This article gives an overview about Whaling Attacks, How it works, types, How to Identify it and How To Prevent Whaling Attacks.
What is a Whaling Attack?

One of the most advanced and dangerous types of spear phishing is called “whaling,” which targets prominent members of an organization. It is also known as CEO fraud or whale phishing.
A “big fish” or “whale” in a firm is the target of an attacker, which is where the phrase “whaling” originates. Compared to typical phishing attacks, these attacks are frequently more challenging to identify and stop due to their extreme targeting.
You can also Types Of Password Attacks And How Password Attacks Work?
Key Targets and Objectives
Whaling attacks target only top executives or senior decision-makers who have significant influence, high authority, and sensitive access within the organization.
Target Audience: Senior managers, directors, board members, and C-level executives including the CEO and CFO are frequently targeted. Because they have the power to access extremely private data or approve large financial transactions, these people are targeted.
Primary Goals (Exploitation): Tricking the victim into doing something that will help the attacker is the primary goal. Authorizing a fraudulent wire transfer is the most frequent effect, and it can cause the business to suffer large financial losses. Obtaining access to computer systems, exposing private information (such as payroll records, customer information, or intellectual property), or stealing login credentials are further objectives.
You can also read How To Prevent Password Attacks, Advantages & Disadvantages
How does Whaling Work
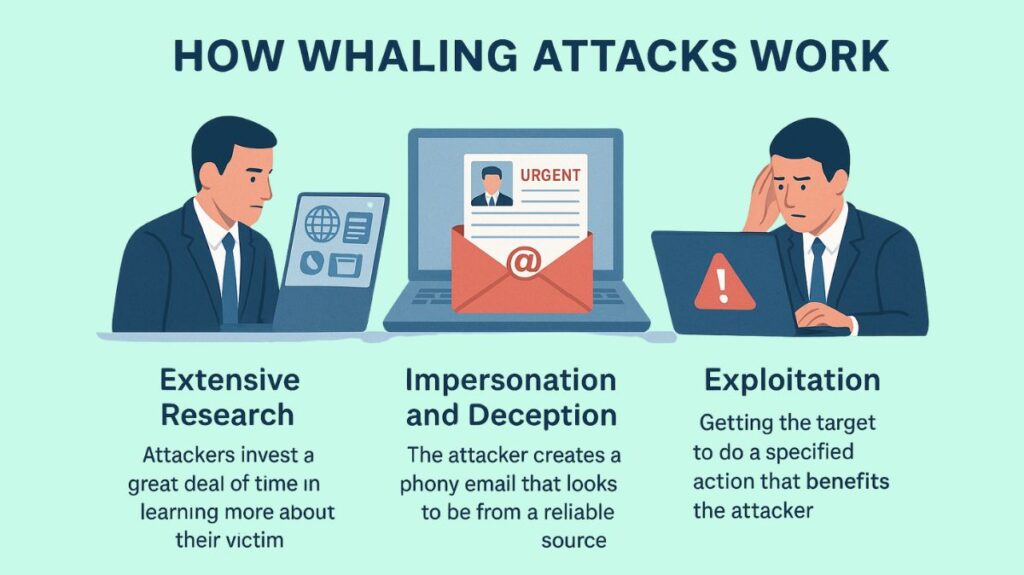
Whaling attacks are carefully prepared and carried out. Usually, they comprise:
Extensive Research: Attackers invest a great deal of time in learning more about their victim. Public resources such as news articles, corporate websites, and social media platforms like LinkedIn and Twitter are used to gather information on the executive’s personal and professional life, role within the organization, business partners, and even communication style.
Impersonation and Deception: Usually a coworker, business associate, or legal organization, the attacker creates a phoney email that looks to be from a reliable source. Utilizing the information acquired during the reconnaissance phase, the highly personalized email makes the message appear genuine. For instance, a phoney email can pretend that the CEO of the business is requesting an urgent wire transfer to a vendor and is sending it to the CFO.
Exploitation: Getting the target to do a specified action that benefits the attacker is the aim of a whaling attack. This can consist of:
- Authorizing a fraudulent wire transfer: Since it might cause the business to suffer large financial losses, this is the most popular goal.
- Revealing sensitive data: The executive could be tricked by the attacker into divulging private information, such IP, client information, or employee payroll details.
- Stealing credentials: In order to gain access to the company’s network and initiate more attacks, the attacker may try to obtain the executive’s login credentials.
How to Identify a Whaling Attack

Red flags to look out for even though whaling attacks are meant to be incredibly convincing:
Urgency and Pressure: With the potential of dire repercussions if the request is not fulfilled right away, the email frequently conveys a sense of urgency. The purpose of this is to get around standard verification methods.
Unusual Requests: Any email asking for a wire transfer, changing your password, or disclosing private information should raise suspicions, especially if the sender is unusual.
Slight Discrepancies: A spoof domain that closely resembles the genuine one, such as microsft.com rather than microsoft.com, might be the sender’s email address. Examine the email address in its entirety.
Requests for Confidentiality: The attacker can advise the target to keep the request private, citing a “confidential matter.” This is a traditional social engineering technique to keep the target from getting a second viewpoint or asking others to confirm the request.
You can also read Different Types Of MitM Attack, How It Work And Advantages
Example of a whaling email
From: “CEO Agarapu Ramesh” Ramesh.agarapu@ceo-company.com
Subject: Confidential — Wire transfer approval needed today
Message:
“Hi, I’m in a board meeting overseas and cannot be disturbed by phone. Please process the attached payment authorization for our new supplier immediately. This is time-sensitive and must be completed before close of business. Keep this confidential.”
Red flags:
- Urgency + secrecy.
- Unusual sender domain.
- Request bypassing normal process.
What to do if suspected
- Do not respond or click any links/attachments.
- Verify request via a trusted method (direct call, official contact).
- Report to IT/security immediately with full email headers.
- If money or data was already sent, contact bank/legal team immediately to try recovery.
You can also read What is Reconnaissance Attack, How it Works, History & Types
How to Prevent Whaling Attacks
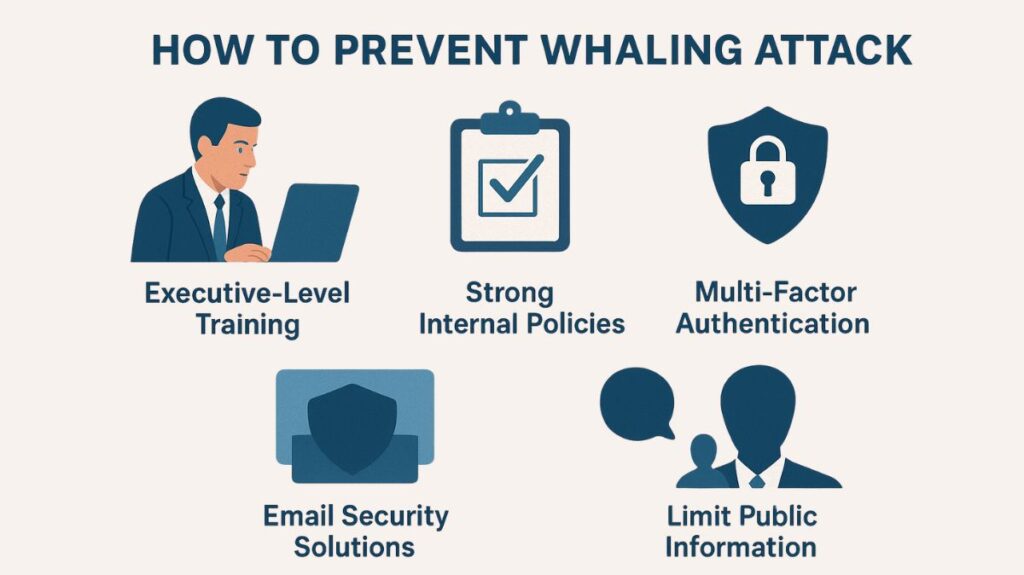
It takes a multifaceted strategy to defend against whale attacks:
Executive-Level Training: High-profile staff, such as C-level executives, should receive specialized cybersecurity training. These people are obvious targets and must understand the particular strategies employed in whaling.
Strong Internal Policies: Adopt a “separation of duties” or “dual-approval” policy for all requests for sensitive data and financial transactions. A secondary channel, like a phone call to a recognized number, should be used to confirm any wire transfer request instead of an email response.
Multi-Factor Authentication (MFA): Apply MFA to all high-privilege and executive accounts. An attacker will be blocked without the second form of authentication, even if they manage to steal a password.
Email Security Solutions: To identify and flag faked domains, strange emails, and other indicators of a whaling attack, use sophisticated email security filters and anti-impersonation software.
Limit Public Information: Urge CEOs to communicate as little personal or professional information as possible with the public, particularly on social media. This information is used by attackers to craft phishing emails that are more convincing.
Phishing vs Spear Phishing vs Whaling
| Feature | Phishing | Spear Phishing | Whaling |
|---|---|---|---|
| Target audience | Anyone (broad, random users) | Specific individuals or groups | High-level executives / top management |
| Personalization | Generic (e.g., “Dear User”) | Customized with personal details | Highly customized, executive-level tone |
| Volume | Mass emails sent to thousands | Small group or single person | Very few, carefully selected targets |
| Common goals | Steal passwords, credit cards, spread malware | Gain access, steal confidential data, financial fraud | Authorize big wire transfers, steal trade secrets, exploit executive authority |
| Message style | Poorly written, obvious errors | Professional, convincing, tailored | Formal, business-like, executive-level language |
| Risk level | Low–Medium | High | Very High (can cost millions) |
| Examples | “Your account will be closed, click here to reset” | Fake HR email asking for employee tax info | Fake CEO email ordering urgent fund transfer |
You can also read Different Types Of Buffer Overflow Attacks And Advantages
