Phishing, how phishing attacks works, key phishing techniques and attack vectors, advanced phishing techniques, how to spot a phishing attempt, signs of a phishing attack, prevention and mitigation are all covered in detail in this blog.
Phishing

Phishing is a common and advanced type of hacking and social engineering. In order to trick victims into disclosing private information or downloading malicious software, attackers pose as reputable organisations, banks, businesses, coworkers, or governmental organisations.
A variant of the word “fishing,” “phishing” describes the practice of using lures to “fish” for private information. As of 2020, phishing is the most prevalent kind of cybercrime, mostly due to the fact that it preys on human trust and vulnerabilities rather than software flaws.
Also Read About How To Prevent Password Attacks, Advantages & Disadvantages
How Phishing Attacks Work?
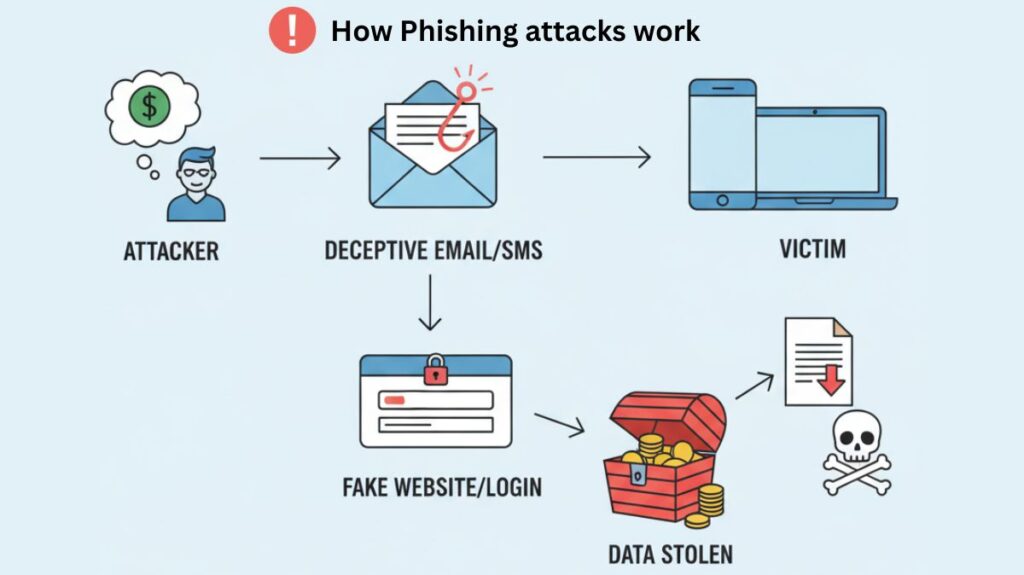
Phishing attacks start with a fake message that is altered to appear as though it came from a real source. Attackers frequently utilise psychological manipulation techniques including fear, hunger, curiosity, or instilling a sense of urgency in order to elicit a strong reaction. A message might, for example, threaten to suspend an account if nothing is done right away.
The message’s objective is to coerce the victim into doing anything that will help the attacker. Typical malevolent behaviours include:
- When a malicious link is clicked, the user is usually taken to a counterfeit website that is nearly identical to the real one. There, they are asked to submit their login credentials, bank information, or other personal information, so giving the attacker access to this information.
- Downloading a dangerous attachment: Malware, like a virus or ransomware, can infect the victim’s device and lock files or steal data.
- Using a bogus data-entry form to enter private information.
An organisation may suffer a serious data breach if just one individual falls for a phishing scam.
Key Phishing Techniques and Attack Vectors
Phishing is carried out using a variety of channels and specialized techniques:
| Attack Type | Description |
|---|---|
| Email Phishing | The most common type of phishing, sent in bulk to a wide audience, attempting to trick individuals into divulging credentials or sensitive information. |
| Spear Phishing | Highly targeted attacks directed at a specific individual or organization. These use personalized messaging and detailed personal information to increase the chance of success. |
| Whaling | A type of spear phishing that targets high-profile individuals such as CEOs, CFOs, or other senior executives. These attacks often involve requests for large money transfers or sensitive company data. |
| Vishing (Voice Phishing) | Phishing conducted over voice calls (often using VoIP technology and text-to-speech synthesizers). Attackers spoof caller ID to appear legitimate and prompt victims to enter sensitive data or speak to a live scammer. |
| Smishing (SMS Phishing) | Phishing attacks delivered via SMS text messages. Victims are typically asked to click a link or call a number. |
| QR Code Phishing (Quishing) | Exploits malicious QR codes embedded in emails, social media, or placed as hard copy stickers over legitimate codes. Scanning the code redirects the victim to a fake website designed to steal data. |
| Man-in-the-Middle (MitM) Phishing | Advanced techniques that intercept communication between the user and a legitimate service. Tools like Evilginx can steal login tokens and session cookies instantly, effectively bypassing Multi-Factor Authentication (MFA) during an active session. |
| Clone Phishing | An attacker creates a near-identical replica of a previous, legitimate email and replaces the original links or attachments with malicious ones. |
| Pharming | A more technical method where an attacker manipulates the Domain Name System (DNS) or local host files to redirect users attempting to visit a legitimate site to a malicious one without their knowledge. |
Advanced Phishing Techniques
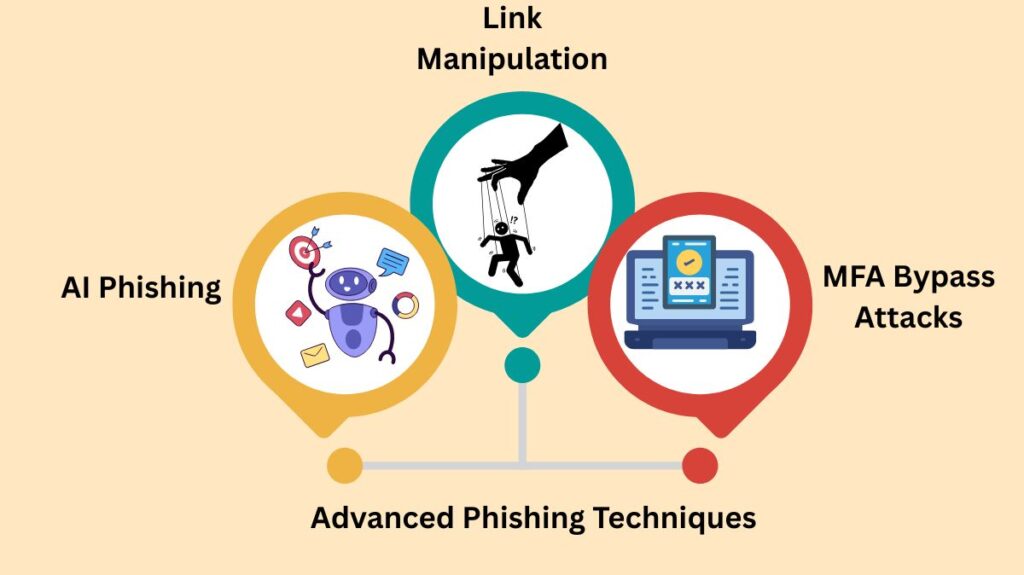
Attackers constantly evolve their techniques:
Link Manipulation: Link manipulation is when attackers use misspelt URLs or subdomains to construct phoney links (paypa1.com instead of paypal.com, for example). They might also conceal malicious URLs with visually identical addresses by using homograph attacks or Internationalised Domain Names (IDNs).
AI Phishing: Scammers may swiftly create incredibly customised and flawless messages with the use of generative AI techniques. Deepfakes of voices can also be produced by AI to support convincing vishing attacks.
MFA Bypass Attacks: Multi-Factor Authentication (MFA) is becoming a more common target of contemporary campaigns. Attackers enable victim authentication by capturing credentials and one-time passcodes using real-time relay tools.
Also Read About What Are Spoofing Attack Types? How It Works, And Advantages
How to Spot a Phishing Attempt
Even while attackers are getting increasingly complex, there are still several typical warning signs to watch out for:
- Links that don’t match: When you hover your cursor over a hyperlink, a different, dubious URL appears, even though the hyperlink’s text reads something like “Click here to login”
- Threats or urgency: The message conveys a fictitious sense of urgency by saying that you need to take immediate action in order to avoid penalties (such as “Your account will be suspended”) or receive rewards.
- Poor spelling and grammar: Although AI is reducing the frequency of these, many phishing emails still have misspellings or grammar mistakes.
- Generic greetings: In place of your name, the email provides a generic welcome such as “Dear Customer”.
- Untrustworthy sender address: The “from” address is either a public domain (such as @gmail.com) or a subtly misspelt version of the name of a reputable business (for example, amaz0n.com rather than amazon.com). To view the complete email address, always hover above the sender’s name.
Signs of a Phishing Attack
Despite the increasing sophistication of phishing attacks, consumers can identify basic warning signs:
- Sense of Threat or Urgency: Communications requesting quick action to prevent unfavourable outcomes, such account suspension, arrest, or financial loss.
- Sensitive Information demands: Uninvited demands for financial information, PINs, credit card numbers, or passwords.
- Suspicious Links: Hyperlinks that, when the mouse is hovered over the link, reveal that the text presented does not correspond to the real destination URL.
- Using general salutations such as “Dear Customer” in place of the recipient’s name is known as “generic greetings.”
- Suspicious Sender Details: Email addresses that contain slight misspellings of a valid company’s name or use a public domain (such as @gmail.com).
- Unexpected Attachments: Getting files or invoices out of the blue.
Prevention and Mitigation
A multifaceted strategy that incorporates both technological solutions and human awareness is needed to combat phishing:
- User Vigilance and Training: The most effective defence against social engineering attacks is thought to be user security awareness training. Workers should receive training on how to spot warning indicators and notify IT personnel of any questionable communications.
- Multi-Factor Authentication (MFA/2FA): Since a stolen password cannot be used to compromise a system on its own, MFA adds a crucial layer of security.
- Technical Filtering: Identifying and blocking phishing emails before they get in the inbox by using specialised spam filters and email security software with machine learning and natural language processing capabilities.
- Verification Procedures: Users should manually enter the official domain URL into their browser rather than opening embedded links. When submitting personal information, they should additionally confirm that SSL (HTTPS) is being used.
- Browser Security: online browsers that warn users about known fraudulent websites (such as Google Safe Browsing) is known as browser security.
Also Read About What is Reconnaissance Attack, How it Works, History & Types
