In this article, we learn about Digital Certificate, Core Purpose and Function, Components of Digital Certificate, How Digital Certificate Works, Uses and Benefits.
Digital Certificate
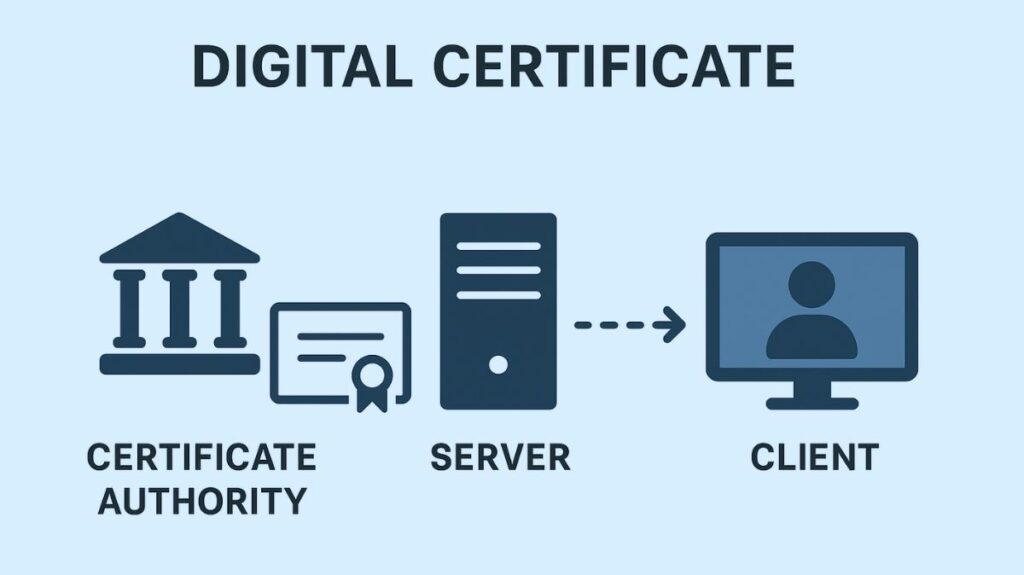
An electronic credential or file used to verify who owns a public key is called a digital certificate. It is also known as an identity certificate or public key certificate. A digital certificate functions essentially as an electronic ID card or “passport.”
In order to guarantee secure communication via networks, digital certificates are essentially a reliable form of identification. They make it possible for entities, systems, and devices to communicate electronically and share data safely and securely online.
Core Purpose and Function
The primary roles of a digital certificate are:
- Authentication: They establish the identity and confirm the legitimacy of an entity, which could be a person, a website, a server, a device, or an organization. By using authentication, businesses can make sure that only reliable devices and users are able to access their networks.
- Public Key Distribution: In order to start safe, encrypted communication, they disperse the owner’s public key.
- Cryptographic Linkage: They employ Public Key Infrastructure (PKI) to establish a cryptographic connection between the owner of a public key and the organization in possession of the matching, confidential private key.
Digital certificates provide more security than passwords alone and are regarded as a factor of authentication based on “something you have.”
You can also read What is SSH in Networking, Architecture and Uses of SSH
Components of Digital Certificate
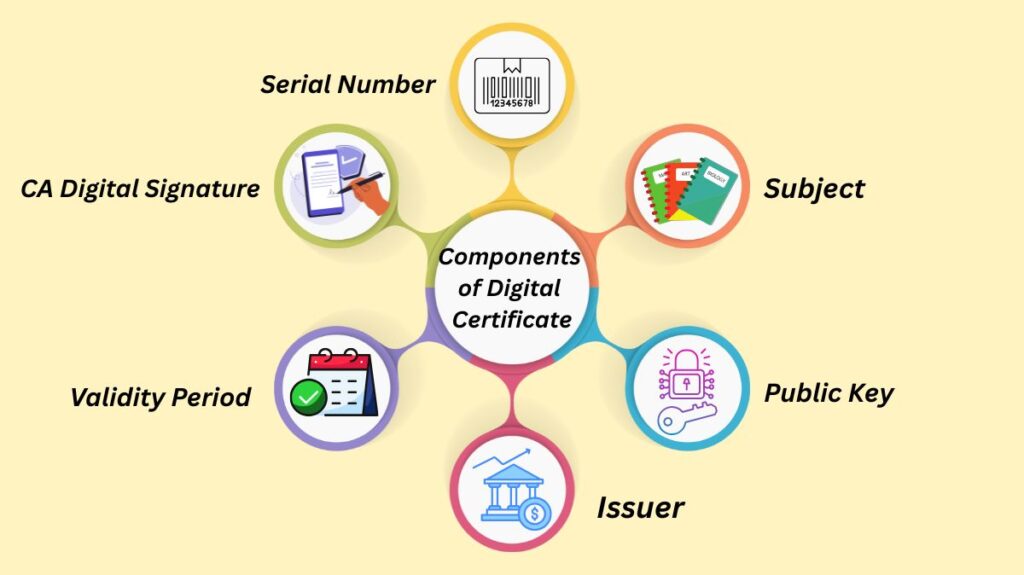
Generally speaking, digital certificates follow a specified structure, like the commonly used X.509 certificate standard. The certificate is a text document with data that has been encrypted.
Critical components found within a digital certificate include:
| Component | Purpose/Content |
|---|---|
| Subject | The name, organization, or domain of the entity being identified (the certificate holder). A Distinguished Name (DN) is often used as a unique identifier for the owner. |
| Public Key | The public portion of the public/private key pair. Others use this key to encrypt data for the subject or verify their digital signature. |
| Issuer | The name of the Certificate Authority (CA) that verified the identity and issued the certificate. |
| Validity Period | The start and expiry date/time window during which the certificate is considered trustworthy. Certificates are time-sensitive and expire. |
| CA Digital Signature | A signature created by the CA’s private key. This allows the recipient to verify the certificate’s authenticity and ensures it has not been tampered with. |
| Serial Number | A unique identifier assigned by the CA. |
When an entity creates a private/public key combination and sends a Certificate Signing Request (CSR) to a CA with the public key and identifying details, the certificate generation process normally begins.
Role of the Certificate Authority (CA) and PKI
Certificate Authorities (CAs), which are reputable companies like Let’s Encrypt or DigiCert, are in charge of issuing digital certificates.
- Trust Establishment: Before issuing certificates, the system depends on the CA being trusted to properly authenticate users. Verifying the identity of companies, people, or devices is the main responsibility of certified public accountants (CAs), who are trusted third parties.
- Signing: After confirming the entity’s identification, the CA uses its private key to sign the entity’s public key and returns the data as a certificate.
- Public Key Infrastructure (PKI): A crucial component of Public crucial Infrastructure (PKI), which is the enterprise-wide set of rules, practices, hardware, and software needed to generate, administer, and revoke these certificates utilizing public and private keys, are certificates.
- Trust Chain: A recipient needs the issuing CA’s public key to validate a certificate. This frequently entails a chain of CAs that ultimately leads to a Root Certificate, which is self-signed and identifies the CA server. Most popular web browsers come with trusted CA certificates installed by default.
If a certificate expires, it may become invalid. The CA has the authority to cancel a certificate if the key is compromised or privileges are taken away. To confirm that a certificate is still valid during authentication, clients can utilize the Online Certificate Status Protocol (OCSP) or a Certificate Revocation List (CRL).
You can also read MFA Vs 2FA Authentication, Methods, Benefits And Importance
How Digital Certificate Works (TLS/SSL Example)
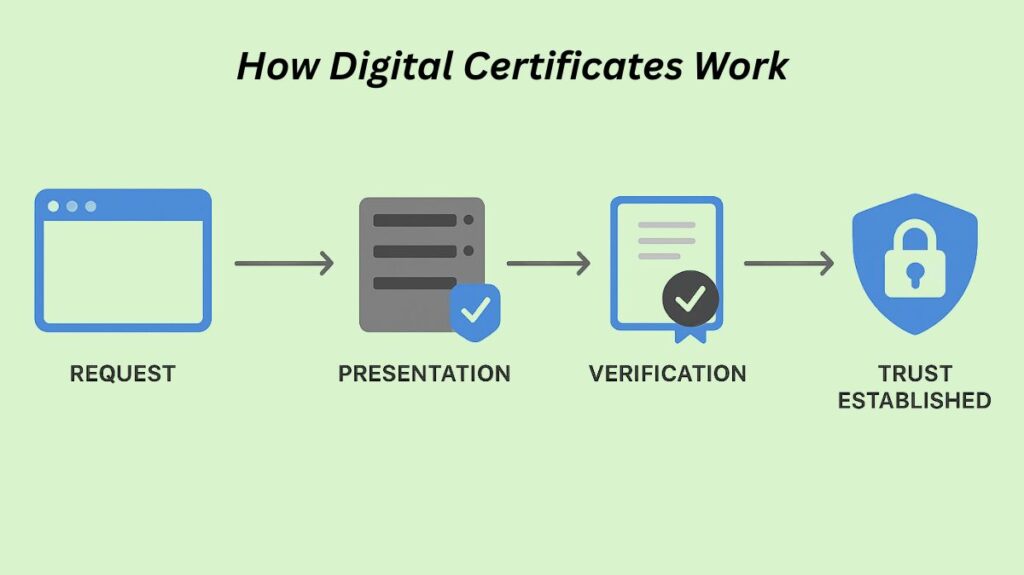
The most common example is the TLS/SSL Certificate used to secure websites, which enables the familiar HTTPS connection.
- Request: A secure connection is requested by your web browser when it connects to a website (the server).
- Presentation: Your browser receives a cryptographic certificate from the website’s server.
- Verification: The certificate is verified by your browser:
- A reputable Certificate Authority (CA), such as DigiCert or Let’s Encrypt, is the one who signed it.
- It hasn’t been revoked or expired.
- The name on the certificate corresponds to the domain name of the website.
- Trust Established: The browser has faith in the identity of the server if the verification is successful. In order to create an encrypted connection and guarantee that information (such as login credentials) is kept private, it then extracts the server’s public key from the certificate.
Uses in Network Protocols
Digital certificates are critical for securing various network communication tunnels and authentication processes:
- VPN Authentication: One of the two peer authentication techniques used to safeguard a VPN connection is digital certificates, more especially the RSA signature method (the other being Pre-Shared Key, or PSK). Digital certificates can be used for authentication in an IPsec site-to-site VPN. Devices can trust the public key for authentication after verifying the CA’s signature by exchanging digital certificates that contain each other’s public keys.
- Wireless Security (EAP-TLS): The EAP Transport Layer Security (EAP-TLS) authentication technique for wireless networks makes extensive use of certificates.
- Both the Authentication Server (AS) and each client device (supplicant) must have certificates for EAP-TLS to function.
- The supplicant and the AS mutually authenticate and exchange certificates.
- In order to safely exchange encryption key material, a Transport Layer Security (TLS) tunnel is constructed using this mutual authentication.
- Although it can be difficult to install and frequently calls for a PKI to maintain certificates for multiple clients, EAP-TLS is thought to be the most secure wireless authentication technique.
- Controller Authentication (WLC/AP): In centralized wireless systems, each Wireless LAN Controller (WLC) and Access Point (AP) has to use digital certificates to authenticate one another. Unauthorized APs are prevented by using a pre-installed X.509 certificate in each device, which is used in the background to make sure devices are authenticated before connecting to the wireless network.
- HTTPS/SSL/TLS: Protocols such as HTTP Secure (HTTPS), Transport Layer Security (TLS), and Secure Sockets Layer (SSL) require digital certificates. When a client establishes a secure connection with a web server, the server presents the client with its digital certificate, which the client verifies using PKI. The client encrypts a shared secret using the public key in the server’s certificate, which the server decrypts with its private key to enable encryption of the connection.
Benefits
Digital certificates offer several key benefits for security:
- Enhanced Security: To stop hackers from intercepting and stealing private information, they encrypt communications both internally and externally.
- Public Trust: By verifying the authenticity of communications and websites, a certificate reassures customers that they are interacting with a legitimate business that respects their privacy and security.
- Data Integrity and Non-repudiation: The sender can’t deny involvement because of data integrity and non-repudiation, which guarantee that data has not been changed during transmission and offer confirmation of origin.
- Scalability and Reliability: Certificates are dependable because of their extensive screening by publicly recognized CAs, offer consistent encryption quality, and are simple to manage and renew.
You can also read What is SSL stripping Attack, How it Works and Prevention
