Let us discuss about File server, it’s history, how it works, Advantages Of A File Server, Types and File Server Management.
File server
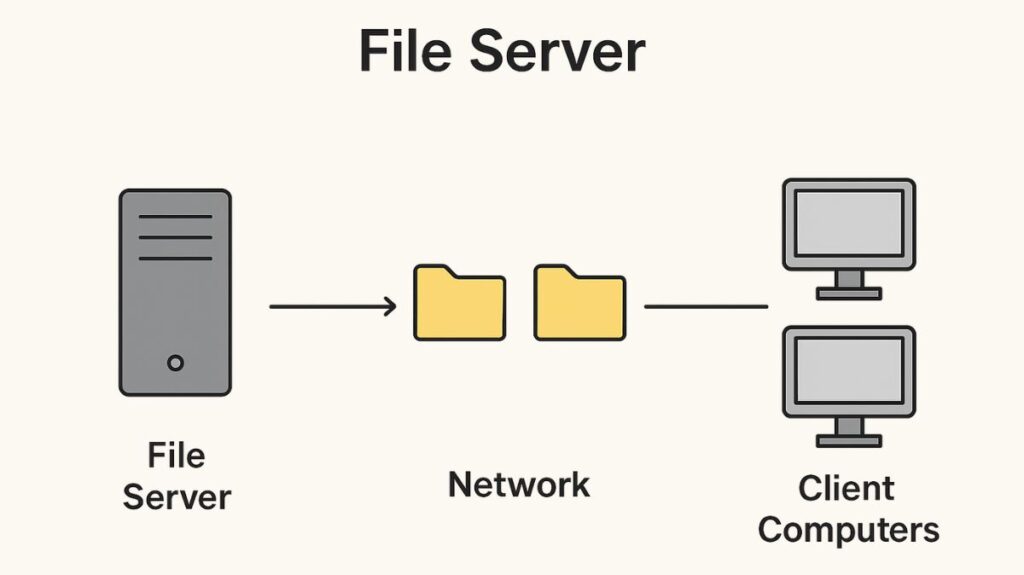
File servers are dedicated computers or networks with specialist applications and storage. It streamlines data management and sharing by storing, organizing, and making files and data accessible to networked users or client devices. A business’s common workspace or storage repository lets employees work on files and folders using networked devices.
To put it briefly, a file server is a digital library or storage space where network users can securely store, arrange, and manage their data.
Historical Context
As a result of the necessity for effective data sharing in businesses, file servers became a fundamental component of computer networking. The emergence of Local Area Networks (LANs) and mainframe computers in the 1970s and 1980s is when this necessity first appeared. Data storage prior to their introduction was dispersed among several computers, which made management and centralization difficult. With the introduction of file servers, collaborative work, access to shared resources, and smooth data exchange were made possible by a centralized point of access for several users. Additionally, by centralizing backup and recovery procedures, data security was greatly improved.
File server Functions
The following are the main functions of a file server in contemporary IT infrastructure:
Centralized Data Management: Reducing redundancy and increasing efficiency, all files are stored in one place for allowed users. Data backup and management are made simpler as a result.
Collaboration & File Sharing: File servers enable teams to collaborate across geographical boundaries by facilitating file access and sharing among numerous people via a network. Version control is frequently used to avoid conflicts.
Data Security & Compliance: User authentication, permissions, and access control lists (ACLs) protect personal data, ensure data integrity, and help enterprises comply with laws.
Scalability: File servers can expand capacity and performance to meet organizational demands.
Disaster Recovery & Backup: They enable redundancy and backup to prevent data loss from cyberattacks, hardware failures, and corruption. File servers are very useful for backup purposes.
Repository for Programs: Computer power and storage capacity are commonly outsourced from client devices to file servers, which host applications and grant access to all permitted users.
File Server Components
Several hardware and software elements are necessary for a file server to operate and perform at its best:
Storage Hardware and File System: The main part consists of solid-state discs (SSDs) or hard disc drives (HDDs). These have a file system format that maintains data integrity, tracks file locations, and organizes data. Disc arrays, which frequently have cache and sophisticated features like RAID, can be used to manage several disc drives at once.
Operating System and Server Software: Storage, access requests, and access control rules are controlled by a server-specific operating system like Windows Server, Linux, or FreeBSD and server-specific software. Any current operating system is supported if your network devices are compatible.
Network Connectivity: For remote file access, communication with client devices is made possible by a necessary network connection.
User Authentication: For file access, users must employ digital certificates, biometrics, or usernames and passwords.
Access Control: Permissions and Access Control Lists control who can read, write, edit, and delete files and folders.
File Sharing Protocols: File servers use SMB, NFS, and FTP to support file requests and transfers.
How Do File Servers Work
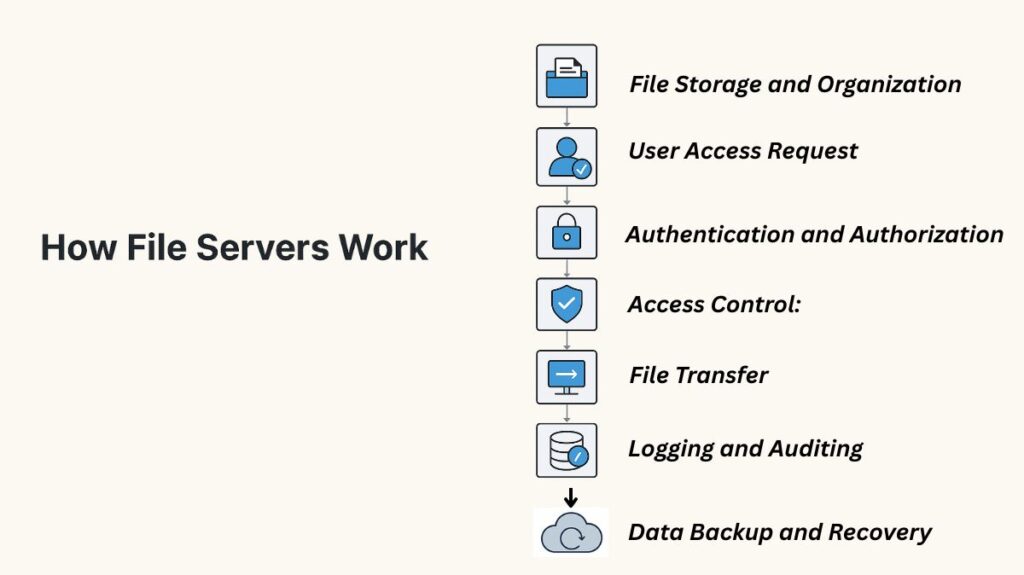
These procedures are how a file server works to centralize storage and make data exchange easier:
File Storage and Organization: On the server’s storage devices, files are arranged into directories and subdirectories along with the related information.
User Access Request: User information and the requested action (such as read, write, or delete) are included in a request sent by a client device to the file server.
Authentication and Authorization: Credentials are verified by the server. If successful, it verifies the resource’s access permissions.
Access Control: Access control policies establish whether a user is authorized. If access is authorized, it is permitted; if not, an error message is displayed.
File Transfer: The server retrieves and sends the requested file to the client over the relevant file sharing protocol if access is allowed. During transmission, data can be encrypted for security purposes.
Logging and Auditing: Access events are recorded by the server, which notes who viewed what files and when. These logs are essential for compliance, security monitoring, and troubleshooting.
Data Backup and Recovery: To prevent data loss, regular backups are planned, which allows for data recovery in the event of hardware failure or corruption.
Advantages of a File Server
Key benefits include of:
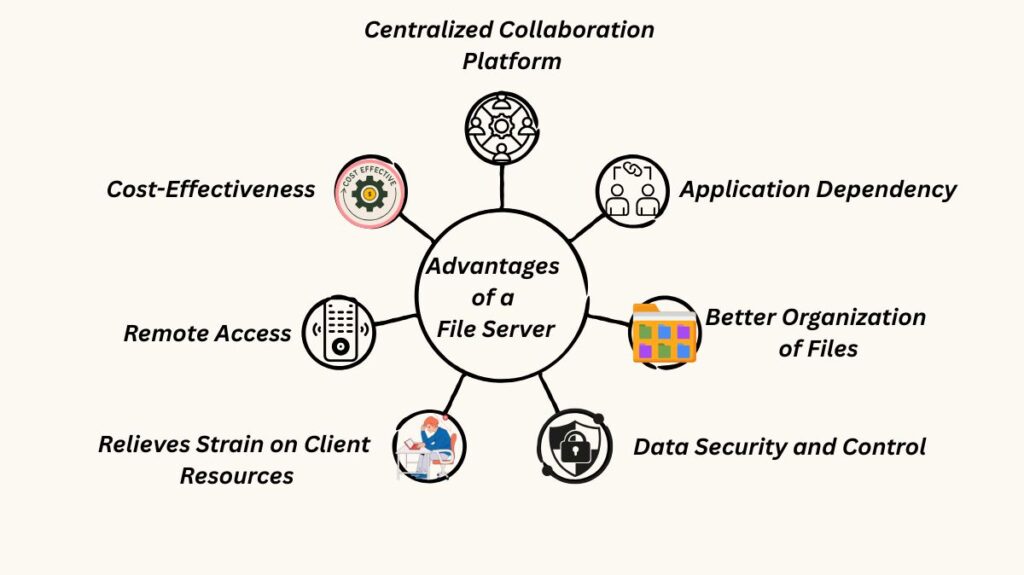
Centralized Collaboration Platform: Permits efficient teamwork and the sharing of work materials.
Application Dependency: Centralized file servers are employed by numerous line-of-business applications.
Better Organization of Files: With a clean directory and folder structure made possible by central storage, the full file inventory can be seen more clearly.
Data Security and Control: Data security and loss prevention are improved by centralized rights control, file locking, and backup features.
Relieves Strain on Client Resources: With the exception of personal documents, client devices don’t need a lot of storage space or processing power because company files are kept in one place.
Remote Access: Similar to online storage services, files are available on-the-go with the right setup.
Cost-Effectiveness: may prove to be an economical way to handle massive volumes of data.
Types of File Servers
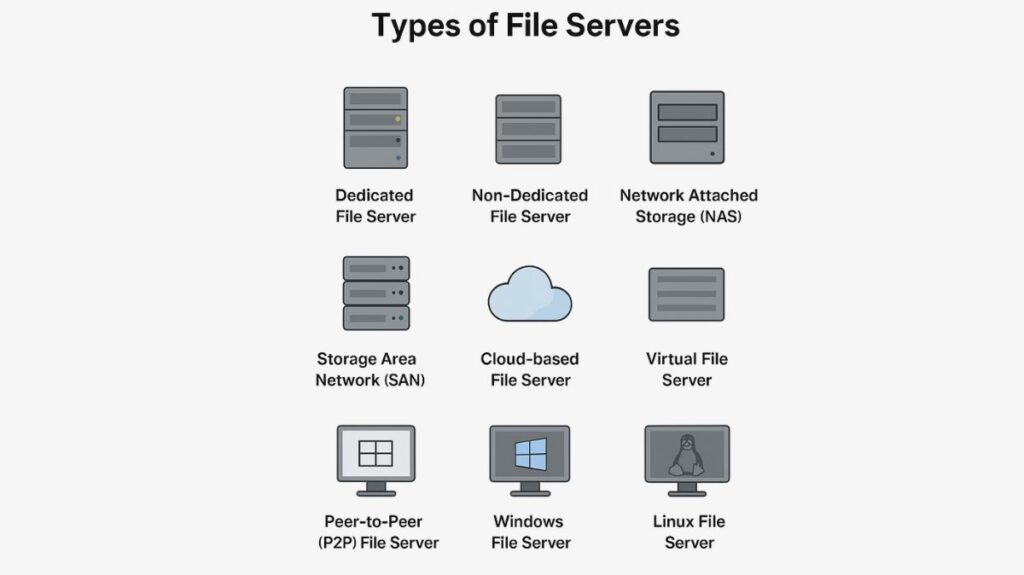
File servers are classed according to their use and functionality:
Dedicated File Server: A dedicated file server is designed to handle file requests only and is only used for file management and storage duties. The extensive storage capabilities and advanced backup and disaster recovery mechanisms guarantee optimal efficiency and performance.
Non-Dedicated File Server: Non-dedicated file servers store files in addition to supporting other server operations like database management and application execution. Their multifunctionality may affect the efficiency of file handling because of the resource allocation on the server.
Network Attached Storage (NAS): Home and small business environments frequently use specialized, standalone file storage devices that are easy to use and administer. They’re not general-purpose computers; they’re designed to serve files exclusively. SMB protocols are used by most NAS devices.
Storage Area Network (SAN): |High-speed, dedicated networks with several storage devices that give several servers access to block-level storage. because to its great performance and scalability, it is mostly used in businesses.
Cloud-based File Server: File servers with expandable storage options and remote internet access are housed on cloud infrastructure. Microsoft OneDrive, Google Drive, and Dropbox are a few examples.
Virtual File Server: A broader physical server architecture is used to deploy virtual file servers as virtual machines. Along with advantages like streamlined backup, replication, and migration procedures, they are reasonably priced.
Peer-to-Peer (P2P) File Server: Often utilized in smaller network contexts, this decentralized architecture uses individual workstations as file servers to enable file sharing among networked devices.
Windows File Servers: Utilized frequently in business settings, providing smooth interaction with Active Directory and Microsoft ecosystems. The SMB protocol is what they usually employ.
Linux File Servers: Because of their affordability and versatility, open-source alternatives like Samba and NFS are recommended. By default, they employ the NFS protocol, while Samba implements SMB to give Windows clients compatibility.
File Transfer and Access Protocols
File server and client communication is facilitated by specific network protocols:
Server Message Block (SMB): Open, read, move, create, and update files are among the functions that allow apps to access files on a distant server. It is primarily utilized in local networks with Windows and macOS devices. SMBv3 incorporates internet transfer optimizations.
Network File System (NFS): SMB’s Unix/Linux equivalent, which lets users read and store files on a distant computer just like they would on their own.
File Transfer Protocol (FTP): File transfers between any two computers using an application layer protocol that works on a client/server architecture. Although FTP can be utilized as a simple option for remote file access, there are security hazards associated with the ordinary version since it transmits data in clear text.
Secure FTP (SFTP) / Secure Copy Protocol (SCP): FTP variations that are encrypted, as well as a more recent addition for file transfers that uses SSH to encrypt data. Utilising the SSH File Transfer Protocol, SFTP is not a secure variant of FTP.
Web Distributed Authoring and Versioning (WebDAV): A protocol based on HTTP that is simpler to get past firewalls since it shares the same port (80), which is open by default for HTTP. Its lengthy and intricate dialect, however, makes it an antiquated procedure.
Trivial File Transfer Protocol (TFTP): FTP using UDP is a simplified, connectionless version that is insecure because it can only send and receive files without directory browsing or authentication. On Cisco equipment, file system management is one of its common uses.
AppleTalk Filing Protocol (AFP): Users can transfer data files and application applications on a file server with this presentation-layer protocol.
Security and Vulnerabilities
Because file servers hold important data, they are frequently the target of cyberattacks. Common weaknesses consist of:
Unauthorized Access: Weak or stolen credentials and a lack of Multi-Factor Authentication (MFA) are common causes.
Malware and Ransomware: Operational and financial losses may result from malicious software’s ability to encrypt files or steal private information.
Insider Threats: It is possible for contractors or employees with authorised access to purposefully or inadvertently abuse their powers.
Unsecured File Transfers: May cause breaches and data interception.
Denial-of-Service (DoS) Attacks: May cause the server to become overloaded with traffic, preventing authorised users from using it.
To secure file servers, essential steps include:
Strong Authentication: MFA implementation and stringent password enforcement.
Patch Management: Maintaining regular operating system and software updates to guard against known exploits.
Data Encryption: Both in transit and at rest, encrypting data.
Access Control: Using the least privilege principle and user roles to assign permissions.
Regular Backups and Disaster Recovery: Ensuring the recovery of data in the event of a system failure or attack.
Network Security Tools: Defending against outside attacks by utilizing VPNs, firewalls, and intrusion detection systems (IDS).
Continuous Monitoring and Logging: Recognising anomalous conduct and reacting to incursions instantly.
File Server Management
Smooth functioning, data security, and user convenience are guaranteed by efficient file server management:
Storage Management: It manages and distributes disc storage in a way that prevents storage bottlenecks and ensures that end users use resources properly.
User Access Control: This regulates the amount of access permission so that only designated users are allowed to access or modify certain files.
Backup & Disaster Recovery: In order to defend against data loss due to cyberattacks, disc failures, or human mistake, it effectively saves daily backups and recovery procedures.
Performance Optimization: In addition to optimizing load balancing and lowering latency for ideal file access, this regularly monitors system health.
Remote Accessibility: Providing cloud connectivity, remote desktop technology, or VPNs for safe remote access.
Remote Access and Cloud Mobility
Access to file servers via the internet can improve teamwork and productivity, but it needs to be done securely:
VPN Connection: Access to the internet is safe and encrypted when a virtual private network is deployed. But for business customers, VPNs can be a hassle because they need to understand network topology and employ specific client agents.
Firewall and Port Forwarding: Setting up firewall rules to limit access and open just the ports that are required.
Remote Desktop or SSH Access: To operate servers securely, use SSH for Linux or Remote Desktop Protocol for Windows.
Secure File Transfer Protocols: Using SFTP or FTPS in place of conventional FTP to improve security.
Multi-Factor Authentication (MFA): An additional layer of authentication is added.
Monitoring and Logging: Checking for questionable activities by routinely monitoring remote login attempts.
Cloud-Based File Sharing Services: Dropbox, Google Drive, and Microsoft OneDrive integration is crucial for safe external access because these services make mobile and web browser file access easier without a VPN.
With its high accessibility, security, and flexibility, cloud file servers reduce on-premise infrastructure and boost scalability. Automated backups, remote access, scalability, cost effectiveness, and provider-managed security and compliance will delight agile, low-maintenance companies
File Server vs. Web Server

Both deal with the distribution and storage of data, but their goals and procedures are different:
File Server: Uses SMB, NFS, and FTP protocols to store and manage shared files, usually for users on internal networks.
Web Server: Mainly uses HTTP and HTTPS protocols to host webpages and web applications for private or public web access. File servers are not the same as web servers, which frequently offer both static files and dynamic online content.
