overflow but is not a direct one. For instance, a programmer may determine the size of a buffer that needs to be allocated using an integer. The computed size may wrap around to a very small or even negative amount if there is an integer overflow. A traditional buffer overflow happens when the application attempts to read a lot of data into this small buffer.
Also Read About User Security Awareness: Tips For Protecting Your Authority
Format String Bug
A format string flaw is a related vulnerability that can result in memory corruption and buffer overflows, even though it is not a genuine buffer overflow. It happens when a program calls a function like printf() using user-supplied input as a format string.
The method of exploiting it involves instructing the application to grab data from the stack and print it using format specifiers such as %s (string) and %x (hexadecimal) in a format string. A malicious user can read or write data on the stack by entering a string that contains these specifiers. Because it writes the number of characters printed thus far to a memory address that is referenced by an argument on the stack, the %n specifier in particular is quite risky. This can be used by an attacker to execute code arbitrarily by overwriting a return address or other important program data.
Advantages
Since the exploit focusses on a weakness in the application’s logic, a successful buffer overflow attack can be quite powerful because it frequently goes beyond many common security measures, such firewalls or intrusion detection systems. Because it can grant the attacker total control over a compromised machine and enable them to run arbitrary code with the privileges of the compromised application, this kind of attack is also incredibly potent.
Disadvantages
The fact that buffer overflow vulnerabilities are extremely complicated and challenging to develop is one of the main drawbacks for an attacker. Because the exploit code is frequently highly particular to the hardware architecture, software version, and operating system of the target, it is not portable and is challenging to utilise on other computers. Additionally, the process may be unstable; a small error in judgement may result in the program crashing rather than executing the malicious code, warning the victim and thwarting the attack.
Applications
- Remote Code Execution (RCE): An attacker can access a server remotely and run instructions by using a buffer overflow.
- Denial of Service (DoS): A software or service can be purposefully crashed using a straightforward overflow, rendering it inaccessible to authorised users.
- Privilege Escalation: A buffer overflow in a privileged program can be used by an attacker with restricted user access to get administrator-level privileges.
Mitigation and Prevention
A number of security precautions have been put in place by contemporary operating systems and software to reduce buffer overflows:
- Boundary Checking: Before copying input data into a buffer, programmers can utilize functions that verify its size.
- Stack Canaries: Prior to the return address, a tiny, randomly generated value known as a canary is stacked. The program recognises the attack and terminates if this value is altered (for example, by an overflow).
- Address Space Layout Randomisation (ASLR): This security feature makes it far more difficult for an attacker to predict the precise location of the code they wish to run by randomly allocating the address space positions of important data regions.
- Non-Executable Stack/Data Segments: Even if an attacker is able to inject code, it cannot be executed from the stack or heap if memory regions are marked as non-executable.
Also Read About Different Types Of MAC Addresses (Media Access Control)
