Clone phishing definition
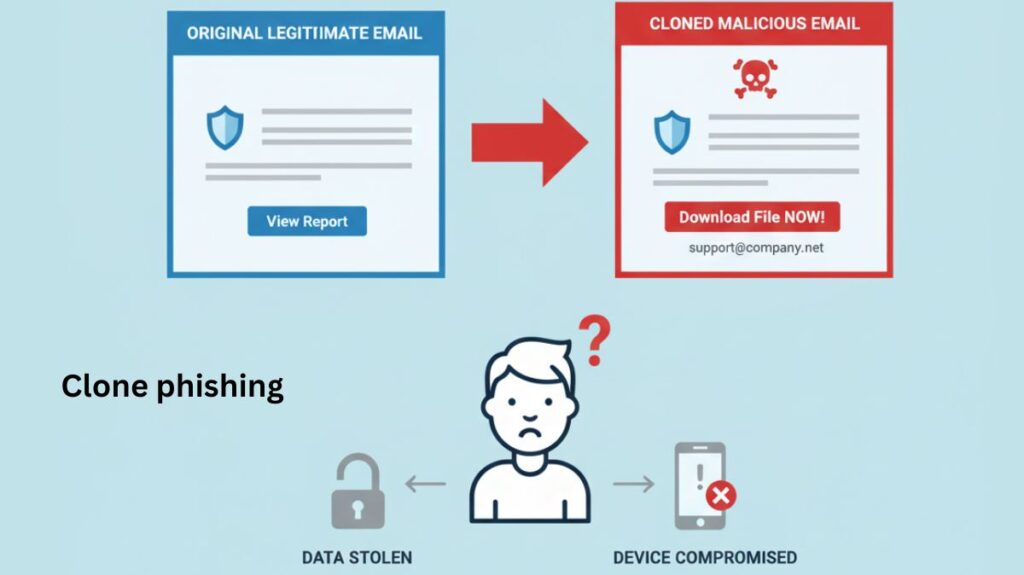
The term “clone phishing” refers to a specific type of phishing attempt in which malevolent links or attachments are substituted for the original ones in an almost identical copy of an authentic email that the recipient has already received. Using the recipient’s trust and familiarity with the format, content, and sender of the original email, this technique tricks them into downloading malware or clicking on a risky link that takes them to a phoney website that compromises devices or steals personal information.
How Clone Phishing Works?
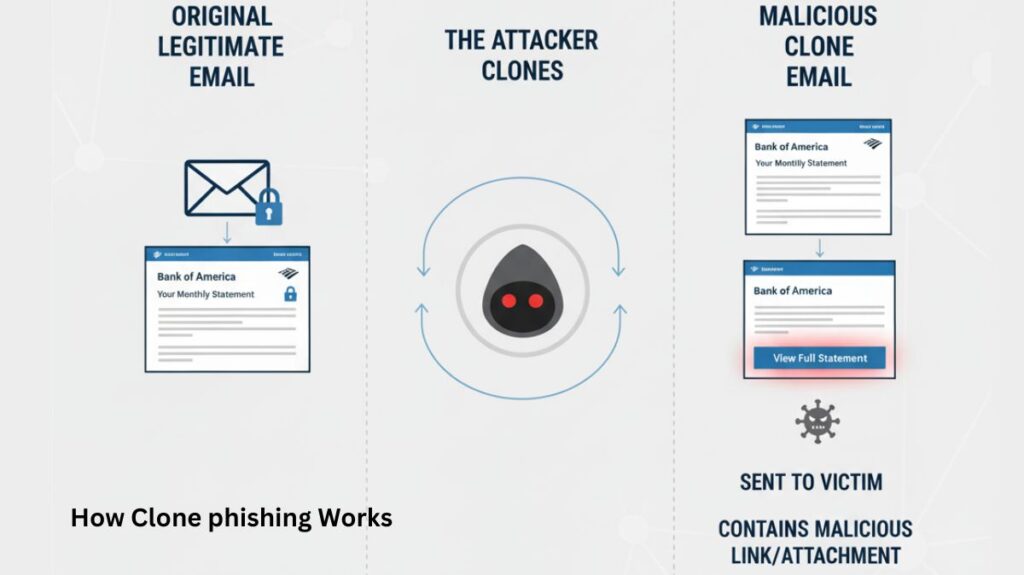
Intercepting a valid transmission, duplicating its contents, and then substituting a malicious payload for the secure information is what it involves.
Also Read About Types Of Phishing Attacks & How To Prevent Phishing Attacks
- “Intercept and replicate” is a reconnaissance approach in which the attackers first receive or intercept a legitimate email that has already been sent to the target, such as an invoice from the firm, software update, newsletter, or HR notice. After that, the attacker creates a perfect duplicate of this genuine email by stealing its text, formatting, and headers to make it seem genuine. In addition to mimicking the logos, colour schemes, and design, this replication entails having the subject line and wording identical or strikingly similar.
- Malicious Substitution: An essential step is altering specific elements of the duplicated email. In order to steal credentials, the attacker replaces links that lead to reliable websites with those that lead to hostile websites (such phoney, lookalike login pages). The same is true for files that replace the original, safe attachments with malicious software, such as viruses, ransomware, or keyloggers.
- Justification for Resend To make the resend appear legit, attackers often include a simple, plausible justification for the message. They may do this by offering a “urgent update,” “resending this,” or apologising for “having a technical issue and had to resend this message.”
- Delivery: The spoof email is delivered to the recipient, typically with the sender’s address distorted to appear as though it was sent by the real sender. Knowing the message already makes the user less suspicious and increases the likelihood that they will open the attachment or click on the malicious link. It is sometimes possible to send clone phishing from a legitimate email account without the need for spoofing.
Why Clone Phishing is Dangerous and Effective
Because it capitalizes on user expectations and established trust, clone phishing is significantly more trustworthy than traditional, generic phishing emails.
- Reduces Suspicion by Using Familiarity: The message’s content already meets the recipient’s expectations (for example, a familiar invoice or shipment notice). The attacker finds it easier to trick the recipient because people are accustomed to the message.
- Often, attackers plan the copied message to include a “correction” or “resend,” which increases the communication’s perceived credibility.
- Bypassing Filters: Clone phishing often works because recipients perceive a response to a legitimate email rather than a new message. It is more likely to be accepted by email filters since a malicious reply could be sent by a legitimate person or through a legitimate channel.
- Spreads Quickly: If a victim falls for the fraud, the attacker can get their contacts and forward the spoof email, which will continue the assault’s spread.
Also Read About Advanced Phishing Techniques, Prevention And Mitigation
Common Targets
Numerous individuals and companies are the targets of clone phishing, which usually involves private or sensitive data:
- Finance Teams: Cybercriminals may change invoices or payment requests to contain fraudulently added bank information.
- HR/Payroll: Phishing payroll attachments or benefits forms are how malware is disseminated.
- IT/Support: Phishing software update alerts may transfer malware payloads.
- Customer Communications Phishing websites can be accessible using phoney “order receipt” or “delivery” emails.
Example of a Clone Phishing Attack
Imagine receiving your monthly statement by email from “Secure Bank,” your bank.
It looks exactly the same when you receive a second email from the same source a week later. According to the email:
“Subject: Re: Your Secure Bank Statement – October
Hello, we are resending our previous email because of a minor issue with the link. We have updated the statement and made the necessary corrections for your assessment. To see your whole statement, please click the following link.
[Click here for your statement]”
Your bank’s secure website would have been the destination of the “Click here” link in the original email. In order to obtain your login credentials, it navigates to a phoney webpage in the clone that imitates your bank’s login page.
How to prevent clone phishing
To prevent clone phishing, users must exercise extreme caution:
Indicators/Red Flags
- A surprise Follow-up: Receiving “correction” or “resend” emails requesting that you click on a link that you have already seen.
- Sender Details: Check for little misspellings or variations in the sender’s name or email address.
- Link Inconsistencies: Hover your cursor over links without clicking to see a preview of the page. There is a risk if the URL seems suspicious or if the apparent text is different from the actual domain.
- Urgency: When pressure or urgent language is added to a message that would otherwise be considered regular, usually with the fear of account termination or legal issues to spur quick action.
- Attachments: Attachments with strange file types (like.exe,.scr, or.zip) or that urge you to permit macros should be avoided.
How to Protect Yourself from Clone Phishing
- Observe “Resent” emails: If you receive an email that purports to be a resend of an old one, proceed with extreme caution.
- Refrain from Using Provided Links: Steer clear of clicking links or opening attachments in questionable emails. If you believe the message to be genuine, open a new browser window and navigate directly to the company’s official website to confirm the facts.
- Hover Over Links: Hold your mouse pointer over any link in the email to see its complete URL before clicking. Any URL that does not match the company’s actual domain is a scam. Observe small misspellings, such securebanc.com instead of securebank.com.
- Check with the Sender: If you are unsure about the authenticity of an email, either contact the sender using a different email address or by contacting the official customer support number.
- Activate Multi-Factor Authentication (MFA): By adding a crucial second tier of security, MFA makes it much harder for an attacker to access your account, even if they are able to get your login information.
- Educate and Train: Regular cybersecurity awareness training is essential for both individuals and employees to recognise the subtle warning signals of sophisticated attacks like clone phishing.
Also Read About Email Phishing Attacks, Why Do Hackers Use Phishing Emails?
