In this blog post, we discussed about computer networks router: What a router is, how it works, its architecture, its advantages, disadvantages of Routers, routing concepts, Physical Aspects and Management, applications, routing protocols, and how a router varies from other network devices are all covered in the following.
In order to link computer networks and manage data flow, network routers are essential networking equipment. They enable numerous devices to share a single Internet connection and are in charge of forwarding data packets between various networks, including Wide Area Networks (WANs) and Local Area Networks (LANs).
What is a Router?
Data packets are forwarded between computer networks by routers, which are networking devices. It links one or more subnetworks or packet-switched networks together. Multiple devices can share an Internet connection to routers, which control traffic between various networks by forwarding data packets to their intended IP addresses. They are frequently referred to as “Layer 3 devices” since they operate at Layer 3 (the Network Layer) of the OSI Model.
How do routers work
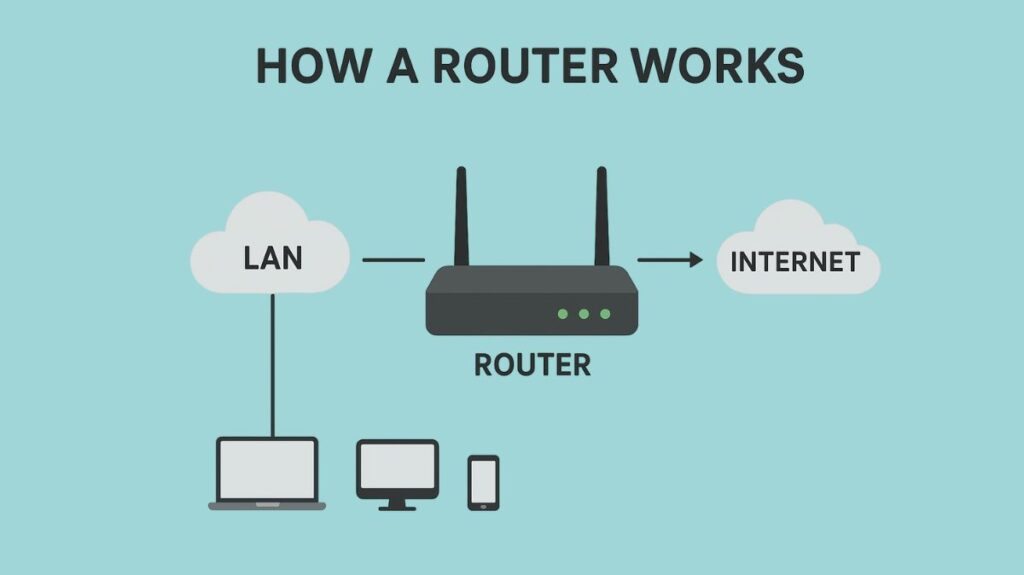
Several crucial procedures are involved in a router’s operation:
Packet Examination and Forwarding
When a router receives a data packet, it looks at the packet’s header to determine the destination IP address. After then, it looks for information about network paths in its routing table, a database. The router sends the packet out through the proper output interface or port after determining the “best” or most efficient way to forward it to its destination based on this table. The packet keeps going through this procedure from router to router until it gets to its destination.
Routing Database (Routing Table)
This is essential for figuring out a packet’s future path since it describes how to convey data to a particular network point.
- Static Routing Tables are appropriate for smaller networks and are manually designed.
- Dynamic Routing Tables are utilized in larger networks and are automatically updated in response to network activity. In order to create or update these dynamic tables, routers exchange information with one another.
- Routing tables usually contain interface information, other routers’ IP addresses, and node IP addresses and subnet masks.
Also Read About What Are Network Components? And Types Of Network Devices
Modem Usage
Routers use a modem (such as a cable, fibre, or DSL modem) to allow devices to communicate with the Internet. In order to connect numerous devices at once, most routers feature multiple ports.
Operational Planes
Three planes can be used to classify all of a networking device’s functions:
Data Plane (Forwarding Plane)
In charge of making actual forwarding decisions and carrying out tasks like Access Control Lists (ACLs) and Network Address Translation (NAT).
Control Plane
Uses routing protocols to understand network layer paths.
Management Plane
Manages tasks like logging in to the device (for example, through SSH or Telnet).
Architecture of Router
The following elements make up a generic router:
- Input Port: Closes the physical connection, communicates with the link-layer (decapsulation, for example), and consults the forwarding table to find the correct output port.
- Switching Fabric: The router’s “heart” that joins input and output ports. It functions as a network within itself. Switching over memory, a bus, or an interconnection network are examples of implementations.
- Output Port: Sends packets from the router to an outgoing link after checking queuing buffers and carrying out link layer operations.
- Routing Processor: Uses different routing methods (e.g., link-state, distance-vector) to construct the forwarding table, handles network administration, and implements routing protocols.
Routing Concepts
Routing Protocol vs. Routed Protocol
- The rules, messages, and algorithms that routers use to share routing information, learn about networks, and identify the optimal paths are defined by a routing protocol (e.g., RIP, EIGRP, OSPF).
- Routable protocols, such as IPv4 and IPv6, specify the logical addressing and packet structure that routers forward.
Router-on-a-Stick (ROAS)
This Cisco router feature routes packets between various VLANs using VLAN trunking on a single Ethernet interface.
Physical Aspects and Management
Hardware: CPU, RAM, BIOS, operating system (OS), motherboard, physical input/output (I/O) ports (also called interfaces), power supply, and chassis are the components that make up a router. Additionally, they have NVRAM (Nonvolatile RAM) to save the startup configuration and ROM (Read-Only Memory) for the bootstrap program and basic OS software.
Connectivity: Ethernet LAN, Ethernet WAN, and serial WAN are just a few of the physical network links that routers can connect to. Usually, they have two or more physical I/O ports.
Command-Line Interface (CLI): Cisco router CLIs function similarly to Cisco switch CLIs, enabling management and configuration. They need very little setup in order to start forwarding IP packets. Verification of operations is done with standard commands like display.
Functions of a Router
In a network infrastructure, routers carry out a number of vital tasks:
Forwarding: After receiving packets from its input ports, the router looks up the suitable output port to dump the packets onto using the routing table, checks the packets’ header, and then forwards them to the appropriate output port.
Routing: Routing is the process by which the router determines the optimal path for a packet to take in order to reach its destination. It keeps track of a routing table that is created solely by the router using various methods.
Network Address Translation (NAT): To convert between several IP address ranges, routers employ NAT. This makes it possible for devices connected to a private network to use a single public IP address to access the internet.
Security: To guard against viruses, illegal access, and other dangers, routers can be set up with firewalls and other security features.
Quality of Service (QoS): Depending on the kind of data being sent, routers can rank network traffic. By doing this, it is made sure that vital services and apps have enough bandwidth and are not impacted by lower-priority traffic.
Virtual Private Network (VPN) connectivity: Routers can be set up to enable secure Virtual Private Network(VPN) connections for distant users.
Bandwidth management: By regulating the quantity of data that is permitted to pass across the network, routers can be used to control network bandwidth. By doing this, network congestion may be avoided and sufficient bandwidth for important apps and services can be guaranteed.
Monitoring and diagnostics: In the case of a network breakdown or other problem, routers can be set up to keep an eye on network traffic and offer diagnostic data. This makes it possible for network managers to find and fix issues fast.
Divide Broadcast and Collision Domains: Routers divide broadcast and collision domains by refusing to forward broadcast or multicast packets to other networks.
Routers create a “internetwork” by facilitating communication between various networks. To ascertain the most efficient route for data packets from a source to a destination, they employ routing tables.
Types of Router
Depending on their function and deployment, routers can take many different forms:
Broadband routers
Among the most crucial types of routers are these. It can be used for a variety of tasks. It can be used to connect to the internet or to connect computers.
Wireless Routers (Wi-Fi Routers)
These devices combine the capabilities of a switch, router, and wireless access point to establish a wireless signal in a house or workplace. Wireless Local Area Networks (WLANs) are created by them.
Also Read About Advantages And Disadvantages Of TCP IP Model & Its Functions
Wired Routers
Using Ethernet wires, a wired router is a physical device that links different devices in your network. For the transmission of data, these cables guarantee a steady and dependable connection. By receiving data from your modem and transmitting it to all connected devices on your local network, wired routers also serve as an internet gateway. Because of this feature, they are perfect for settings like small workplaces and schools where several devices need internet connection.
Edge Routers (Gateway Routers)
Edge routers, also known as gateway routers, are found at a network’s edges. They link to an Internet service provider (ISP) and distribute packets among several networks. For connectivity, they make use of the Border Gateway Protocol (BGP).
Core routers
Usually utilized by ISPs for large data transfers on the Internet backbone, these devices distribute packets inside the same network. They serve as a network’s backbone and usually don’t interact with other networks.
Virtual routers
A virtual router is a piece of software that does the same job as a physical router. In the event that one fails, it may create primary and backup virtual routers using the Virtual Router Redundancy Protocol (VRRP).
Portable routers
Made to be easily portable, these devices enable private Wi-Fi.
SOHO (Small Office/Home Office) routers
Located in employee residences or small locations with few personnel, these devices frequently combine wireless, switching, and routing functions into one unit and rely mostly on Internet access for wide area network (WAN) connectivity.
Customer Edge (CE) Routers
These are routers that connect to a service provider’s network, usually at a customer’s location, particularly with MPLS services.
Brouters
They are specialized routers that can also perform bridge-like functions. Brouters provide data flow between networks, much like a bridge. They also route data among network devices, just like a router does.
Security Challenges in Routers
Numerous security issues that routers encounter can result in unwanted access:
- Vulnerability Exploits: Hackers can take advantage of vulnerabilities in router firmware, which is software that is loaded automatically. To address these vulnerabilities, firmware updates must be performed on a regular basis. Unpatched routers may join a botnet or be used for traffic monitoring.
- Distributed Denial-of-Service (DDoS) attacks are a threat to routers that can overwhelm them, crash them, and create network outages.
- Administration Credentials: By default, routers provide admin credentials (such as “admin” for username and password), which an attacker might simply use to take control the router remotely if they don’t alter them.
- Open Ports: A router’s open ports can be used to access the network and devices connected to it.
- Virus and Malware Infections: Viruses and malware can infiltrate routers, jeopardising linked devices.
- Router Hijacking: Hackers can take control of routers to steal confidential data or reroute users to phoney websites.
Advantages of Routers
There are various advantages to using routers:
- Easier Connection: Increases productivity by enabling several devices to share a single network connection.
- Security: Serves as a bridge between networks, adding an extra degree of protection by shielding PCs from direct Internet access.
- NAT Use: Enhances Internet connectivity and information flow by mapping several private IP addresses to a single public IP address.
- Facilitates Dynamic Routing: Selects the best data path, establishing broadcast and collision domains, and lowering network traffic.
- Packet filtering: This method allows or prohibits network traffic according to a set of rules.
- Backup Plan: In the event that external network components fail, traffic routing problems are avoided by using backup parts.
Also Read About What A Network Is And What Are Benefits Of Networking
Disadvantages of Routers
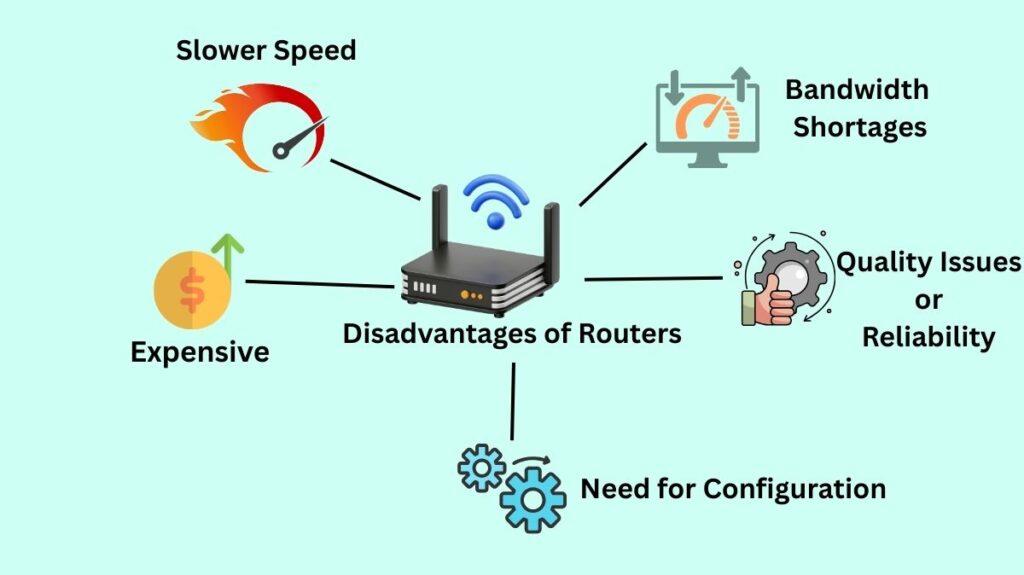
Routers have significant disadvantages despite their advantages:
- Slower Speed: Connections may be slowed down by routers’ analysis of several information layers, ranging from the physical to the network layers. “Connection waiting” can also be caused by multiple connected devices.
- Expensive: Usually more costly than hubs, bridges, and switches, among other network equipment.
- Need for Configuration: Configuration is necessary for routers to function properly; more complicated applications call for expert installation, which raises the price.
- Quality Issues/Reliability: Some contemporary devices using the 2.4GHz spectrum may frequently disconnect, particularly in crowded residential areas, and time transitions may not always be precise. Devices that do not support certain bands, such as 5GHz, may also have compatibility problems.
- Bandwidth Shortages: Network overheads caused by dynamic routing algorithms can slow down connections and use a lot of bandwidth. Additionally, bandwidth is used for routine network maintenance.
Applications of Routers
Nowadays, routers are utilized in the majority of networking communications:
- Connecting Hardware: Connects servers (such BSC, MGW, and SGSN) and other distant network equipment.
- Wireless and Wired Communication: Facilitates fast data transfer in both wireless and wired settings.
- Internet Service Providers (ISPs): ISPs commonly employ destination IP addresses to send different kinds of data (email, pictures, video, and audio) around the world.
- Access Control: This feature can be set up to give different users varying degrees of data access.
- Controlling network traffic and permitting several addresses to use a single Internet connection is known as congestion management.
- Logical groups of connected computers with various network prefixes can be linked together using connecting subnets.
- Port Forwarding: Private ISPs use this feature.
- Traffic Classification: Determines which data packet has to be handled first by using QoS.
Routing Protocols
Routing protocols are essential collections of rules and algorithms that allow routers to identify one another, share routing data, and dynamically choose the optimal path for data packet forwarding between networks. Among the examples are:
- Distance-Vector Protocols: Use a routing table to find the optimal route. Examples are IGRP and RIP.
- Link-State Protocols: Create a network map using topology data. Intermediate System to Intermediate System (IS-IS) and Open Shortest Path First (OSPF) are two examples.
- Hybrid Protocols: The advantages of link-state and distance-vector protocols are combined in hybrid protocols. Enhanced Interior Gateway Routing Protocol (EIGRP) is one example.
- Path Vector Protocols: Make use of a routing table and take into account other elements such as QoS and network policies. Border Gateway Protocol (BGP) is one example.
Also Read About What Is Data Encapsulation In Networking & De-Encapsulation
Router vs. Other Network Devices
- Router vs. Modem: A modem converts ISP signals into digital signals to link networks to the Internet, whereas a router creates networks and controls data flow both within and between them. A few ISPs include both onto a single gadget.
- Router vs. Switch: While a network switch passes data packets between groups of devices within the same network, a router forwards data between separate networks.
- Hub vs. Router: A hub links devices in a network and broadcasts data to all of the devices, whereas a router links various networks and routes data packets according to their addresses.
In conclusion, routers are essential to contemporary networking because they provide sophisticated communication, Internet sharing, and network security in a variety of settings.
