Man-in-the-Middle MitM phishing
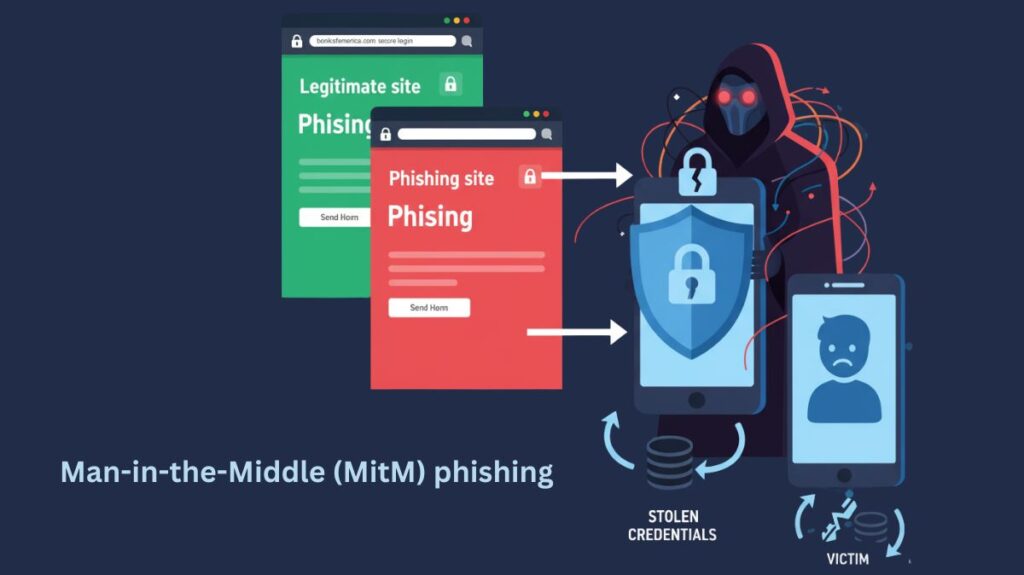
Man-in-the-Middle (MitM) phishing is a sophisticated sort of cyberattack in which a threat actor eavesdrops on a user’s conversation with a legitimate service in order to instantly acquire credentials or other private data. By acting as a proxy between the user and the legitimate website, MitM phishing makes it considerably more difficult to identify than classical phishing, which depends on a phoney website.
Also Read About Different Types Of MitM Attack, How It Work And Advantages
How MitM Phishing Works?
The attack frequently makes use of a reverse proxy, which is a server that stands in between the target website and the user’s browser. This is a detailed breakdown:
First Deception: The attacker sends a phishing email or text with a link. The link appears valid but sends users to the attacker’s reverse proxy instead of the website.
Intercepting Communication: The victim’s browser connects to the proxy server when they click the link, intercepting communication. After that, the proxy server concurrently launches a session with the actual website. All information is passed through the proxy, including cookies, login forms, and web pages.
Real-time Credential Theft: The proxy records every event while the user interacts with the website, which is actually a live, mirrored version of the original one. As soon as the victim inputs their username and password, the proxy immediately records these details.
Bypassing Multi-Factor Authentication (MFA): When it comes to getting around Multi-Factor Authentication (MFA), MitM phishing is especially successful. Being a live middleman, the proxy can also instantly record tokens, biometric confirmations, or one-time passcodes (OTPs). As soon as the user enters their MFA code on the fraudulent website, the proxy forwards it to the authenticated website. The attacker can now access the account completely as a result.
Smooth User Experience: The proxy takes the user’s credentials and MFA code and then sends them to the authentic website’s logged-in account. The user has no idea that their session has been compromised; they see a successful, typical login.
Also Read About What Is Spear Phishing Attack? Phishing Vs Spear Phishing
MitM phishing techniques
- All traffic travels through the attacker when users connect to these bogus coffee shops or airport hotspots.
- Ethernet poisoning or ARP spoofing: A local network attacker delivers traffic through their computer.
- DNS hijacking or poisoning: Attackers send victims to bogus websites using IPs they control (or a modified cache).
- The attacker forces or exploits non-HTTPS connections to break TLS and transfer credentials in plaintext.
- Reverse or transparent proxies: The attacker configures a proxy that logs session cookies and credentials while relaying requests.
- Live proxying phishing pages: To evade detection and obtain session tokens, sophisticated phishing pages instantly send credentials to the legitimate website.
How to prevent MitM phishing
For individual users:
- Use HTTPS at all times: Look for the lock icon and, if the browser alerts you, confirm the certificate.
- Avoid using public Wi-Fi that you can’t trust: Avoid using public networks to access sensitive accounts. If required, make advantage of a reliable VPN.
- Employ MFA (choose hardware tokens or authenticator apps): Phished passwords and usernames are insufficient on their own.
- Update your devices and browsers: Patches lessen vulnerability to network attack exploits.
- Employ DNS protection: Use reliable DNS resolvers whenever possible, and use DNS over HTTPS/TLS.
- Pay attention to certificate warnings: To log in, never get around certificate errors.
- Make use of password managers: They aid in the detection of fake URLs by only autofilling on domains that match exactly.
- Use apps instead of the web when using public Wi-Fi: Native apps frequently (though not always) make use of pinned certificates or more robust security.
For organizations / defenders:
- Implement HTTPS and HSTS (HTTP Strict Transport Security) everywhere.
- When it is feasible, use certificate pinning for mobile apps.
- ARP spoofing, rogue APs, and unusual DNS responses can be found by using network segmentation and monitoring.
- Use DoH/DoT for clients and DNSSEC on authoritative zones to implement secure DNS, and keep an eye out for DNS changes.
- Enforce strict MFA and keep an eye out for unusual logins or credential stuffing.
- To find phishing and proxying patterns, use logging and WAFs.
- Staff should receive user training on phishing cues, cert warnings, and rogue Wi-Fi.
If you suspect you were targeted or compromised
- Disconnect from the network (switch off cellular and Wi-Fi) right away.
- Passwords for impacted accounts should be changed from a trustworthy network or device.
- If at all feasible, remove the passwords for any active sessions and apps.
- Re-enroll MFA and take hardware tokens into consideration, particularly if SMS OTP could be intercepted.
- Check for malware on devices and erase or restore to a clean image if necessary.
- In the event that financial information is compromised, notify your bank or service providers.
- Inform the relevant authorities or the security team at your company about the occurrence.
Also Read About How Does Voice Phishing Work And Common Vishing Scenarios
