HTTPS Spoofing
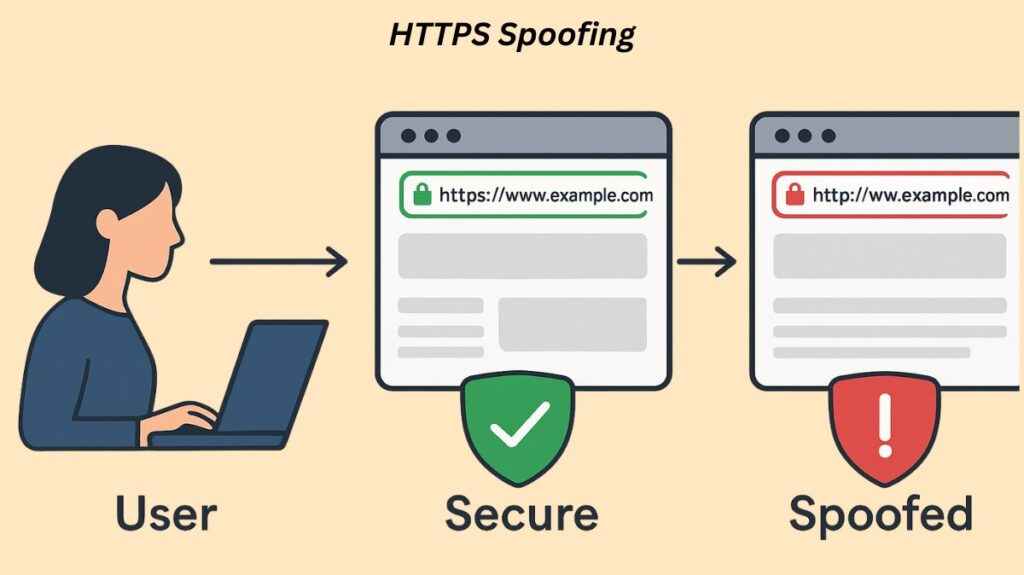
HTTPS spoofing is a type of cyberattack, usually a phishing attacks, in which the attacker makes a fake website that appears precisely like the real one and, most importantly, shows the padlock icon and ‘https://’ in the address bar of the browser.
This attack deceives users into inputting sensitive information, such as login passwords and financial information, by taking advantage of their faith in the HTTPS symbol, which is intended to signify a secure and secured connection. By displaying these reliable security symbols, the attacker can obtain private data that the unwary user enters, including login credentials and financial information.
The most prevalent version of this attack is actually based on a flaw in the International Domain Name (IDN) system, even if the names correspond to the protocols (HTTP/HTTPS). Another kind of man-in-the-middle (MITM) attack is HTTPS spoofing.
How HTTPS Spoofing Works (IDN Homograph Attack)
The IDN Homograph Attack is the main method for HTTPS spoofing. This method uses a legitimate security certificate in conjunction with visual trickery.
Taking advantage of Internationalized Domain Names (IDNs): IDNs enable the use of Unicode letters from different alphabets (like Greek or Cyrillic).
Using Homoglyphs: By substituting a homoglyph, or similar character from a non-Latin alphabet, for one or more conventional ASCII characters, an attacker can register a domain name that is visually identical to the target domain. For example, depending on the typeface, the Cyrillic character “Ά” and the Latin letter “I” (capital I) appear to be the same. Instead of using Google.com, a fraudster can use non-Latin characters to register ơοοʡle.com.
Getting a Certificate: For this phoney domain, the attacker buys a genuine, reasonably priced Domain Validation (DV) SSL/TLS certificate. This legitimate certificate is what enables the fraudulent website to show the browser’s ‘https://’ security indicators and the trusted padlock icon.
Attracting Victims: Using phishing emails or malicious links, attackers entice visitors to visit the spoof website.
Data Theft: The victim enters sensitive information after seeing the familiar website and the reliable security symbols, which allows the attacker to obtain it.
The Role of Punycode
Punycode, which uses ASCII to represent Unicode characters, is used to store and process IDNs because the original domain name system was not made for Unicode.
- Upon registration, an IDN domain such as ɡοοɡlе.com is transformed into a Punycode string (for example, xn--l-r1aa31la42e.com).
- The majority of contemporary browsers conceal the true underlying Punycode address by automatically displaying the decoded Unicode (homoglyph) version of the URL to the user. The deceit is made possible by this automatic display.
Also Read About Advanced Phishing Techniques, Prevention And Mitigation
Related Spoofing Techniques
Although the most prevalent type of HTTPS spoofing is homograph attacks, the phrase can also refer to other types of attacks that undermine TLS trust:
- Using certificates that are approved by the browser but may have come from a rogue or hacked Certificate Authority (CA) is known as forging.
- TLS Downgrade Attacks: Making the user and server use a cypher suite or earlier, less secure protocol that is simple for the attacker to crack.
- MitM Combination: This method intercepts communication and reroutes the user to the fraudulent server without the need for social engineering by combining HTTPS spoofing with other MitM techniques like ARP spoofing, IP spoofing, or DNS cache poisoning.
Risks of HTTPS Spoofing
Falling for HTTPS spoofing exposes victims to a number of grave risks, such as:
- HTTPS spoofing puts people and organizations at serious danger in a number of ways. The following are a few possible risks:
- Financial Losses: Unauthorized transactions made on spoof websites may cause victims to incur financial losses.
- Sensitive Information Compromise: Users may unintentionally provide malicious actors access to private and sensitive data, including financial information and login credentials.
- Unauthorized Account Access: This allows hackers to access user accounts without authorization, which can result in more data breaches and exploitation.
- A successful spoofing campaign can cost businesses customers’ trust, harm their brand’s reputation, and possibly result in legal and regulatory repercussions (such as fines under the CCPA or GDPR). Attackers may also disseminate software, including ransomware or botnet clients, using counterfeit websites.
Also Raed About How Does Voice Phishing Work And Common Vishing Scenarios
Prevention of HTTPS Spoofing
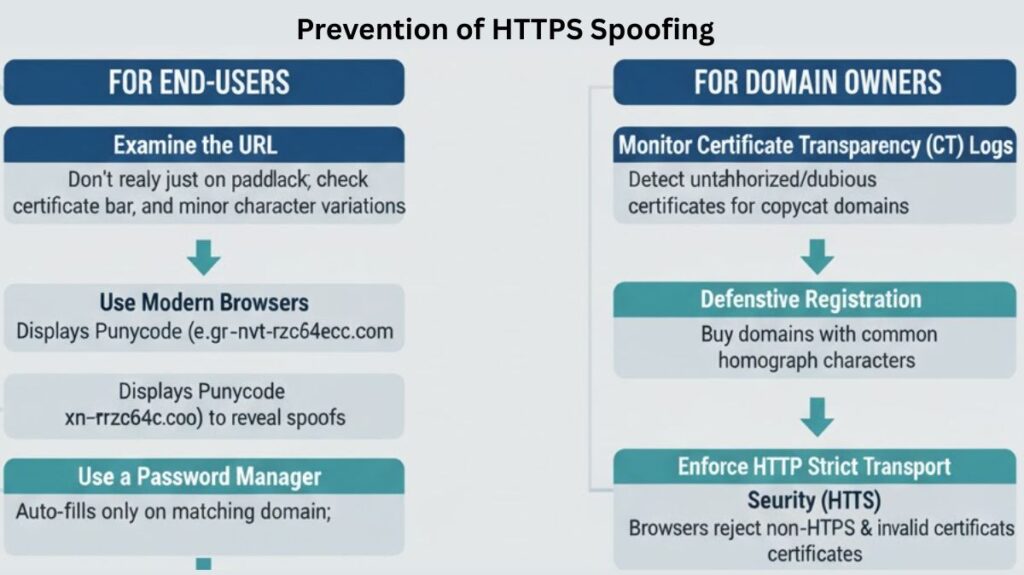
For End-Users:
- Examine the URL: Carefully don’t depend just on the padlock emblem. Check the certificate details (by clicking the padlock icon), pay special attention to the address bar, and look for any minor character variations in the domain name.
- Use Modern Browsers: The spoof name is frequently displayed in the address bar of modern browsers in its Punycode form (xn--nvt-rzc64ecc.com, for example), making the deceit instantly apparent.
- Use a Password Manager: Password managers are made to only automatically fill in login information when the recorded domain name and the domain in the address bar match. The manager will not fill out the form if the domain is a homoglyph, which is a serious red flag.
- Use Multi-Factor Authentication (MFA): MFA limits the impact even in the event that credentials are taken through a fake website, offering an essential layer of protection.
- Advanced Mitigation: To force the display of the encoded domain name and instantly expose the spoof, users can disable Punycode display support in their browser settings.
Domain Owners:
- Monitor Certificate Transparency (CT) Logs: In order to determine whether a Certificate Authority (CA) has granted unauthorised or dubious certificates for copycat domains that are aimed at their brand, organisations should keep a close eye on CT logs.
- Defensive Registration: Buying domains with frequent homograph characters that could be used for impersonation is known as defensive registration.
- Enforce HTTP Strict Transport Security (HSTS): By putting HSTS into practice, browsers are guaranteed to reject non-HTTPS connections and invalid certificates for the authentic domain.
- User Education: Educate users on the significance of verifying the entire URL and about homograph attacks.
Detection & incident response
- Keep an eye out for odd certificate chains and TLS handshakes at perimeter proxies.
- Keep an eye on CT logs and configure alerts for when your domains receive new certificates.
- Rotate keys, block malicious IPs, examine CA logs, revoke compromised certificates, and require reauthentication if spoofing is found.
- If a CA is hacked, notify the impacted users and work with browser vendors and CAs.
Also Read About How Does Voice Phishing Work And Common Vishing Scenarios
