Let us discuss about Vishing, How Does Voice Phishing Work, Common Vishing Scenarios and How to Protect Yourself from Vishing.
Vishing Meaning
In a social engineering crime known as “voice phishing,” or “vishing,” scammers utilize voice messages or phone calls to fool victims into disclosing private information, like passwords or bank account information. Attackers frequently use tactics like number spoofing and sophisticated AI voice cloning to pose as reputable organizations, such as banks or government institutions, in order to create urgency and credibility. Avoid sharing private information on unwanted calls, confirm the identity of the caller by calling the company using their official number, and be cautious of requests for personal information that seem urgent in order to prevent vishing.
You can also read How To Prevent Whaling Attacks And How Does Whaling Work
How does Voice Phishing Work
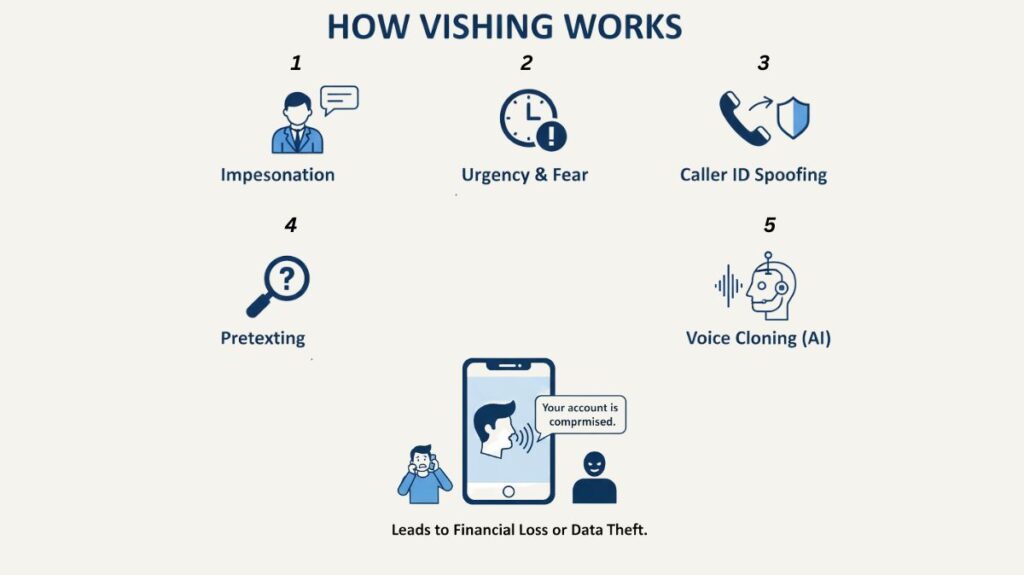
To control victims, vishing attacks frequently combine a number of social engineering techniques:
Impersonation: Bank representatives, government officials (such as those from the IRS or Social Security Administration), tech support agents, or even a distressed family member are all examples of scammers posing as trustworthy organizations.
Urgency and Fear: By stating there is a fraudulent charge, a pending legal matter, or an issue with the victim’s account, the caller frequently incites fear or a sense of urgency. They put pressure on the victim to take immediate action in order to prevent unfavourable outcomes, which may impair judgement.
Caller ID Spoofing: Using technology, attackers can spoof their caller ID so that it looks like the call is coming from a real company.
Pretexting: The fraudster fabricates a plausible, made-up situation or “pretext” to cover up their information request. For instance, in order to resolve an issue or handle a refund, they may claim that they must confirm your identity.
Voice Cloning (AI): Criminals employ artificial intelligence (AI) to mimic a person’s voice in more sophisticated attacks, which makes the call appear even more authentic particularly when they are posing as a well-known supervisor or colleague.
Examples
- A fake bank representative calling to “verify” your account after suspicious activity.
- A recorded message pretending to be from the IRS, demanding immediate payment.
- A tech support call warning of a virus on your computer and asking for remote access.
Common Vishing Scenarios
Bank or Financial Institution Impersonation: Claiming to be from the fraud department of your bank, the caller warns you of questionable activity on your account. They then want your PIN, account number, or other private information in order to “verify” your identity or “resolve the issue.”
Tech Support Scams: The caller poses as someone from a well-known IT business, such as Apple or Microsoft, and says they have found a virus or other issue with your computer. Convincing you to pay for a phoney service or give them remote access to your device is their goal.
Government Scams: The fraudster poses as an IRS or Social Security Administration official and threatens to take legal action or jail the victim if they don’t instantly give up personal information or pay a fictitious debt with wire transfers or gift cards.
Grandparent Scams: Often speaking in a panicky tone, the caller poses as a grandchild who is in dire need of money sent to them because they were in an accident or were detained.
You can also read What Is Spear Phishing Attack? Phishing Vs Spear Phishing
How do vishing emails avoid detection?
Not all phone calls are the first step in a vishing attack. Many attackers begin their fraud by pretending to be a reliable or authoritative source in a carefully constructed email. They convince the recipient to call them to follow up on their demands. How can phishing emails get past email security filters when a vishing attack starts with one? Three factors could be at play here:
No links in email: Malicious links in emails are quickly detected by security systems. However, a vishing email usually asks the receiver to call, thus it doesn’t require links that are detectable by ordinary security measures. The content places more emphasis on making a phone call than on the conventional clickable buttons or links that are common in phishing attempts.
Email from a so-called authentic sender: Sender Policy Framework (SPF), Domain Based Message Authentication Reporting (DMARC), and DomainKeys Identified Mail (DKIM) are authentication screenings that impersonated email accounts can pass if they are sent from a personal email address, such a Gmail account.
Ineffective email security tools: Basic email security systems may classify an email as low risk if it passes the first two filters and is sent to the recipients’ inboxes. Advanced email security tools that are made to identify and stop ransomware, phishing efforts, and business email compromise will help lessen this frequent issue.
In the cybersecurity field, phone numbers are not frequently monitored and disseminated as indicators of compromise (IOC), in contrast to URLs. Vishing campaigns are more likely to avoid standard email security checks when phone numbers are not structured.
You can also read Difference Between DoS Vs DDoS Attack, Types & Advantages
How to Protect Yourself from Vishing
Be Skeptical of Unsolicited Calls: Watch out for any unexpected calls, especially if they want for personal information or urgent action.
Verify the Caller’s Identity: If someone calls claiming to be from a business or government organisation, end the call and call them back using a number you know is correct (from their business card, recent statement, or official website, for example). Never call someone using a number they provide you.
Never Give Out Personal Information: Credible companies won’t call you without permission and seek for private information like your credit card number, passwords, PINs, or Social Security number.
Don’t Be Pressured: In order to get you to act without thinking, scammers frequently instill a sense of urgency. A trustworthy organization will give you time to confirm their statements.
Use Call-Blocking Tools: To cut down on the quantity of spam and scam calls you receive, use call-blocking applications or services provided by your phone provider.
Educate Yourself and Others: Being aware is the best defence. Keep up with the most recent scam tactics and let your loved ones know about them, especially if they could be more susceptible to these attacks.
Report Suspicious Calls: In the event that you think you have been the victim of a vishing scam, notify the appropriate authorities, such as the Federal Trade Commission (FTC) in the United States.
You can also read Email Phishing Attacks, Why Do Hackers Use Phishing Emails?
