Man in the Browser Attack
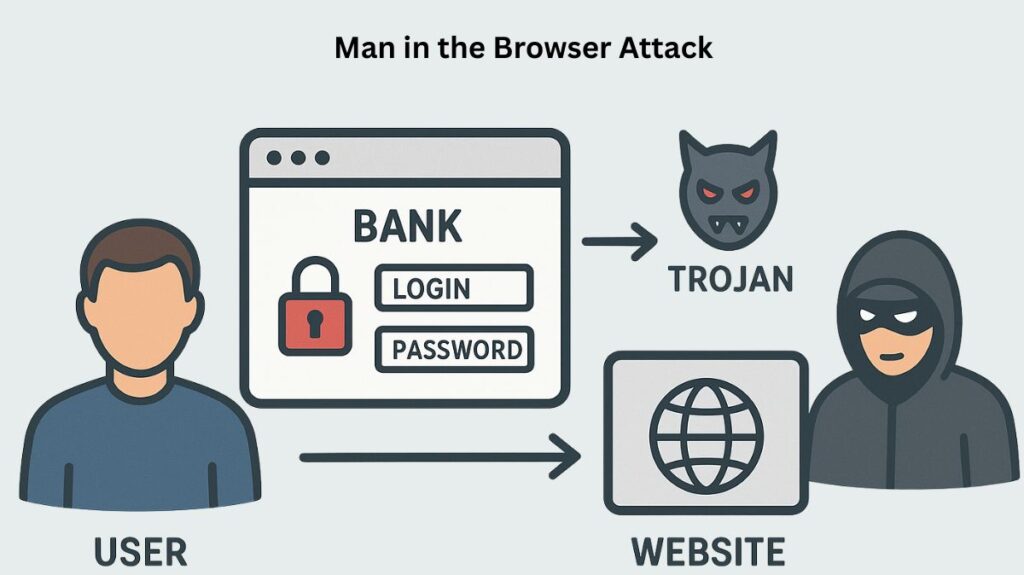
Man-in-the-Browser (MitB) attacks are complex cyberattacks in which malicious software, usually a Trojan horse, infiltrates a user’s web browser to secretly intercept, record, and alter data sent back and forth between the user and web applications.
A subtype of the Man-in-the-Middle (MitM) attacks, MitB is categorised as an Internet danger. Man in the Browser attack directly compromises the browser, running solely on the user’s device, in contrast to traditional MitM attacks that compromise network traffic.
After Augusto Paes de Barros demonstrated the threat in 2005, Philipp Gühring came up with the term “man in the browser” on January 27, 2007.
How does man in the browser attack work?
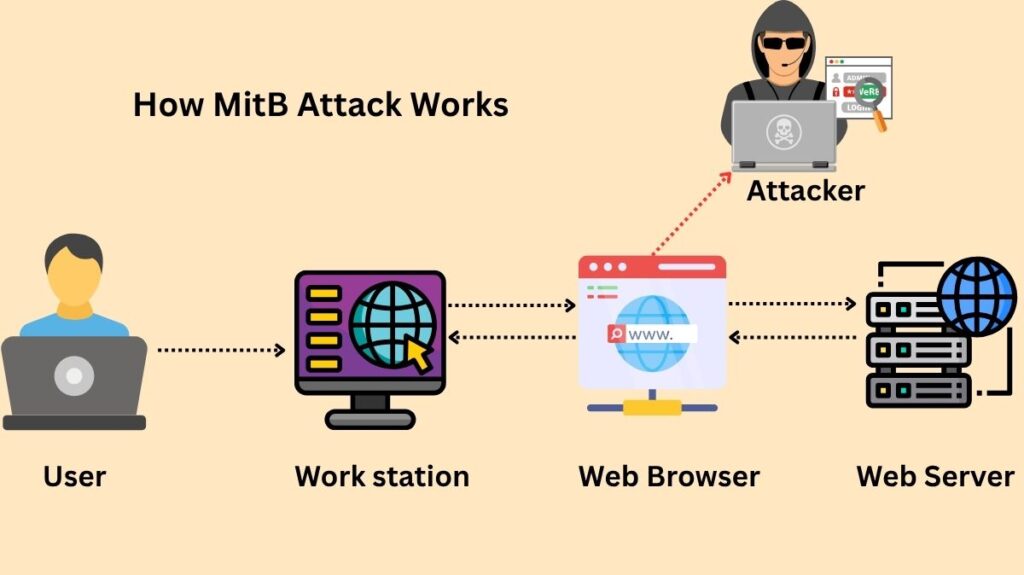
These steps are typically followed by the attack process:
Infection
Via vectors like phishing emails, fraudulent downloads, or compromised websites, the victim unintentionally installs the malicious software, which is frequently a Trojan (like Zeus or SpyEye).
Browser Injection
By hooking into the victim’s web browser (such as Chrome, Firefox, or Edge), the virus does browser injection. By exploiting browser flaws, it accomplishes this and frequently installs itself as a malicious plugin, extension, user script (such as JavaScript), or Browser Helper Object (BHO, exclusive to Internet Explorer).
Interception and Activation
The malware keeps an eye on the user’s actions. The MitB trojan is activated when the victim accesses a targeted, high-value website, such their online banking portal.
Manipulation and Data Theft
To function in real-time, the malware takes control of the browser’s processes:
- Data Stealing: It functions as a form-grabber or keylogger, obtaining session cookies, login passwords, and private data entered into online forms.
- Modifying Transactions: Prior to being sent to the server, it has the ability to intercept and covertly modify outgoing transaction information. For example, if a user tries to pay $100 to a designated recipient, the malware intercepts the request, modifies the destination account to the attacker’s account and the amount to $1,000, and then transmits the updated request to the bank server.
- Injecting Content: It can alter the HTML content that is shown to the user, for instance, by inserting phoney pop-ups or forms that ask for more private information, such as security questions or PINs.
Cover-up
Importantly, the malware alters the information that is shown to the user on the screen to correspond with the user’s initial, intended activity. Because the victim perceives a typical webpage and an apparently accurate confirmation screen (such as the initial $100 transfer), the fraud is hard to spot because they think the transaction was authentic.
Important Risks and Benefits of MitB Attacks
Man in the Browser attacks are regarded as extremely dangerous because of a number of sophisticated features:
Encryption Bypass: MitB functions on the user’s device at the application layer either before to or following data encryption by the browser’s SSL/TLS/HTTPS protocols. Standard encryption and server certificates are useless against the attack since it occurs before the browser’s security features are activated.
Bypassing Multi-Factor Authentication (MFA): MitB attacks are very successful at getting around two-factor or multi-factor authentication systems because they compromise the browser itself and allow unauthorised operations to take place after the user has successfully logged in.
Stealth: The user cannot see the manipulation because the pages appear normal.
Targeted Operations: In order to steal credentials and perpetrate fraud, MitB malware is usually made to concentrate on high-value platforms, like online banking and financial services, e-commerce websites, and enterprise dashboards. The MitB Trojans Zeus, SpyEye, OddJob, Gozi, and URLZone are a few examples.
Also Read About What Is Spear Phishing Attack? Phishing Vs Spear Phishing
MitB vs MitM Comparison
Despite having the same objective (interception and manipulation), the two attacks’ locations and methods are very different:
| Feature | Man in the Browser (MitB) | Man-in-the-Middle (MitM) |
|---|---|---|
| Location of Attack | Inside the browser software (on the user’s device/endpoint). | In the network path between the user and the server. |
| Mechanism | Malware (Trojan) infection on the endpoint device (application layer). | Network manipulation (e.g., SSL stripping, malicious Wi-Fi). |
| Bypass Encryption | Yes. It operates before SSL/TLS encryption, making HTTPS useless against it. | No, not easily. MitM attacks are typically blocked by strong encryption (HTTPS). |
Protection and Mitigation
Focussing on endpoint security and strong transaction verification is necessary for MitB protection:
For Users
- Employ Robust Antivirus/Endpoint Protection: To identify and block Trojan horses and other malware, keep security software updated and perform routine scans.
- Be Wary of Phishing: The main ways to install the MitB malware are via clicking on dubious links or downloading attachments from unidentified sources.
- Maintain Software Updates: To fix security flaws that malware could take advantage of, update your operating system and web browser on a regular basis.
For Financial Institutions
- Verification of Out-of-Band (OOB) Transactions: The best countermeasure is this one. Following a transaction submission by the user, the server confirms the information via an independent, non-browser route, like:
- Delivering the complete transaction information (amount and beneficiary) via SMS or push notification to a registered mobile device. Before the transaction is completed, the user must verify that the information reflects their original purpose.
- Behavioural Analysis: Keep an eye out for irregularities in user behaviour, such as unexpected transaction amounts, newly added beneficiaries, or quick, preprogrammed activities.
- Client-side protection and hardened browsers: Use form-field and anti-keylogging safeguards to encrypt user input before the browser can process it.
Also Read About How To Prevent Password Attacks, Advantages & Disadvantages
