Important MAC Models, Types of MAC Systems, Use Cases and Operating System Implementations, Core Principles and Mechanisms, Mandatory Access Control (MAC), and the Mandatory access control advantages and disadvantgaes were all covered in this blog.
Define mandatory access control
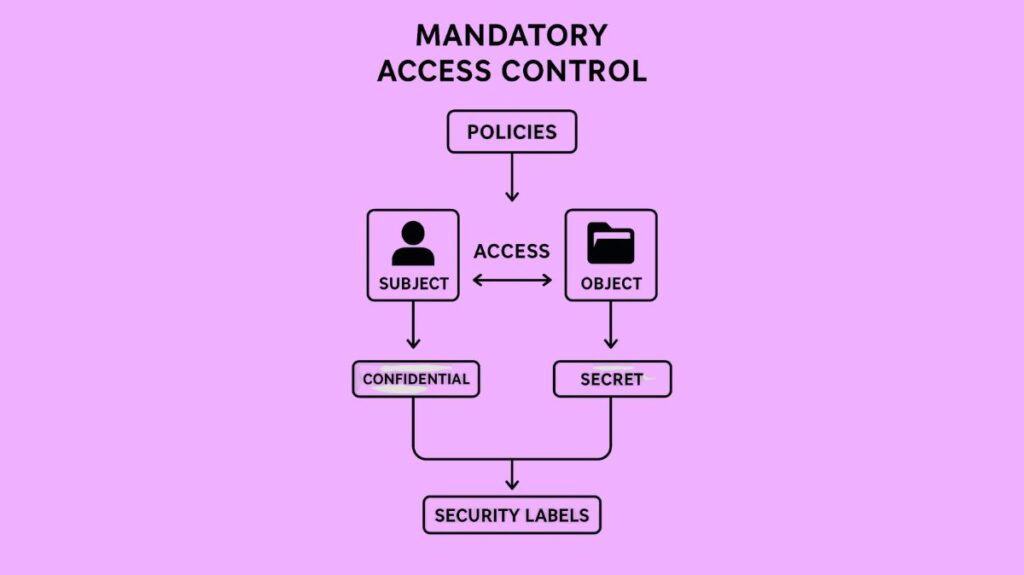
In the centralized security approach known as Mandatory Access Control (MAC), a central authority rather than the resource owner or user determines access to resources based on predetermined policies and security labels. Users are unable to control their own permissions, in contrast to Discretionary Access Control (DAC); instead, access is enforced by a central system according to the security clearance of the user and the level of sensitivity of the data. In extremely secure settings, such as the military, government, and healthcare, MAC is used to tightly regulate access to private data, thwarting insider threats and guaranteeing compliance.
In MAC, the operating system (OS) or security kernel rigorously enforces predetermined regulations that are used by a central authority to control resource access.
Also Read About MAC Address Tables In Switch For Network Data Forwarding
Core Principles and Mechanisms
The way MAC works is by giving persons and objects security properties (labels and clearances) and comparing them:
Security Labels (Objects)
A sensitivity label or classification level is given to each resource or object (such as files, databases, processes, network connections, shared memory segments, or IO devices). “Confidential,” “Restricted,” “Secret,” and “Top Secret” are a few examples of these classifications. Every named object on a trusted AIX system has a Sensitivity Label (SL).
Clearance Levels (Subjects)
Each user or process (subject) is given a security clearance level that denotes the highest level of sensitivity of the data they are officially permitted to view. The user can only work within the range of valid SLs that the system gives to each user account.
Enforcement and Access Decisions
The system compares the user’s clearance level with the resource’s security label. Only when the user’s clearance level matches or exceeds the resource’s sensitivity level is access allowed. Without requiring user intervention, this enforcement system prevents unauthorised access in a transparent manner.
Non-discretionary Control
All subjects and objects are subject to the same MAC policies. Access permissions cannot be delegated, changed, or overridden by users or resource owners. The main objective is to prevent a subject from transferring data to unapproved entities, providing others access to its privileges, or altering security features or access control regulations.
Important MAC Models
MAC frameworks frequently make use of structured models to accomplish particular security goals:
Bell-LaPadula Model
The Bell-LaPadula Model is primarily concerned with data privacy. It adheres to the idea that
- “No read up”: Information classified higher than the user’s clearance level cannot be read by the user.
- “No write down”: To stop high-clearance information from leaking to objects of lower classification, a user can only write data at their level or higher. Both government and military systems frequently employ this concept.
Biba Model
The fundamental tenet of the Biba model is “no write up, no read down,” which highlights data integrity. Only data at their integrity level or below can be written by users, and only data at their integrity level or higher can be read. By preventing users with lower integrity from tainting higher integrity data, this approach guarantees that judgements are founded on trustworthy data sources.
Types of MAC Systems
Two MAC system types are described by the sources according to the structure of security levels:
Multilevel Security Systems (MLS): Usually set up vertically, Multilevel Security Systems function using a hierarchical system of security levels. In order to avoid unwanted access to higher-level data and to ensure rigorous classification-based separation, users are only allowed access to information classified at or below their security clearance level. MAC and MLS have a long history together, especially in systems that safeguard sensitive military data.
Multilateral Security Systems: By combining both vertical and horizontal aspects of access control, multilateral security systems go beyond the conventional vertical hierarchy. Multilateral systems grant security clearances according to certain segments, compartments, or domains, as opposed to multilevel systems, which only use classification levels.
Also Read About Different Types Of MAC Addresses (Media Access Control)
Use Cases and Operating System Implementations
Data that could be seriously harmed by compromise, such trade secrets, financial transactions, or protected health information, must be safeguarded with MAC.
The industry standard for access control in settings that demand centralized policy enforcement and high security is MAC, which includes:
- Government and Military Systems: Systems used by the military and government to handle secret data.
- Healthcare: Employed to safeguard patient information in accordance with laws such as HIPAA.
- Critical Infrastructure: Used to protect technological systems that are in use.
- Corporate Environments: Used in production settings, cloud infrastructure, and CI/CD pipelines.
Certain operating systems employ MAC implementations, frequently departing from the strict limitations of conventional MLS systems:
- Linux: Examples of implementations include the well-known and intricate Security-Enhanced Linux (SELinux); AppArmor, which is renowned for its simplicity and configuration ease; and TOMOYO Linux, which employs a pathname-based methodology.
- Windows: Microsoft introduced Mandatory Integrity Control (MIC) in Windows Vista, adding integrity levels (IL) to processes.
- Apple: The TrustedBSD framework is implemented in iOS and macOS.
Mandatory access control advantages
Because of its strict enforcement, MAC provides a number of security advantages:
- Enhanced Security: Unintentional permission sharing is avoided to centrally maintained policies that only allow access to users who have been expressly granted permission.
- Policy Enforcement: To stop users from evading or changing controls, security policies are rigorously implemented at the system level (e.g., kernel-level enforcement).
- Compliance: GDPR, HIPAA, and PCI DSS compliance is made easier with structured and auditable access control.
- Insider Threat Mitigation: By enforcing a need-to-know basis, MAC reduces the danger of insider threats because even system administrators are unable to access sensitive data unless their security labels permit them.
- Clear Audit Trails: MAC records all user actions and access attempts, offering thorough logs for incident response and forensic investigation.
Mandatory access control disadvantages
MAC systems do have several disadvantages, though:
- Complexity: MAC systems are challenging to set up and maintain, necessitating constant label and classification updates.
- Decreased Flexibility: Users’ autonomy and freedom to share resources are restricted by the rigorous, policy-driven nature.
- Administration Burden and Cost: For applications with a large user base or complicated IT systems, it is impractical and costly because the administrator bears the full responsibility for configuring and managing all accesses.
Also Read About What Is Wi-Fi Eavesdropping, The Threat Of Network Snooping?
