What Is EdDSA
Using a version of the Schnorr signature method, EdDSA (Edwards-curve Digital Signature method) is a contemporary and safe digital signature system that is mostly based on twisted Edwards curves. A group comprising Daniel J. Bernstein, Niels Duif, Tanja Lange, Peter Schwabe, and Bo-Yin Yang created it; public-domain software served as its reference implementation.
Purpose and Characteristics: With EdDSA, security is maintained while speed is increased over current digital signature systems. It is very appropriate for a variety of applications, including secure communication, data protection, and blockchain technology, since it offers efficiency and security for digital signatures. The general consensus is that EdDSA is faster and more secure than alternative algorithms, such as Rivest-Shamir-Adleman (RSA) and ECDSA.
Underlying Principles: The Elliptic Curve Discrete Logarithm Problem (ECDLP) is a challenging problem that the EdDSA algorithm depends on. For optimal performance, the Edwards form of elliptic curves is used in its signatures. The technical description of the algorithm and its variations, Ed25519 and Ed448, can be found in RFC 8032.
Components of EdDSA: The two main steps of the EdDSA algorithm are the creation of keys and the creation/verification of signatures.
Key Generation
A public key and a private key make up an EdDSA key pair.
Private Key (privKey):
- This number was obtained by taking a random integer (seed).
- It starts with hashing the seed.
- Specific bit transformations are then applied: Setting the second-highest bit requires clearing the highest bit and the curve cofactor’s final few bits (8 for Ed25519 and 4 for X448). These changes keep the private key in the proper subgroup of elliptic curve points and maintain a consistent bit length to prevent time-based side-channel attacks.
- For Ed25519, the private key is 32 bytes.
- For Ed448, the private key is 57 bytes.
- To sign messages, the private key is kept confidential.
Public Key (pubKey):
- This point on the curve is elliptic.
- The private key is multiplied by the curve’s generating point (G) to determine it: pubKey = privKey * G.
- Compressed EC points of the y-coordinate and x-coordinate’s lowest bit (parity) encode the public key.
- For Ed25519, the public key is 32 bytes.
- For Ed448, the public key is 57 bytes.
- Sharing public keys lets others verify signatures.
Signature Generation (Signing)
A digital signature, consisting of two integers, {R, s}, is generated using the EdDSA signing method using a message (msg) and the signer’s private key (privKey) as input. The following is the procedure, with some slight simplifications:
- Calculate pubKey: pubKey = privKey * G.
- Deterministically generate a secret integer r: r = hash(hash(privKey) + msg) mod q.
- Calculate the public key point R: R = r * G.
- Calculate h: h = hash(R + pubKey + msg) mod q.
- Calculate s: s = (r + h * privKey) mod q.
- The signature is {R, s}.
Ed25519’s digital signature is 64 bytes (32 bytes for R + 32 bytes for s), while Ed448’s is 114. The receiver then receives the message and signature.
Signature Verification
The EdDSA signature verification procedure requires the signature {R, s}, message (msg), and signer’s public key (pubKey). Then it returns a boolean indicating whether the signature is valid. Simplifications are made to the procedure:
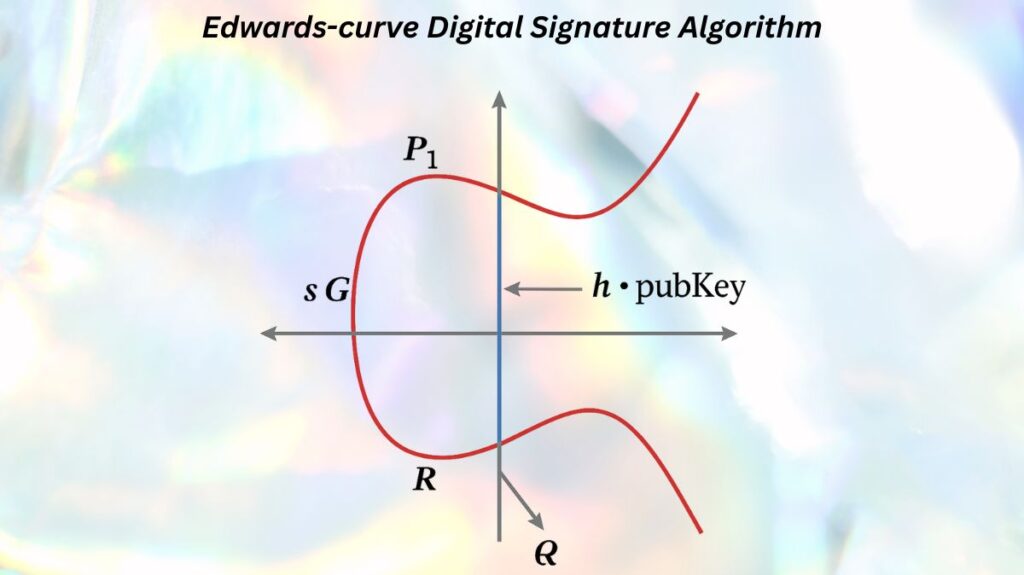
- Calculate h: h = hash(R + pubKey + msg) mod q.
- Calculate P1: P1 = s * G.
- Calculate P2: P2 = R + h * pubKey.
- The signature is valid if P1 == P2.
How Verification Works (Mathematical Proof)
During verification, P1 is calculated as s * G. From the signing process, we know s = (r + h * privKey) mod q. Substituting s into the equation for P1: P1 = s * G = (r + h * privKey) mod q * G. This expands to r * G + h * privKey * G. Since R = r * G and pubKey = privKey * G, the equation becomes R + h * pubKey. This is precisely P2. If P1 and P2 are the same elliptic curve point, it proves that the point calculated using the private key matches the point created by its corresponding public key, thereby verifying the signature.
Security Benefits and Features
Comparing EdDSA to more conventional signature algorithms like Digital Signature Algorithm or ECDSA, there are a number of security benefits:
- Quick verification and signing.
- Signatures that are brief.
- Resistance to timing attacks and other forms of attacks.
- Deterministic Generation of Nonce
- EdDSA hashes a piece of the private key and the message to produce a secret number r deterministically, in contrast to other conventional techniques that depend on a random nonce for every signature. This eliminates the need for a cryptographically secure random number generator while signing, reducing the possibility of private key leakage due to malfunctioning random number generators.
Specific Implementations
Ed25519 and Ed448 are EdDSA signature variants.
Ed25519:
- This implementation uses Curve25519 in this case Edwards25519.
- A 128-bit security level is provided.
- 32-byte secret and public keys and 64-byte signatures are employed.
- Ed25519 is popular in cryptography because of its speed, security, and small signature size for network protocols and distributed systems.
Ed448:
- Specifically, edwards448 is the Curve448-Goldilocks used in this implementation.
- A 224-bit security level is provided.
- It generates 114-byte signatures using 57-byte private keys and 57-byte public keys.
- For effective and safe cryptographic technique implementations, Curve448 uses the Edwards form of elliptic curves.
Comparison with ECDSA
A comparison of EdDSA with ECDSA reveals various points:
Simplicity: EdDSA is thought to be easier to comprehend and apply than ECDSA because it is simpler.
Security Strength: The security strength of both techniques is comparable when curves with equal key lengths are used.
Performance: The EdDSA algorithm outperforms ECDSA for well-known curves such as Edwards25519 and Edwards448; nevertheless, this greatly depends on the particular curves and implementation.
Public Key Recovery: A method to retrieve the signer’s public key from the signature and message is absent from EdDSA signatures, in contrast to ECDSA.
Recommendation: In general, EdDSA is advised for the majority of contemporary applications.
Applications and Support
The following cryptographic contexts allow EdDSA:
EJBCA Support: For establishing Certificate Authorities (CAs) and producing client certificates, EJBCA accepts EdDSA signature keys. The OCSP signer keypair and the CA signing keypair will both utilize the chosen EdDSA key type when utilizing EdDSA keys for a CA, and the matching certificates will be signed using the chosen signature method.
Hardware Security Module (HSM) Support: Support for EdDSA by HSM is rather new. Most HSMs were still using PKCS#11v2.40 as of October 2020, and PKCS#11 did not standardize EdDSA support until v3. To support EdDSA, however, PKCS#11v2 is extended by many HSMs. Using the P11-NG PKCS#11 provider, EJBCA enables EdDSA on HSMs; however, HSM implementation may vary. An HSM must handle both EdDSA and RSA keys since the encryption key in an HSM cannot be EdDSA. Currently, the majority of tested HSMs, if not all of them, support Ed25519 but not Ed448.
Client Certificates: Using EdDSA keys, you can submit normal requests for client certificates. It goes without saying that any certificate signed by an EdDSA CA will employ EdDSA signatures, whether the client keys are EdDSA, RSA, or ECDSA. A sample CSR for clients using Ed25519 can be produced with OpenSSL.
Smart Cards: Oracle included EdDSA to the Java Card Platform 3.1 specification, although there aren’t any Java Cards with this version on the market yet.
