Fundamental ideas in computer networking, data encapsulation and de-encapsulation are necessary for the safe and effective movement of data between networks. When data moves through various network model layers, such as the OSI or TCP/IP model, these procedures entail adding and deleting protocol-specific metadata.
Data Encapsulation
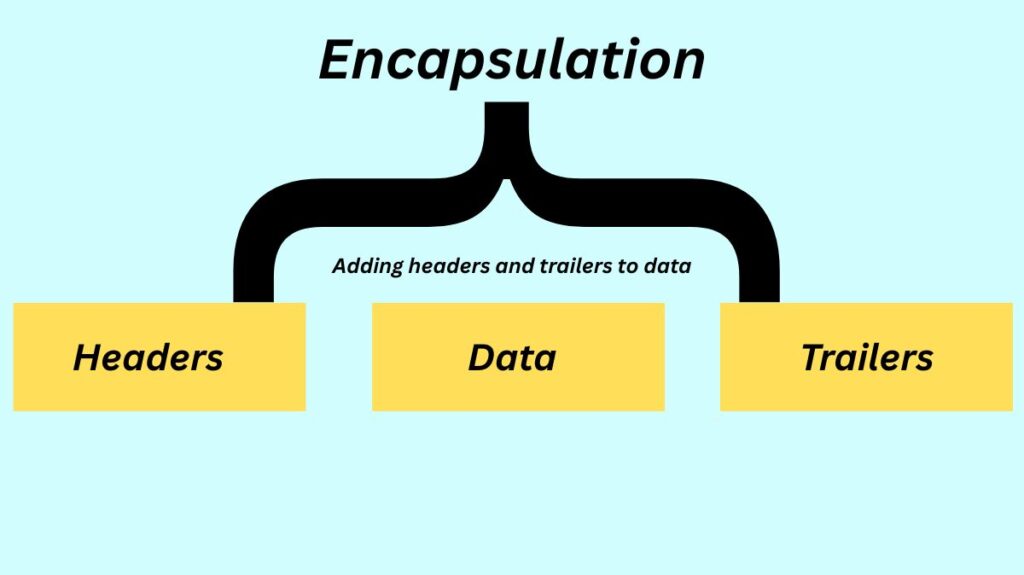
Adding headers and trailers to data when it moves from a higher layer to a lower layer of a network model usually on the sender’s side is known as data encapsulation. Consider it similar to packaging a gift in several boxes before delivery, with each box standing in for a layer that adds a unique “wrapper” of information. Encapsulation serves to ensure that the data is correctly transferred and processed by the receiving end by adding control information like addressing and error checking. A Protocol Data Unit (PDU) is the name of the data structure at any particular layer.
You can also read Network Topology Types: Bus, Star, Mesh And More Topologies
How does data encapsulation work?
The following steps are usually included in the process:
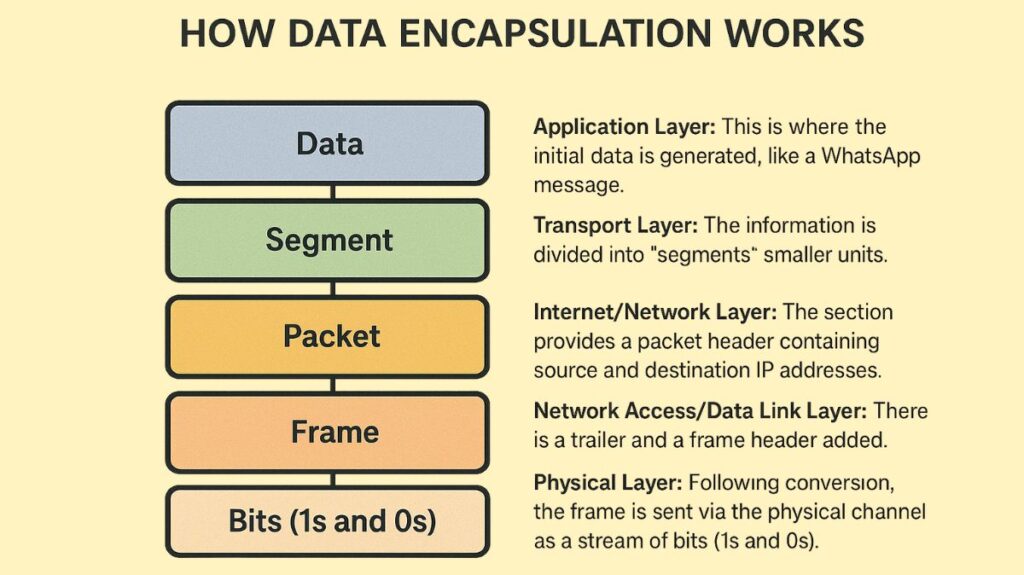
Application Layer: This is where the initial data is generated, like a WhatsApp message. Layers 5-7 (Application, Presentation, Session) of the OSI model often don’t contribute further information to the user’s data.
Transport Layer: The information is divided into “segments” smaller units. Destination port numbers and sequence numbers are included in the segment header. The enclosed data is referred to as a Segment if the transmission is using TCP and a Datagram if it is using UDP.
Internet/Network Layer: The section provides a packet header containing source and destination IP addresses. This layer’s enclosed data is now referred to as a packet or datagram.
Network Access/Data Link Layer: There is a trailer and a frame header added. Source and destination MAC addresses are included in the header, and an error-checking field is frequently seen in the trailer. A Frame is created from the contained data. Neither a header nor a trailer are used by any other layer.
Physical Layer: Following conversion, the frame is sent via the physical channel as a stream of bits (1s and 0s).
The data acquires a layered structure at the conclusion of the encapsulation process: Frame Header [MAC] + Packet Header [IP] + Segment Header [TCP/UDP] + Data + Trailer.
De-encapsulation
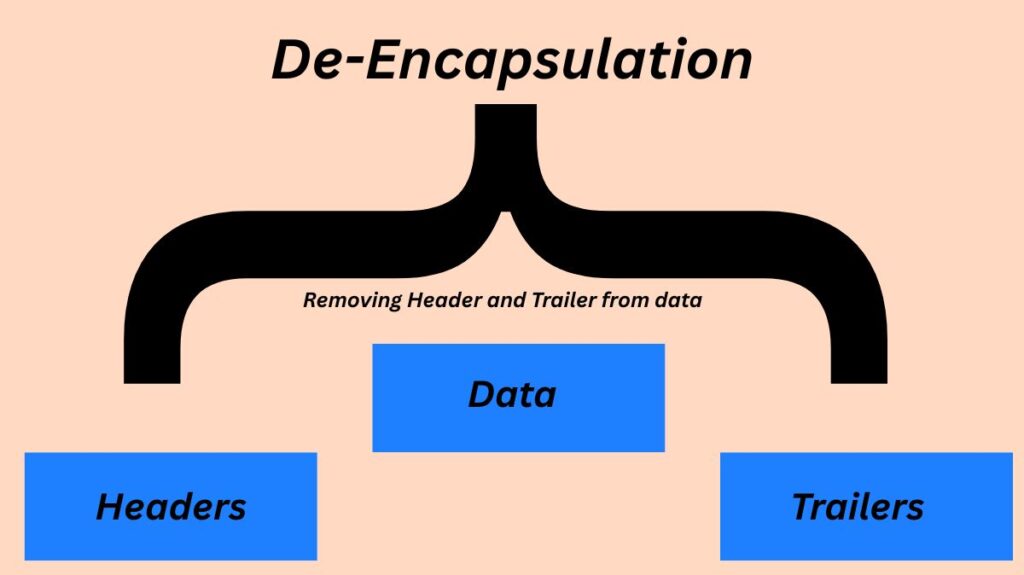
The opposite of encapsulation, known as de-encapsulation, takes place at the receiving device. Imagine those boxes being unpacked in reverse order by the recipient. Until the original data is extracted and sent to the intended application, each tier of the protocol stack removes its own header and trailer as it goes up the stack, exposing the PDU at the next higher layer.
You can also read How Data Flows Through The OSI Model And It’s Importance
How does Data De-encapsulation work?
The following steps are usually included in the process:
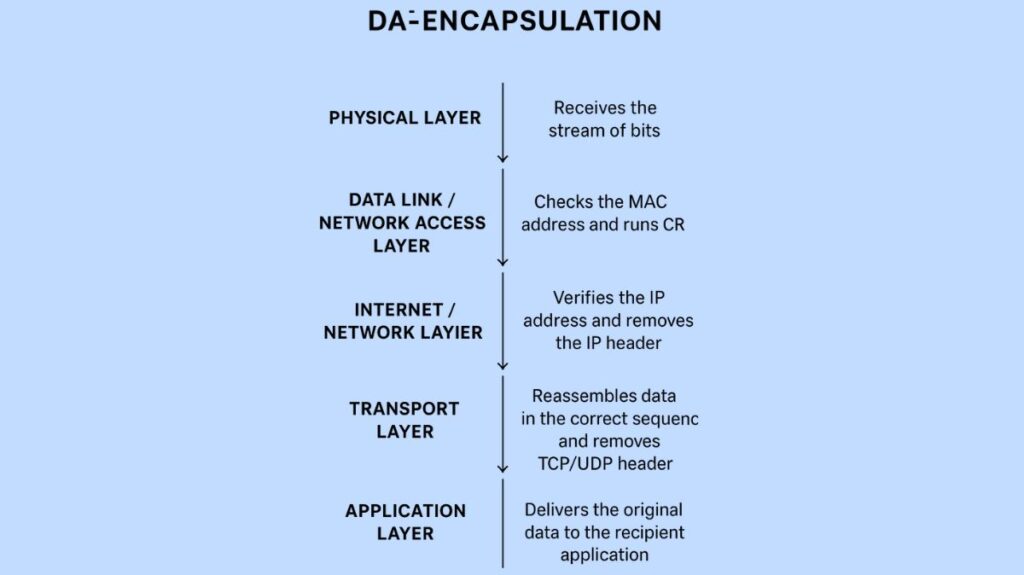
Physical Layer: The stream of bits is received by the destination device, which then transforms it back into a frame.
Network Access/Data Link Layer: After receiving the frames, the device confirms the MAC destination address and runs a Cyclic Redundancy Check (CRC) using the trailer to look for mistakes. The frame header and trailer are eliminated, and the data now a packet is forwarded up if the MAC address matches and there are no mistakes.
Internet/Network Layer: After receiving the packet, the network layer verifies the IP address and deletes the IP header if it matches. After that, the data now in the form of a segment or datagram is sent to the Transport Layer.
Transport Layer: After receiving the segments or datagrams, the transport layer reassembles the data stream in the proper sequence after removing the TCP/UDP header. It could also notify the transmitting station that it has been received.
Application Layer: The de-encapsulated data is ultimately transmitted to the recipient’s application, which reads and displays the original message after it has passed through the Transport, Session, and Presentation levels (in the OSI model).
Importance
For multiple reasons, encapsulation and de-encapsulation are essential:
Reliability and Security: They protect data during transport and prevent unwanted access.
Hiding Complex Details: They lessen the possibility of gearbox faults by concealing the intricate mechanics of the gearbox system.
Efficiency: By securely delivering symmetric keys which are faster for encrypting large amounts of data using asymmetric encryption, these procedures particularly the Key Encapsulation Mechanism (KEM) improve efficiency in cryptographic situations by guaranteeing that only the intended recipient may decrypt the key.
Simplification of Key Management: Forward secrecy is achieved by establishing symmetric session keys at the start of every secure communication session.
Flexibility: They enable safe key exchange over unprotected channels, which is necessary for TLS connections.
Although they serve different purposes, these two techniques are essential for secure and efficient networking and cryptography communication.
Key Differences between Encapsulation and De-encapsulation
| Basis of Differences | Encapsulation | De-encapsulation |
| OSI Model Movement | Data traverses from the upper layer to the lower layer. | Data traverses from the lower layer to the upper layer. |
| Effect on Headers & Trailers | It adds headers and trailers to the data. | It removes headers and trailers from the data. |
| Device Specification | This process happens at the source computer. | This process happens at the destination computer. |
| Sequence of Process | This is the initial step of encoding. | It follows encapsulation for decoding. |
| Functionality | It secures and tags the original data to make transmission easier. | It extracts the original existing data or message. |
You can also read Types of Hubs, Features, Advantages And Disadvantages Of Hub
